A Compliance Assessment Document Sample for Technology Audits provides a structured framework to evaluate adherence to regulatory standards and internal policies within IT systems. This document outlines specific criteria, audit procedures, and evidence collection methods to ensure comprehensive technology compliance reviews. Utilizing such a sample enhances consistency and accuracy in identifying potential risks and gaps during technology audits.
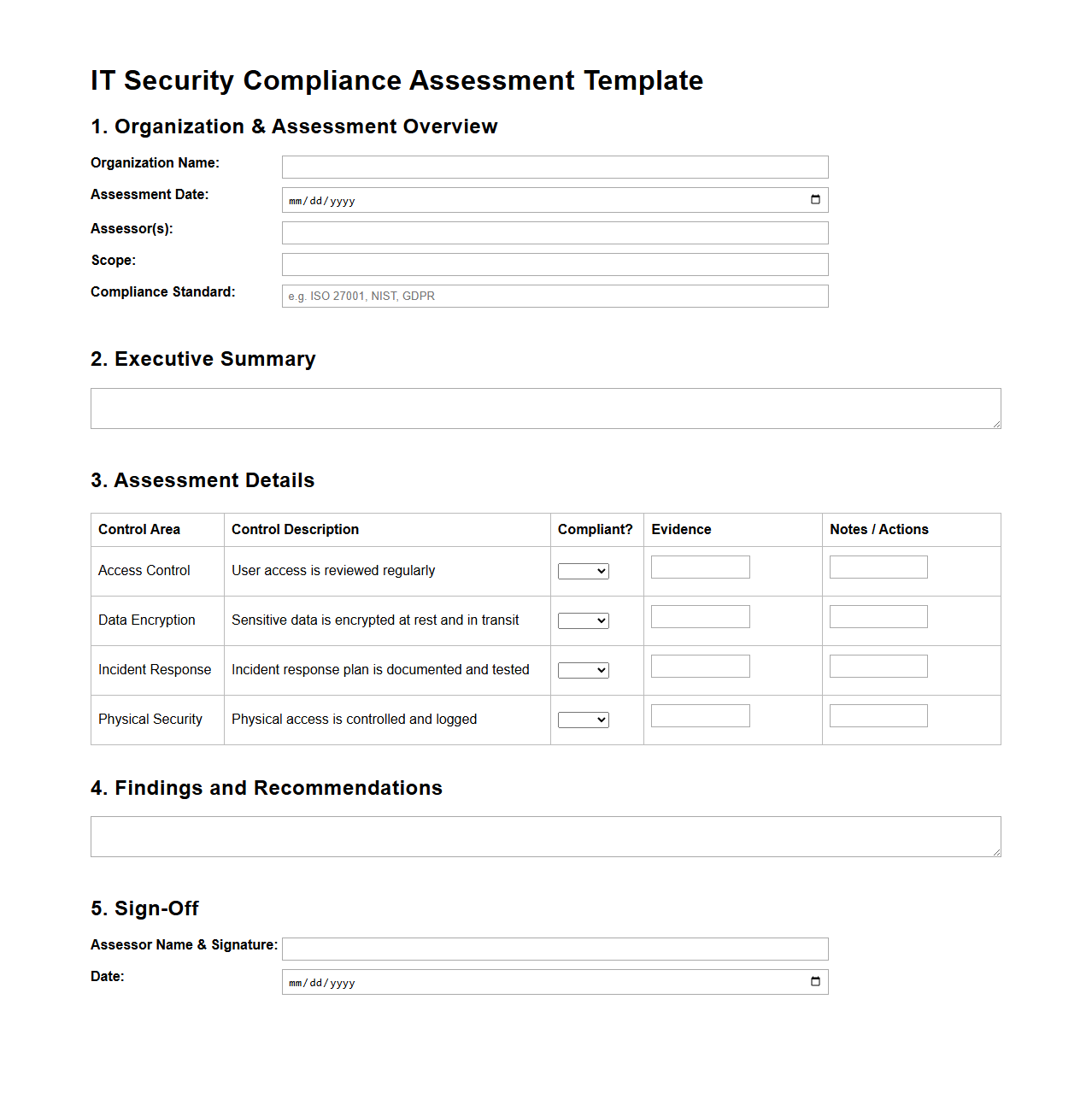
IT Security Compliance Assessment Template
An
IT Security Compliance Assessment Template document serves as a structured framework to evaluate an organization's adherence to cybersecurity policies, standards, and regulatory requirements. It includes predefined criteria, checklists, and questionnaires designed to identify vulnerabilities and measure the effectiveness of existing security controls. This template streamlines the audit process, ensuring comprehensive coverage of key compliance areas such as data protection, access management, and incident response protocols.
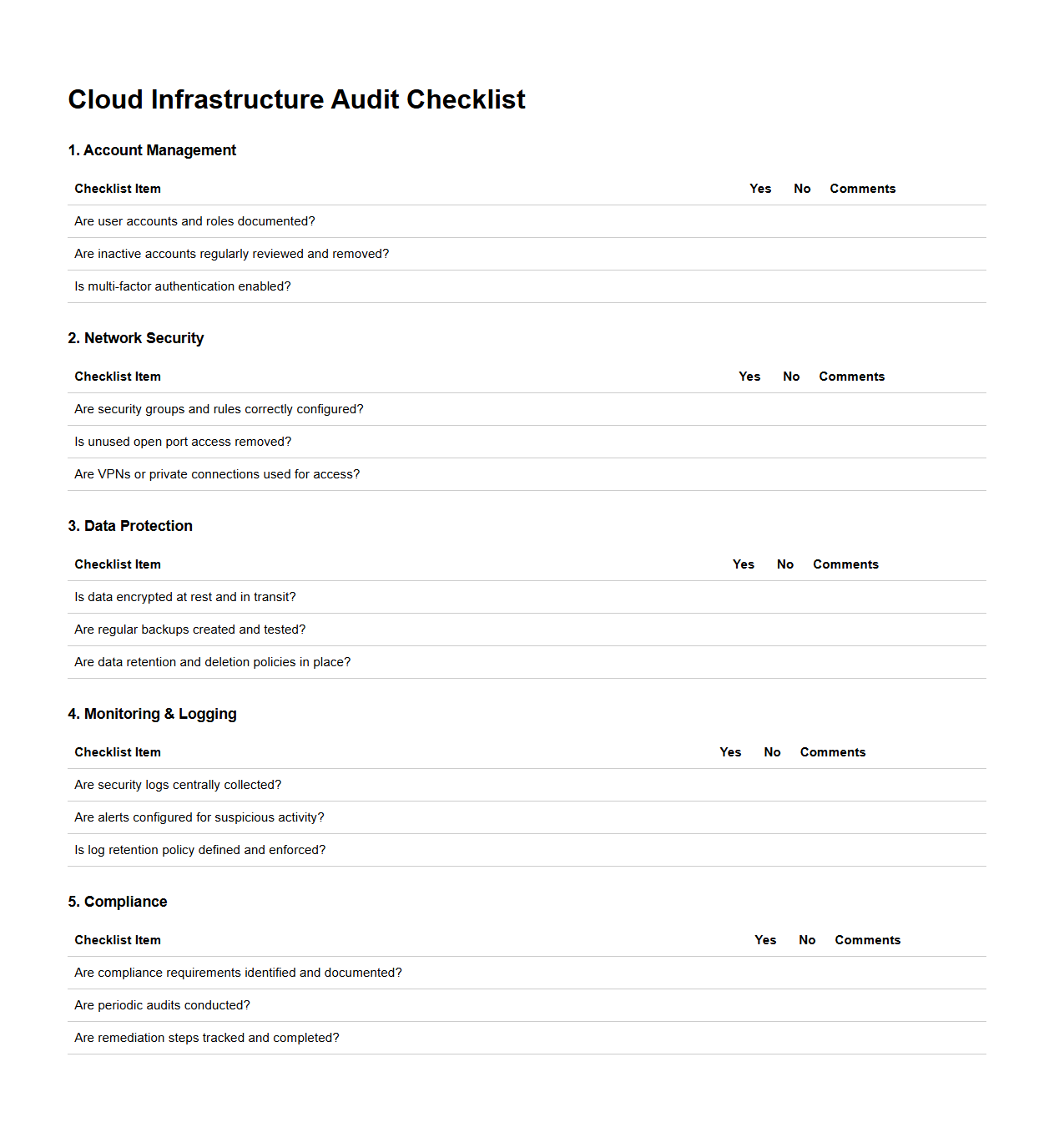
Cloud Infrastructure Audit Checklist
A
Cloud Infrastructure Audit Checklist document is a comprehensive tool designed to systematically evaluate cloud-based environments for security, compliance, and operational efficiency. It includes detailed checkpoints covering access controls, configuration settings, data protection measures, and regulatory adherence to ensure optimal cloud resource management. Organizations use this checklist to identify vulnerabilities, enforce best practices, and maintain compliance with industry standards such as ISO 27001 and GDPR.
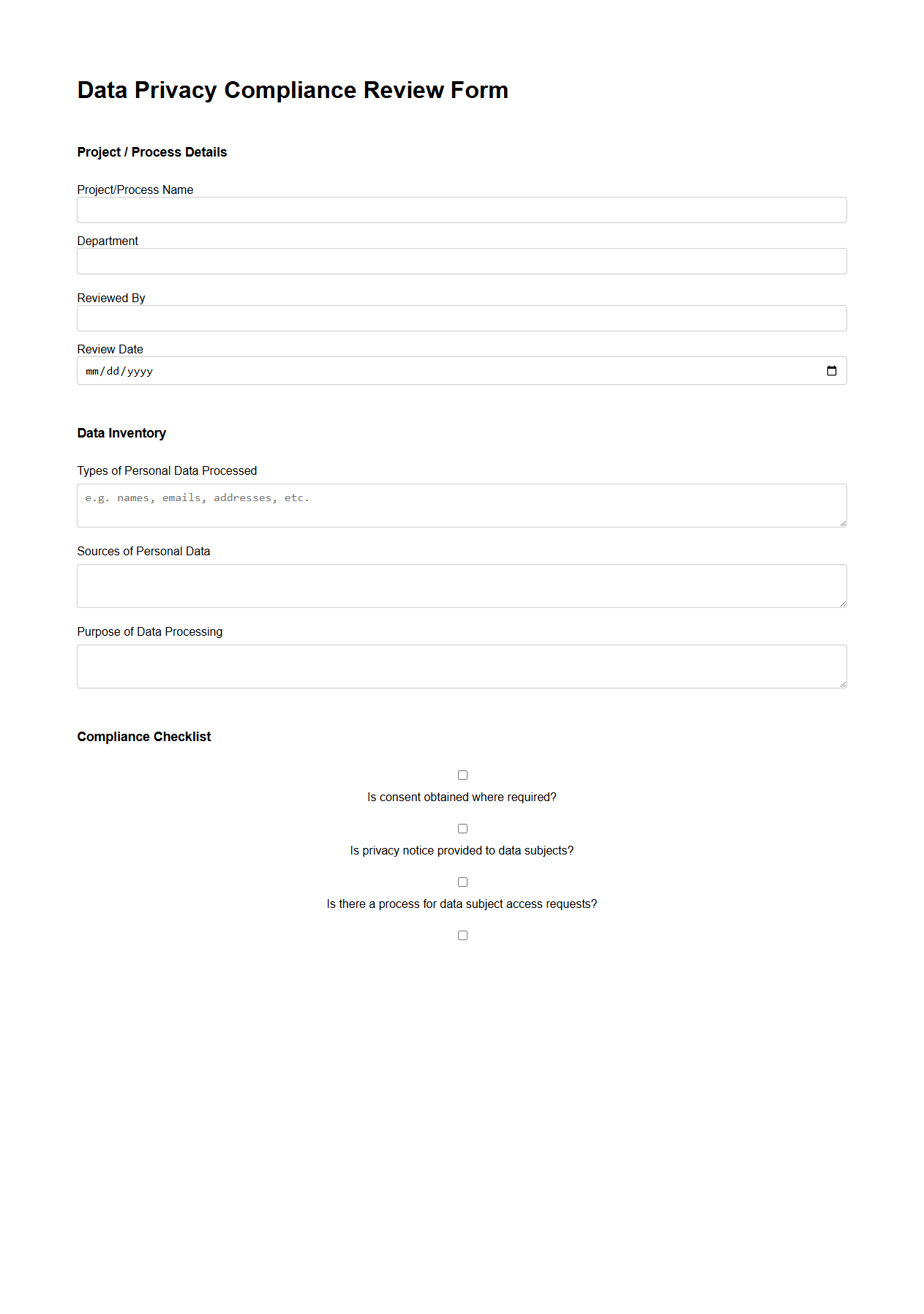
Data Privacy Compliance Review Form
A
Data Privacy Compliance Review Form document is a structured tool used to evaluate an organization's adherence to data privacy laws and regulations, such as GDPR or CCPA. It systematically assesses data handling practices, identifying risks and ensuring appropriate safeguards are in place to protect personal information. This document facilitates accountability and helps maintain regulatory compliance by documenting review outcomes and necessary actions.
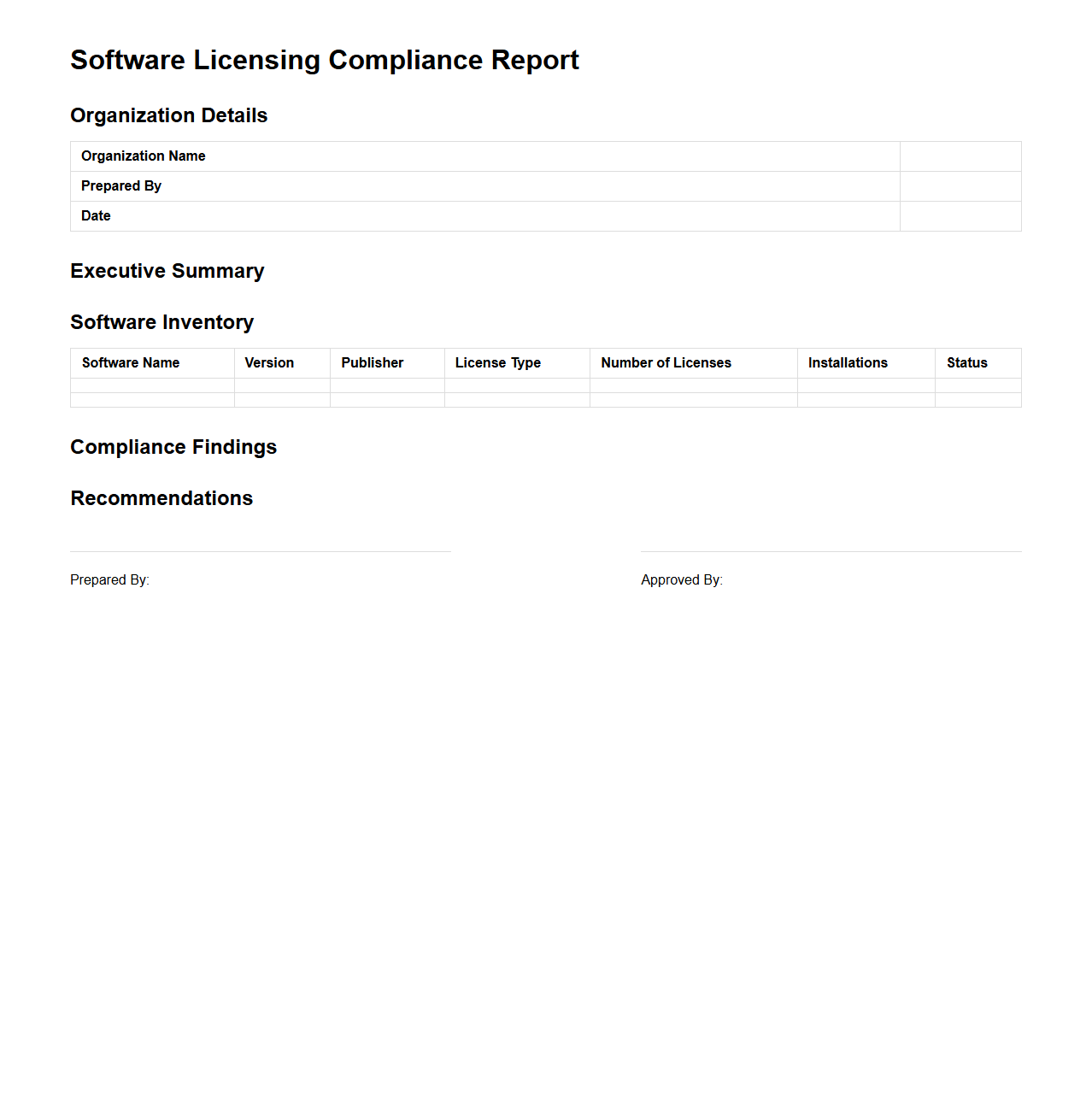
Software Licensing Compliance Report
A
Software Licensing Compliance Report is a detailed document that evaluates an organization's adherence to software license agreements, ensuring legal and financial compliance. It identifies discrepancies between purchased licenses and software usage, helping prevent unauthorized installations and potential penalties. This report supports risk management by providing clear insights into software inventory and license allocation.
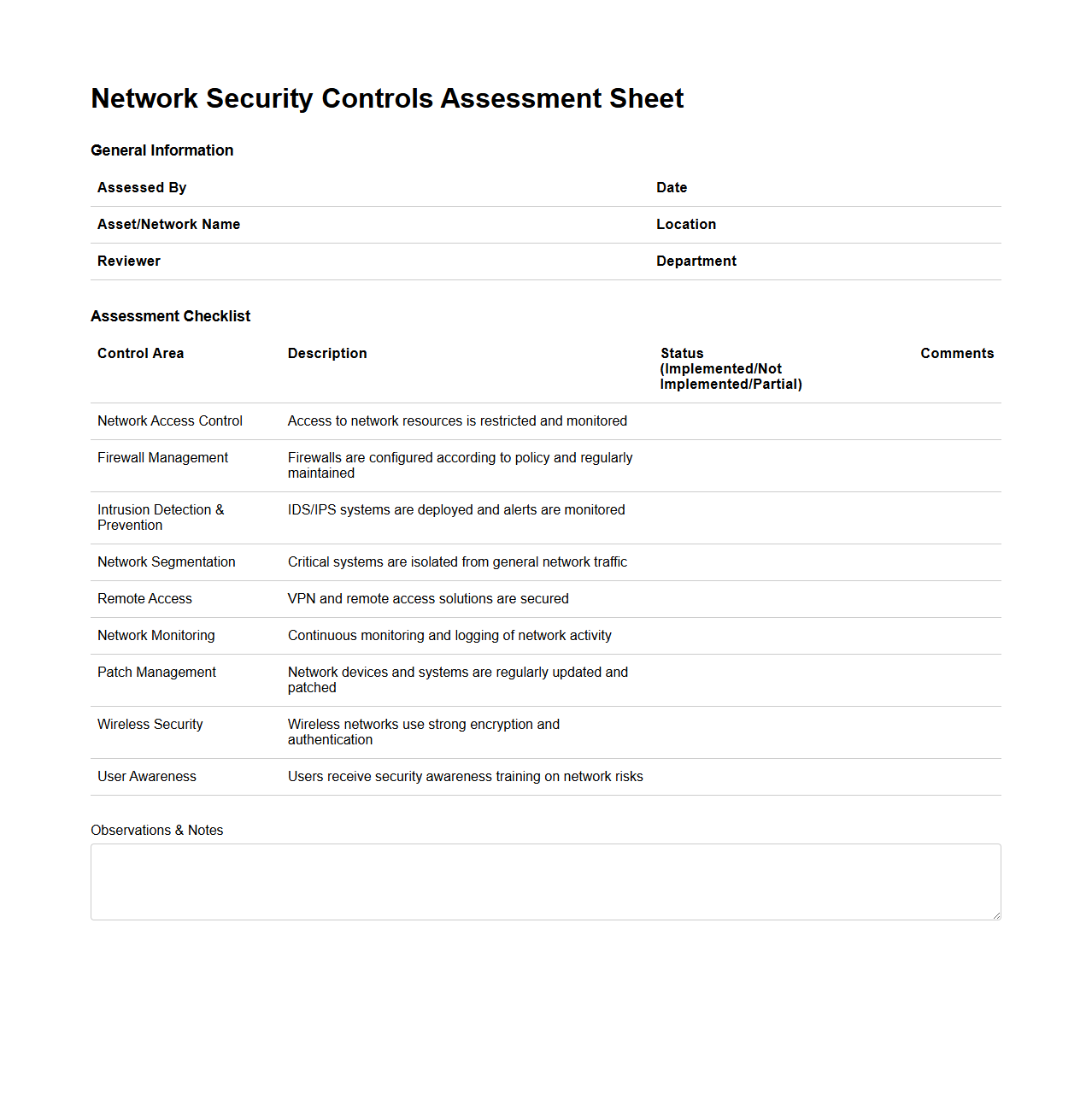
Network Security Controls Assessment Sheet
A
Network Security Controls Assessment Sheet document is a detailed tool used to evaluate the effectiveness and implementation of security measures within a network infrastructure. It outlines specific control standards, identifies vulnerabilities, and tracks compliance with organizational or regulatory security policies. This document helps IT teams prioritize risk mitigation efforts and supports continuous improvement in network defense strategies.
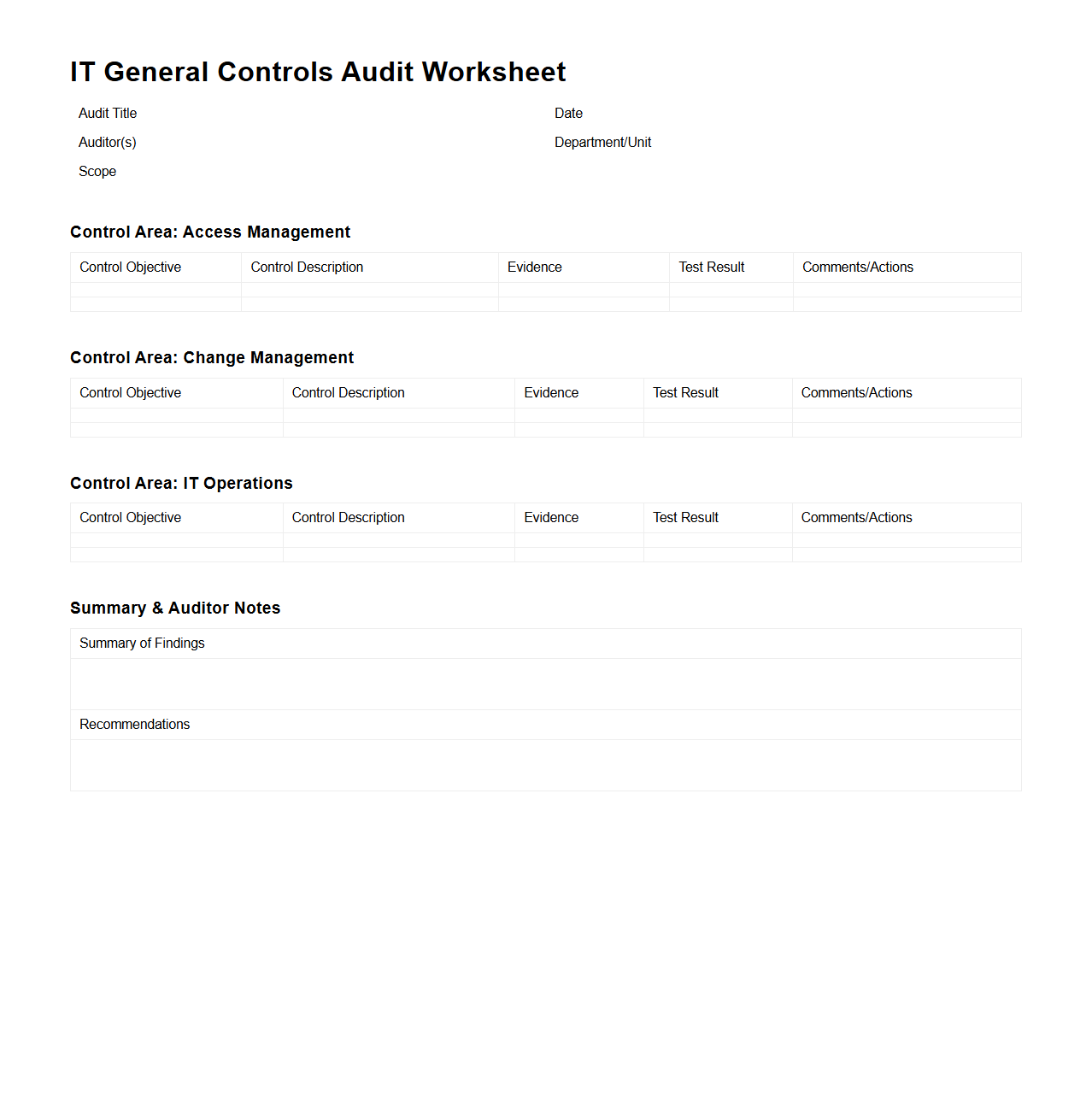
IT General Controls Audit Worksheet
The
IT General Controls Audit Worksheet document serves as a structured tool for auditors to assess and document the effectiveness of an organization's IT general controls, including access management, change management, and system operations. It facilitates systematic evaluation by providing predefined control objectives, testing procedures, and space for recording findings and recommendations. This worksheet ensures thorough compliance verification with regulatory standards such as SOX, HIPAA, and ISO 27001, improving overall IT governance and risk management.
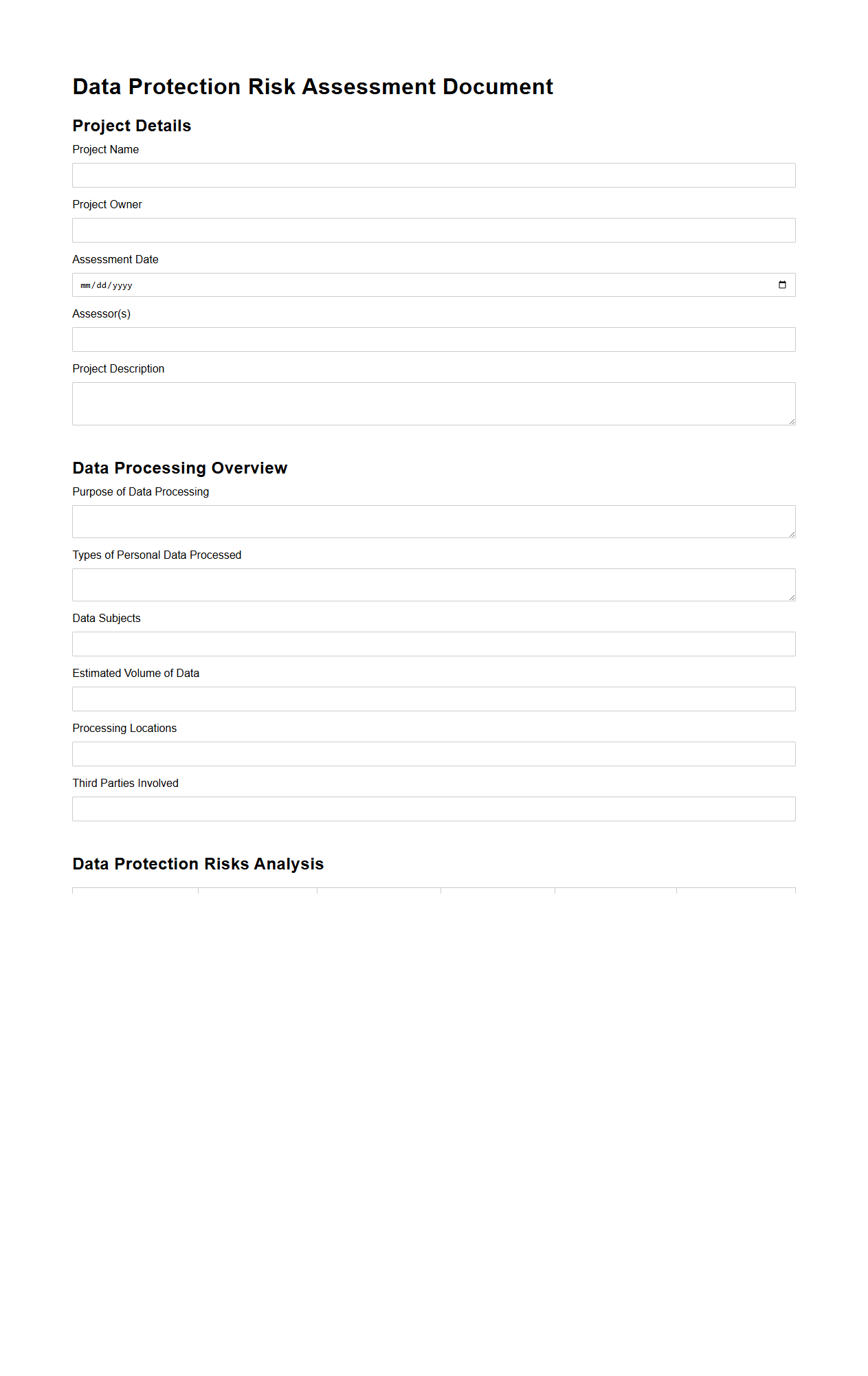
Data Protection Risk Assessment Document
A
Data Protection Risk Assessment Document identifies and evaluates potential threats to personal data within an organization, ensuring compliance with regulations like GDPR. It systematically analyzes vulnerabilities in data processing activities to mitigate risks related to unauthorized access, data breaches, and non-compliance penalties. This document serves as a critical tool for implementing effective data security measures and maintaining robust privacy standards.
Access Management Compliance Evaluation Sample
Access Management Compliance Evaluation Sample document provides a structured framework to assess the effectiveness of an organization's access controls and policies. It includes criteria for verifying user authentication, authorization processes, and adherence to regulatory standards such as ISO 27001 or NIST guidelines. This document is essential for ensuring comprehensive
access management compliance and mitigating security risks associated with unauthorized access.
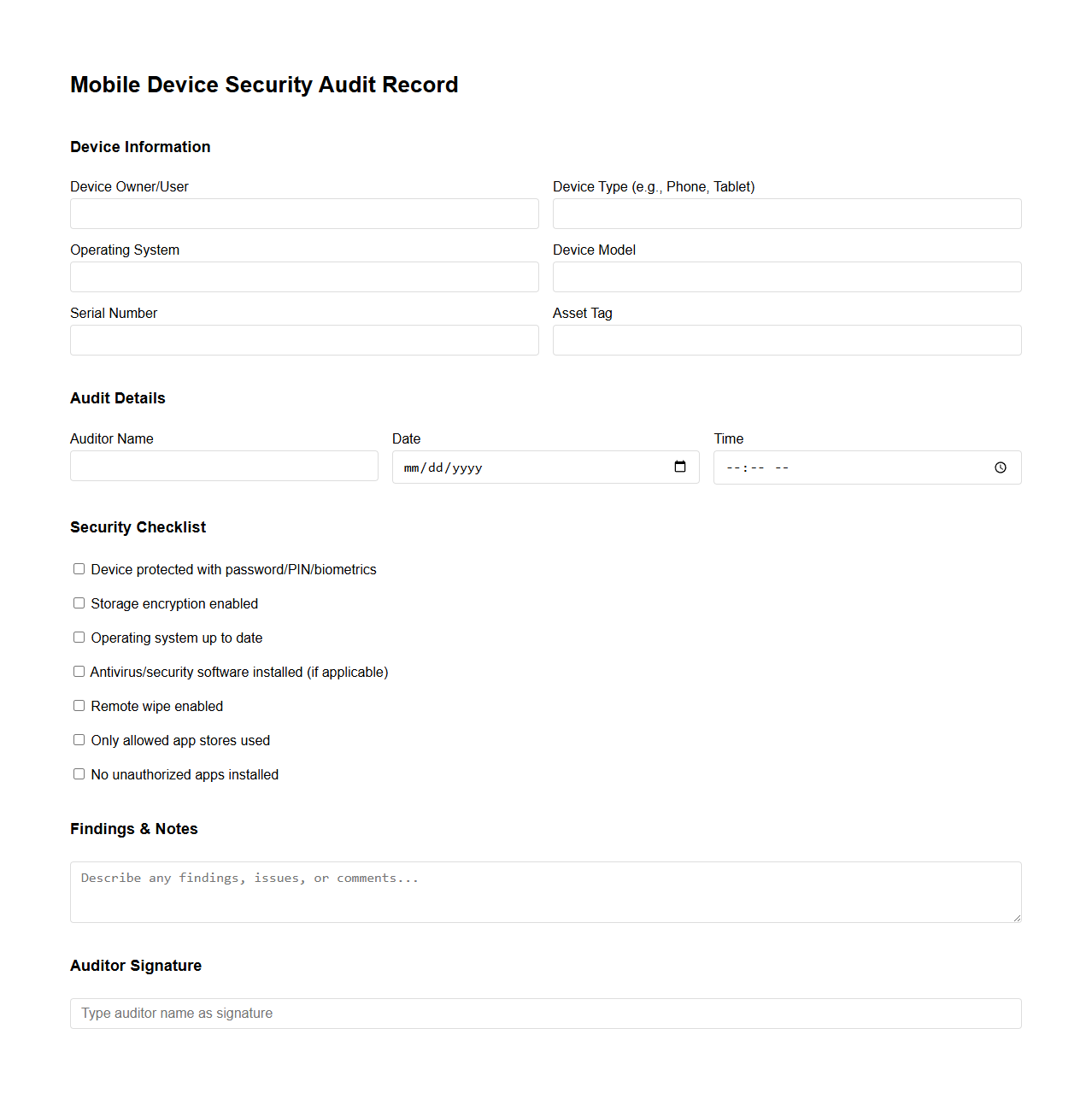
Mobile Device Security Audit Record
A
Mobile Device Security Audit Record document is a detailed report that tracks and evaluates the security status of mobile devices within an organization. It includes records of security incidents, compliance checks, software updates, and vulnerability assessments to ensure devices meet the organization's security policies. This document is essential for identifying risks, maintaining regulatory compliance, and enhancing the overall mobile security posture.
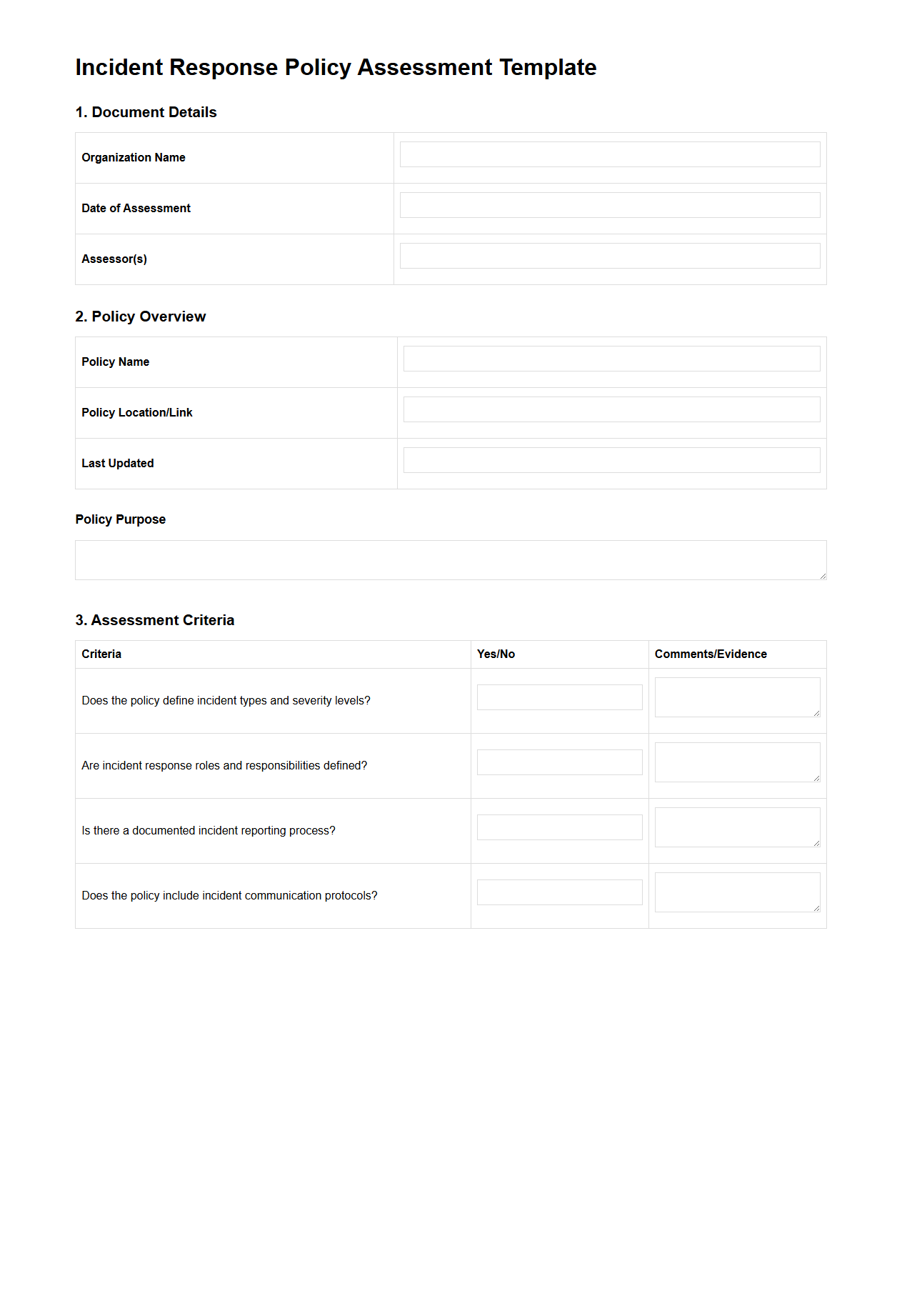
Incident Response Policy Assessment Template
The
Incident Response Policy Assessment Template document is a structured framework designed to evaluate and analyze an organization's incident response policies. It helps identify gaps, ensure compliance with industry standards, and improve the effectiveness of incident management processes. This template supports organizations in maintaining robust cybersecurity defenses by systematically reviewing policy components and readiness for potential security incidents.
What encryption standards are documented for data transmission in the compliance assessment?
The compliance assessment highlights the use of AES-256 encryption as the standard for securing data transmission. It ensures that all data transfers comply with industry-approved encryption protocols to protect sensitive information. The document also references the adoption of TLS 1.2 or higher for secure communication channels.
How does the compliance assessment address third-party vendor technology risks?
The assessment outlines a comprehensive vendor risk management framework that includes due diligence and continuous monitoring of third-party technologies. It emphasizes the importance of contractual obligations requiring vendors to adhere to security standards. Additionally, the document mandates periodic security assessments and audits of all third-party providers.
Are there documented procedures for incident response and technology audit trails?
The compliance assessment contains detailed incident response procedures designed to ensure timely identification and mitigation of security incidents. It also mandates the maintenance of technology audit trails to provide a clear record of system activities and changes. These protocols help in forensic analysis and regulatory reporting.
What evidence supports compliance with data retention policies in the assessment document?
The document provides retention logs and automated reports as evidence supporting compliance with data retention policies. It specifies timelines aligned with legal and regulatory requirements for storing and securely disposing of data. Additionally, system configurations enforcing data archiving and deletion rules are documented.
How does the document detail access control measures during technology audits?
The compliance assessment describes strict access control mechanisms including role-based access and multi-factor authentication during technology audits. It ensures that audit activities are restricted to authorized personnel only to maintain data confidentiality. The document also requires the logging of all access attempts and audit session activities.
More Technology Templates