A Incident Response Plan Document Sample for Network Security provides a structured framework for identifying, managing, and mitigating cybersecurity incidents within a network. It outlines clear procedures, roles, and communication strategies to ensure a swift and effective response to threats. This document helps organizations minimize damage, recover quickly, and strengthen overall network security posture.
Network Security Incident Identification Template
The
Network Security Incident Identification Template document serves as a structured framework for recognizing and documenting potential security breaches or threats within a network. It outlines critical indicators, such as unusual traffic patterns, unauthorized access attempts, and malware detections, enabling rapid and consistent incident identification. By standardizing the identification process, this template enhances the efficiency of security teams in mitigating risks and preventing widespread network damage.
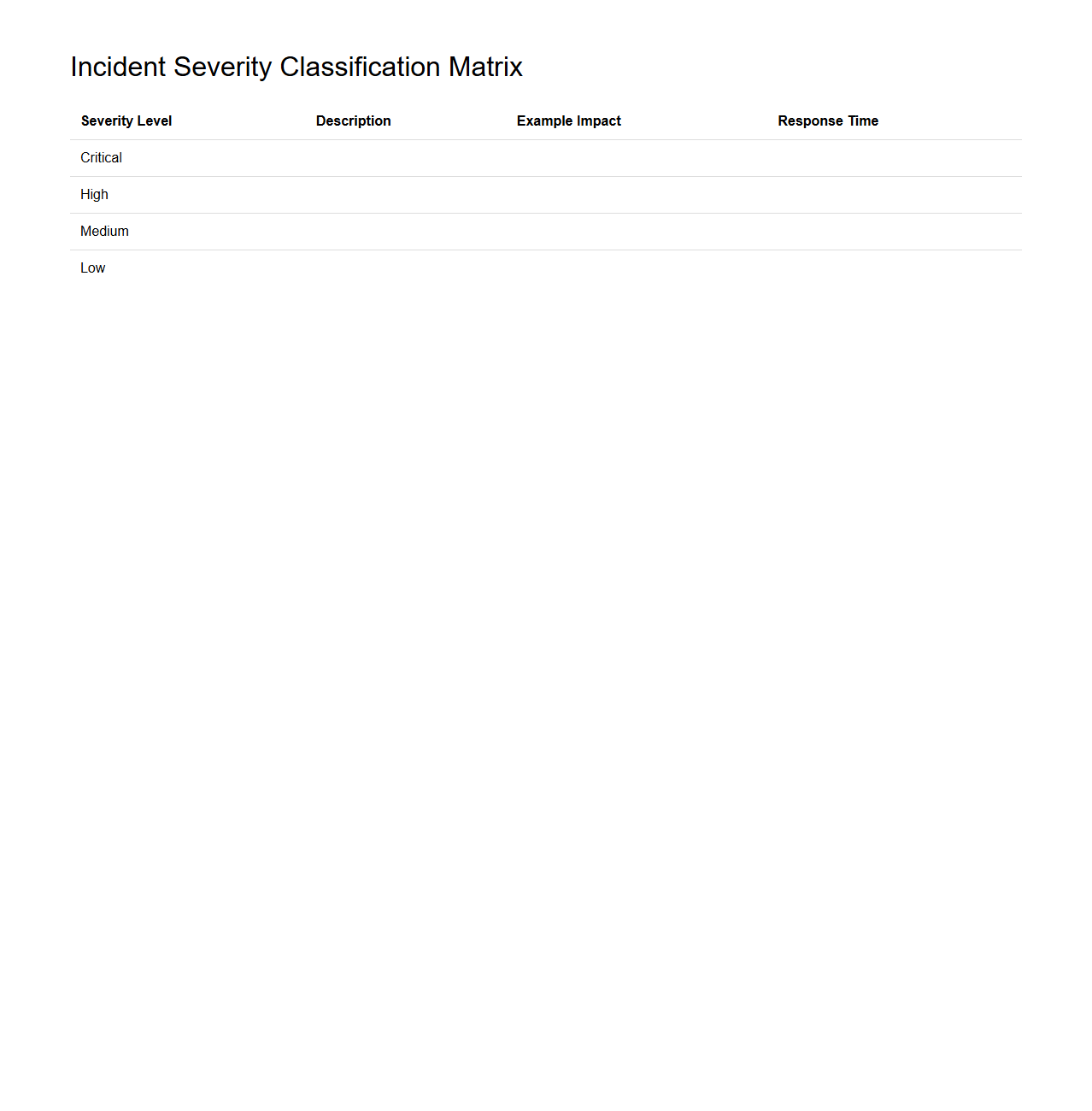
Incident Severity Classification Matrix
The
Incident Severity Classification Matrix document categorizes incidents based on their impact and urgency to ensure consistent prioritization and response across an organization. It defines specific criteria for different severity levels, enabling clear communication among teams and helping allocate resources effectively. This matrix is essential for minimizing downtime and enhancing overall incident management efficiency.
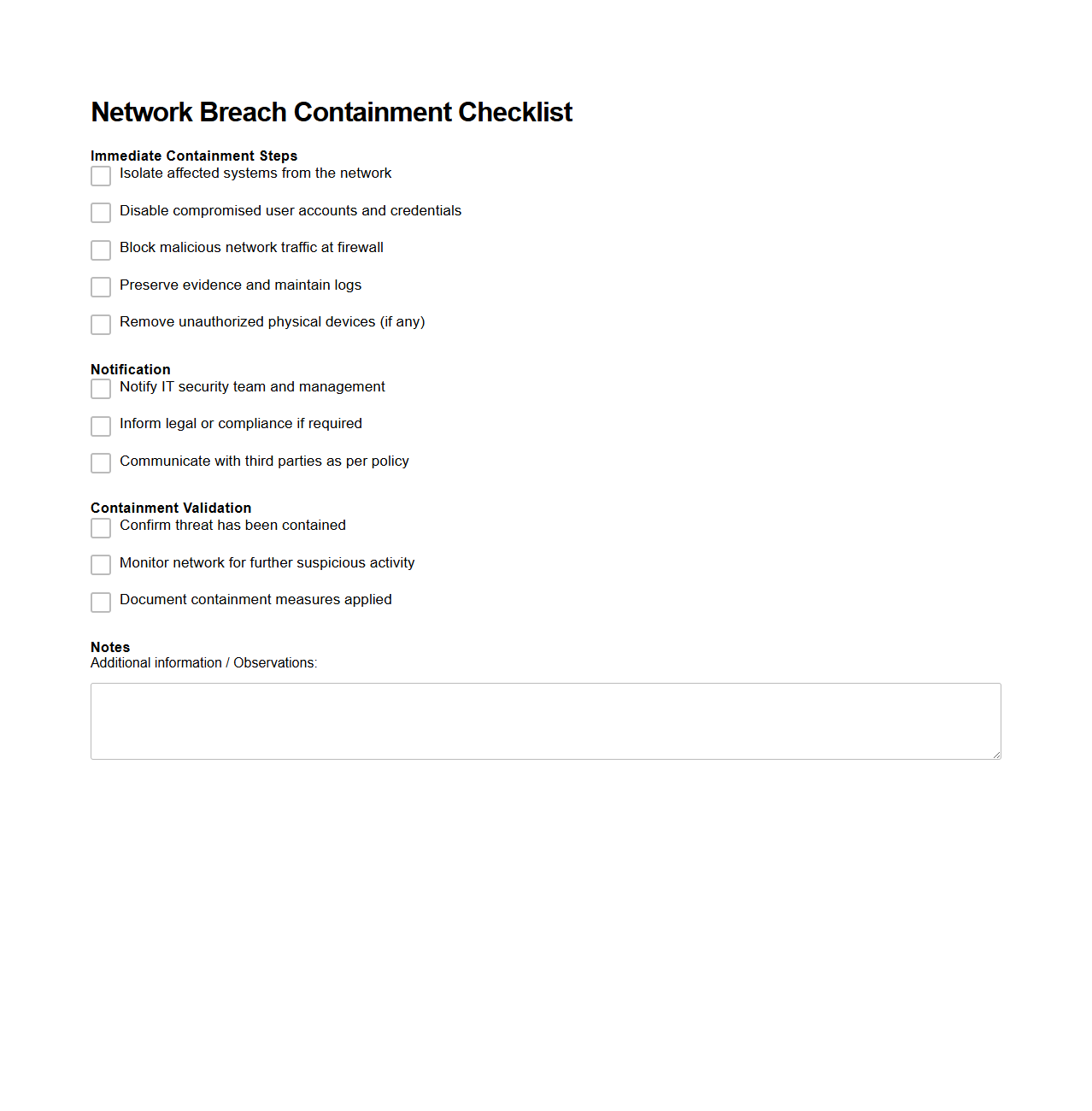
Network Breach Containment Checklist
The
Network Breach Containment Checklist document provides a detailed guide for IT and security teams to swiftly identify, isolate, and mitigate the impact of a network breach. It outlines specific steps such as disconnecting affected devices, preserving forensic evidence, and notifying stakeholders to minimize data loss and operational disruption. This checklist ensures a systematic response aligned with industry best practices to enhance overall cybersecurity resilience.
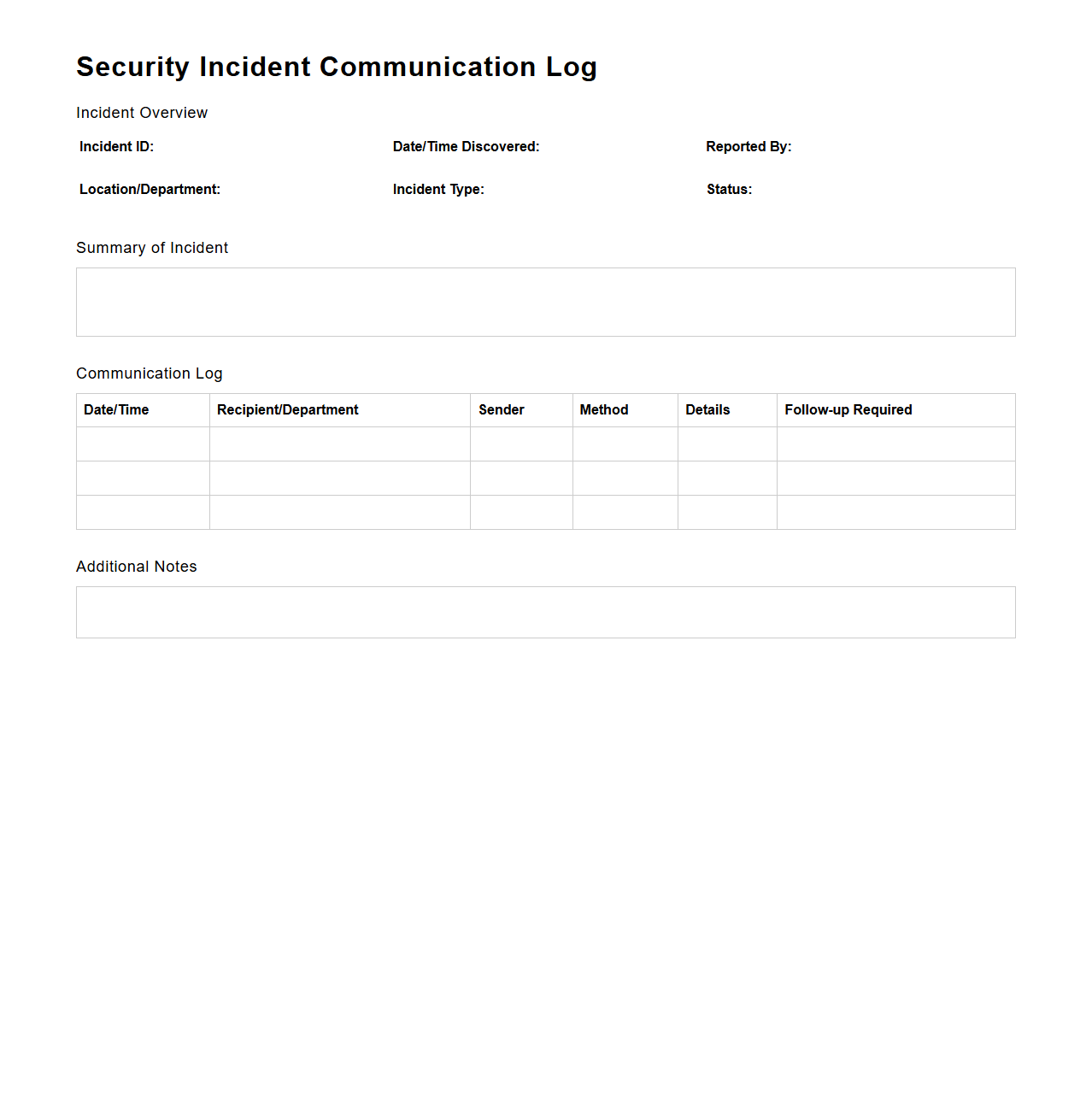
Security Incident Communication Log
A
Security Incident Communication Log document records all communications related to a security incident, including timestamps, participants, and the content of messages exchanged. This log serves as a critical tool for tracking incident response activities, maintaining transparency, and providing an audit trail for post-incident analysis and compliance reporting. Accurate documentation within this log helps organizations improve their security posture by identifying communication gaps and facilitating effective coordination during cybersecurity events.
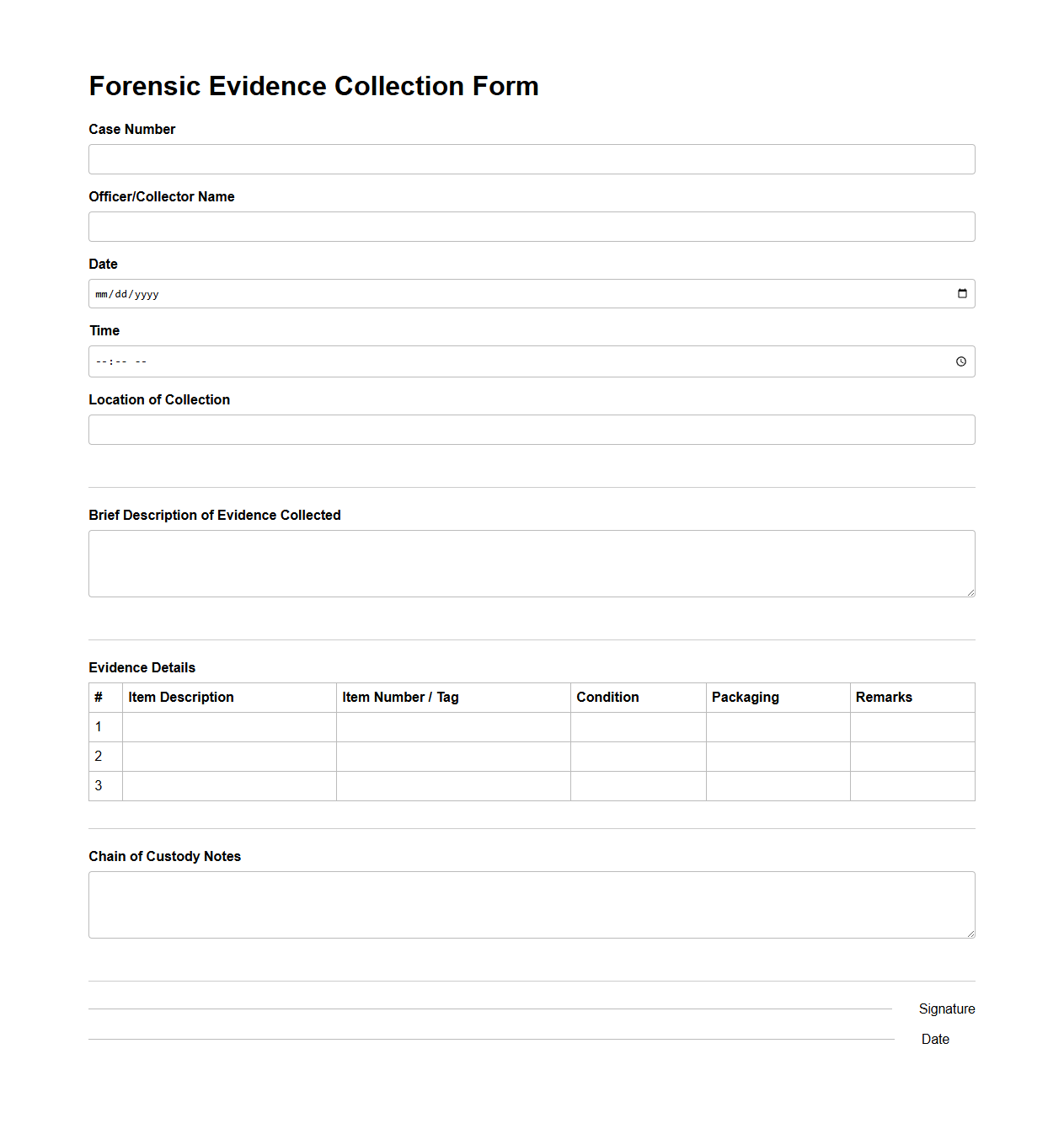
Forensic Evidence Collection Form
The
Forensic Evidence Collection Form is a critical document used to systematically record and track physical evidence gathered from a crime scene. It ensures proper chain of custody by detailing the type, location, and condition of each piece of evidence, along with the collector's information and timestamps. Accurate completion of this form is essential for maintaining the integrity of evidence during investigations and legal proceedings.
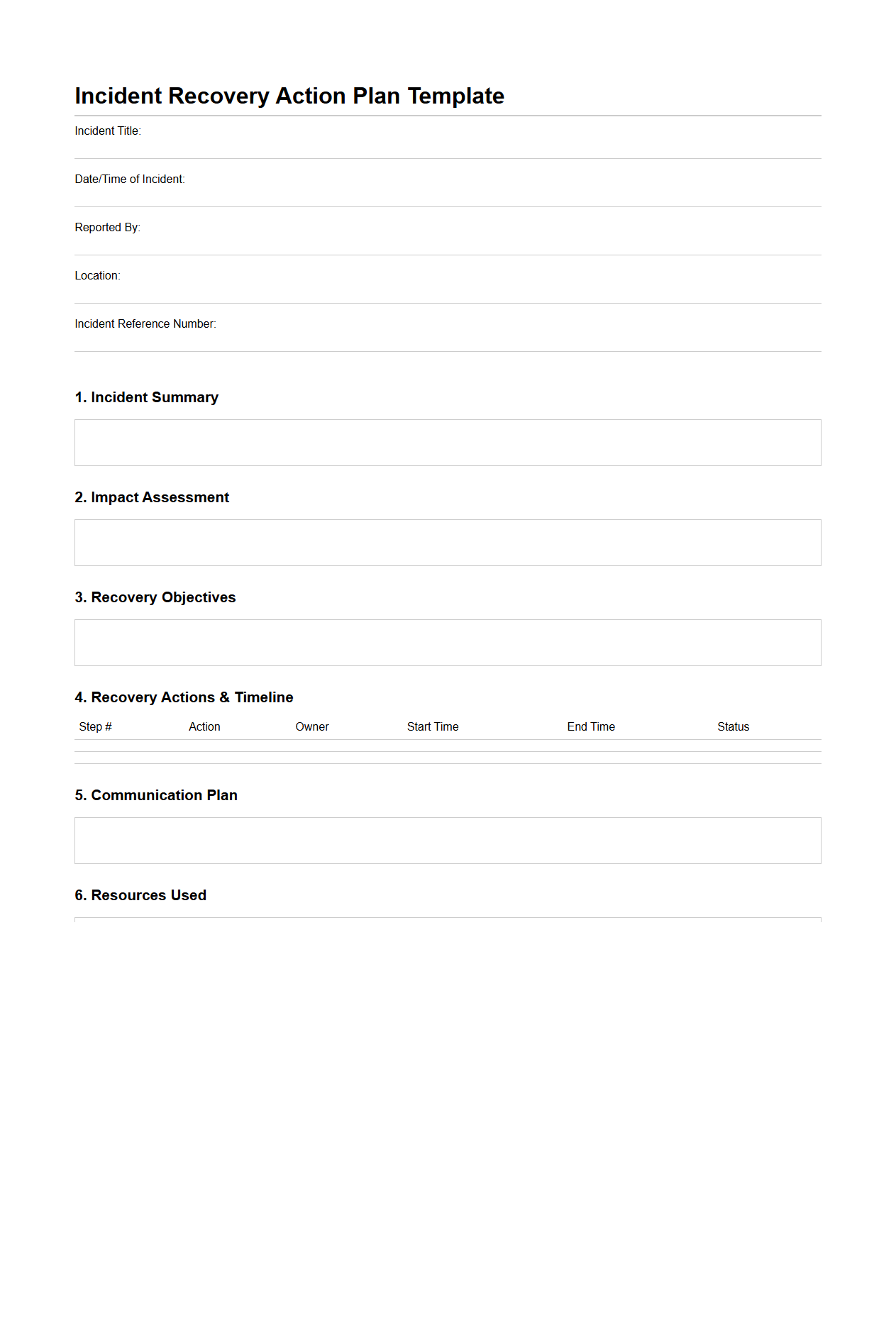
Incident Recovery Action Plan Template
An
Incident Recovery Action Plan Template document provides a structured framework for organizations to effectively manage and recover from unexpected incidents or disruptions. It outlines specific steps, responsibilities, and timelines to restore normal operations quickly while minimizing impact. This template ensures consistency, accountability, and swift response during incident resolution.
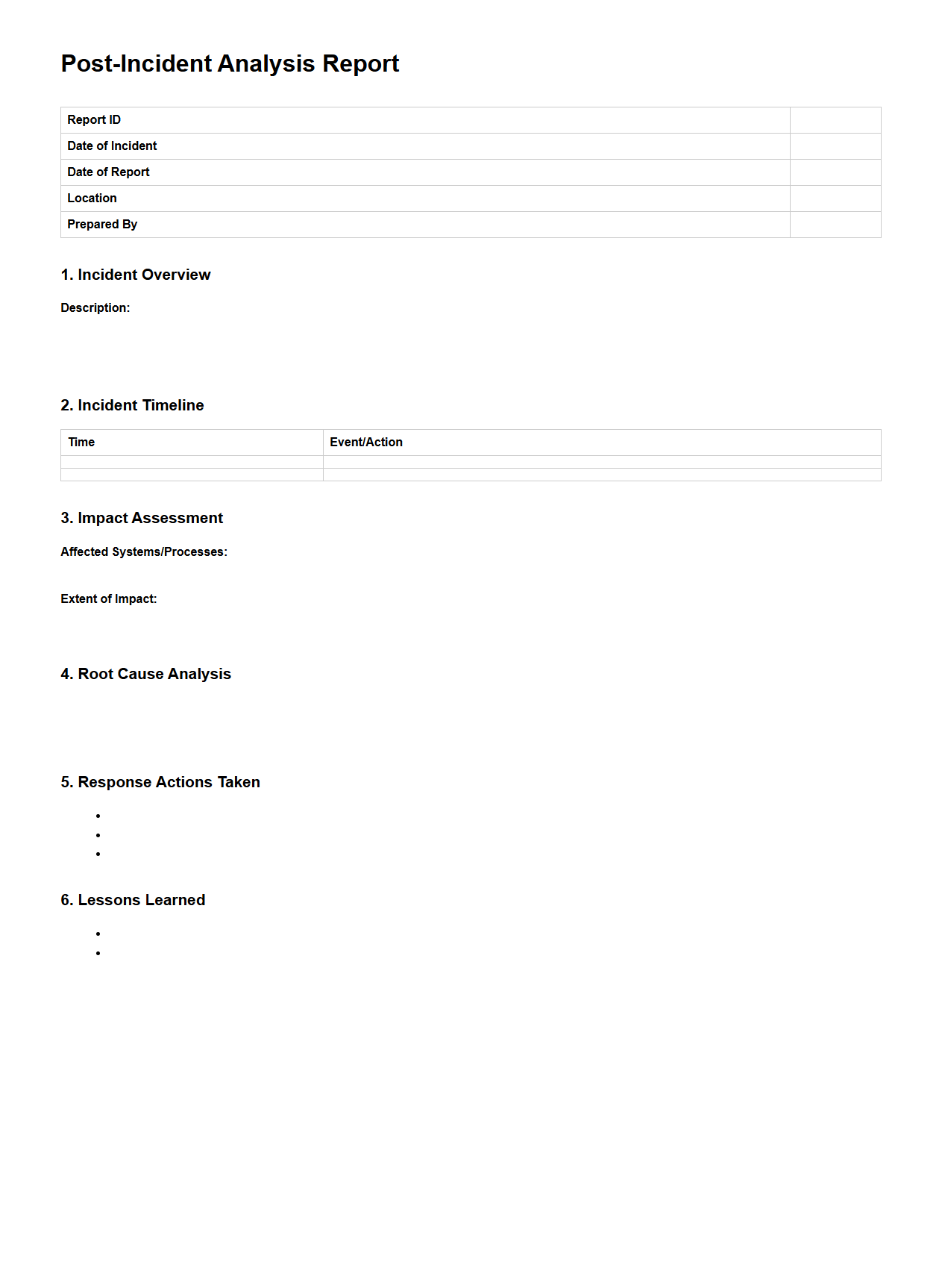
Post-Incident Analysis Report Sample
A
Post-Incident Analysis Report Sample document provides a structured template outlining the investigation and evaluation of security breaches, system failures, or operational incidents. It includes sections such as incident description, root cause analysis, impact assessment, and recommended corrective actions to prevent recurrence. This report is essential for improving incident response strategies and ensuring organizational resilience.
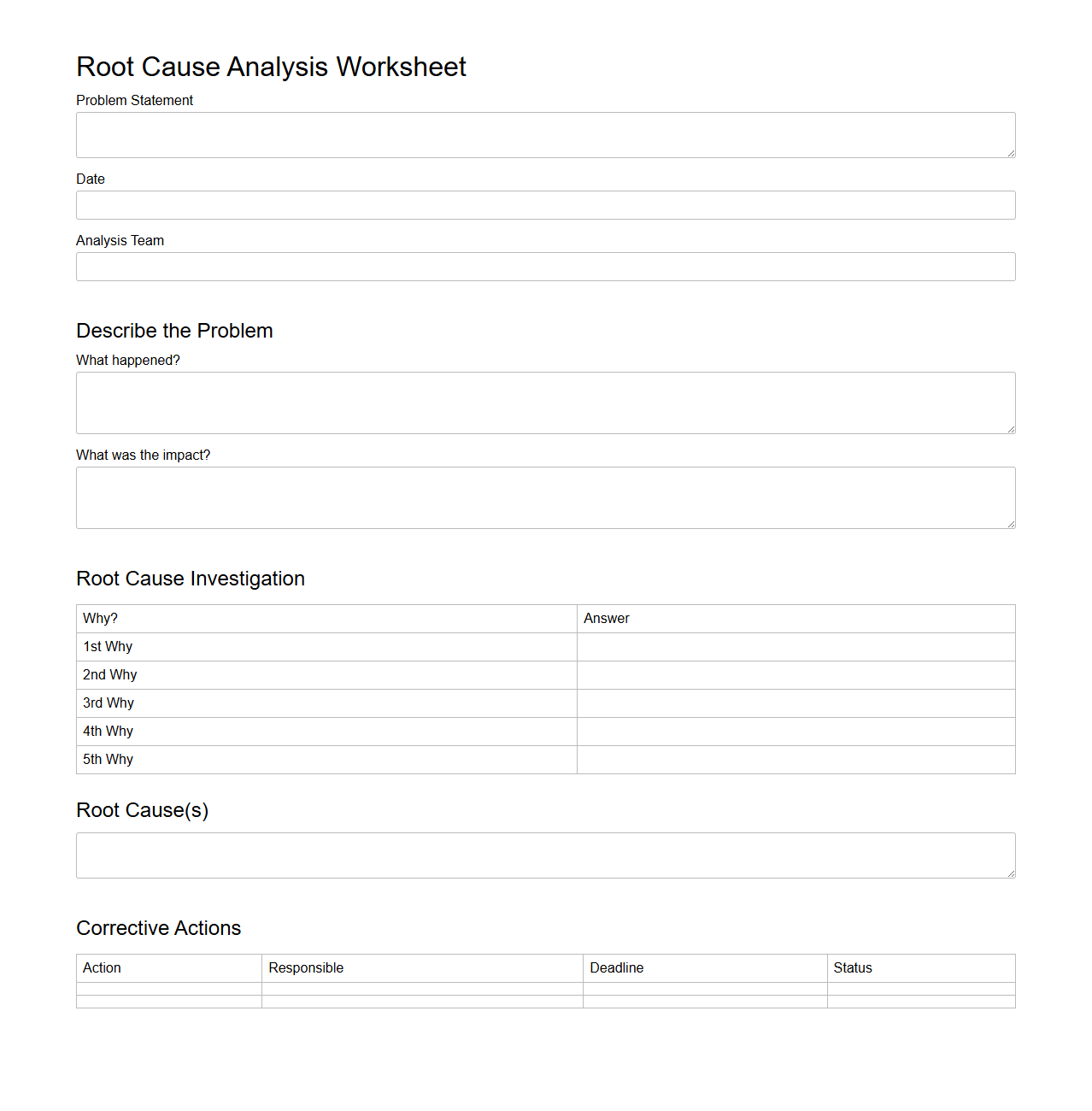
Root Cause Analysis Worksheet
A
Root Cause Analysis Worksheet document is a structured tool used to identify the primary cause of a problem or defect in processes, systems, or products. It helps teams systematically collect data, analyze contributing factors, and develop corrective actions to prevent recurrence. This worksheet enhances problem-solving efficiency and supports continuous improvement within organizations.
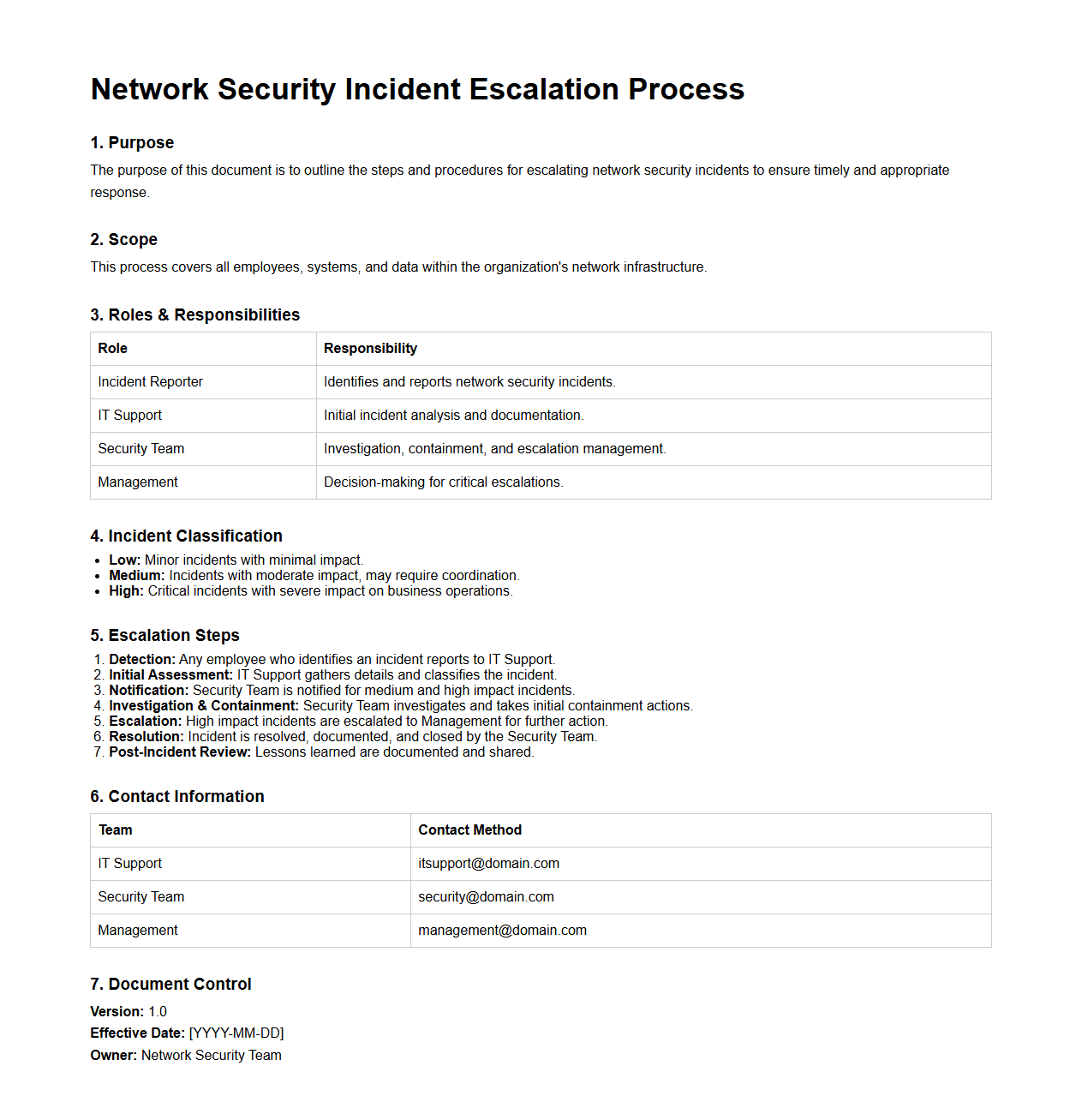
Network Security Incident Escalation Process
The
Network Security Incident Escalation Process document outlines the systematic approach for identifying, assessing, and escalating network security incidents to appropriate response teams. It defines roles, responsibilities, and communication protocols to ensure timely resolution and minimize impact on organizational assets. This document is essential for maintaining network integrity and complying with cybersecurity policies.
Incident Response Team Contact List
The
Incident Response Team Contact List document contains essential contact information for key personnel responsible for managing and mitigating cybersecurity incidents. It ensures rapid communication channels are established during security breaches or emergencies, minimizing response time and potential damage. Maintaining an up-to-date contact list is critical for effective coordination and incident resolution.
What are the specific escalation procedures outlined in the Incident Response Plan for network intrusions?
The Incident Response Plan details escalation procedures that initiate immediate reporting to the Security Operations Center upon detection of network intrusions. It mandates escalation to senior cybersecurity analysts and management if the intrusion severity exceeds predefined thresholds. These procedures ensure timely involvement of key personnel to mitigate damages effectively.
How does the document address containment strategies for ransomware attacks on critical network segments?
The Incident Response Plan emphasizes rapid isolation of affected systems to prevent ransomware propagation across critical network segments. It includes steps for deploying network segmentation and access restrictions specifically tailored for ransomware containment. The strategy prioritizes minimizing operational impact while securing sensitive data from further compromise.
Which communication templates are included for notifying stakeholders during a network security incident?
The plan provides standardized communication templates designed to notify stakeholders promptly and clearly during network security incidents. Templates cover initial incident alerts, status updates, and post-incident summaries to ensure consistent and transparent communication. These documents facilitate coordinated response efforts among internal teams and external partners.
What predefined roles and responsibilities are assigned for network forensics within the Incident Response Plan?
The Incident Response Plan assigns dedicated roles such as forensic analysts responsible for evidence collection, preservation, and analysis after network incidents. It outlines clear responsibilities including chain of custody management and collaboration with legal teams for compliance. These roles ensure forensic integrity and support effective incident investigation.
How frequently does the document require revision and testing of the network incident response procedures?
The document mandates a minimum annual review and testing cycle to keep the network incident response procedures current with evolving threats and technologies. Regular tabletop exercises and simulations are scheduled to validate the effectiveness of response strategies. This practice ensures preparedness and continuous improvement in incident handling.
More Technology Templates