A Access Control Policy Document Sample for Remote Work Environments outlines the rules and protocols to safeguard sensitive information while employees work outside the office. It defines user authentication methods, device security requirements, and access permissions to ensure secure remote connectivity. This policy is essential for minimizing security risks and maintaining organizational data integrity.
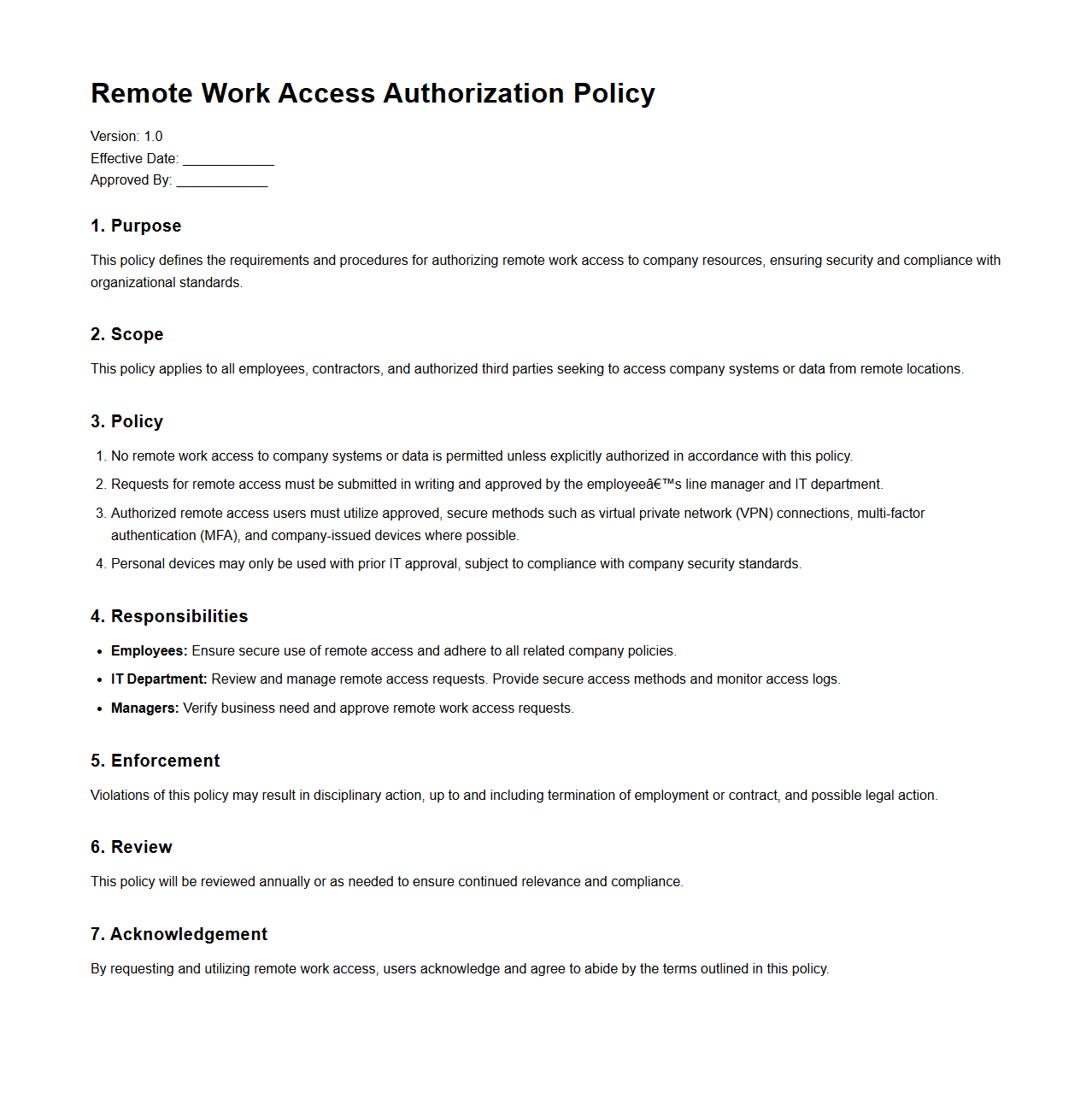
Remote Work Access Authorization Policy
A
Remote Work Access Authorization Policy document outlines the guidelines and security measures for granting employees permission to access company systems and data from remote locations. It defines roles, authentication methods, and acceptable use protocols to ensure secure and controlled remote connectivity. This policy helps mitigate risks associated with unauthorized access, data breaches, and compliance violations.
User Authentication policy for Remote Employees
The
User Authentication Policy for Remote Employees document establishes the standards and protocols to verify the identity of remote users accessing company systems and data. It outlines the multi-factor authentication methods, password requirements, and session management practices designed to protect against unauthorized access and cybersecurity threats. This policy ensures compliance with industry regulations and safeguards sensitive information in remote work environments.
VPN Usage Guidelines for Offsite Access
The
VPN Usage Guidelines for Offsite Access document outlines the protocols and best practices employees must follow to securely connect to the company's network remotely. It details authorized VPN configurations, access restrictions, and data protection measures to prevent unauthorized access and ensure compliance with cybersecurity policies. The guidelines help maintain network integrity while enabling efficient and safe remote work.
Remote Desktop Protocol (RDP) Security Policy
The
Remote Desktop Protocol (RDP) Security Policy document outlines the standards and procedures to safeguard remote desktop connections within an organization. It specifies authentication methods, encryption requirements, access controls, and session management to protect against unauthorized access and data breaches. This policy ensures compliance with security best practices and regulatory requirements for remote access.
Strong Password Requirements for Remote Work
The
Strong Password Requirements for Remote Work document outlines essential guidelines to ensure secure access to company systems by remote employees. It specifies criteria such as minimum length, complexity including uppercase, lowercase, numbers, and special characters, and mandatory periodic password changes. Adhering to these requirements significantly reduces the risk of unauthorized access and protects sensitive organizational data from cyber threats.
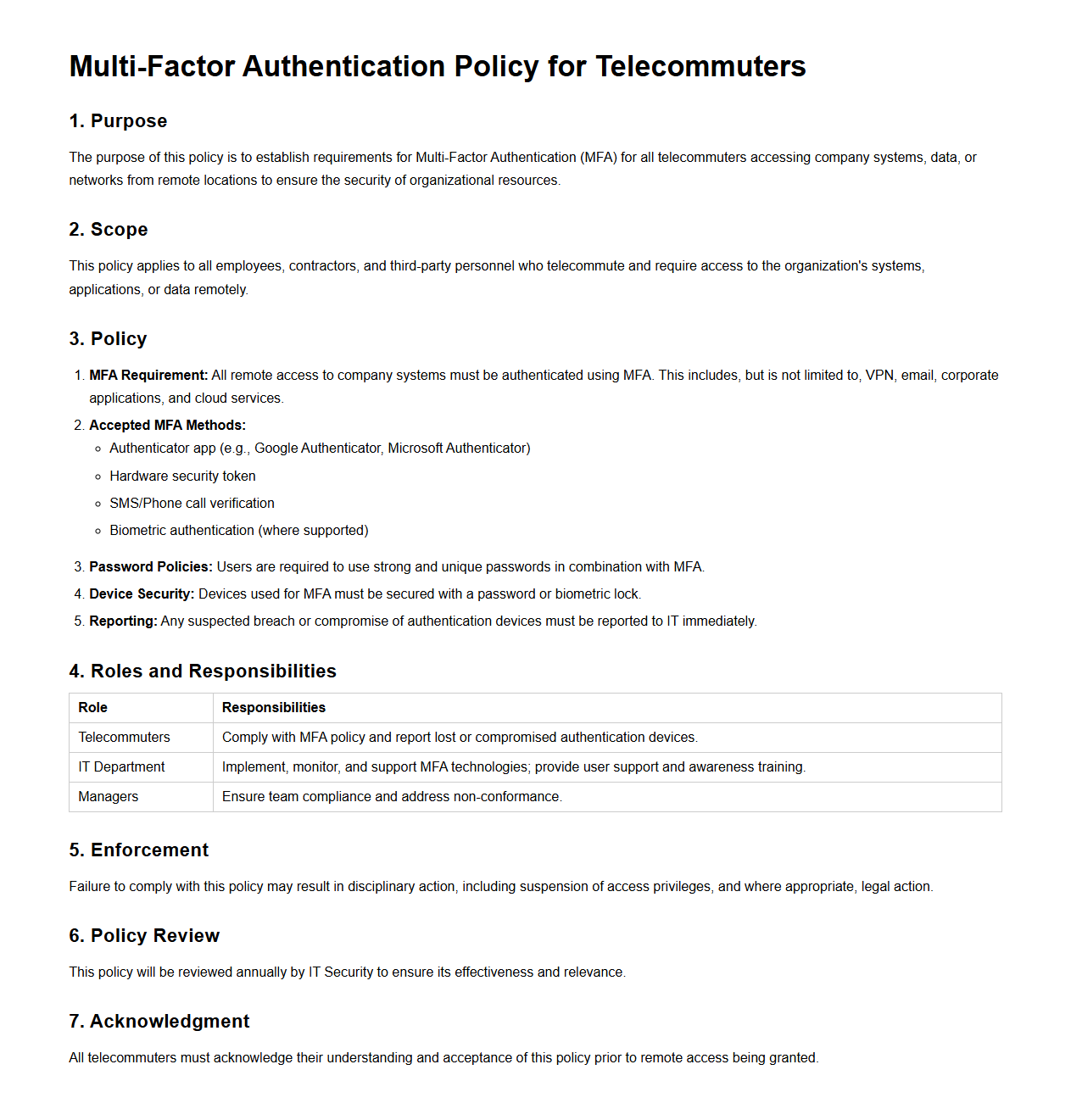
Multi-Factor Authentication Policy for Telecommuters
A
Multi-Factor Authentication Policy for Telecommuters document outlines the security protocols requiring remote employees to use multiple verification methods before accessing corporate systems. It ensures enhanced protection against unauthorized access by combining something the user knows, has, or is, such as passwords, security tokens, or biometric data. This policy is critical for safeguarding sensitive data and maintaining network integrity in telework environments.
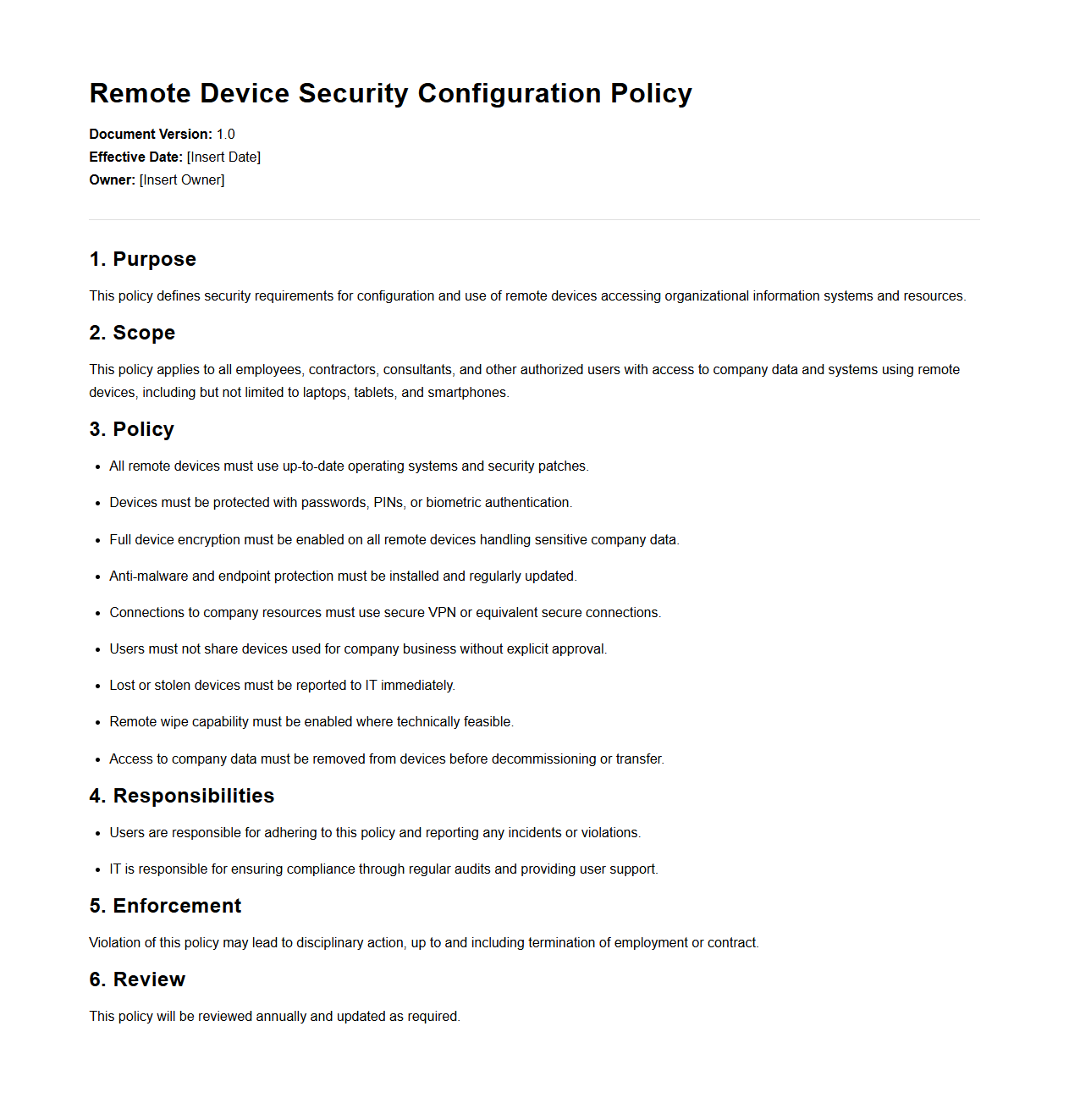
Remote Device Security Configuration Policy
A
Remote Device Security Configuration Policy document outlines the standards and procedures for securing devices that connect to an organization's network remotely. It defines requirements for encryption, authentication, access controls, and software updates to mitigate risks associated with remote access. This policy ensures consistent security measures are applied across all remote devices to protect sensitive data and maintain compliance.
Endpoint Encryption Standards for Home Offices
The
Endpoint Encryption Standards for Home Offices document outlines best practices and technical requirements for securing data on devices used in remote working environments. It provides guidelines to implement strong encryption protocols, ensuring sensitive information remains protected from unauthorized access on laptops, desktops, and mobile devices. This standard aims to enhance cybersecurity measures, mitigate data breach risks, and support compliance with organizational policies and regulatory frameworks.
Third-Party Remote Access Management Policy
The
Third-Party Remote Access Management Policy document outlines the rules and procedures for granting, monitoring, and revoking remote access privileges to external vendors or partners. It ensures secure connections, protects sensitive data, and minimizes risks associated with third-party access to organizational systems. This policy is essential for maintaining compliance with cybersecurity standards and safeguarding the network from unauthorized activities.
Incident Response Policy for Remote Access Breaches
The Incident Response Policy for Remote Access Breaches outlines a structured approach to detecting, managing, and mitigating unauthorized access incidents through remote connections. It defines roles, responsibilities, and procedures to ensure timely containment, investigation, and recovery from breaches affecting remote access systems. This policy is critical for maintaining
network security and safeguarding sensitive organizational data against cyber threats exploiting remote access vulnerabilities.
How does the Access Control Policy address authentication for remote VPN connections?
The Access Control Policy mandates multi-factor authentication (MFA) for all remote VPN connections to ensure robust security. Users must provide two or more verification factors before gaining access, reducing the risk of unauthorized entry. Additionally, periodic credential updates and strict password policies are enforced to maintain secure authentication over time.
What procedures exist for revoking remote access upon employee termination?
Upon employee termination, the policy requires immediate deactivation of all remote access credentials to prevent unauthorized use. Human Resources coordinates with the IT department to ensure a timely and complete revocation of VPN and system access. Additionally, audits are conducted to verify that no residual permissions remain active post-termination.
How are privilege escalation requests monitored for remote users?
Privilege escalation requests for remote users are subject to a stringent approval and logging process to maintain accountability. Each request must be documented, reviewed by a supervisor, and granted on a least-privilege basis. Continuous monitoring tools track any changes, with alerts generated for suspicious or excessive privilege escalations.
What encryption standards are mandated for remote document transmission?
The Access Control Policy enforces the use of Advanced Encryption Standard (AES) with 256-bit keys for all remote document transmissions. This ensures data confidentiality and protection against interception during transit. Compliance with industry-recognized encryption protocols like TLS 1.2 or higher is also strictly required.
How is compliance with access log reviews enforced for distributed teams?
Compliance is maintained through mandatory regular audits and automated monitoring of access logs across all distributed teams. The Access Control Policy requires scheduled reviews to identify any anomalies or policy violations promptly. Enforcement is supported by centralized logging tools and reporting mechanisms tailored for remote and diverse workforce environments.
More Technology Templates