A Encryption Methodology Document Sample for Data Security outlines the specific techniques and protocols used to protect sensitive information from unauthorized access. It includes detailed descriptions of encryption algorithms, key management practices, and implementation guidelines to ensure data confidentiality and integrity. This document serves as a critical reference for organizations aiming to maintain robust cybersecurity standards.
Encryption Key Management Policy Template
An
Encryption Key Management Policy Template document outlines standardized procedures and guidelines for the secure generation, distribution, storage, rotation, and revocation of encryption keys within an organization. It ensures compliance with industry regulations and helps mitigate risks associated with unauthorized access or data breaches. By defining roles, responsibilities, and controls, the policy template supports effective cryptographic security and operational consistency across all encryption-related activities.
Data-at-Rest Encryption Architecture Overview
The
Data-at-Rest Encryption Architecture Overview document outlines the structural framework and security measures employed to protect stored data from unauthorized access. It details encryption algorithms, key management processes, and compliance requirements to ensure data integrity and confidentiality. This document serves as a critical reference for designing and implementing robust encryption solutions within an organization's data storage systems.
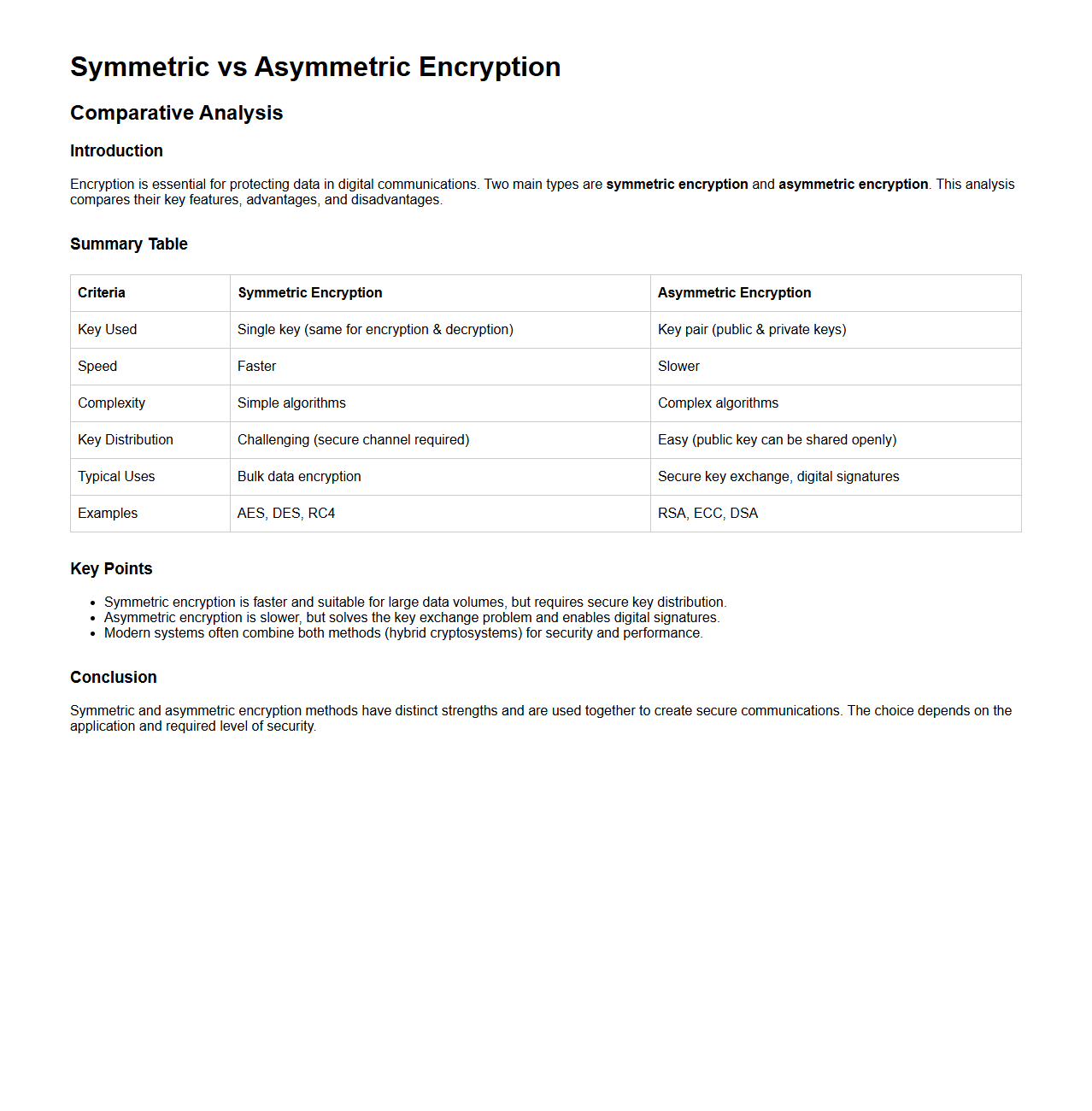
Symmetric vs Asymmetric Encryption Comparative Analysis
The
Symmetric vs Asymmetric Encryption Comparative Analysis document provides a detailed examination of both cryptographic techniques, highlighting their operational mechanisms, key management processes, and security implications. It evaluates the advantages and drawbacks of symmetric encryption, which uses a single key for both encryption and decryption, against asymmetric encryption that employs a pair of public and private keys. This analysis supports informed decision-making for selecting appropriate encryption methods based on performance, scalability, and security requirements in various applications.
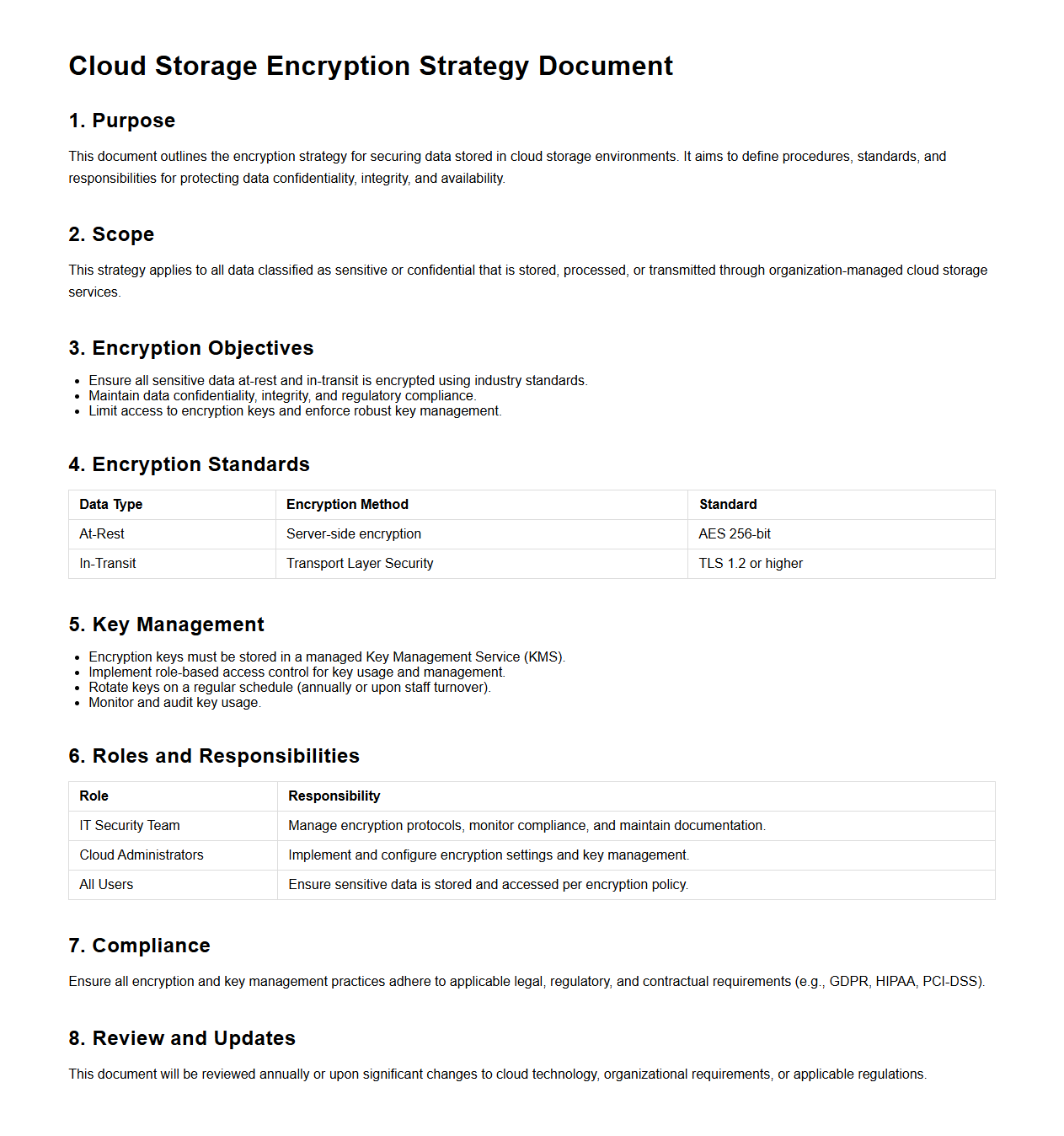
Cloud Storage Encryption Strategy Document
A
Cloud Storage Encryption Strategy Document outlines the policies and procedures to secure data stored in the cloud using encryption technologies. It defines encryption standards, key management practices, and compliance requirements to protect sensitive information from unauthorized access. This document serves as a critical guide for organizations to implement robust data protection and ensure data privacy and integrity in cloud environments.
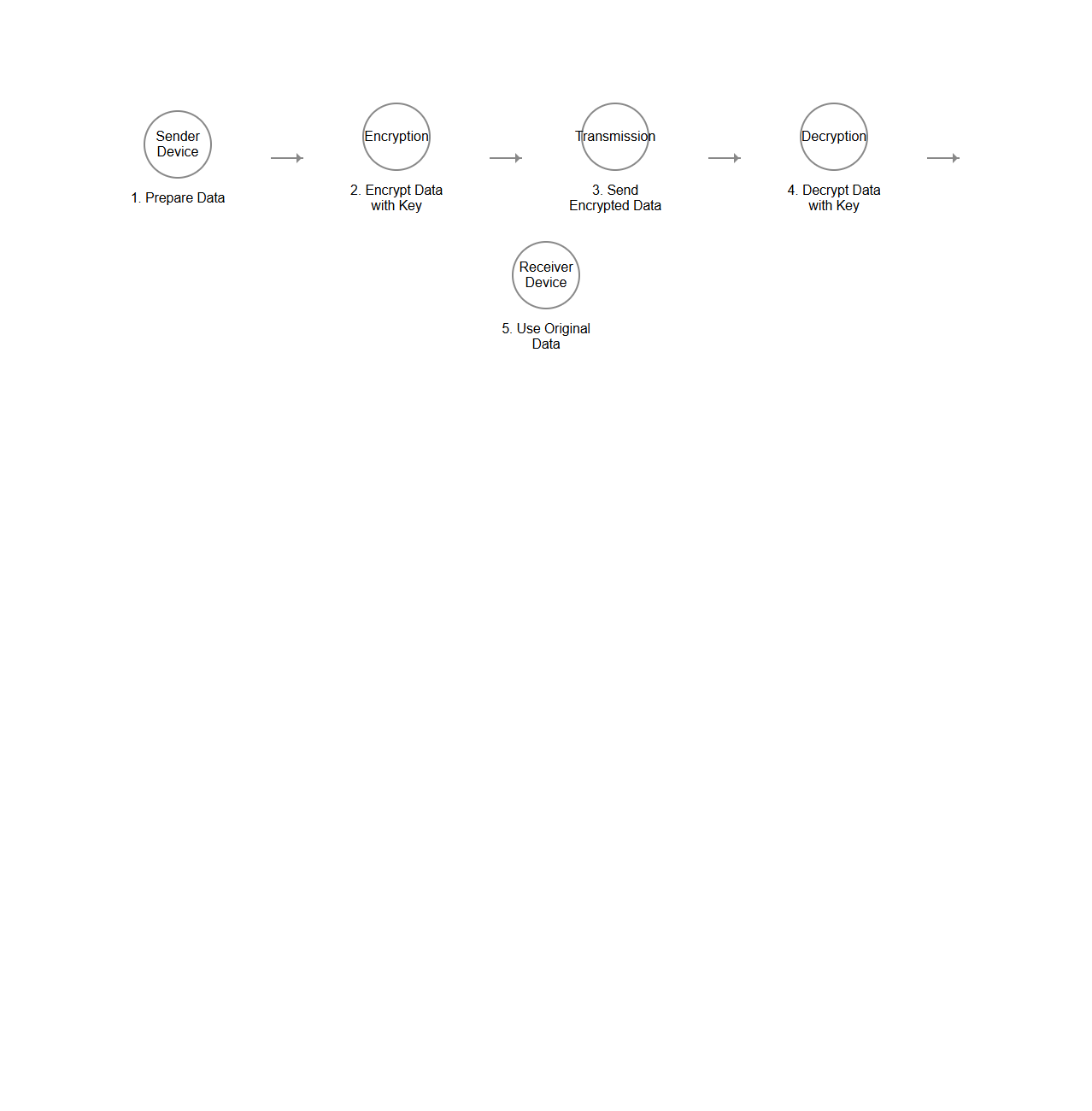
End-to-End Data Transmission Encryption Flowchart
The
End-to-End Data Transmission Encryption Flowchart document visually represents the step-by-step process ensuring secure data transfer between sender and receiver. It details encryption algorithms, key exchanges, and protocol sequences used to maintain confidentiality and integrity throughout data transmission. This flowchart serves as a crucial tool for cybersecurity professionals to analyze, implement, and verify encryption methods within communication systems.
Mobile Application Encryption Implementation Guide
The
Mobile Application Encryption Implementation Guide document provides detailed instructions on integrating robust encryption techniques within mobile apps to safeguard sensitive data against unauthorized access. It outlines best practices for selecting encryption algorithms, managing cryptographic keys, and ensuring compliance with industry standards like AES and RSA. This guide serves as a critical resource for developers aiming to enhance security protocols and protect user information effectively.
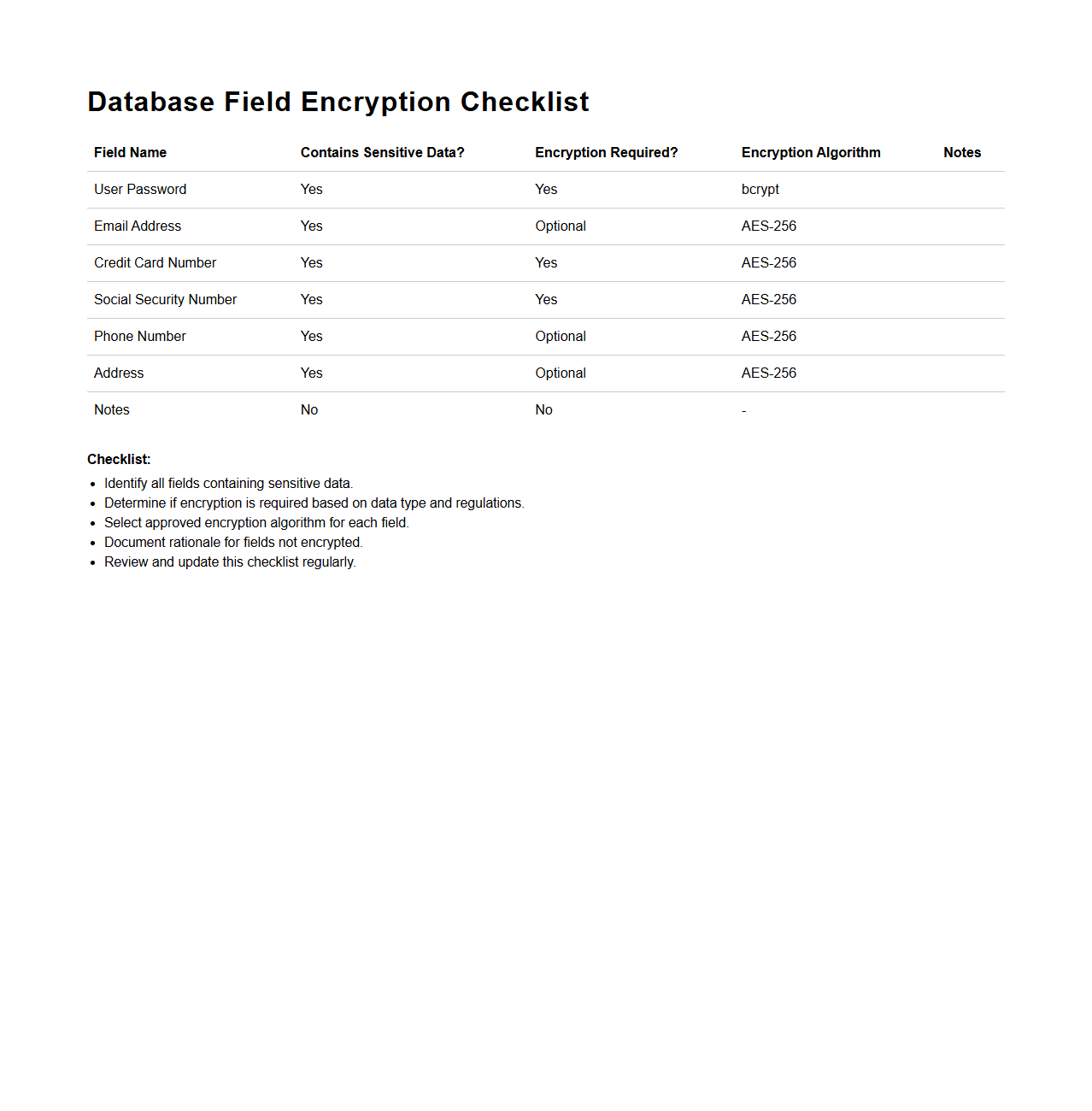
Database Field Encryption Checklist
A
Database Field Encryption Checklist document outlines essential steps and best practices for encrypting sensitive data fields within a database to ensure data security and compliance with regulations. It typically includes criteria for selecting encryption algorithms, key management protocols, and verification methods to maintain the confidentiality and integrity of protected information. This checklist serves as a practical guide for database administrators and security teams to implement robust field-level encryption strategies effectively.
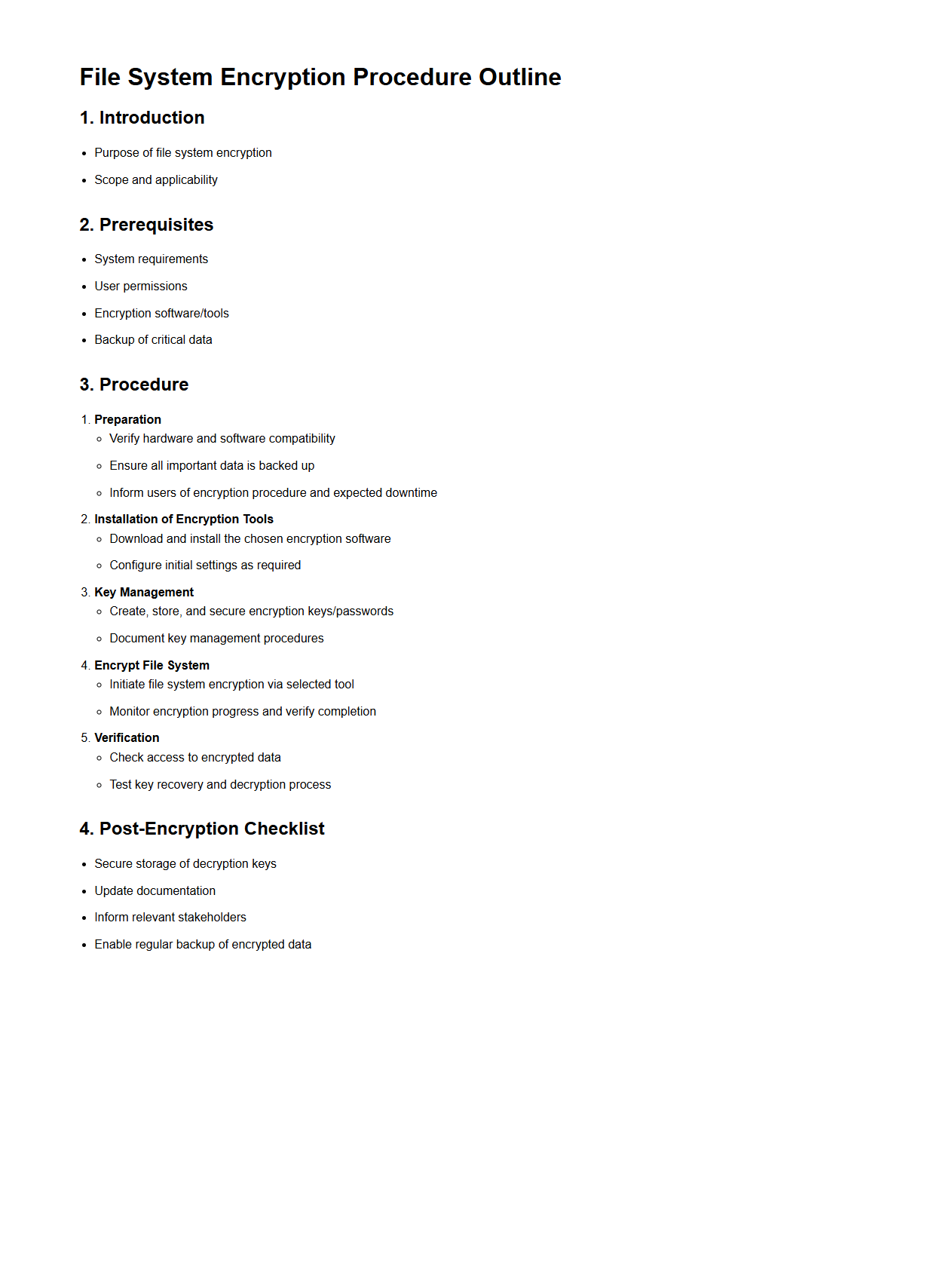
File System Encryption Procedure Outline
The
File System Encryption Procedure Outline document provides a comprehensive framework for implementing encryption protocols to safeguard data stored within file systems. It details step-by-step guidelines for selecting encryption algorithms, managing encryption keys, and ensuring compliance with security policies. This document is essential for IT professionals aiming to enhance data confidentiality and protect sensitive information from unauthorized access.
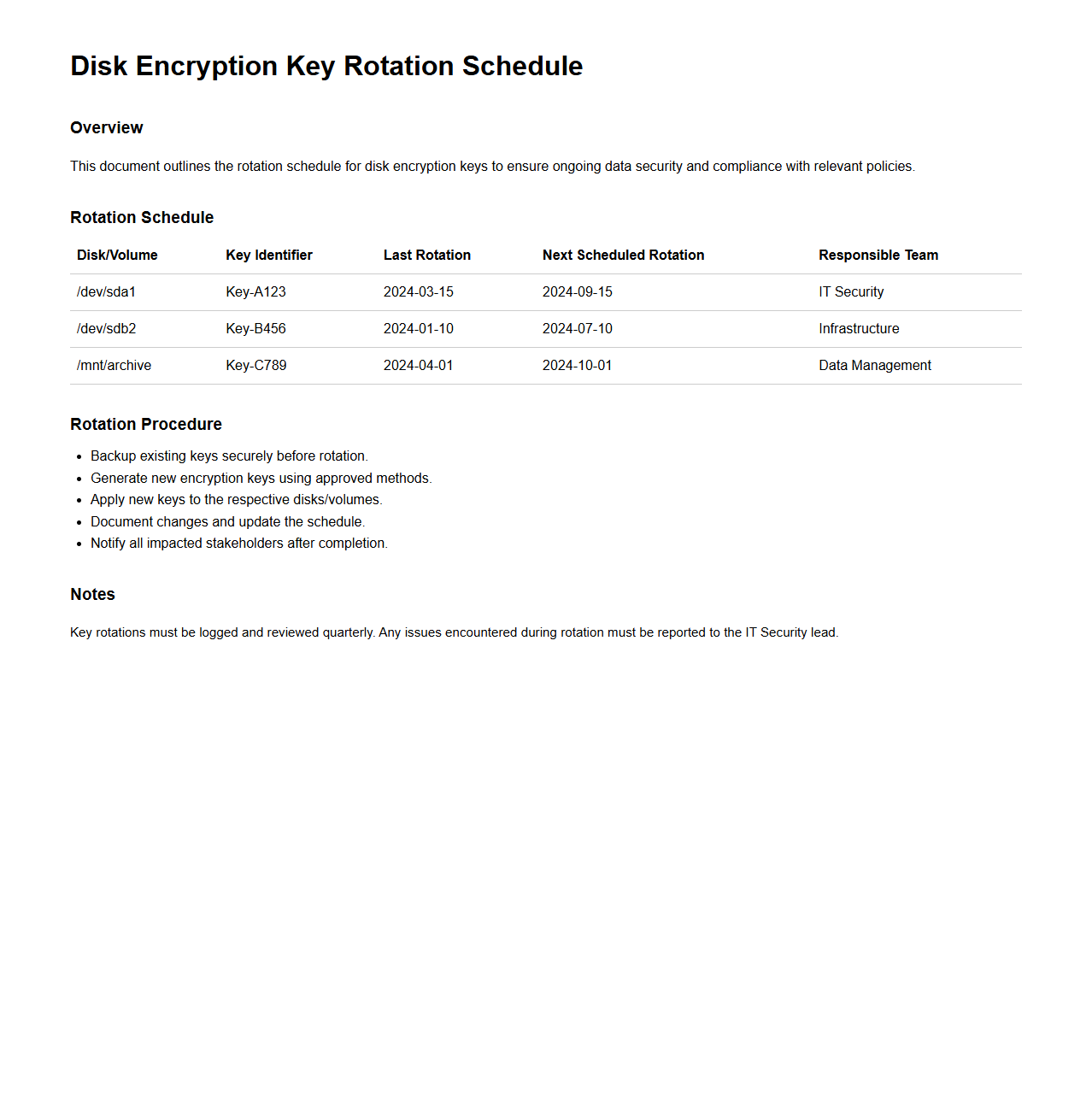
Disk Encryption Key Rotation Schedule
The
Disk Encryption Key Rotation Schedule document outlines a systematic process for regularly updating encryption keys to maintain data security and compliance standards. It specifies time intervals and protocols for generating, distributing, and retiring encryption keys used to protect sensitive disk data. Following this schedule minimizes the risk of unauthorized access due to key compromise and supports robust cybersecurity practices.
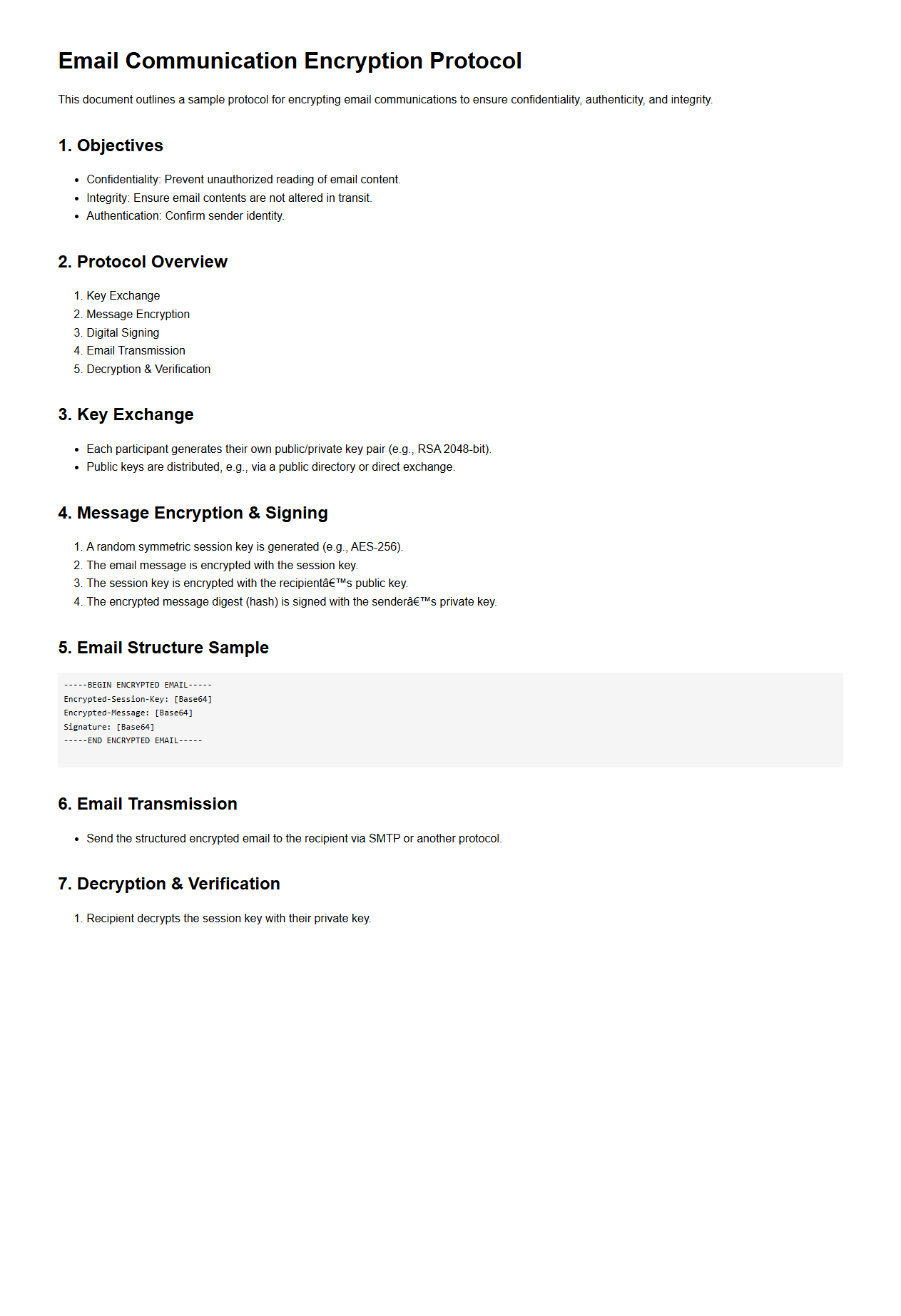
Email Communication Encryption Protocol
An
Email Communication Encryption Protocol document outlines the standards and methods used to secure email messages during transmission and storage, ensuring confidentiality and integrity. It details encryption algorithms, authentication processes, key management, and policy guidelines to protect sensitive information from unauthorized access. This protocol is essential for safeguarding communication in environments requiring strict data privacy and regulatory compliance.
Which cryptographic algorithms are detailed in the document for data-in-transit protection?
The document specifies the use of AES-256 and TLS 1.3 as the primary cryptographic algorithms for securing data-in-transit. These algorithms provide robust encryption and ensure the confidentiality and integrity of data during transmission. Emphasis is placed on the implementation of strong cipher suites to mitigate potential vulnerabilities.
How does the document address key management and rotation procedures?
Key management is highlighted as a critical process involving secure generation, storage, and disposal of cryptographic keys. The document mandates periodic key rotation to reduce the risk of key compromise, recommending rotation intervals no longer than 90 days. Additionally, automated systems are encouraged to enforce rotation and provide audit trails for compliance.
What compliance frameworks are referenced in the document's encryption policy?
The document aligns its encryption policy with major compliance frameworks including PCI-DSS, HIPAA, and GDPR. These frameworks guide the required encryption standards and data protection measures for regulated environments. Adherence ensures that the organization meets legal and industry best practices for data security.
Are there outlined protocols for handling encryption failure or breaches?
Protocols for encryption failures include immediate notification, isolation of affected systems, and forensic analysis to identify the breach source. The document mandates incident response plans that involve encryption failure detection and mitigation steps to minimize data exposure. Reporting mechanisms and communication plans are also detailed to comply with regulatory requirements.
Does the document specify requirements for end-to-end versus at-rest encryption?
The document differentiates between end-to-end encryption for data-in-transit and encryption-at-rest for stored data, specifying unique controls for each. End-to-end encryption is required to protect data between communicating parties without intermediary decryption. Meanwhile, encryption-at-rest uses strong cryptographic standards to safeguard data within storage systems and backups.
More Technology Templates