A Network Configuration Document Sample for IT Infrastructure provides a detailed template outlining the setup and management of network devices, IP address schemes, and security protocols within an organization. It serves as a critical reference to ensure consistency, streamline troubleshooting, and maintain network integrity across all IT components. This document enhances communication among IT teams by clearly defining hardware configurations, software settings, and connectivity standards.
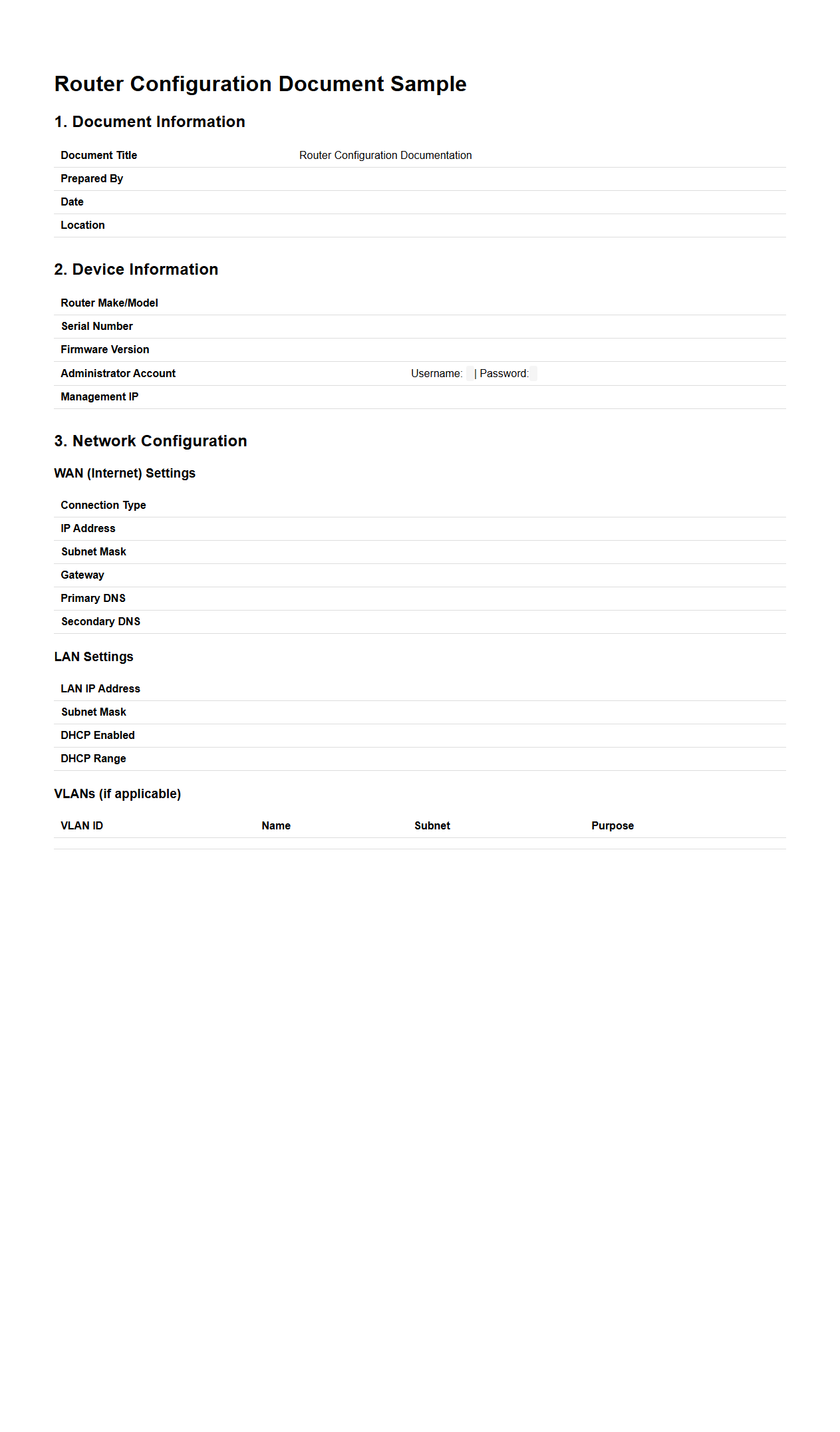
Router Configuration Document Sample for IT Setup
A
Router Configuration Document Sample for IT setup outlines the specific settings and parameters required to configure network routers effectively. It includes details such as IP addressing schemes, routing protocols, security settings, and interface configurations to ensure optimal network performance and security. This documentation serves as a vital reference for network administrators to implement, troubleshoot, and maintain consistent router setups across the organization.
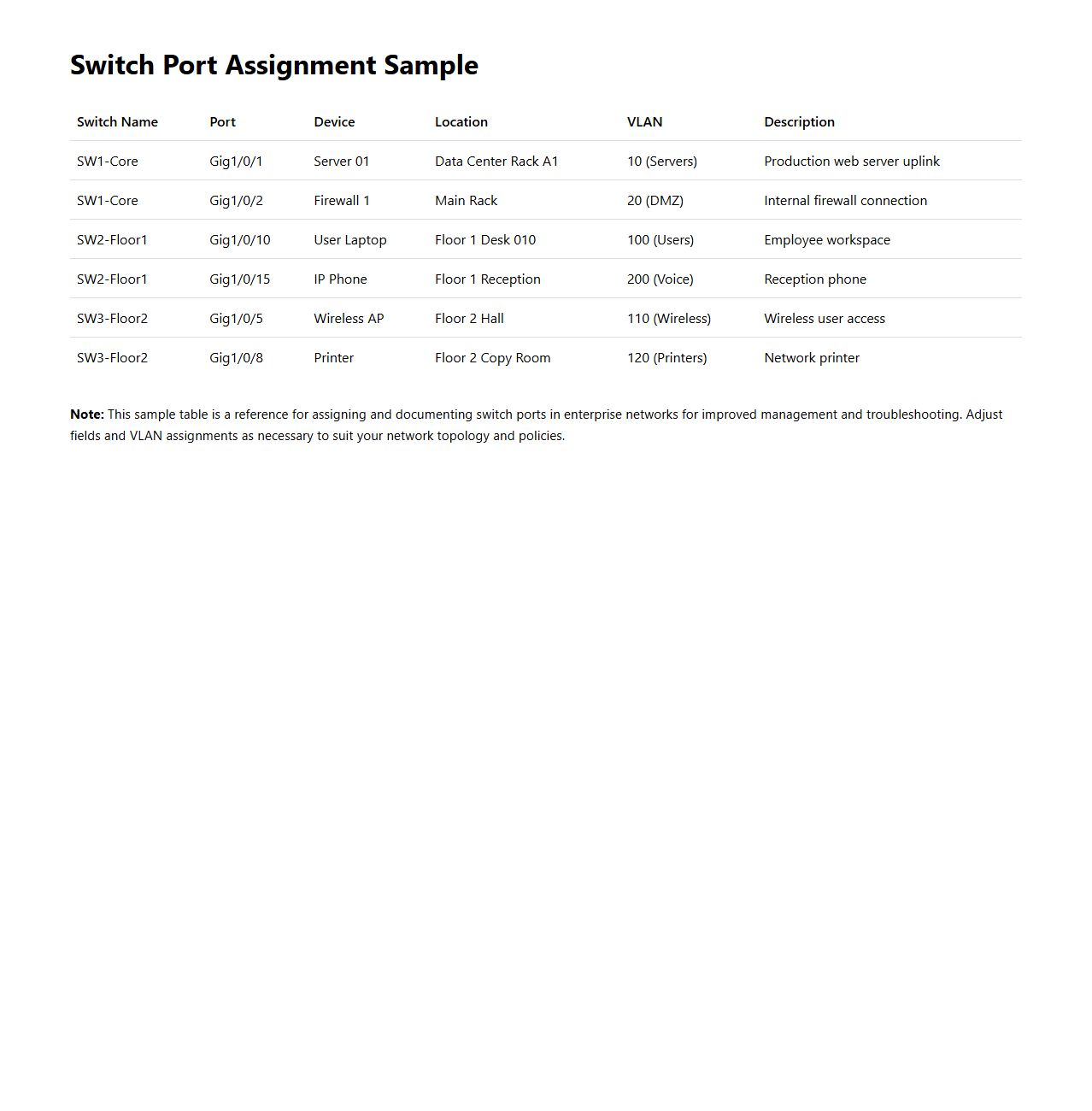
Switch Port Assignment Sample for Enterprise Networks
The
Switch Port Assignment Sample for Enterprise Networks document provides standardized guidelines for configuring switch ports to optimize network performance and security. It details best practices for assigning VLANs, managing port security settings, and ensuring proper segmentation in large enterprise environments. This resource is essential for network administrators aiming to maintain consistent and efficient switch port configurations across complex infrastructures.
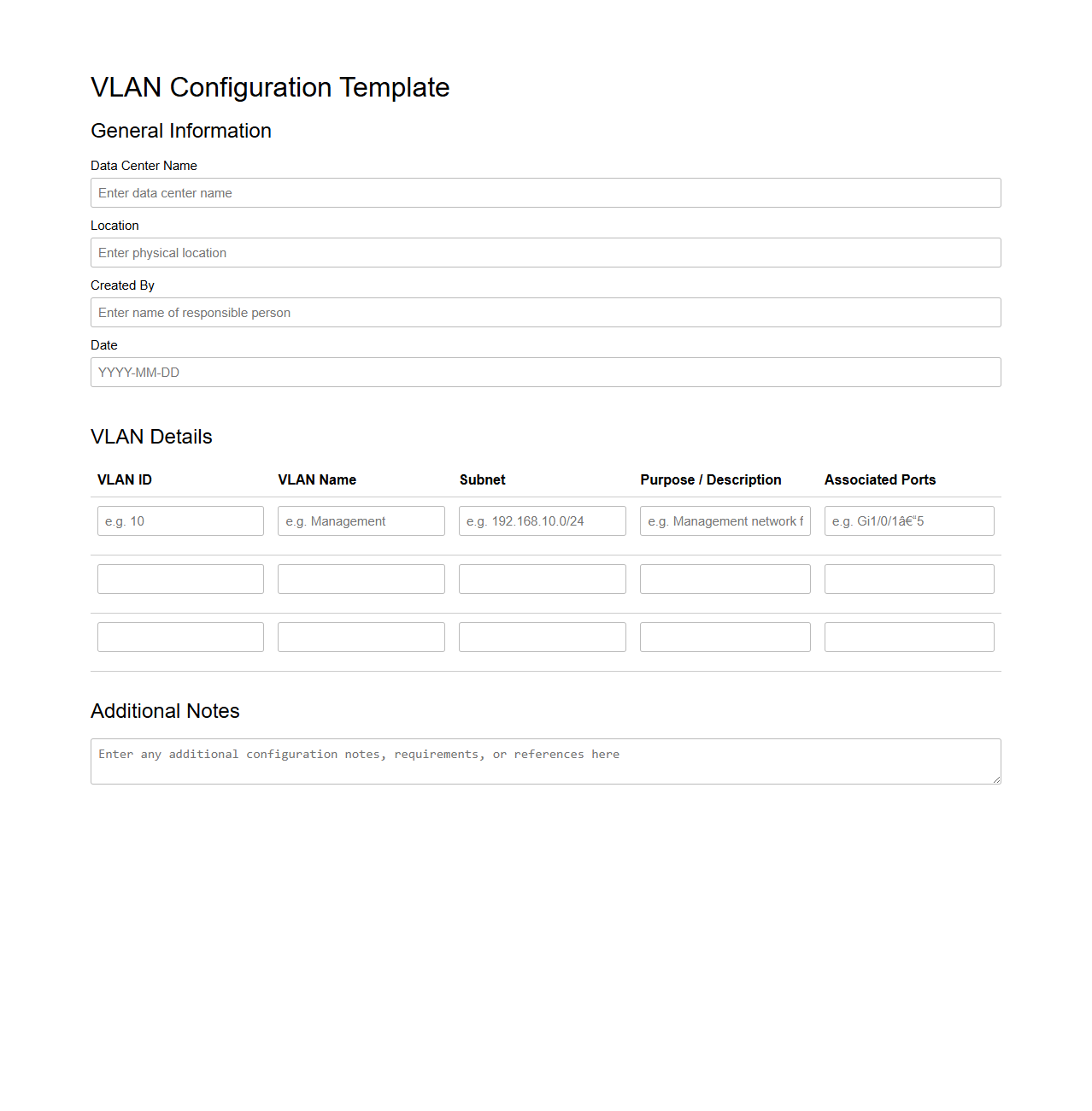
VLAN Configuration Template for Data Centers
A
VLAN Configuration Template for Data Centers document standardizes the setup of Virtual Local Area Networks, ensuring consistent segmentation, security, and management across the infrastructure. It outlines predefined VLAN IDs, IP addressing schemes, and port assignments tailored to optimize traffic flow and isolate sensitive data within the data center environment. This template serves as a critical reference for network administrators to streamline deployment, reduce configuration errors, and maintain compliance with organizational policies.
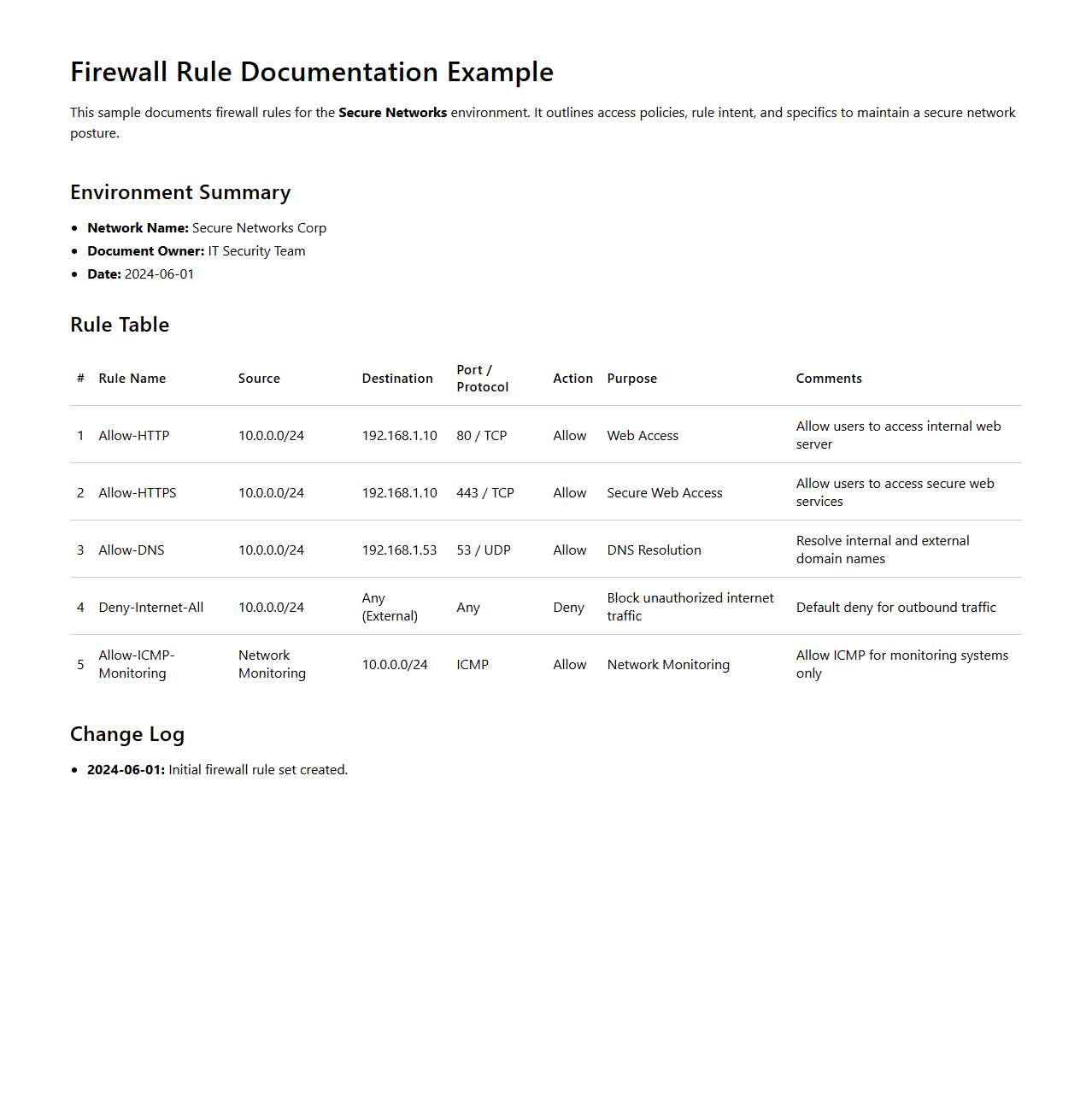
Firewall Rule Documentation Example for Secure Networks
Firewall Rule Documentation Example for Secure Networks provides a detailed guide on structuring and maintaining firewall policies to enhance network security. It includes
comprehensive templates illustrating rule specifications, such as source and destination IP addresses, protocols, and action permissions, to ensure consistency and clarity. The document serves as a reference to streamline audits, compliance checks, and facilitate efficient firewall management.
Wireless Network Setup Document Sample for Offices
A
Wireless Network Setup Document Sample for Offices provides a comprehensive guide outlining the step-by-step process to configure and deploy a secure wireless network within an office environment. It includes detailed information on hardware requirements, network topology, IP addressing schemes, security protocols like WPA3, and troubleshooting procedures. This document ensures consistent implementation standards, optimizing network performance and safeguarding sensitive office data.
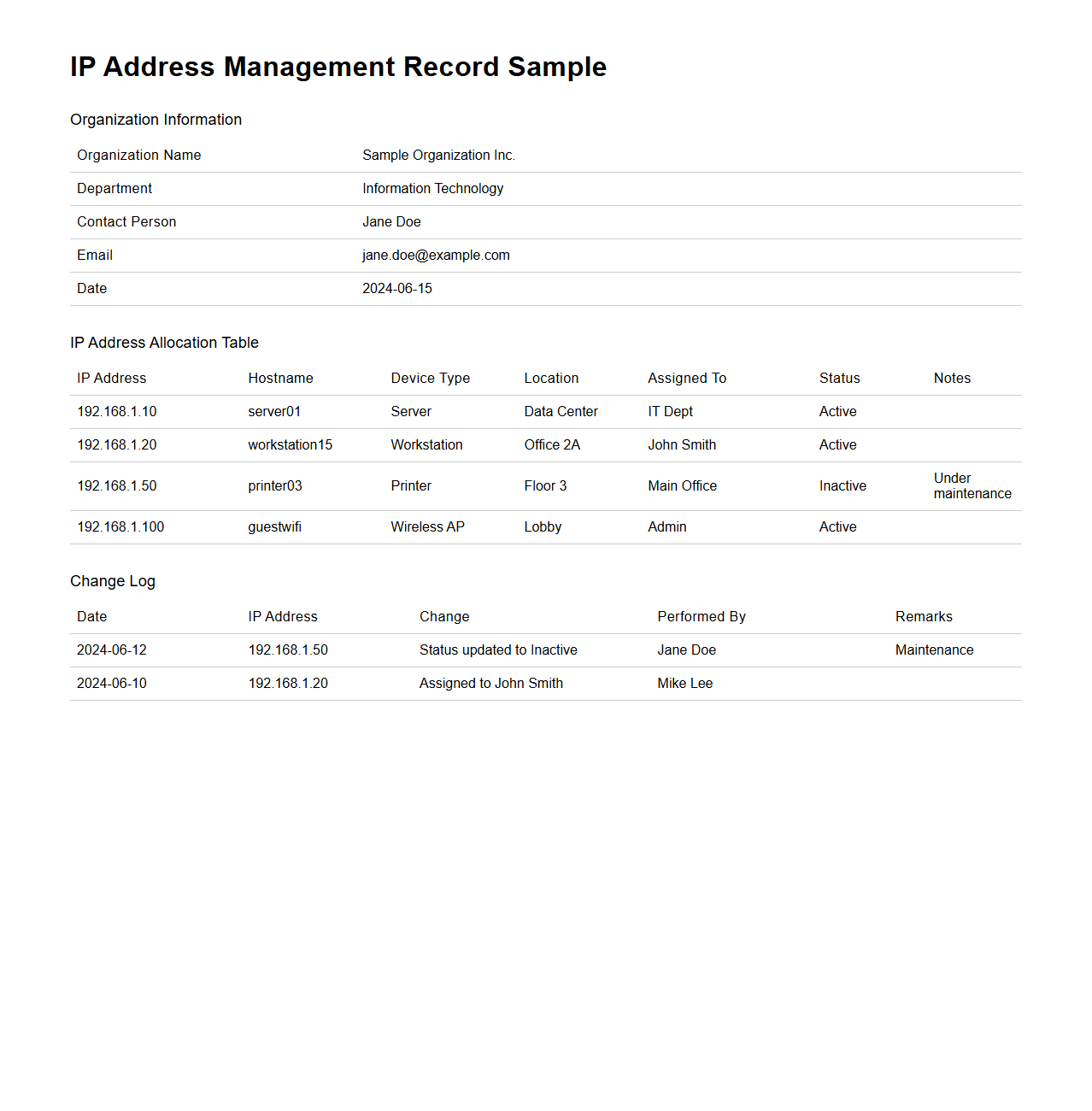
IP Address Management Record Sample for Organizations
An
IP Address Management Record Sample for organizations is a structured document that details the allocation, assignment, and tracking of IP addresses within a network. It ensures efficient utilization, prevents conflicts, and aids in network planning by maintaining clear records of subnet ranges, device IPs, and related metadata. This document is crucial for IT teams to manage both IPv4 and IPv6 addresses systematically and support seamless network operations.
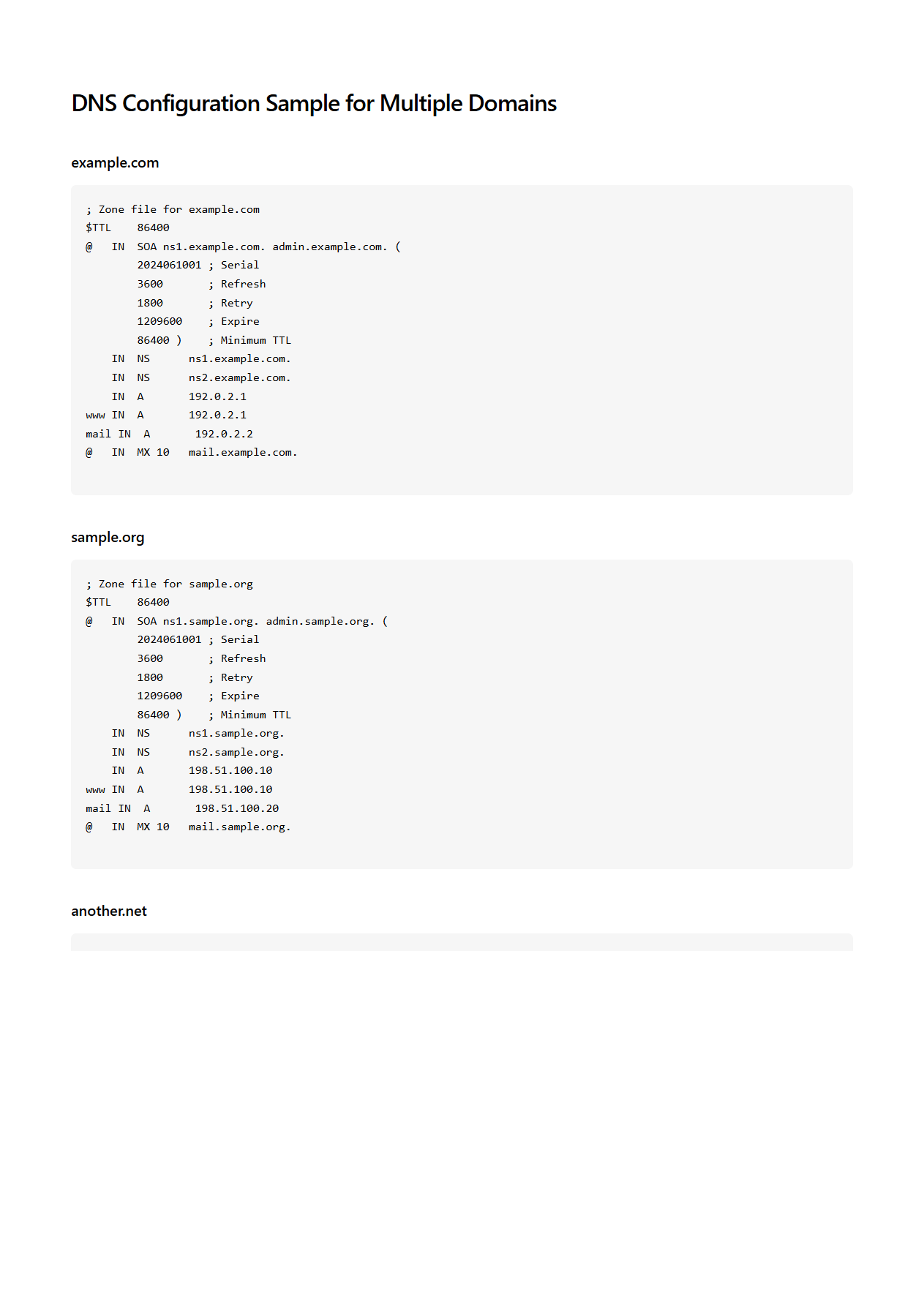
DNS Configuration Sample for Multiple Domains
The
DNS Configuration Sample for Multiple Domains document provides a detailed template for setting up Domain Name System records across various domain names efficiently. It includes best practices for managing A, MX, CNAME, and TXT records to ensure proper domain resolution and email routing. This sample configuration helps administrators streamline DNS setups, reduce errors, and maintain consistent policies for multiple domains under a single management system.
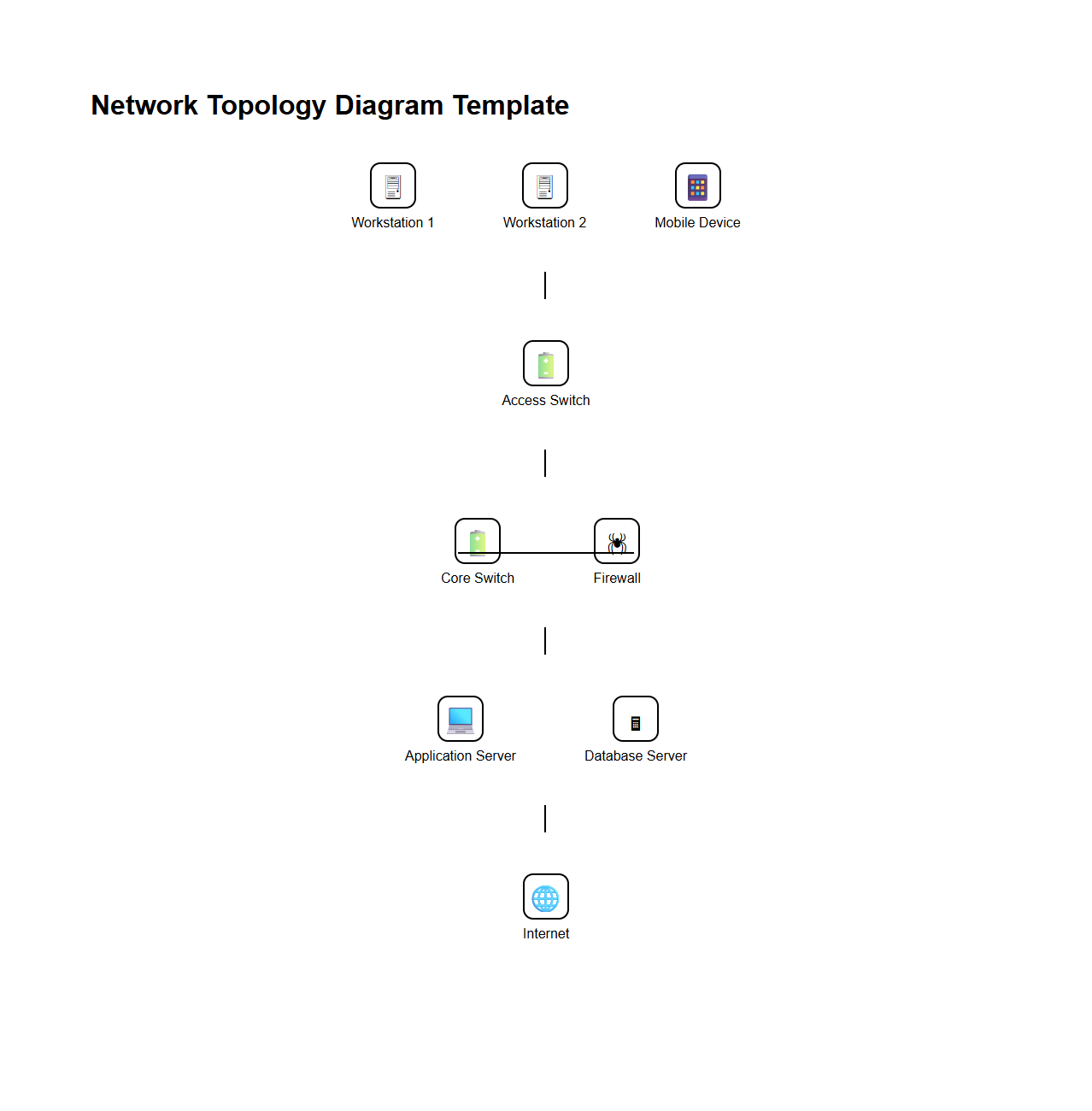
Network Topology Diagram Template for IT Teams
A
Network Topology Diagram Template for IT teams is a structured visual framework used to map out the arrangement of network devices, connections, and communication pathways within an IT infrastructure. This document facilitates efficient planning, troubleshooting, and management by clearly illustrating the physical and logical layout of routers, switches, servers, and endpoints. IT teams rely on this template to standardize network design documentation, improve collaboration, and enhance overall network performance analysis.
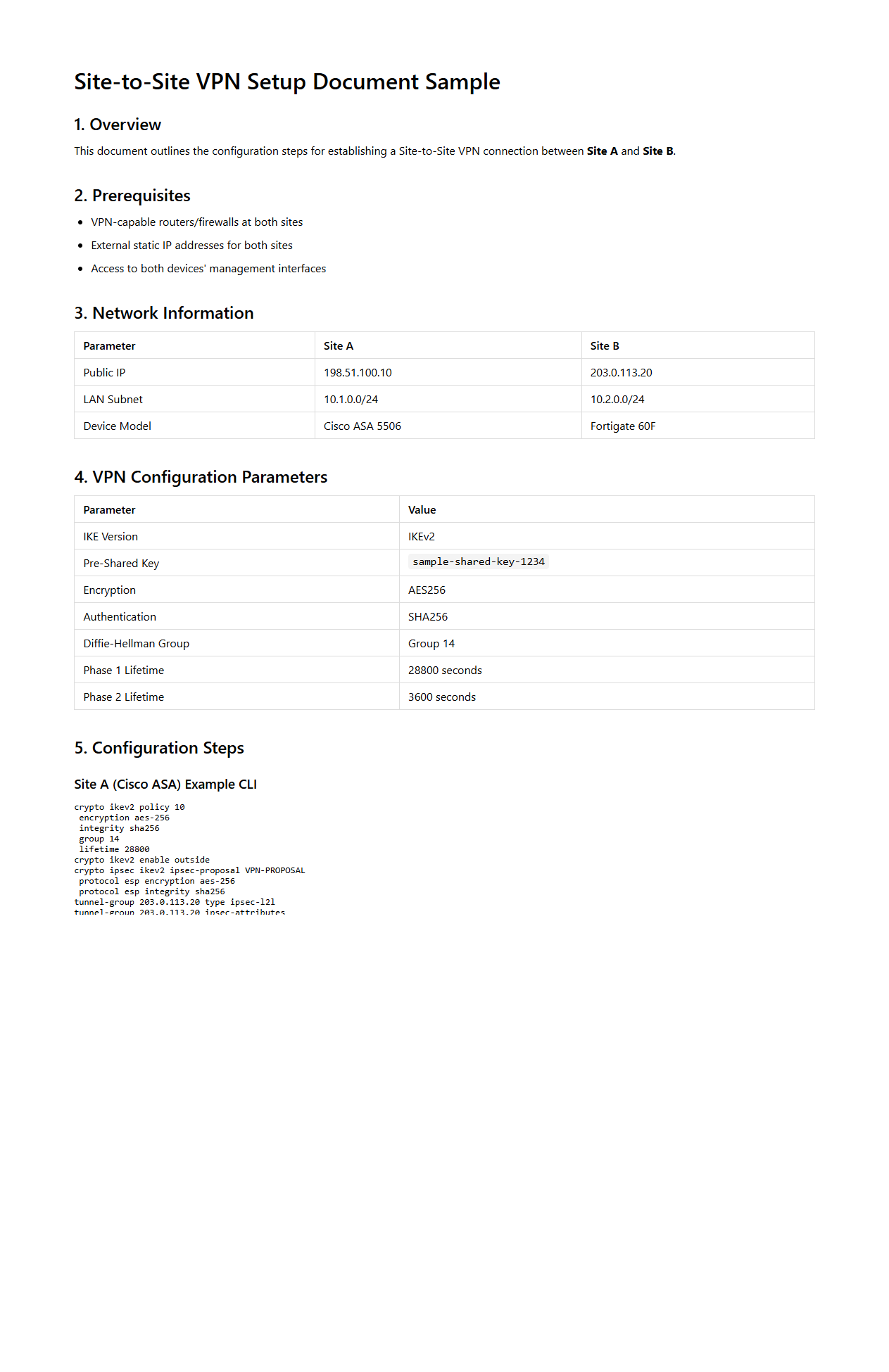
Site-to-Site VPN Setup Document Sample
A
Site-to-Site VPN Setup Document Sample provides a detailed guide for configuring secure, encrypted network connections between multiple office locations or data centers. It typically includes step-by-step instructions, network settings, IP addresses, encryption protocols, and authentication methods to ensure seamless communication across different sites. This document serves as a reference to establish and maintain reliable VPN tunnels, enhancing data security and connectivity for distributed systems.
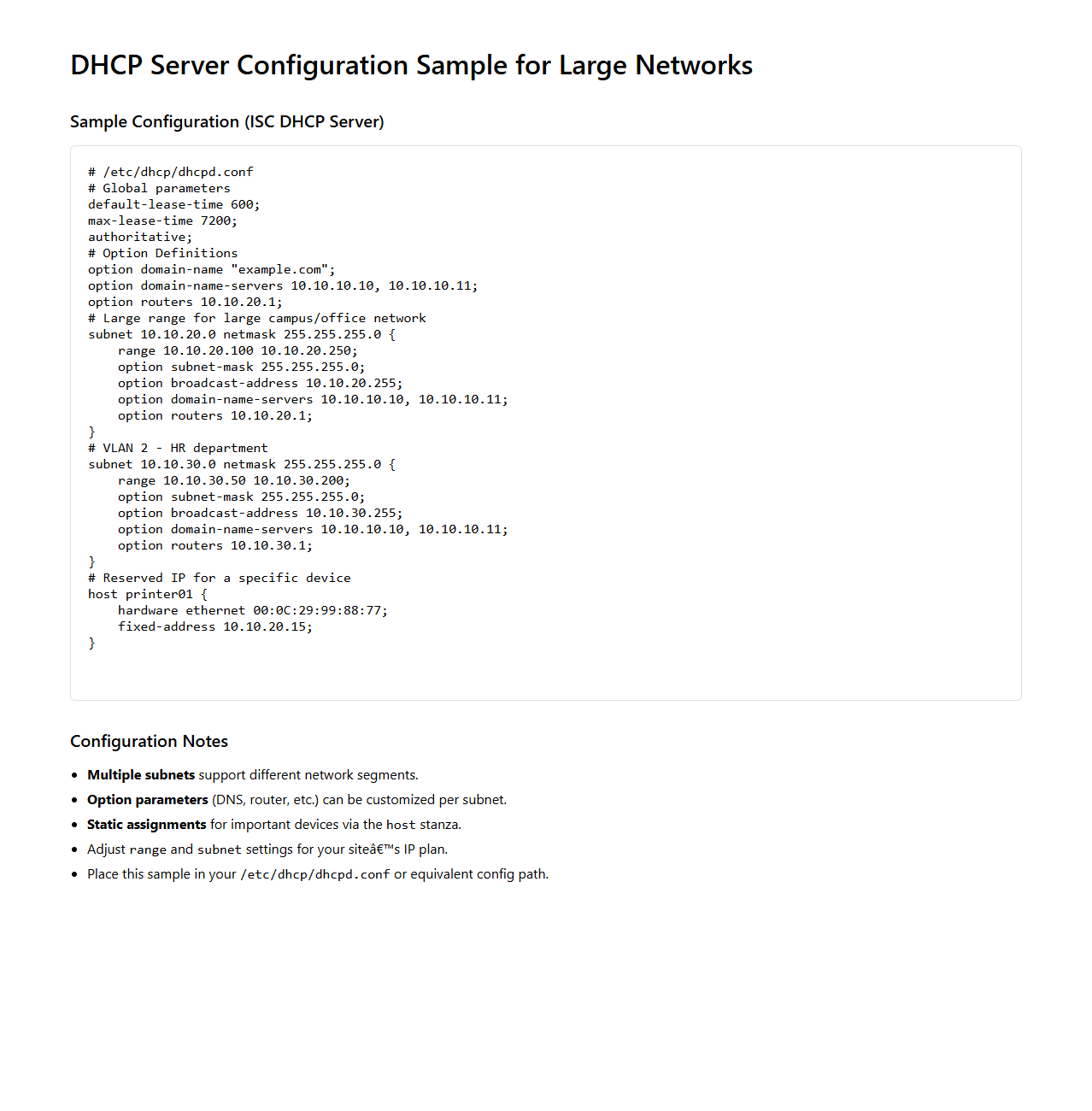
DHCP Server Configuration Sample for Large Networks
The
DHCP Server Configuration Sample for Large Networks document provides detailed guidelines and best practices for setting up DHCP servers to efficiently manage IP address allocation in extensive network environments. It covers configuration parameters, subnetting strategies, lease duration settings, and scalability considerations to ensure reliable and optimized network performance. This resource is essential for network administrators aiming to maintain seamless connectivity and avoid IP conflicts in large-scale infrastructures.
What protocols are standardized in the Network Configuration Document for secure device communication?
The Network Configuration Document mandates the use of SSL/TLS and SSH protocols for secure device communication. These protocols ensure encrypted data transfer, protecting against unauthorized access. Additionally, protocols like IPsec are specified for secure VPN connections within the network.
How does the document address VLAN segmentation across multiple departments?
The document details VLAN segmentation by assigning distinct VLAN IDs to each department to isolate traffic and improve security. It emphasizes strict access controls between VLANs to prevent unauthorized cross-department communication. Inter-VLAN routing is managed through configured Layer 3 devices ensuring segmented yet efficient network traffic flow.
Which redundancy methods are specified for core network switches?
The Network Configuration Document specifies the implementation of Link Aggregation Control Protocol (LACP) and Spanning Tree Protocol (STP) for redundancy in core switches. It also recommends deploying dual power supplies and redundant switch pairs to ensure uninterrupted network availability. These measures collectively provide failover capabilities and minimize downtime.
Are change management procedures for IP schema modifications detailed in the document?
Yes, the document outlines comprehensive change management procedures for IP schema modifications, including approval workflows and impact analysis. It requires maintaining updated documentation and communication with stakeholders before implementing changes. This process ensures network stability and consistency across all devices.
How does the document handle remote access configurations for third-party vendors?
Remote access for third-party vendors is strictly regulated through multi-factor authentication and time-limited access policies. The document mandates the use of secure VPN tunnels with strong encryption to protect data integrity. Additionally, vendor activities are logged and monitored to maintain audit trails and compliance standards.