A Cybersecurity Assessment Document Sample for Financial Services provides a comprehensive framework to evaluate the security posture of financial institutions. It includes detailed analysis of potential vulnerabilities, risk management strategies, and compliance with industry regulations. This sample helps organizations identify gaps and strengthen their defenses against cyber threats.
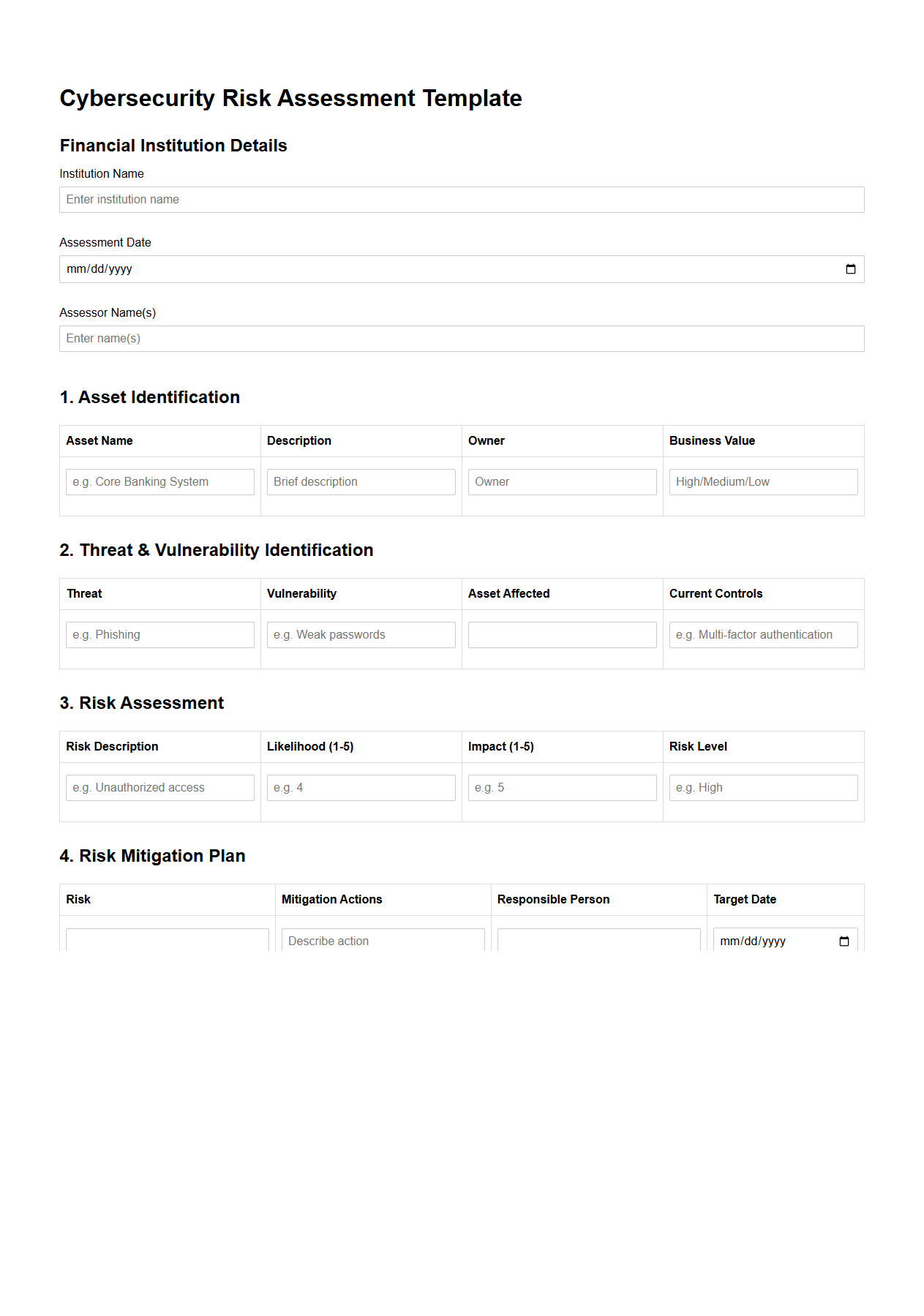
Cybersecurity Risk Assessment Template for Financial Institutions
A
Cybersecurity Risk Assessment Template for financial institutions is a structured framework designed to identify, evaluate, and prioritize potential cyber threats specific to banking and financial services. It systematically guides organizations through assessing vulnerabilities related to data breaches, regulatory compliance, and operational disruptions. This document supports risk mitigation efforts by providing clear criteria and standardized metrics tailored to the unique challenges faced by financial institutions.
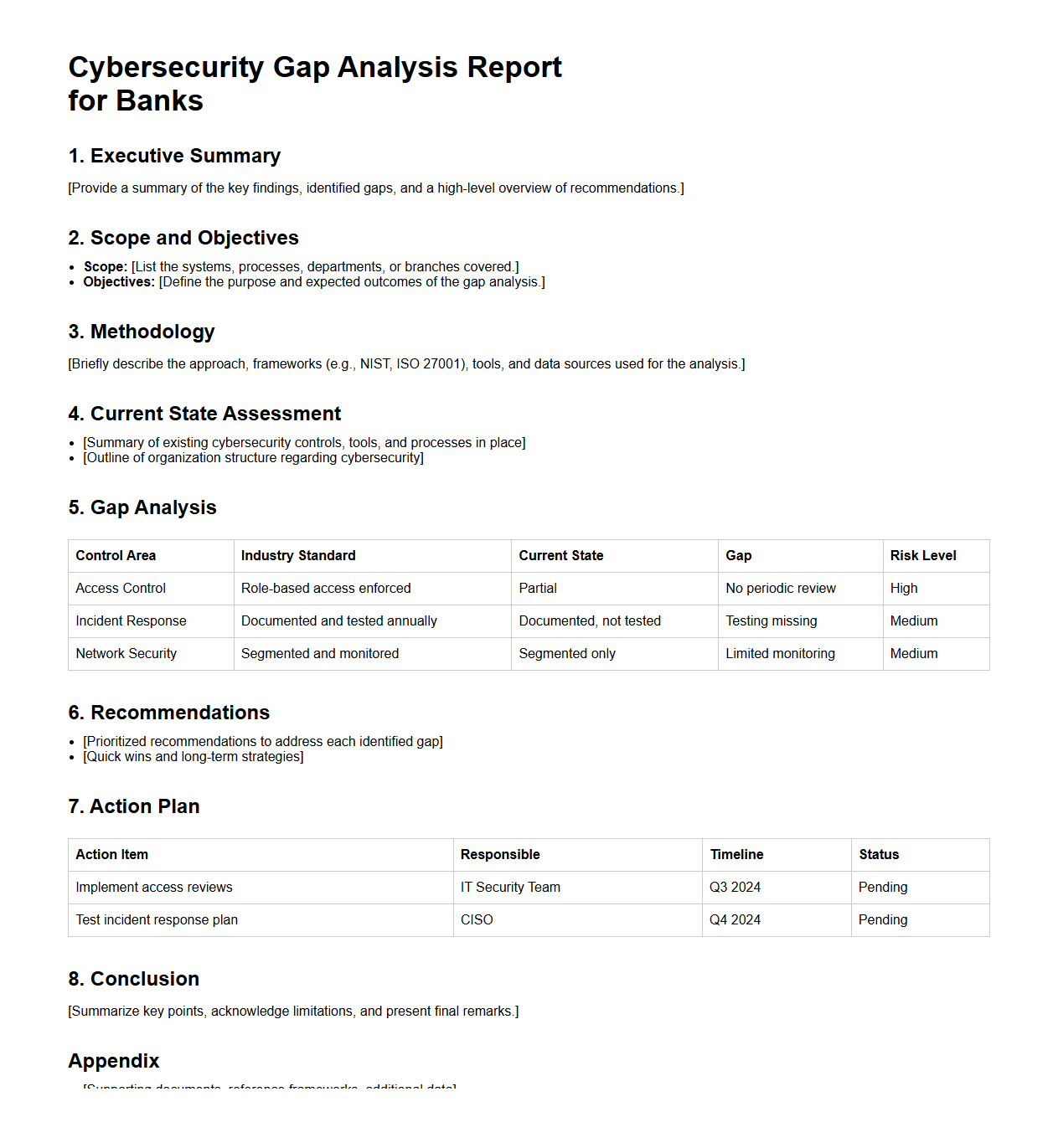
Cybersecurity Gap Analysis Report for Banks
A
Cybersecurity Gap Analysis Report for banks identifies vulnerabilities and weaknesses in existing security measures by comparing current practices against industry standards and regulatory requirements such as FFIEC and PCI-DSS. This document provides actionable insights to enhance risk management strategies, ensuring the protection of sensitive financial data and maintaining compliance. Banks rely on this report to prioritize cybersecurity investments and strengthen defense mechanisms against evolving cyber threats.
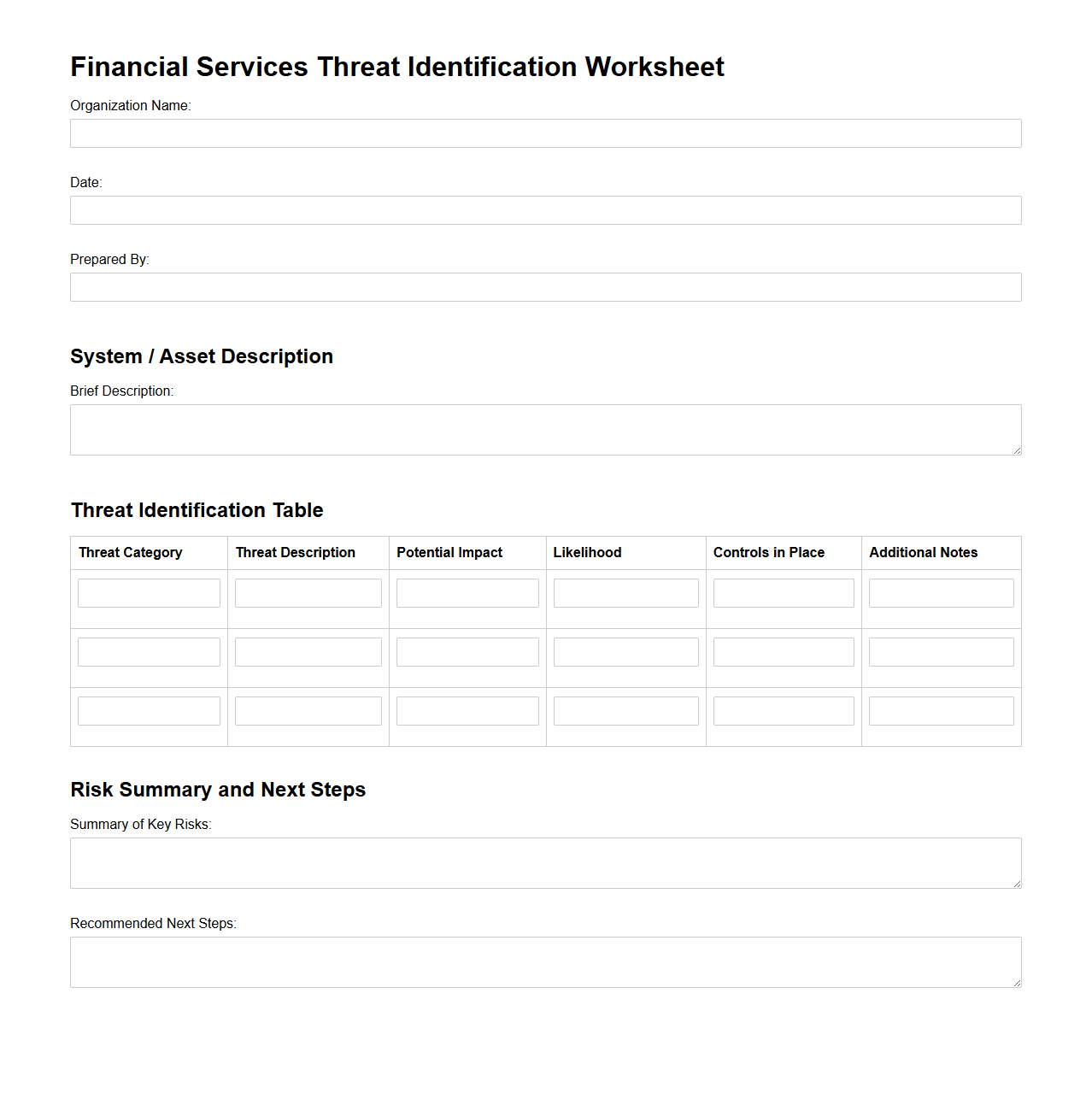
Financial Services Threat Identification Worksheet
The
Financial Services Threat Identification Worksheet document serves as a structured tool to systematically identify and assess potential threats within the financial services sector. It enables organizations to categorize risks such as cyberattacks, fraud, regulatory non-compliance, and operational vulnerabilities, facilitating proactive risk management. By documenting threat sources, impact levels, and mitigation strategies, this worksheet supports comprehensive security planning and regulatory adherence.
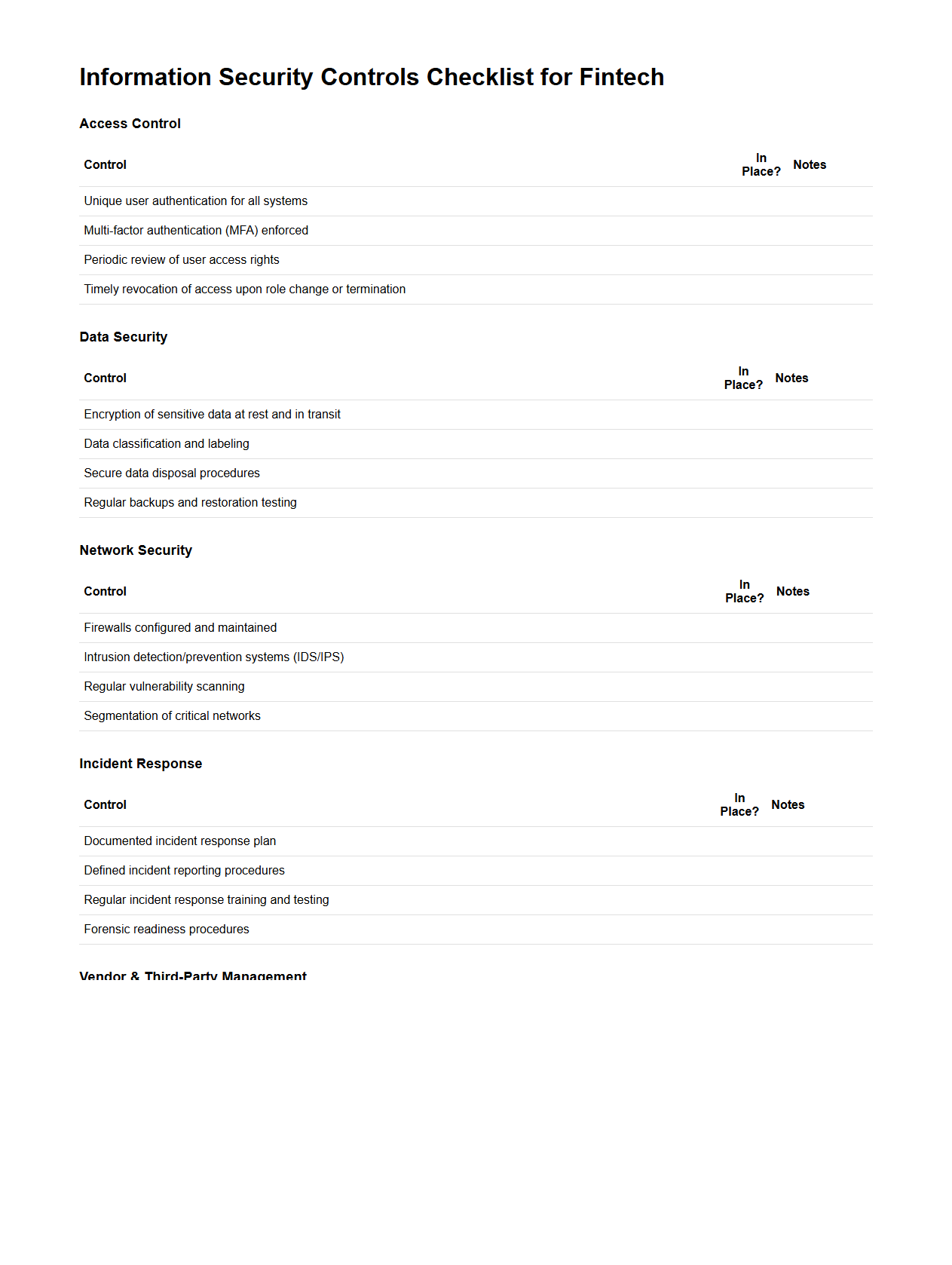
Information Security Controls Checklist for Fintech
An
Information Security Controls Checklist for Fintech is a comprehensive tool designed to ensure that financial technology organizations implement essential security measures to protect sensitive data and comply with regulatory standards. This document typically includes guidelines on risk management, access controls, encryption protocols, and incident response procedures tailored specifically for fintech environments. It serves as a practical framework for assessing vulnerabilities and strengthening the overall cybersecurity posture within the fintech sector.
Vendor Risk Assessment Form for Financial Services
A
Vendor Risk Assessment Form for Financial Services is a critical document used to evaluate potential and existing third-party vendors by identifying associated risks such as compliance, security, and operational vulnerabilities. This form collects detailed information on vendors' financial stability, regulatory adherence, data protection measures, and business continuity plans to ensure alignment with industry standards and internal policies. Utilizing this assessment enables financial institutions to mitigate risks, safeguard sensitive data, and maintain regulatory compliance effectively.
Cyber Incident Response Evaluation for Investment Firms
The
Cyber Incident Response Evaluation for Investment Firms document provides a structured framework to assess an organization's preparedness and effectiveness in managing cybersecurity incidents. It outlines essential protocols, roles, and responsibilities designed to minimize the impact of cyber attacks on sensitive financial data and maintain compliance with regulatory requirements. This evaluation supports continuous improvement in incident detection, containment, and recovery processes specific to the investment sector.
Data Protection Assessment Template for Credit Unions
A
Data Protection Assessment Template for Credit Unions document serves as a structured framework to evaluate and ensure compliance with data privacy regulations specific to credit unions. It helps identify potential risks related to the handling, storage, and sharing of sensitive member information, enabling institutions to implement effective security measures. This template supports credit unions in maintaining regulatory standards such as the Gramm-Leach-Bliley Act (GLBA) and enhances overall data governance practices.
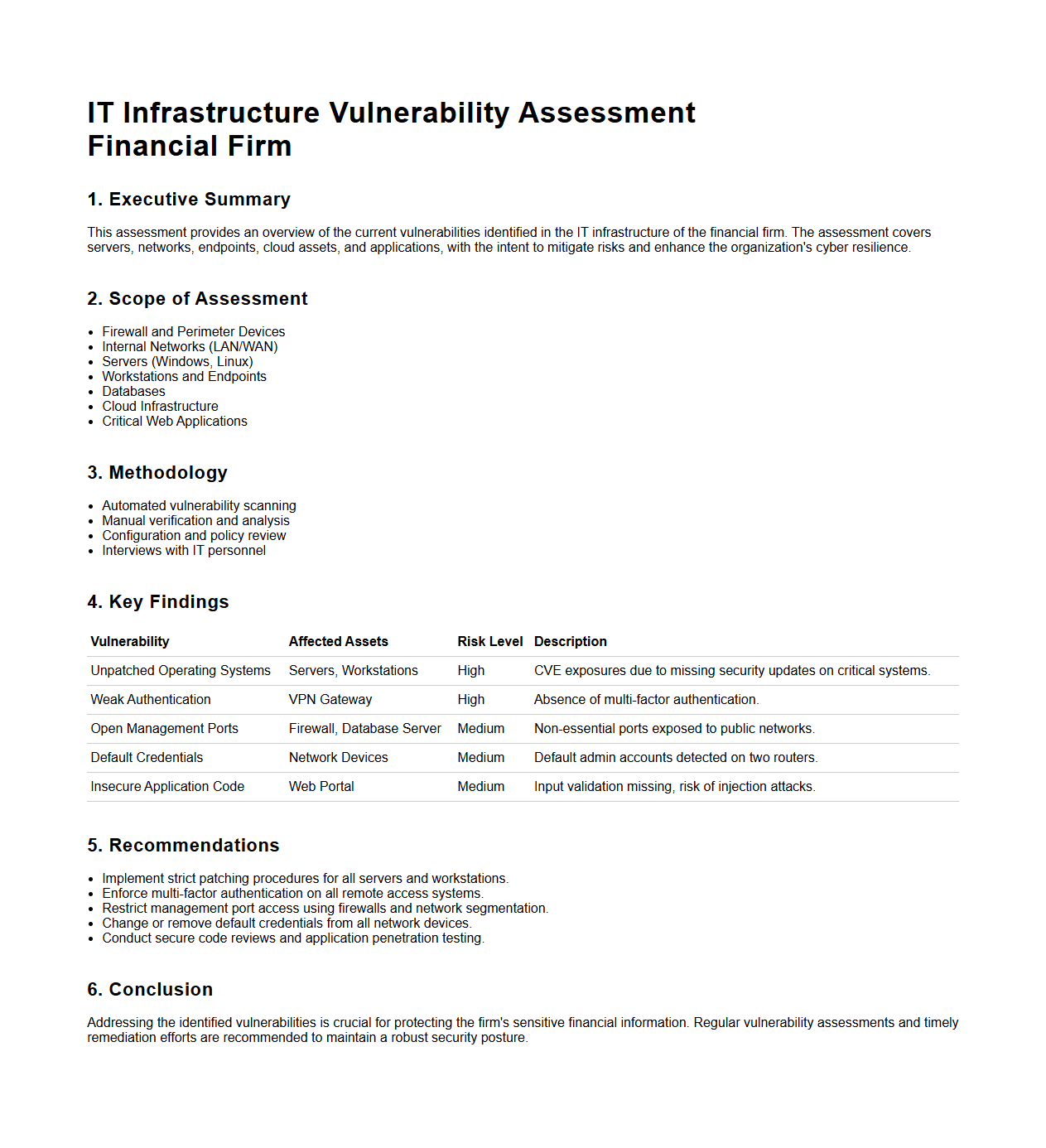
IT Infrastructure Vulnerability Assessment for Financial Firms
An
IT Infrastructure Vulnerability Assessment for financial firms is a comprehensive analysis designed to identify and evaluate security weaknesses within an organization's hardware, software, networks, and data centers. It focuses on detecting potential risks that could lead to data breaches, financial losses, or compliance failures specific to the financial industry's regulatory requirements such as PCI DSS and SOX. The document typically outlines methodologies, tools, and prioritized remediation strategies to strengthen defenses and protect sensitive financial information.
Regulatory Compliance Cybersecurity Assessment for Finance
A
Regulatory Compliance Cybersecurity Assessment for finance is a comprehensive evaluation designed to ensure financial institutions adhere to relevant laws, regulations, and industry standards such as GLBA, PCI DSS, and SOX. This assessment identifies vulnerabilities in cybersecurity controls, risk management practices, and data protection measures to mitigate potential breaches and regulatory penalties. It also provides actionable recommendations to maintain compliance and protect sensitive financial data against evolving cyber threats.
Business Continuity Cybersecurity Assessment for Financial Services
A
Business Continuity Cybersecurity Assessment for Financial Services document evaluates the resilience and security measures of financial institutions against cyber threats, ensuring critical operations remain uninterrupted during disruptions. It identifies vulnerabilities, assesses risk management strategies, and outlines protocols to maintain data integrity and operational continuity. This assessment supports regulatory compliance and reinforces stakeholder confidence by demonstrating robust preparedness in the face of cyber incidents.
Third-Party Vendor Risk Management in Financial Transactions
The document emphasizes the importance of third-party vendor risk management by establishing strict criteria for vendor selection and ongoing evaluation. It mandates comprehensive due diligence processes to ensure that vendors comply with security and privacy standards in financial transactions. Regular audits and risk assessments are required to mitigate potential threats posed by external partners.
Recommended Encryption Protocols for Protecting Customer Data
To safeguard sensitive customer information, the document recommends using advanced encryption protocols such as AES-256 and TLS 1.3. These protocols ensure data confidentiality and integrity during transmission and storage. It also advises the use of end-to-end encryption to protect financial service transactions from unauthorized access.
Guidelines for Continuous Monitoring of Insider Threats
The assessment outlines detailed continuous monitoring strategies to detect insider threats within banking environments. This includes implementing behavior analytics, access controls, and anomaly detection systems to identify suspicious activities in real-time. Regular training and awareness programs are also emphasized to reduce risks from internal personnel.
Regulatory Compliance for Multi-Jurisdictional Financial Institutions
The document provides a comprehensive framework to ensure regulatory compliance across diverse jurisdictions. It highlights the need for alignment with local laws, international standards, and cross-border data privacy requirements. Institutions are encouraged to maintain documentation and governance processes that facilitate audits and regulatory reviews globally.
Incident Response Procedures for Payment System Breaches
The incident response section outlines specific steps for addressing payment system breaches, including immediate containment and eradication measures. It emphasizes rapid coordination among security teams, legal advisors, and regulatory bodies to minimize damage and comply with notification requirements. Post-incident analysis and continuous improvement are also key components of the response framework.
More Technology Templates