Executive Summary for Cloud System Architecture
An
Executive Summary for a Cloud System Architecture document provides a concise overview of the cloud infrastructure design, highlighting key components such as scalability, security, and integration with existing systems. It summarizes strategic objectives, major architectural decisions, and anticipated benefits to stakeholders, ensuring quick comprehension without technical depth. This section aids executives in grasping the project's value proposition and alignment with business goals.
Cloud Infrastructure Overview Document
A
Cloud Infrastructure Overview Document provides a detailed summary of the architecture, components, and services involved in a cloud computing environment. It outlines the deployment models, resource allocation, security protocols, and scalability features critical for managing and optimizing cloud infrastructure. This document serves as a strategic guide for IT teams to ensure efficient cloud operations and alignment with business goals.
Functional Requirements for Cloud Architecture
Functional requirements for cloud architecture document outline specific capabilities and services that the cloud system must provide to meet business needs, such as scalability, availability, and security features. This document details user interactions, data processing workflows, and integration points with other systems to ensure the architecture supports operational goals effectively. Clear articulation of
functional requirements guides the design and implementation phases, ensuring alignment with organizational objectives and technical constraints.
Cloud Solution Technical Architecture Design
A
Cloud Solution Technical Architecture Design document outlines the structural blueprint for deploying cloud-based applications and services, detailing components such as infrastructure, network topology, security measures, and integration points. It serves as a critical guide for development and operations teams to ensure scalability, reliability, and compliance within cloud environments like AWS, Azure, or Google Cloud. The document includes architecture diagrams, technology stack choices, and best practices for resource management tailored to specific business objectives.
Security Controls in Cloud System Architecture
Security controls in a cloud system architecture document refer to the specific policies, procedures, and technologies implemented to protect cloud infrastructure, applications, and data from unauthorized access, breaches, and other cyber threats. These controls include identity and access management, encryption protocols, network security measures, and continuous monitoring to ensure compliance with regulatory standards and organizational security requirements. Emphasizing
security controls helps organizations maintain data integrity, confidentiality, and availability within their cloud environments.
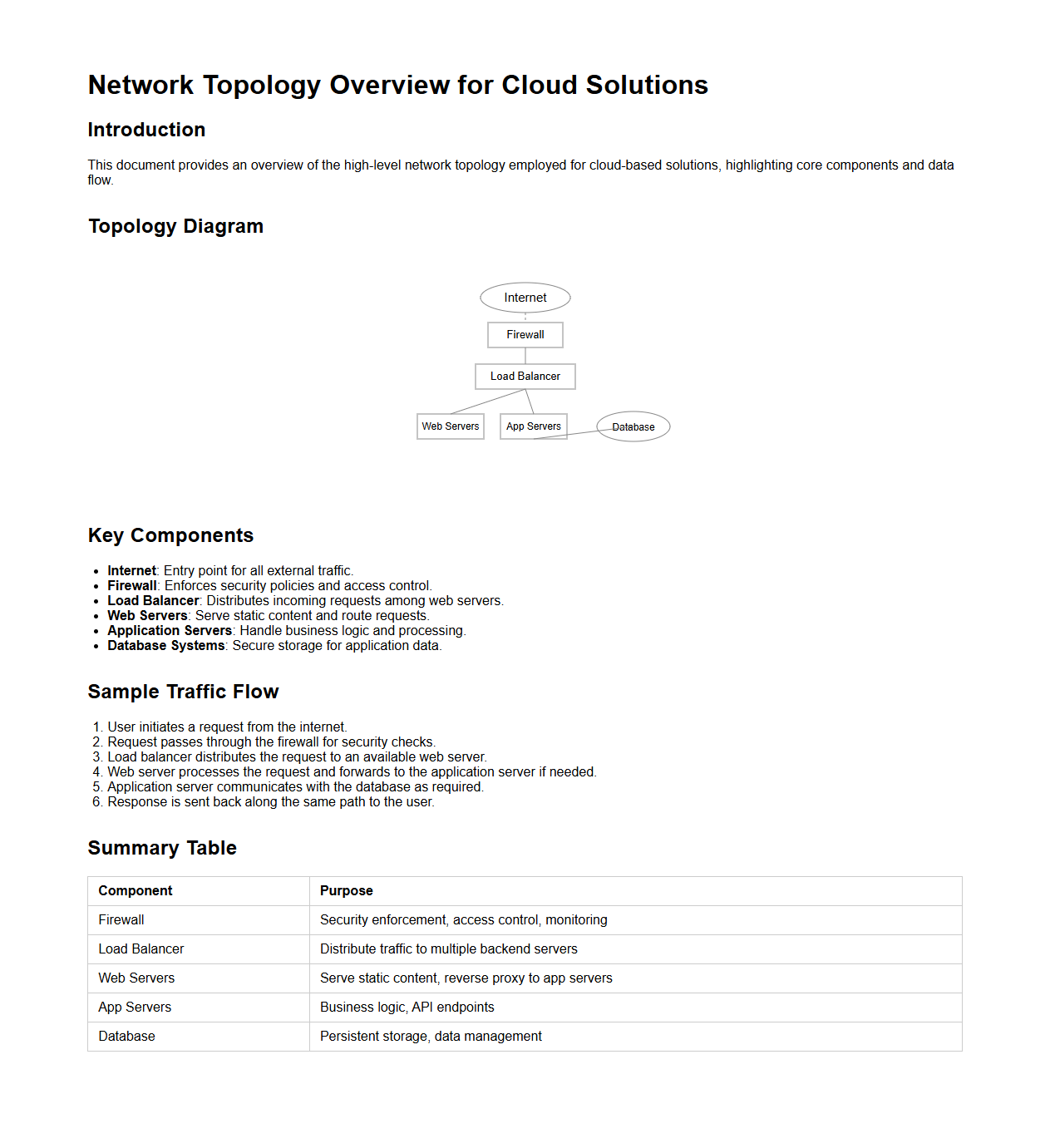
Network Topology Overview for Cloud Solutions
The
Network Topology Overview for Cloud Solutions document provides a detailed representation of the structural arrangement of network components within cloud environments, including virtual machines, subnets, gateways, and firewalls. It highlights how these elements interconnect to optimize performance, scalability, and security across public, private, or hybrid cloud infrastructures. This overview is essential for architects and engineers to design, deploy, and troubleshoot cloud networks effectively.
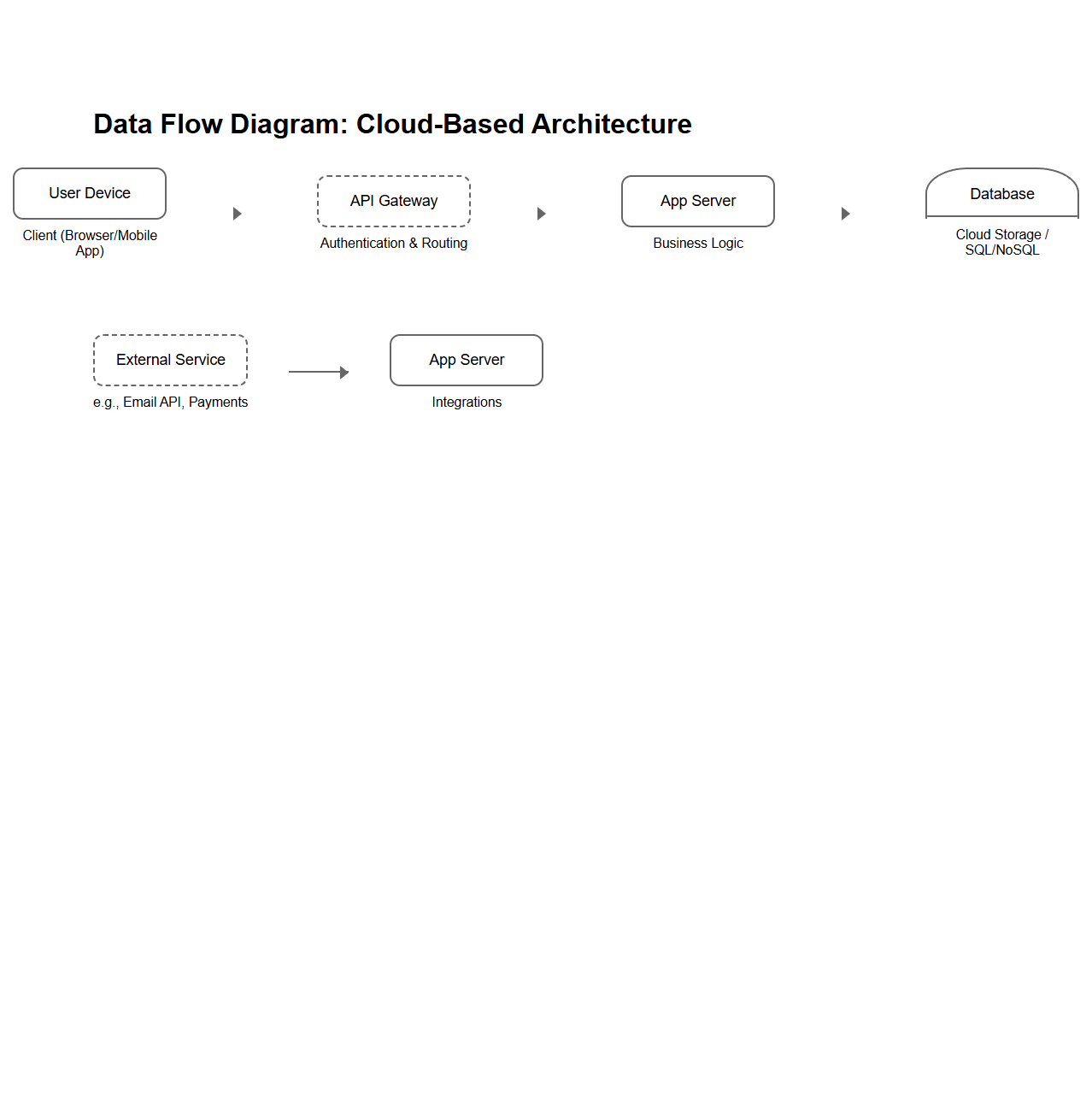
Data Flow Diagram for Cloud-Based Architecture
A
Data Flow Diagram (DFD) for Cloud-Based Architecture document visually represents the movement of data between cloud services, users, and external systems to ensure efficient data processing and security. It outlines key components such as data sources, processing nodes, storage units, and data sinks in a cloud environment, highlighting the relationships and data exchanges. This diagram aids in identifying potential bottlenecks, security vulnerabilities, and optimizing resource allocation within cloud infrastructure.
Scalability and Performance Plan for Cloud Systems
A
Scalability and Performance Plan for Cloud Systems document outlines strategies to ensure cloud infrastructure can efficiently handle increasing workloads while maintaining optimal performance. It includes metrics for capacity planning, load balancing techniques, and resource scaling policies to meet demand fluctuations without service degradation. This plan helps organizations optimize cloud resource utilization, reduce latency, and enhance user experience under varying operational conditions.
Deployment and Integration Strategy for Cloud Platforms
The
Deployment and Integration Strategy for Cloud Platforms document outlines the comprehensive plan for implementing cloud services while ensuring seamless integration with existing systems. It details the methodologies, tools, and best practices to deploy applications securely and efficiently across various cloud environments. This strategy addresses compatibility, data migration, security protocols, and continuous monitoring to optimize cloud resource utilization and operational performance.
High Availability and Disaster Recovery Architecture Document
The
High Availability and Disaster Recovery Architecture Document outlines the strategic framework designed to ensure continuous system operation and data integrity during failures or disasters. It details the technical approaches, infrastructure configurations, and recovery procedures to minimize downtime and data loss, supporting business continuity objectives. This document serves as a critical reference for IT teams to implement resilient architectures and effective disaster recovery plans.
What specific cloud deployment model is detailed in the system architecture document?
The system architecture document outlines a hybrid cloud deployment model, integrating both private and public cloud resources. This model ensures flexibility by leveraging the strengths of on-premises infrastructure alongside cloud services. The architecture promotes optimal resource utilization and enhanced security management.
How does the document address multi-region failover or disaster recovery in the architecture?
The document details a multi-region failover strategy to ensure high availability and resilience. It involves real-time data replication across geographically dispersed data centers, minimizing downtime during regional outages. Disaster recovery plans include automated failover mechanisms and regular testing to maintain system reliability.
Which security controls for API gateways are specified in the system architecture?
Security controls for API gateways in the architecture emphasize authentication and authorization protocols such as OAuth 2.0 and JWT tokens. Rate limiting and traffic filtering are implemented to prevent abuse and denial-of-service attacks. Additionally, end-to-end encryption using TLS secures data in transit through the gateway.
Does the document define auto-scaling strategies for microservices in the cloud environment?
The architecture document defines auto-scaling policies based on CPU utilization, memory usage, and request rates for microservices. It incorporates event-driven scaling triggered by workload changes to maintain optimal performance. These strategies ensure cost efficiency by dynamically adjusting resource allocation.
Are cloud vendor lock-in risks and mitigation strategies discussed in the architecture document?
The document highlights cloud vendor lock-in risks and proposes mitigation strategies like containerization and multi-cloud deployment. It advocates for using open standards and abstraction layers to maintain portability. These practices reduce dependency on a single vendor and enhance system flexibility.