A Business Continuity Plan Document Sample for Technology Operations outlines essential strategies and procedures to ensure critical IT systems remain functional during disruptions. It details risk assessment, recovery objectives, and communication protocols tailored to technology environments. This document serves as a blueprint for minimizing downtime and maintaining seamless business functions.
IT Disaster Recovery Plan Template
An
IT Disaster Recovery Plan Template document provides a structured framework for organizations to efficiently restore critical IT systems and data following unexpected disruptions or disasters. It outlines key procedures, roles, responsibilities, and resources necessary to minimize downtime and data loss, ensuring business continuity. This template serves as a customizable guide to help companies develop a comprehensive recovery strategy tailored to their specific IT infrastructure and risk exposure.
Data Backup and Restoration Procedures Example
A
Data Backup and Restoration Procedures Example document outlines the standardized steps for creating and recovering data copies to ensure business continuity and data integrity. It details specific methods, tools, schedules, and roles involved in performing reliable backups and timely restoration in case of data loss or system failures. This document serves as a crucial reference for IT teams to minimize downtime and data loss risks.
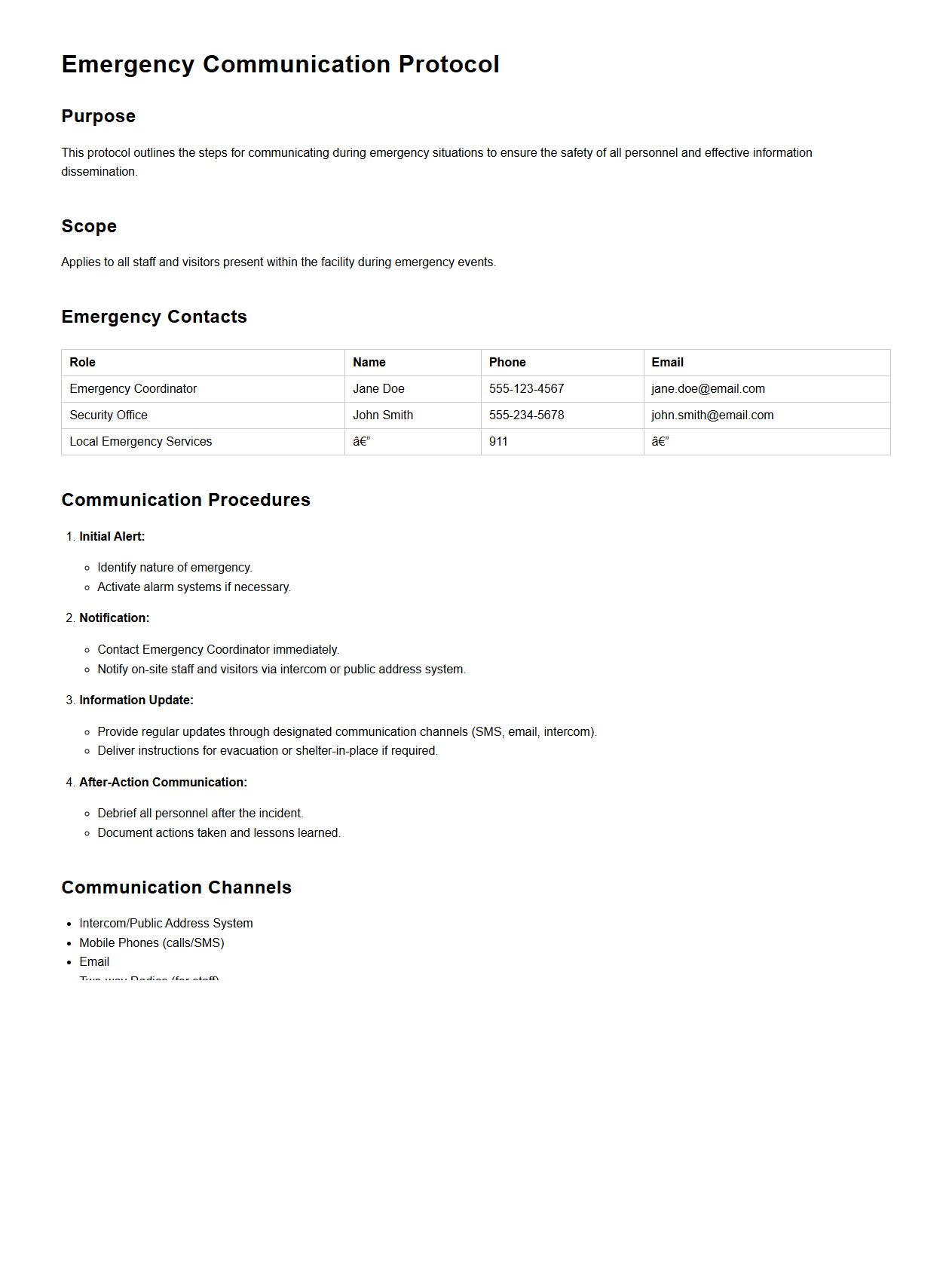
Emergency Communication Protocol Sample
An
Emergency Communication Protocol Sample document outlines standardized procedures for effective information exchange during crises, ensuring timely alerts and coordination among responders. It typically includes contact lists, communication methods, message templates, and step-by-step instructions to manage various emergency scenarios. This document enhances organizational readiness by minimizing confusion and facilitating clear, consistent communication under pressure.
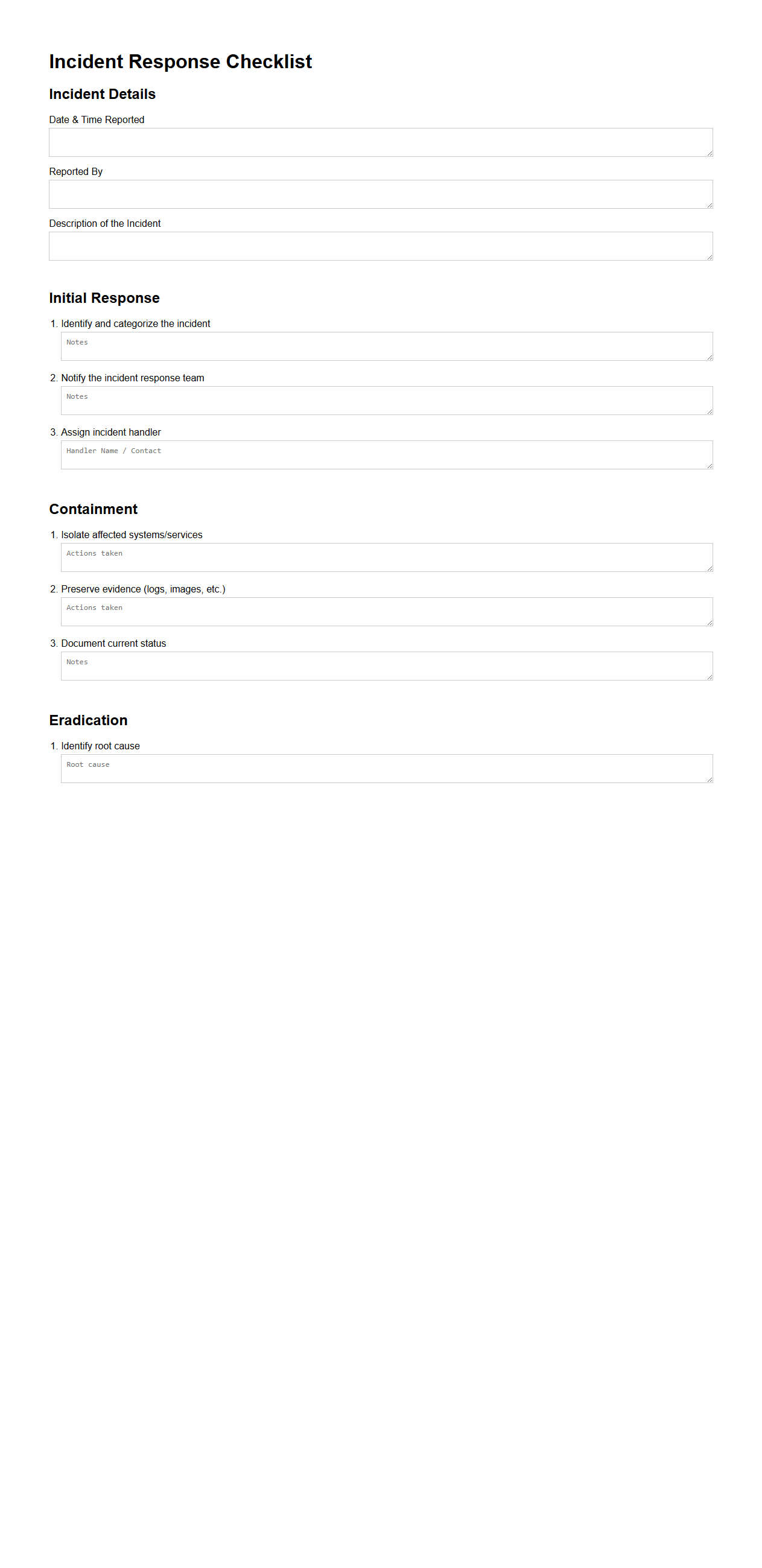
Incident Response Checklist for Technology Teams
An
Incident Response Checklist for Technology Teams document outlines a structured series of steps to quickly identify, analyze, and mitigate security breaches or system failures. It serves as a practical guide for IT professionals to ensure consistent and effective handling of incidents by detailing key actions such as initial detection, containment strategies, communication protocols, and recovery procedures. This checklist helps minimize downtime, reduce impacts on business operations, and supports compliance with industry standards and regulations.
Technology Risk Assessment Matrix
A
Technology Risk Assessment Matrix document is a strategic tool used to identify, evaluate, and prioritize potential technology-related risks within an organization. It categorizes risks based on their likelihood and impact, enabling informed decision-making for risk mitigation and resource allocation. This matrix supports proactive risk management by providing a clear visual representation of vulnerabilities across hardware, software, networks, and data systems.
Critical Systems Inventory Document
The
Critical Systems Inventory Document is a comprehensive record detailing all essential systems within an organization that support core business functions and require stringent security measures. It includes information such as system names, owners, risk assessments, dependencies, and compliance status to ensure effective management and protection against potential threats. Maintaining this document aids in prioritizing system security efforts and aligning with regulatory requirements.
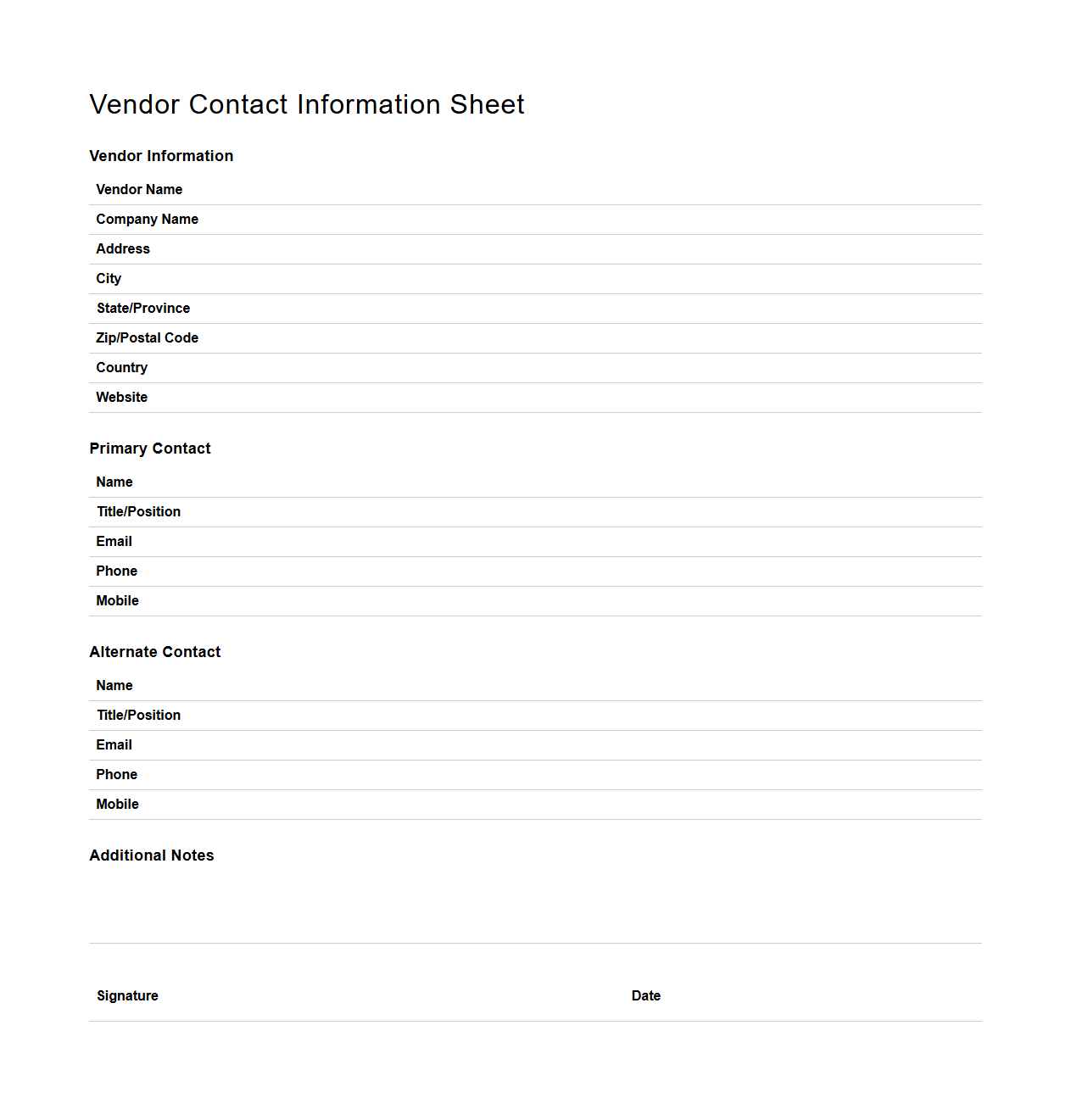
Vendor Contact Information Sheet
A
Vendor Contact Information Sheet is a document used to compile essential contact details of suppliers or service providers, facilitating efficient communication and management. It typically includes names, phone numbers, email addresses, physical addresses, and points of contact for specific departments or roles within the vendor organization. Maintaining this sheet ensures quick access to vendor information, streamlining procurement processes and issue resolution.
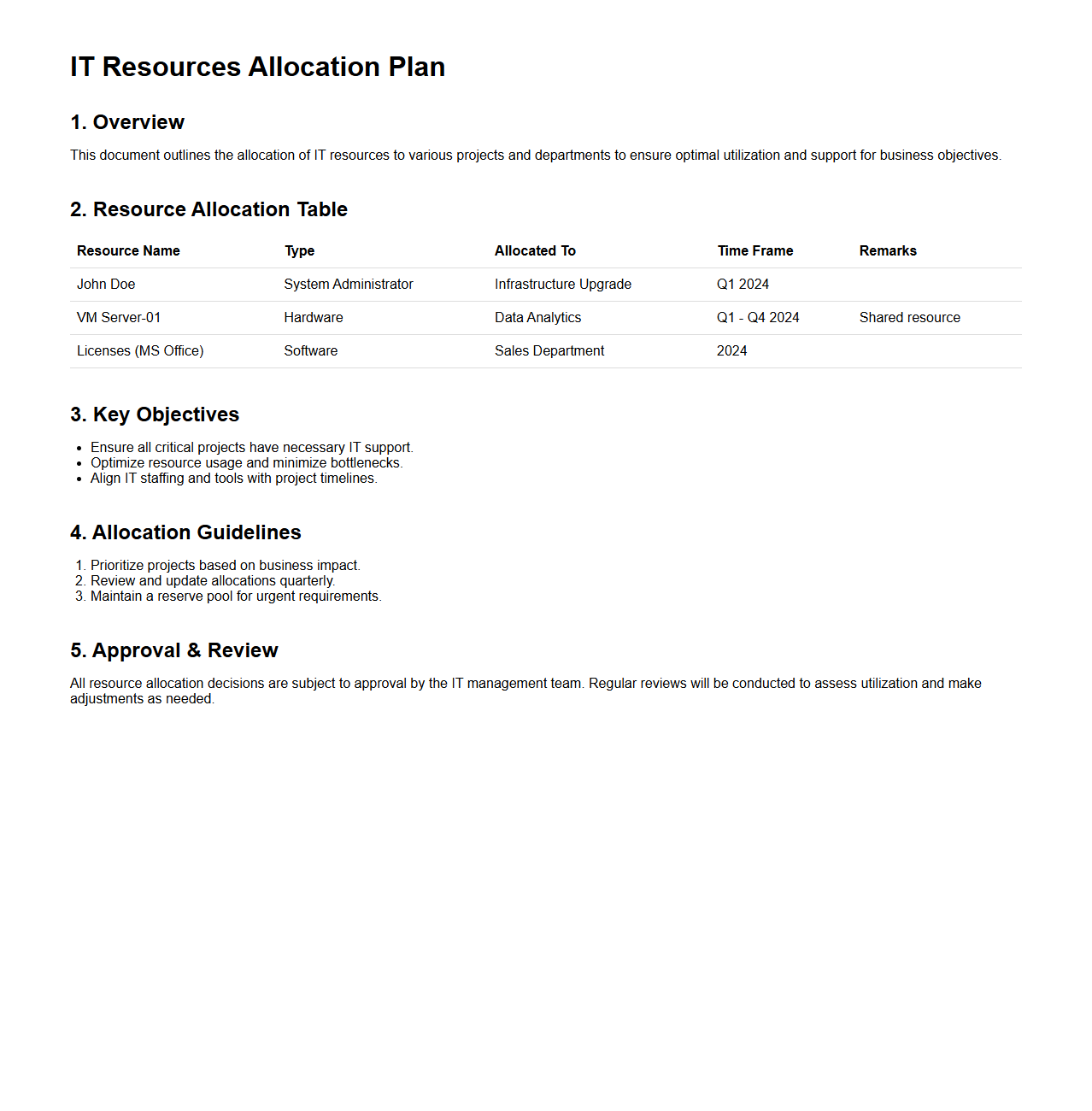
IT Resources Allocation Plan
An
IT Resources Allocation Plan document precisely outlines the distribution and management of technological assets, including hardware, software, and human resources, across various projects or departments. It ensures efficient utilization by aligning resources with organizational priorities, project timelines, and budget constraints. This plan supports optimal workflow, reduces resource conflicts, and enhances project delivery success rates.
Business Impact Analysis Report Example
A
Business Impact Analysis Report Example document outlines the potential effects of disruptions on critical business functions, helping organizations identify priorities for recovery and continuity planning. It includes detailed assessments of operational impacts, financial losses, and resource dependencies to guide risk management decisions. This report serves as a template to standardize impact analysis and support informed strategy development for business resilience.
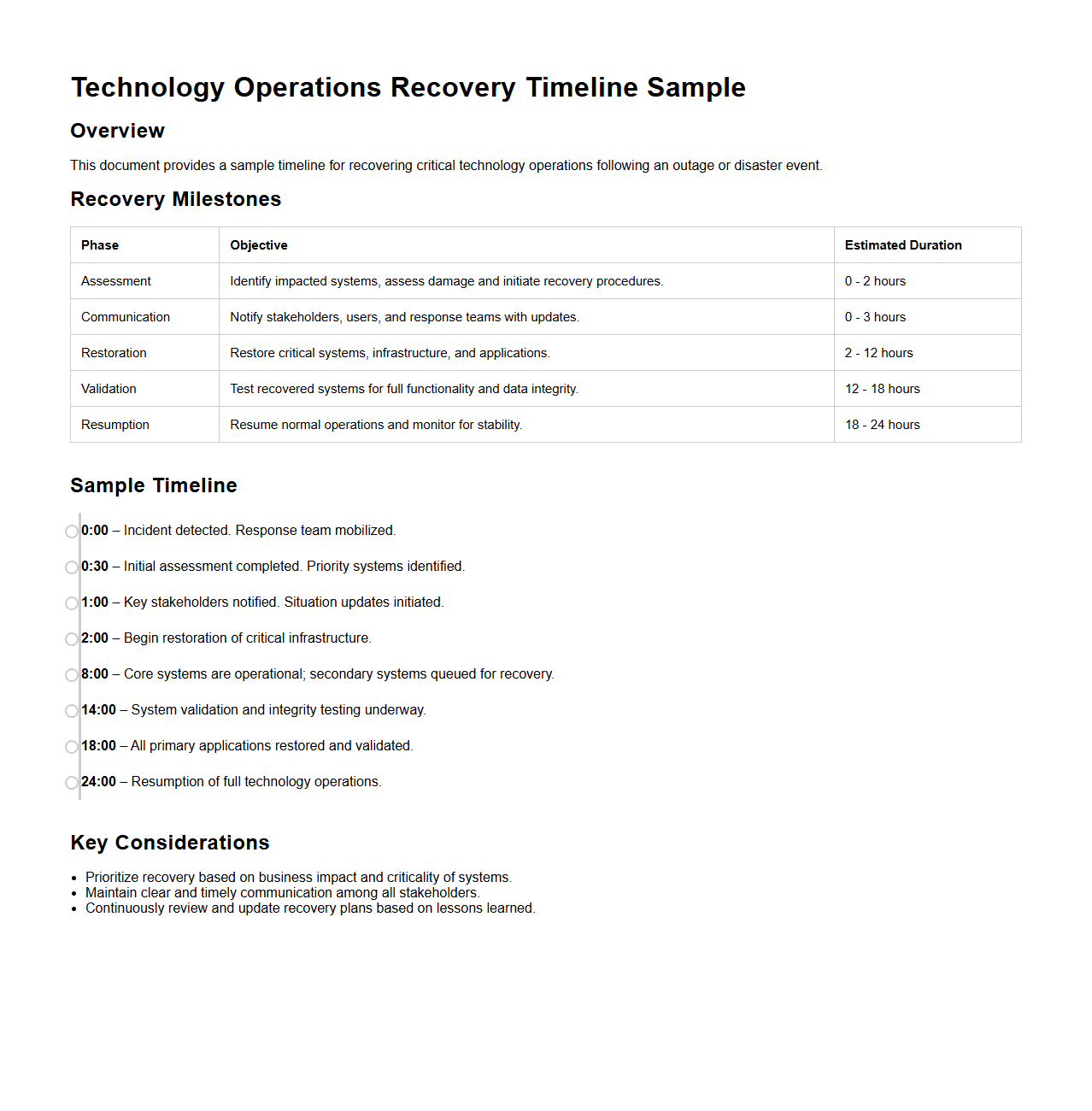
Technology Operations Recovery Timeline Sample
A
Technology Operations Recovery Timeline Sample document outlines the step-by-step schedule and actions required to restore IT systems and services after a disruption or disaster. It includes specific timelines for recovering critical infrastructure, applications, and network components to minimize downtime and data loss. This plan ensures coordinated efforts across teams to meet recovery time objectives (RTO) and maintain business continuity.
Mandatory Data Backup Protocols in Business Continuity Plan
The Business Continuity Plan mandates daily backups of all critical data to secure offsite locations. Backup integrity checks are performed weekly to ensure data reliability. Retention policies require maintaining backup copies for a minimum of 90 days to support recovery efforts.
Third-Party Vendor Risk Management
The plan includes comprehensive third-party vendor risk assessments to evaluate their reliability and security measures. Vendors providing critical technology services must comply with established cybersecurity standards and continuous monitoring protocols. Regular audits and contingency agreements are mandated to mitigate operational risks from these external providers.
Communication Procedures for IT Incident Escalation
During disruptions, the plan enforces a structured IT incident escalation process beginning with immediate notification of the IT support team. Incidents are categorized by severity, triggering predefined communication flows to stakeholders and executive management. This ensures timely and effective coordination throughout the incident lifecycle.
Metrics for Assessing RTO and RPO
Recovery Time Objectives (RTO) are measured by the duration from disruption onset to restoration of full IT functionality. Recovery Point Objectives (RPO) are assessed based on the maximum tolerated data loss timeframe during recovery. Continuous monitoring of these metrics ensures alignment with business impact analyses and improvement of resiliency strategies.
Roles and Responsibilities for IT Disaster Recovery Team
The document defines clear roles and responsibilities to organize efficient response efforts during IT disasters. Team members are assigned specific tasks such as incident assessment, system recovery, and communication management to streamline recovery operations. Regular training and drills ensure readiness and accountability within the disaster recovery team.
More Technology Templates