A Vulnerability Assessment Document Sample for Cloud Storage outlines the identification and analysis of security weaknesses within cloud storage systems. It provides a detailed evaluation of potential threats, vulnerabilities, and the impact on data integrity and confidentiality. This document serves as a crucial tool for implementing appropriate mitigation strategies to enhance cloud storage security.
Cloud Storage Vulnerability Assessment Report Template
The
Cloud Storage Vulnerability Assessment Report Template is a structured document designed to systematically identify, evaluate, and document security weaknesses within cloud storage environments. It provides sections for detailing vulnerabilities, risk levels, potential impacts, and recommended mitigation strategies, helping organizations enhance their cloud storage security posture. This template facilitates consistent reporting and supports compliance with industry standards like ISO 27001 and NIST.
Cloud Data Security Risk Assessment Sample
A
Cloud Data Security Risk Assessment Sample document provides a structured template to identify, evaluate, and mitigate potential security threats associated with storing and processing data in cloud environments. It outlines key risk factors such as data breaches, compliance issues, and access vulnerabilities, enabling organizations to implement robust protective measures. This document serves as a critical tool for IT and security teams to enhance cloud security posture and ensure regulatory compliance.
Cloud Storage Threat Analysis Document Example
A
Cloud Storage Threat Analysis Document example provides a detailed assessment of potential security risks associated with cloud storage solutions. It identifies vulnerabilities, threat sources, and attack vectors specific to cloud environments, helping organizations implement appropriate safeguards. This document is essential for understanding and mitigating risks in cloud data storage infrastructures.
Cloud Infrastructure Vulnerability Assessment Format
A
Cloud Infrastructure Vulnerability Assessment Format document systematically outlines the process and criteria for identifying security weaknesses within cloud environments. It provides a standardized framework for scanning, categorizing, and reporting vulnerabilities across various cloud components such as virtual machines, containers, and network configurations. This document ensures consistent evaluation and prioritization of risks to enhance cloud security posture and compliance efforts.
Cloud Storage Penetration Testing Report Sample
A
Cloud Storage Penetration Testing Report Sample document provides a detailed analysis of security vulnerabilities found during penetration testing of cloud storage systems. It outlines identified risks, exploited weaknesses, and recommended mitigation strategies to enhance data protection and prevent unauthorized access. This report serves as a crucial tool for organizations to understand their cloud storage security posture and comply with industry standards.
Cloud Storage Risk Mitigation Assessment Template
The
Cloud Storage Risk Mitigation Assessment Template document is designed to systematically identify, evaluate, and address potential risks associated with cloud storage solutions. It provides structured criteria and checkpoints to ensure data security, compliance, and resilience against threats such as data breaches, unauthorized access, and service downtime. This template supports organizations in implementing effective controls and maintaining robust cloud storage governance.
Cloud Data Access Control Evaluation Document
A
Cloud Data Access Control Evaluation Document outlines the framework and criteria used to assess how effectively access to cloud-stored data is managed and secured. It details the various access control policies, authentication mechanisms, and permission levels applied to protect sensitive information from unauthorized use. This document is essential for ensuring compliance with data protection regulations and maintaining robust security standards in cloud environments.
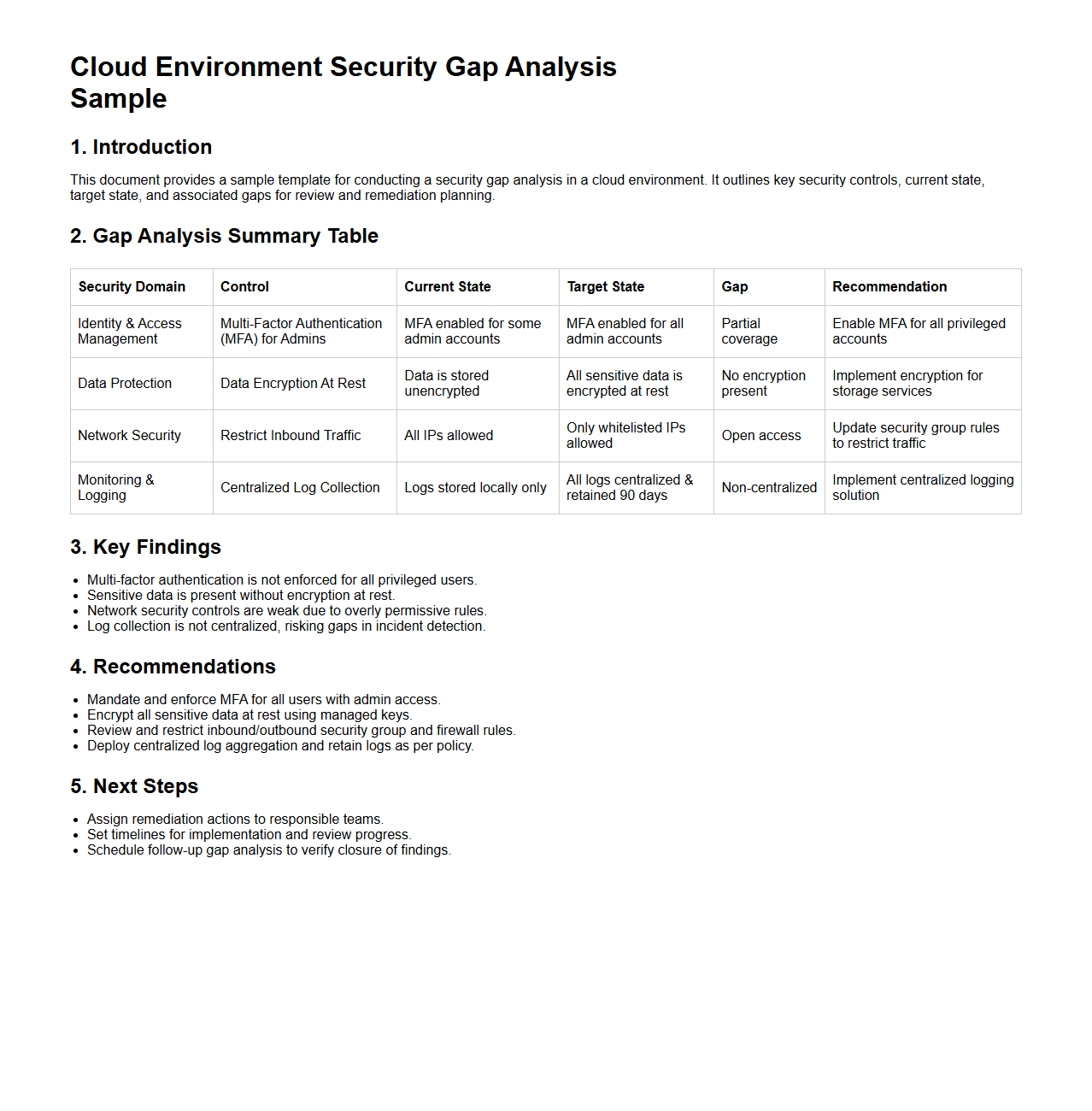
Cloud Environment Security Gap Analysis Sample
A
Cloud Environment Security Gap Analysis Sample document identifies vulnerabilities and assesses compliance against established cloud security standards and best practices. It provides a structured framework to compare current security controls with desired security postures, helping organizations pinpoint weaknesses in identity management, data protection, and network security. This sample serves as a practical template for organizations to systematically evaluate and enhance their cloud security strategies.
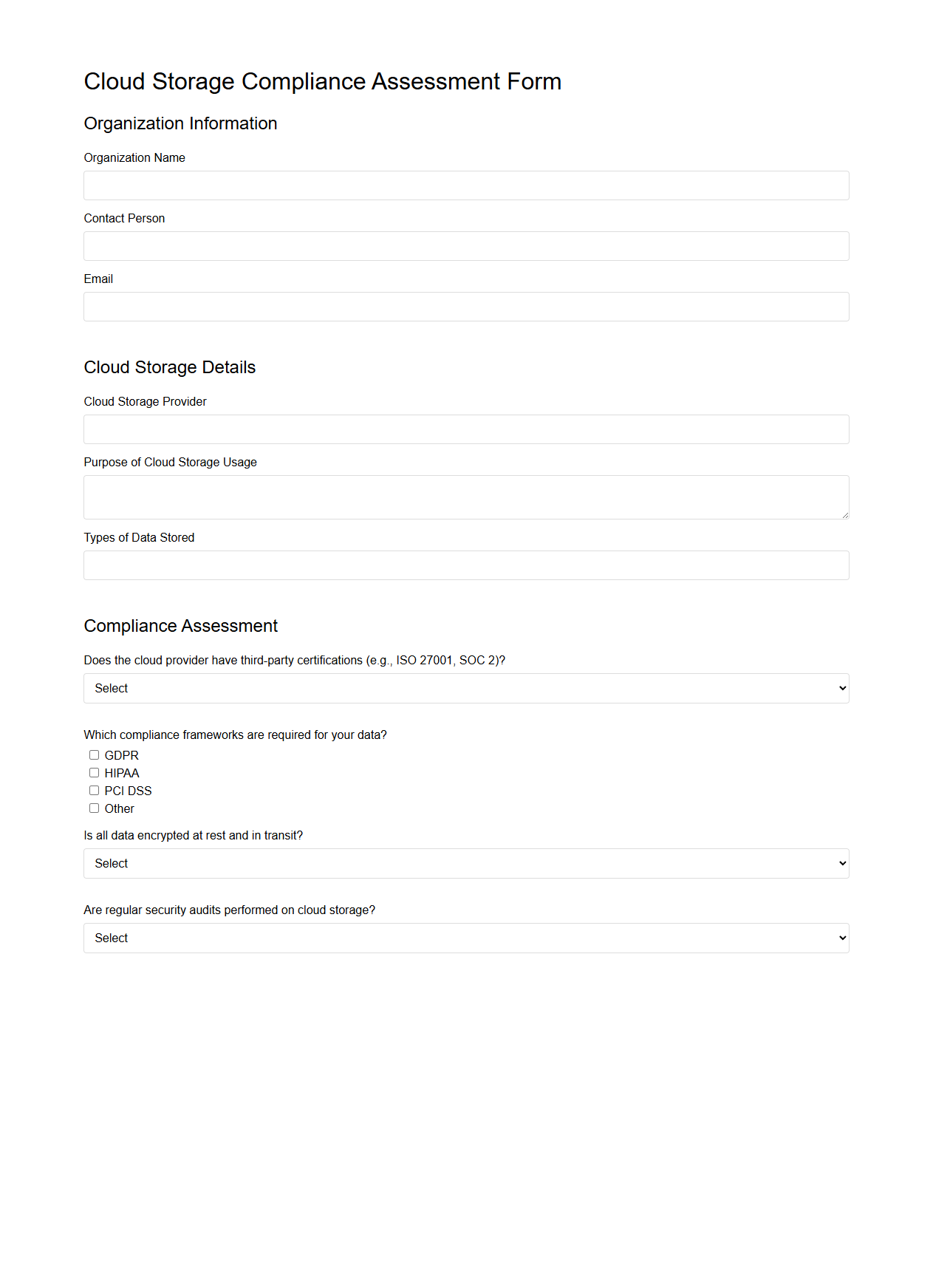
Cloud Storage Compliance Assessment Form
The
Cloud Storage Compliance Assessment Form document evaluates how cloud storage solutions adhere to regulatory standards and organizational policies. It systematically captures data on security controls, data privacy measures, and risk management practices to ensure compliance with laws such as GDPR, HIPAA, or SOC 2. This form aids organizations in identifying gaps and implementing corrective actions to maintain secure and compliant cloud storage environments.
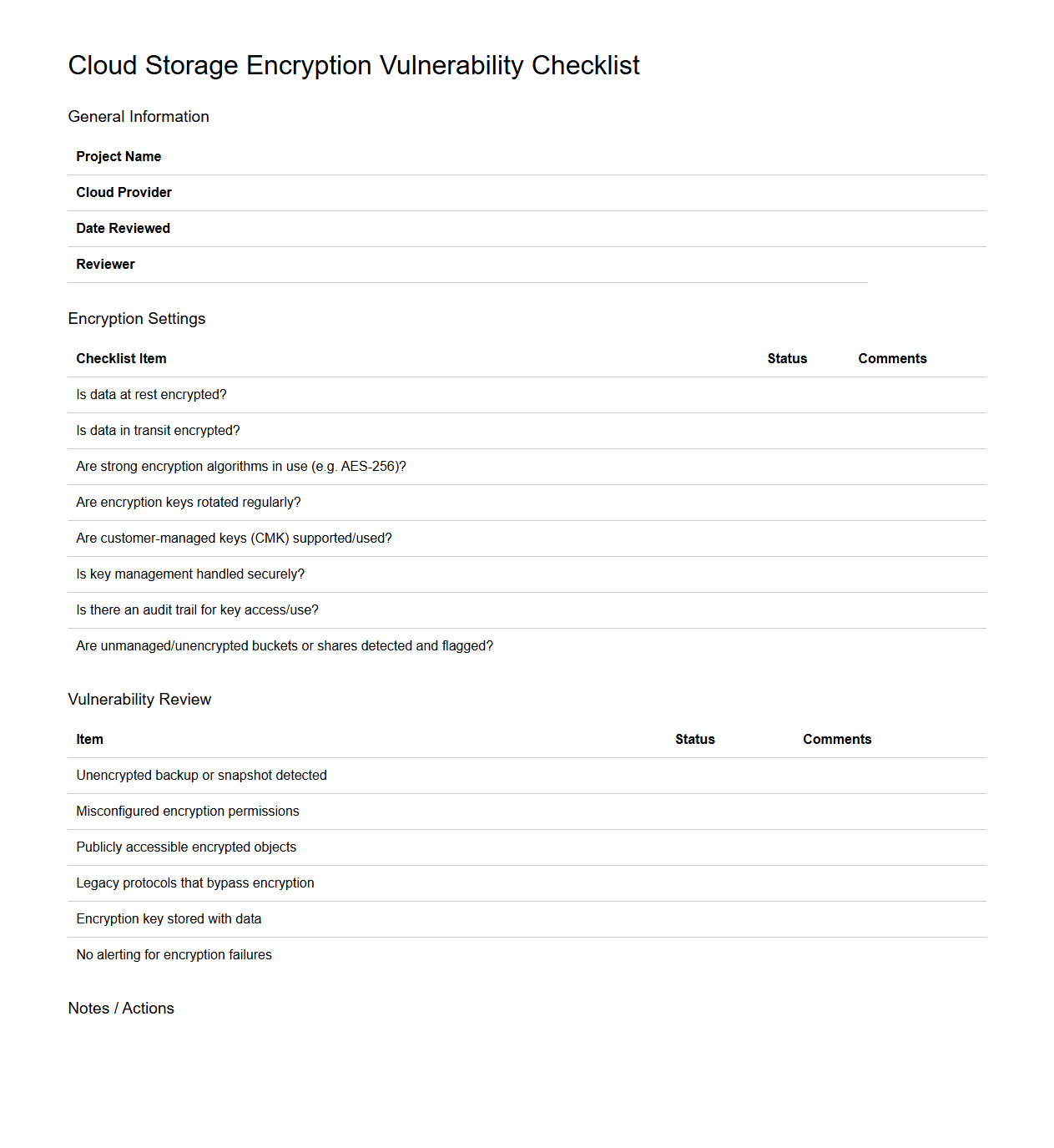
Cloud Storage Encryption Vulnerability Checklist
The
Cloud Storage Encryption Vulnerability Checklist document serves as a comprehensive guide to identifying and mitigating security risks associated with cloud storage encryption practices. It outlines critical assessment criteria for encryption algorithms, key management protocols, and access control mechanisms to ensure data confidentiality and integrity. Organizations utilize this checklist to enhance their cloud security posture by systematically addressing potential vulnerabilities in their encryption implementations.
What encryption protocols are specified in the vulnerability assessment document for cloud storage?
The vulnerability assessment document specifies the use of AES-256 encryption as the primary protocol for securing data at rest in cloud storage. Additionally, it mandates TLS 1.2 or higher for encrypting data in transit to safeguard against interception. These protocols ensure robust protection against unauthorized access and data breaches.
How does the document address multi-tenant data isolation risks?
The document highlights strict logical isolation mechanisms to prevent data leakage between tenants in a multi-tenant environment. It enforces the use of access control policies and tenant-specific encryption keys to ensure data privacy. Regular audits are recommended to verify the effectiveness of these isolation controls.
What are the documented remediation steps for identified storage misconfigurations?
Remediation steps include immediate reconfiguration of access permissions to align with the principle of least privilege. The assessment advises enabling encryption for all storage buckets and removing public access where unnecessary. Continuous monitoring is emphasized to detect and correct any future misconfigurations promptly.
How is third-party access to cloud storage assessed and documented?
The assessment document requires a thorough review of third-party access policies, including the scope and legitimacy of permissions granted. It mandates documentation of all third-party accounts and their associated access levels for accountability. Periodic re-evaluation of third-party access ensures ongoing compliance with security standards.
Does the vulnerability assessment detail versioning and audit logging practices for stored documents?
Yes, the document specifies the implementation of versioning controls to maintain historical copies of stored documents for recovery purposes. It also requires detailed audit logging to track access and modifications, which supports forensic investigations. These practices are critical for maintaining data integrity and regulatory compliance.
More Technology Templates