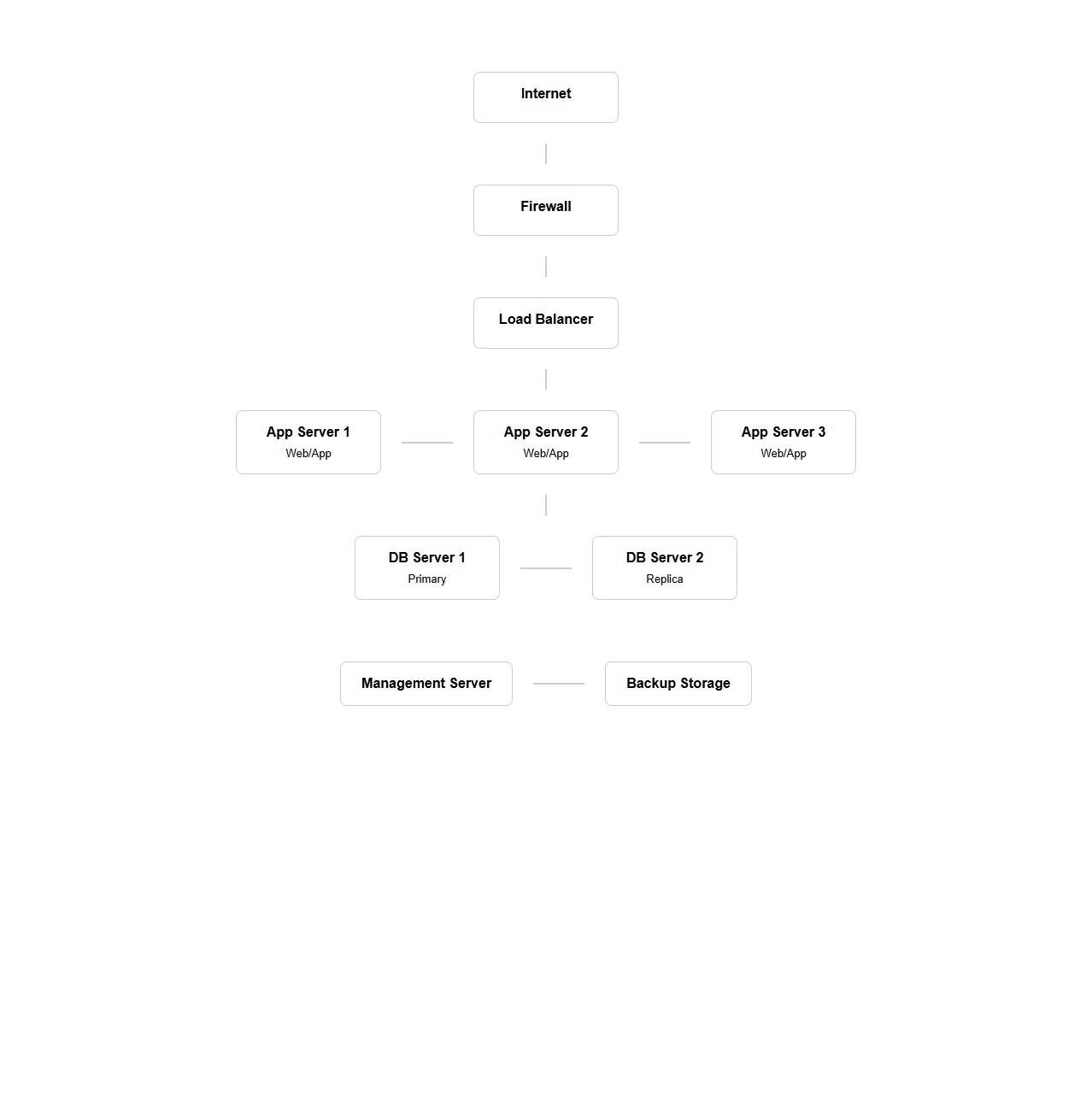
Network Topology Diagram Template for Enterprise Systems
A
Network Topology Diagram Template for Enterprise Systems document visually represents the arrangement and connection of various network components within a large-scale business infrastructure. It outlines the layout of devices such as routers, switches, servers, and workstations, providing a clear map for network design, troubleshooting, and optimization. This template standardizes documentation, improving communication among IT teams and supporting efficient network management across the enterprise.
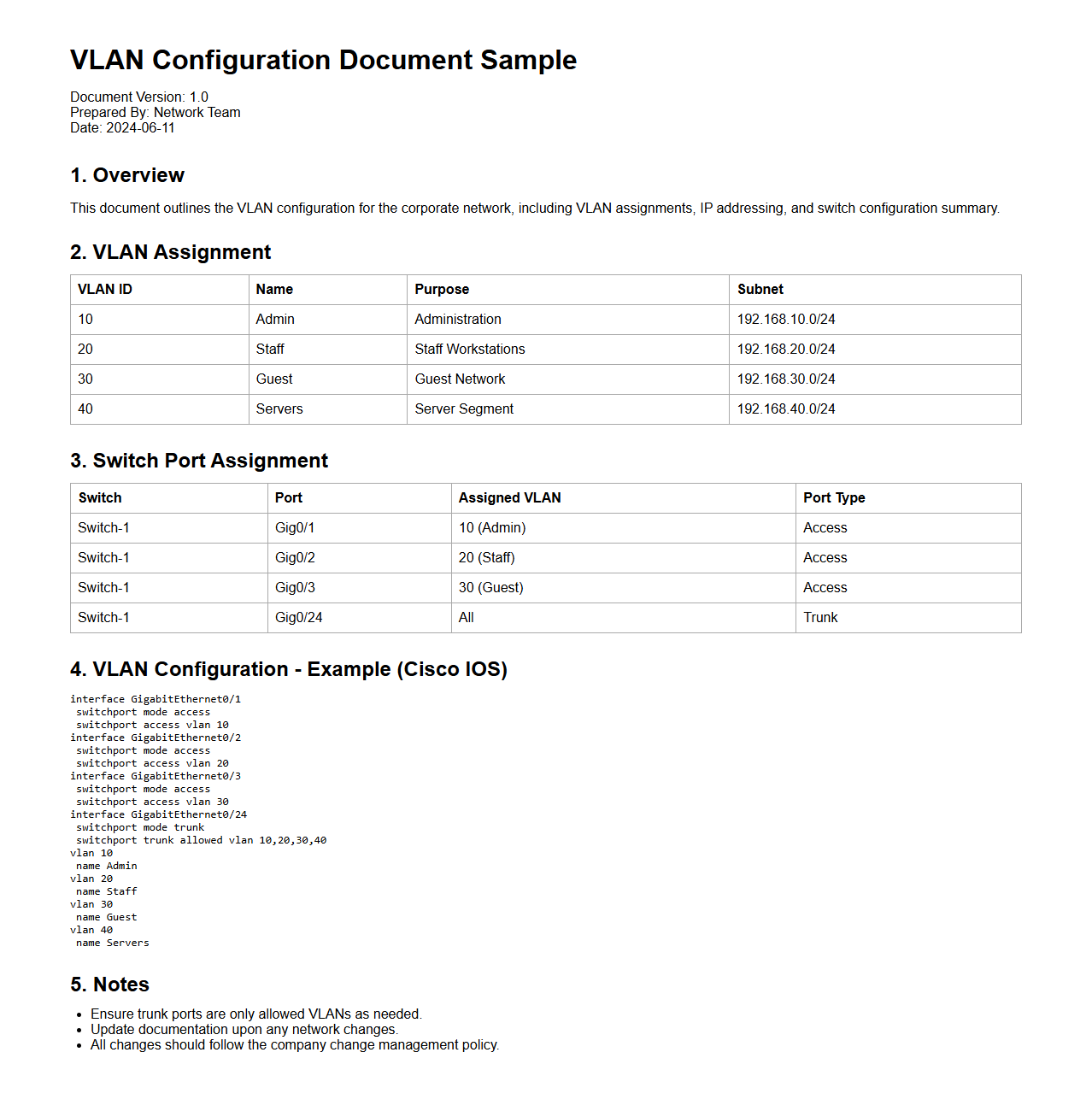
VLAN Configuration Document Sample for Corporate Networks
A
VLAN Configuration Document Sample for Corporate Networks serves as a comprehensive guide detailing the setup and management of Virtual Local Area Networks within an organization. It includes essential parameters such as VLAN IDs, port assignments, IP subnetting, and security policies to ensure efficient network segmentation and enhanced performance. This document aids IT teams in maintaining consistent network configurations, troubleshooting connectivity issues, and enforcing access controls across various departments.
IP Address Management Worksheet for Enterprise IT
An
IP Address Management Worksheet for Enterprise IT is a structured document used to systematically record, track, and organize IP address allocations across complex network environments. It facilitates efficient management of IP resources by documenting subnet ranges, device assignments, and usage status, helping to prevent address conflicts and optimize address space utilization. This worksheet supports network administrators in maintaining accurate IP inventories, ensuring scalability, and enhancing overall network reliability.
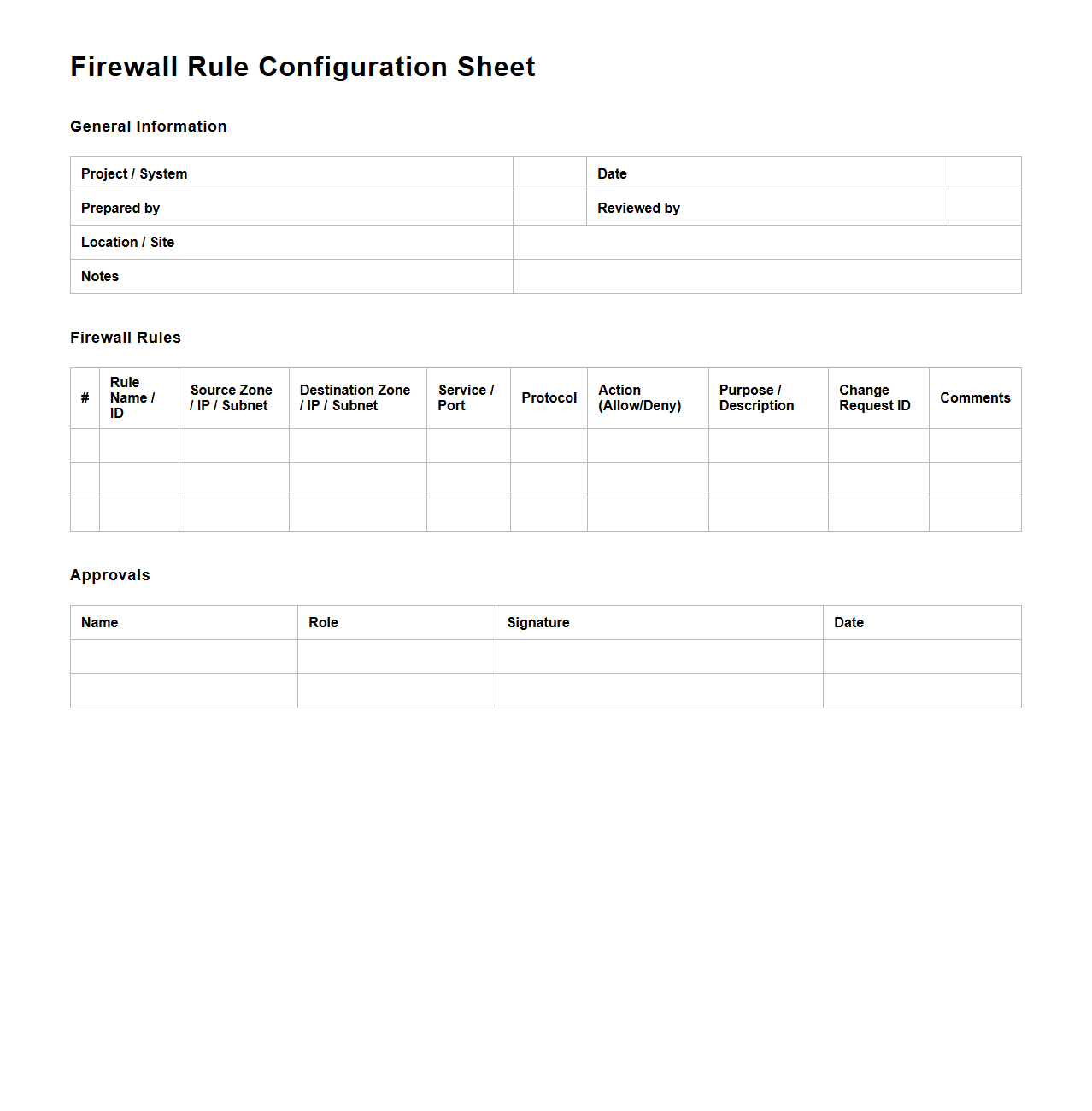
Firewall Rule Configuration Sheet for Large Organizations
The
Firewall Rule Configuration Sheet for large organizations is a comprehensive document that details the specific firewall rules applied across the network to control traffic and enhance security. It specifies rule identifiers, source and destination IP addresses, ports, protocols, and action settings to ensure consistent and auditable firewall policies. This document serves as an essential reference for network security teams to manage, review, and update firewall configurations effectively, minimizing risks and ensuring compliance with organizational security standards.
Switch Configuration Script Example for Enterprise Networks
The
Switch Configuration Script Example for Enterprise Networks document provides a detailed template for automating the setup and management of network switches within large-scale business environments. It includes standardized commands and best practices to ensure consistent, secure, and efficient network performance across multiple devices. This script helps network administrators streamline configuration tasks, minimize errors, and maintain optimal connectivity in complex enterprise infrastructures.
Wi-Fi Network Setup Documentation for Business Environments
Wi-Fi Network Setup Documentation for Business Environments outlines a comprehensive guide to designing, configuring, and securing wireless networks within corporate settings. It includes detailed information on access point placement, SSID configurations, encryption protocols like WPA3, and network segmentation to ensure optimal performance and data protection. This document serves as a critical resource for IT teams to maintain consistent
network reliability and security across all business locations.
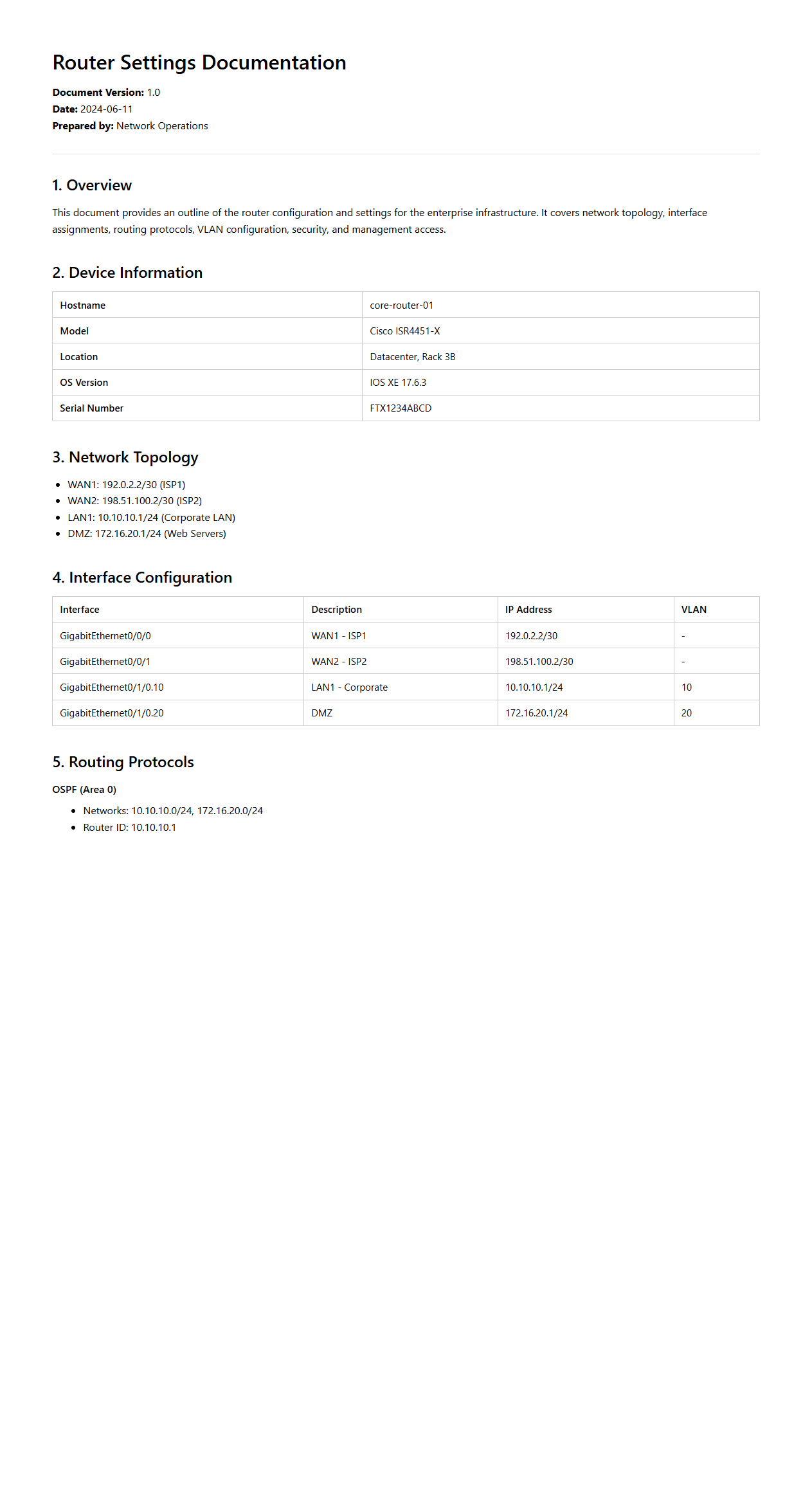
Router Settings Documentation for Enterprise Infrastructure
Router Settings Documentation for Enterprise Infrastructure is a comprehensive guide detailing the configuration parameters, protocols, and security policies necessary for managing routers within a corporate network. It includes specifics on IP addressing, routing protocols such as OSPF or BGP, VLAN configurations, and access control lists to ensure optimal performance and network security. This documentation serves as a critical resource for network administrators to maintain consistency, troubleshoot issues efficiently, and enforce compliance with organizational IT standards.
Device Inventory Sheet for Enterprise Network Assets
A
Device Inventory Sheet for Enterprise Network Assets is a comprehensive document that catalogs all hardware and software components within an organization's network infrastructure. It includes detailed information such as device types, serial numbers, IP addresses, locations, and ownership, enabling efficient asset management and troubleshooting. Maintaining this sheet supports network security, compliance audits, and lifecycle management of enterprise IT resources.
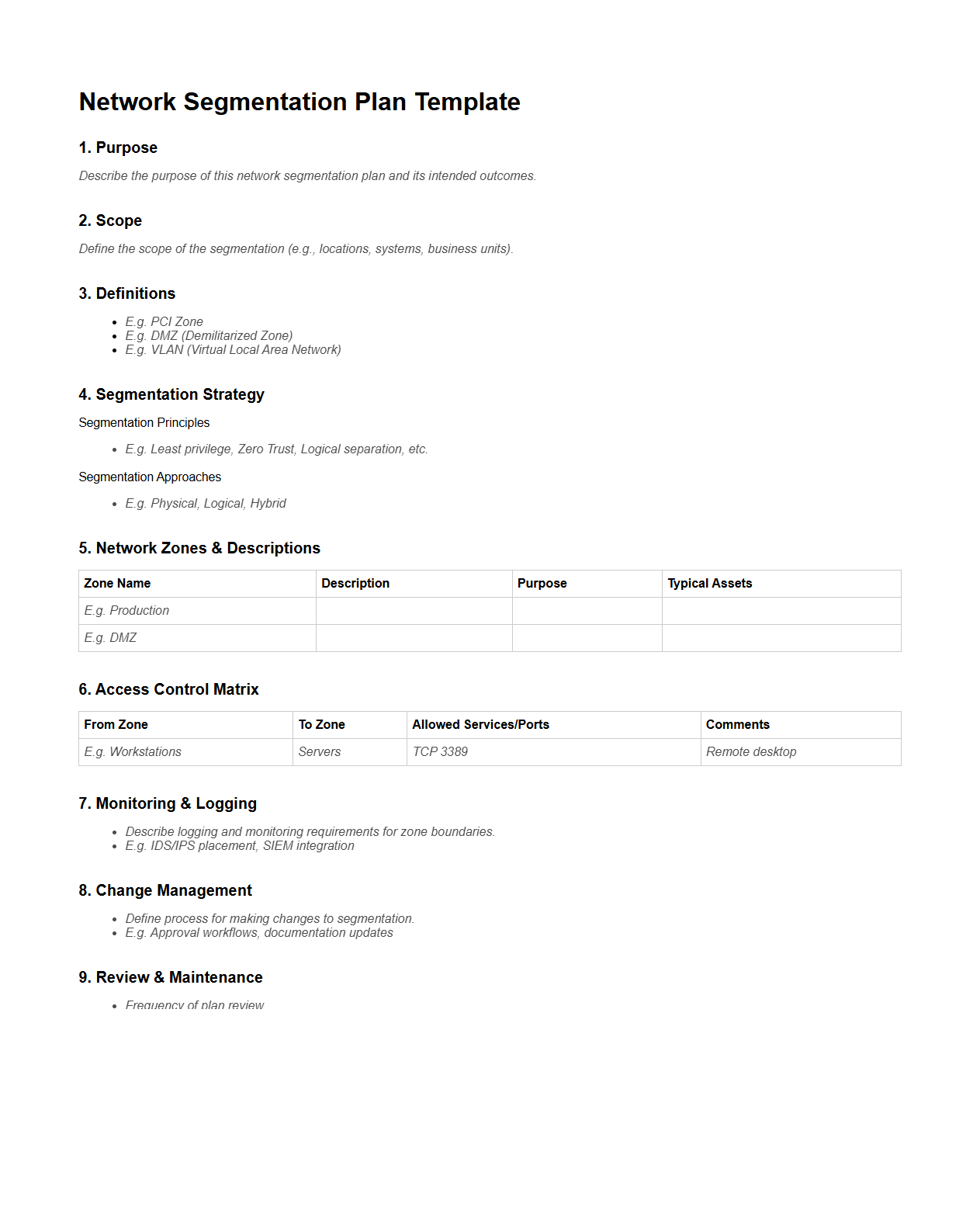
Network Segmentation Plan Template for Enterprises
A
Network Segmentation Plan Template for enterprises is a structured document designed to guide the division of a corporate network into distinct, secure segments. It outlines strategies for improved security, traffic management, and regulatory compliance by isolating sensitive data and systems from general network access. This template helps IT teams implement effective segmentation policies, reduce attack surfaces, and enhance overall network performance.
MPLS Configuration Record for Corporate Systems
The MPLS Configuration Record for Corporate Systems document details the setup and management of
MPLS (Multiprotocol Label Switching) within an enterprise network, ensuring efficient traffic routing and enhanced security. It includes configuration parameters, network topology, label distribution protocols, and device settings essential for maintaining seamless connectivity across corporate sites. This document serves as a critical reference for network administrators to troubleshoot, update, and optimize MPLS services in alignment with organizational requirements.
What protocols are standardized in the enterprise network configuration document?
The enterprise network configuration document standardizes protocols such as TCP/IP, HTTP/HTTPS, SNMP, and DNS. These protocols ensure consistent communication and management across all network devices. Adhering to these standards improves interoperability and enhances network stability.
How does the document address VLAN segmentation for system isolation?
The document specifies the use of VLAN segmentation to isolate different systems and departments for enhanced security. VLANs are configured to separate sensitive systems from general user traffic, minimizing the risk of unauthorized access. This segmentation supports efficient traffic management and reduces broadcast domain sizes.
Are backup and failover configurations detailed in the documentation?
The configuration document details both backup and failover strategies to ensure network resilience. It includes scheduled backup procedures and specifies failover protocols like VRRP or HSRP for critical network devices. These measures maintain network availability during hardware failures or outages.
What encryption standards are mandated for data in transit within the document?
The document mandates the use of strong encryption standards such as TLS 1.2/1.3 and IPsec for securing data in transit across the enterprise network. These protocols protect data confidentiality and integrity against interception and tampering. Enforcing these standards is vital for safeguarding sensitive information.
How are access controls and user authentication methods specified in the configuration document?
The network configuration document specifies strict access controls using role-based access control (RBAC) models and multi-factor authentication (MFA) for user verification. It outlines procedures for granting, reviewing, and revoking user permissions to maintain security integrity. These methods ensure only authorized personnel access network resources.