Legacy Data Migration Mapping Template
A
Legacy Data Migration Mapping Template document serves as a structured framework to accurately map data fields from an older legacy system to a new target system during data migration projects. It ensures data consistency, integrity, and alignment by detailing source-to-destination field relationships, transformation rules, and validation criteria. This template is essential for smooth transition and minimizing errors in complex data migration processes.
Data Extraction Plan Example for Legacy Systems
A
Data Extraction Plan Example for Legacy Systems document outlines the structured approach for retrieving data from outdated or obsolete IT systems. It details specific methods, tools, and steps to ensure accurate, efficient extraction while preserving data integrity and minimizing system disruption. This plan is essential for successful data migration, integration, or modernization projects involving legacy databases.
Source-to-Target Field Mapping Matrix
A
Source-to-Target Field Mapping Matrix document is a critical tool in data migration and integration projects that outlines the correlation between source data fields and their corresponding target system fields. It details the transformation rules, data types, and validation criteria necessary to ensure accurate and consistent data transfer. This mapping matrix serves as a blueprint for developers and analysts to facilitate seamless data mapping and minimize errors during migration.
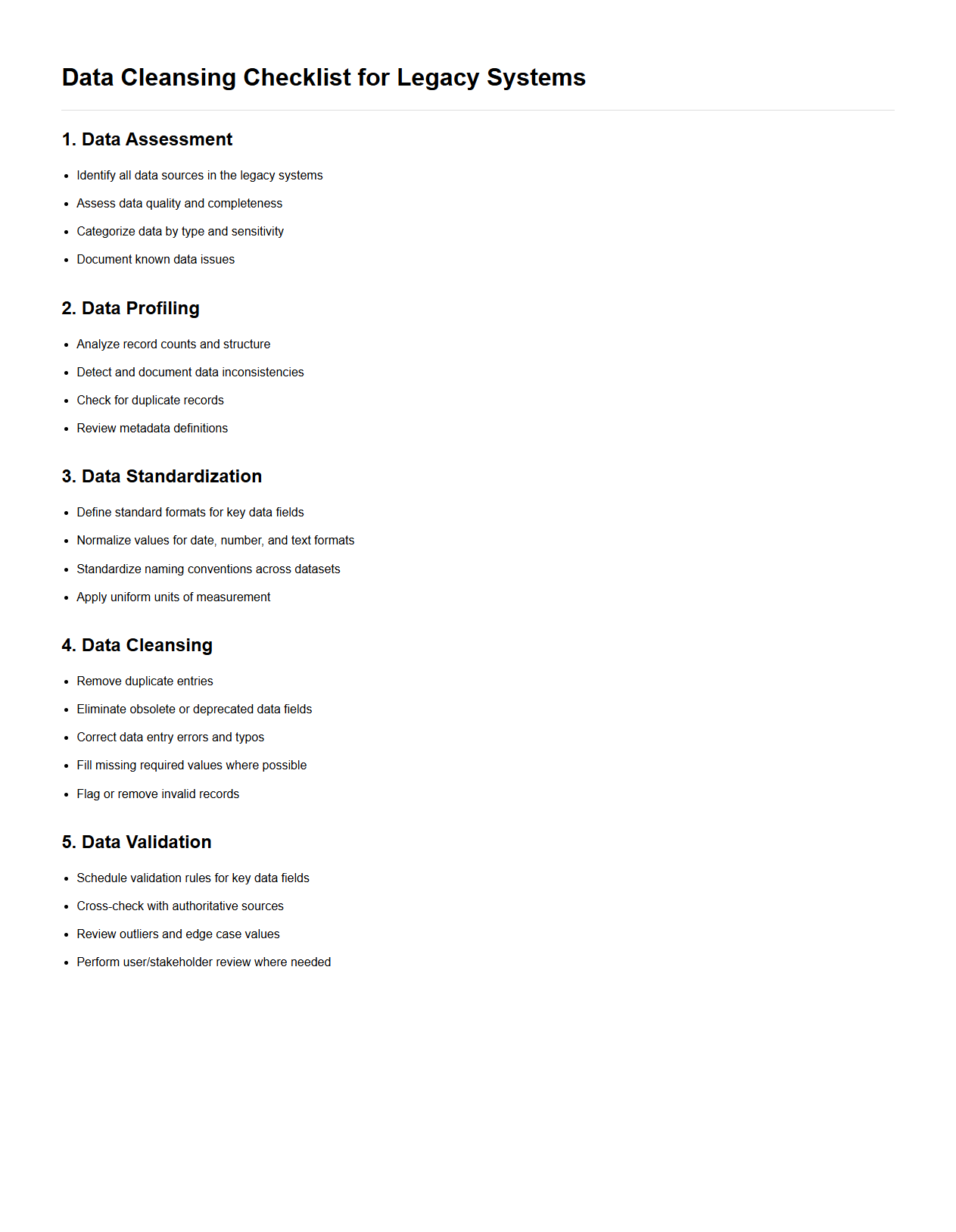
Data Cleansing Checklist for Legacy Systems
The
Data Cleansing Checklist for Legacy Systems document outlines a structured approach to identify, validate, and correct inaccuracies within outdated data repositories. It focuses on essential tasks such as detecting duplicate records, standardizing data formats, and ensuring compliance with current data quality standards. This checklist helps organizations enhance data reliability and improve system integration efficiency by addressing legacy data challenges systematically.
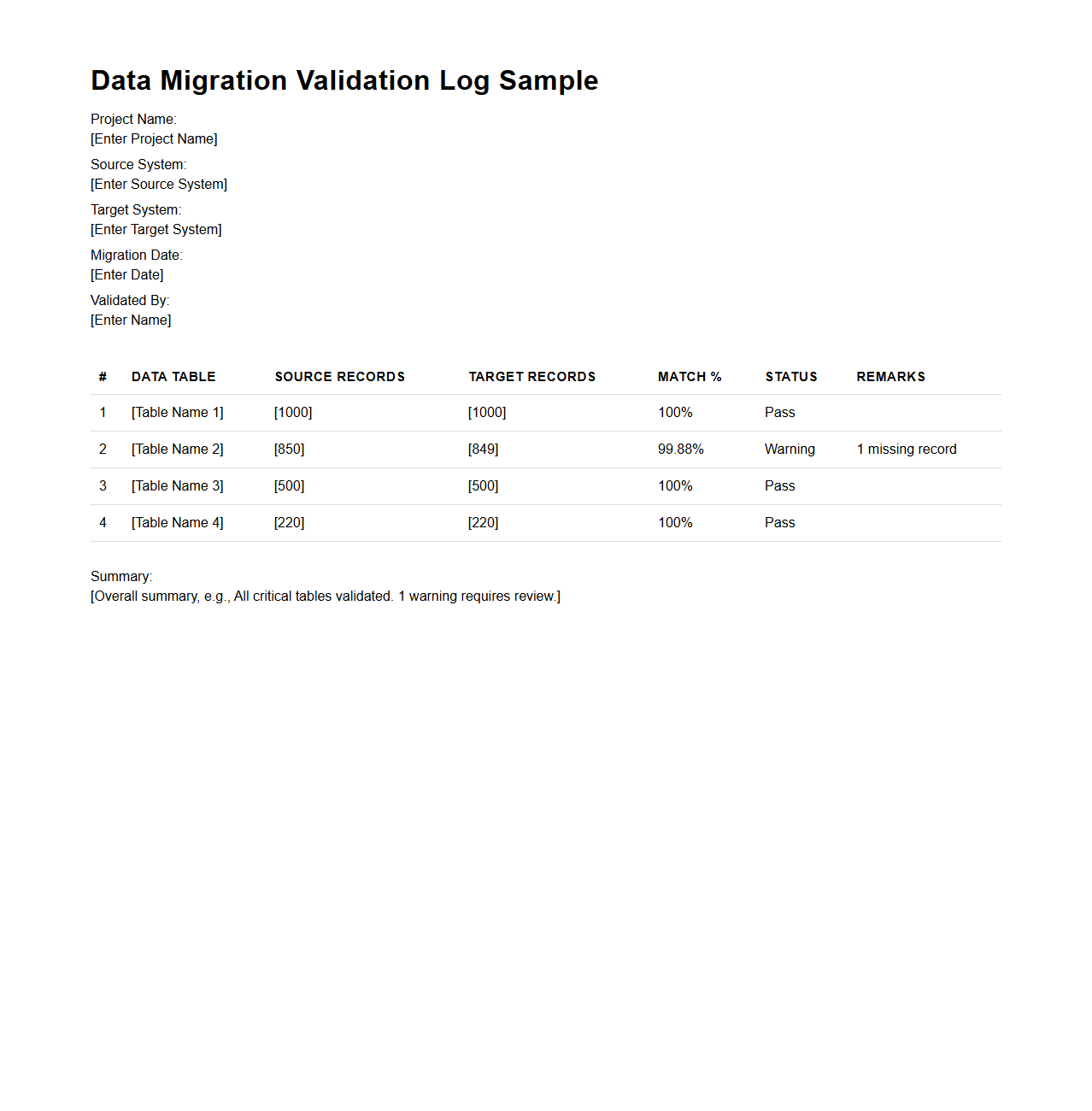
Data Migration Validation Log Sample
The
Data Migration Validation Log Sample document captures detailed records of data verification steps during the migration process, ensuring accuracy and completeness. It includes information on data sources, validation criteria, discrepancies identified, and resolution status to maintain data integrity. This log acts as a critical tool for auditing and troubleshooting migration projects.
Legacy Database Inventory Sheet
A
Legacy Database Inventory Sheet document serves as a comprehensive record of all existing legacy databases within an organization, detailing their structure, storage locations, and associated metadata. It facilitates efficient management, migration planning, and risk assessment by providing critical insights into outdated systems that may require modernization or integration. Maintaining this inventory ensures data consistency, compliance, and informed decision-making during technology upgrades or system consolidations.
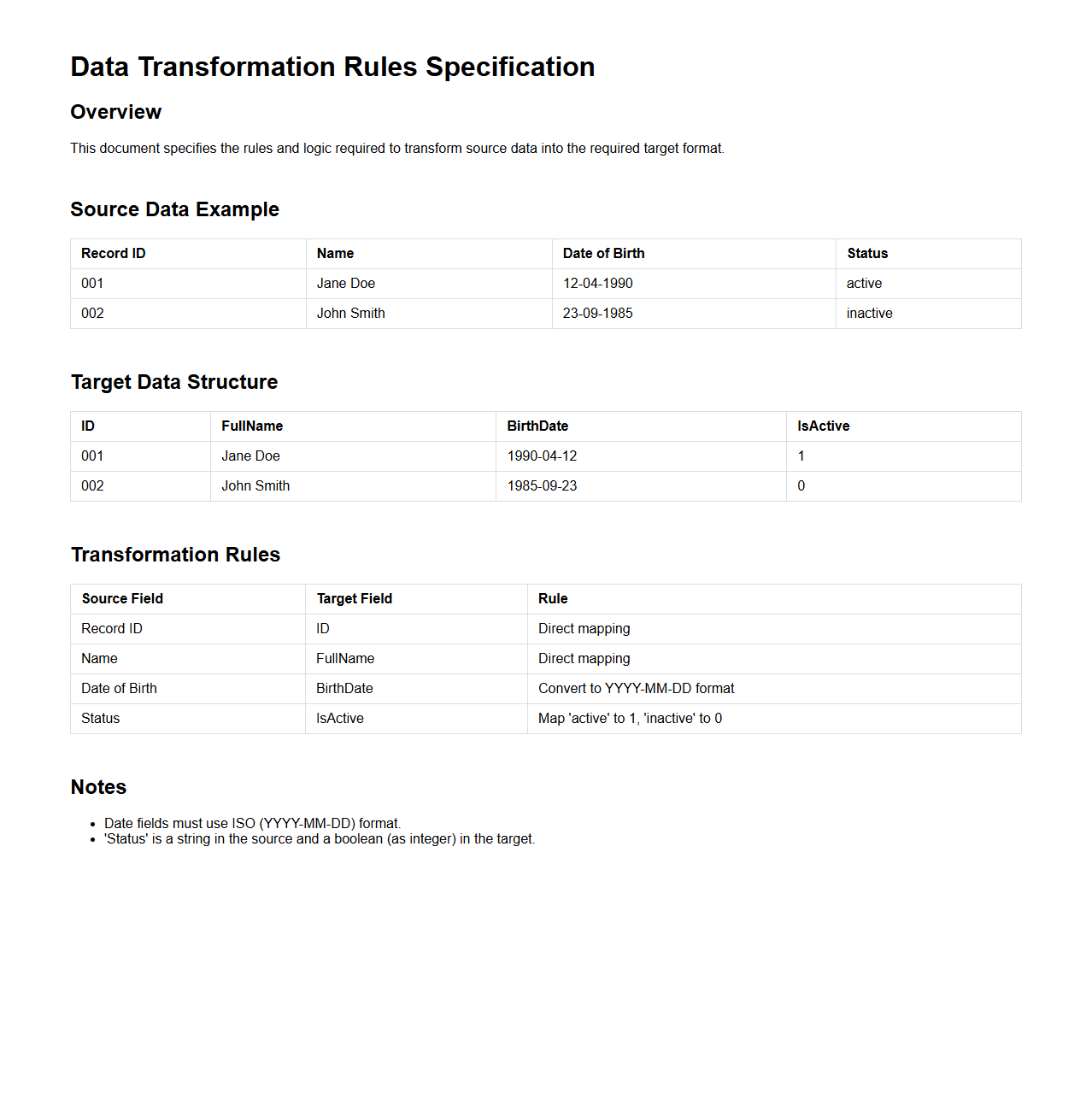
Data Transformation Rules Specification
A
Data Transformation Rules Specification document outlines detailed guidelines and criteria for converting source data into a target format, ensuring consistency and accuracy across systems. It defines mapping rules, data cleansing procedures, validation criteria, and transformation logic to maintain data integrity during migration or integration processes. This document serves as a critical reference for developers and data engineers to implement precise data transformations aligned with business requirements.
Migration Cutover Plan Outline
A
Migration Cutover Plan Outline document serves as a strategic roadmap detailing the step-by-step process for transitioning systems, data, and users from a legacy environment to a new platform with minimal disruption. It includes critical elements such as timelines, resource allocation, risk management, backup procedures, fallback strategies, and communication plans to ensure a smooth and efficient cutover. This document is essential for coordinating technical teams and stakeholders, reducing downtime, and ensuring data integrity throughout the migration process.
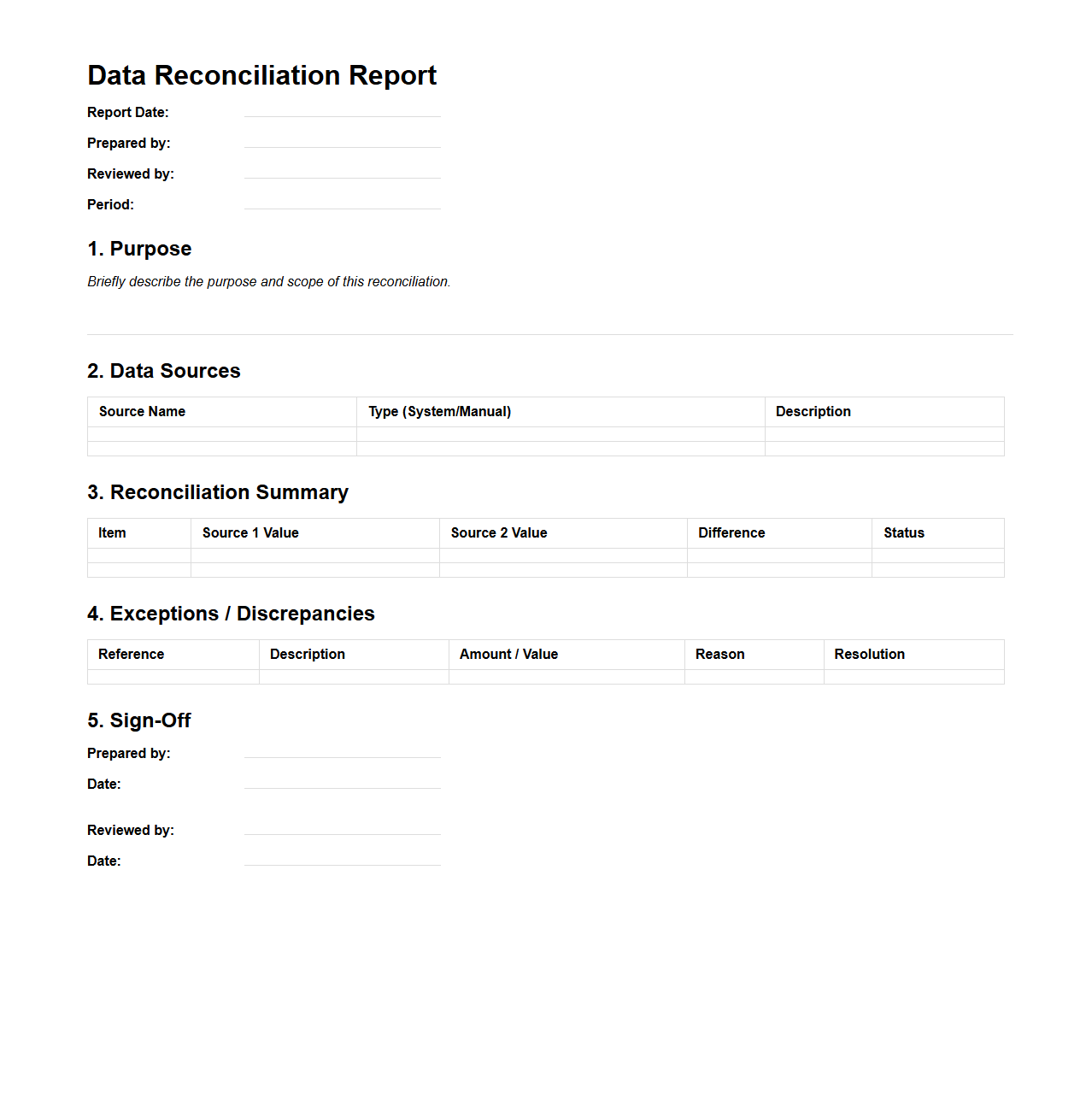
Data Reconciliation Report Template
A
Data Reconciliation Report Template document serves as a structured framework to compare and verify data sets from multiple sources, ensuring accuracy and consistency. It streamlines the identification of discrepancies, facilitating error correction and improving data integrity across financial, operational, or transactional records. This template enhances decision-making by providing clear, organized insights into data alignment and variance analysis.
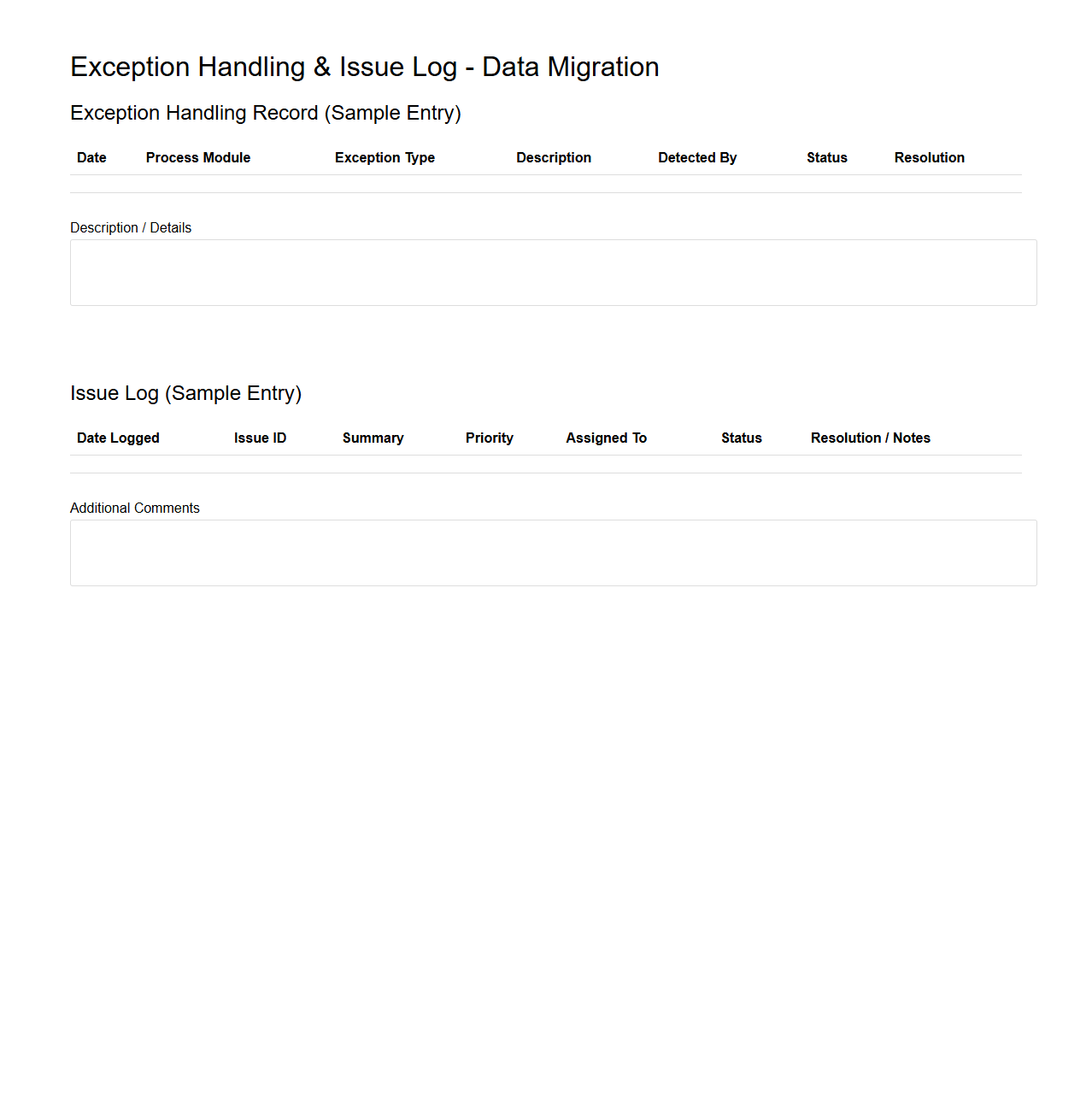
Exception Handling and Issue Log for Data Migration
Exception Handling in a Data Migration document refers to the systematic process of identifying, managing, and resolving errors or anomalies that occur during the transfer of data between systems. An
Issue Log serves as a detailed record of all encountered problems, including their status, impact, and resolution steps, ensuring transparency and facilitating troubleshooting. Together, these components enhance the reliability and accuracy of the data migration process by providing structured mechanisms to address unexpected challenges.
What data integrity checks are outlined for the migration of legacy system records?
The migration process includes comprehensive data integrity checks to ensure accuracy and consistency of records. Validation steps verify record completeness and correctness after each migration phase. Additionally, checksum and hash comparisons are implemented to detect any data corruption during transfer.
How does the document address data mapping between legacy and target schemas?
The document provides a detailed data mapping strategy linking legacy fields to target schema attributes. Transformation rules and data type conversions are clearly defined to maintain data compatibility. It also includes examples of custom mappings to handle complex legacy structures seamlessly.
What rollback procedures are specified in case of data migration failure?
Rollback procedures involve automated backups taken before each migration batch to ensure quick restoration. In case of failure, the system triggers a defined rollback protocol that reverts changes to maintain data stability. Detailed logs assist in identifying failure points to prevent recurrence during subsequent attempts.
Are legacy data cleansing and deduplication processes detailed?
The document outlines a thorough data cleansing and deduplication process to improve data quality before migration. It specifies criteria for identifying duplicates and erroneous entries using algorithmic and rule-based techniques. Cleansing workflows include standardization, validation, and enrichment steps to enhance data usability.
How is user access and security managed during the migration phase?
User access is strictly controlled through role-based security policies to protect sensitive information. Temporary access privileges are granted only to authorized personnel involved in the migration. Additionally, all data transfers are encrypted, and audit trails are maintained to monitor access and activities.