A Incident Response Plan Document Sample for IT Infrastructure outlines the procedures and protocols to identify, manage, and resolve security incidents effectively within IT environments. This document includes detailed roles, communication strategies, and recovery steps to minimize downtime and data loss. It serves as a critical reference to ensure rapid and coordinated actions during cyber threats or system disruptions.
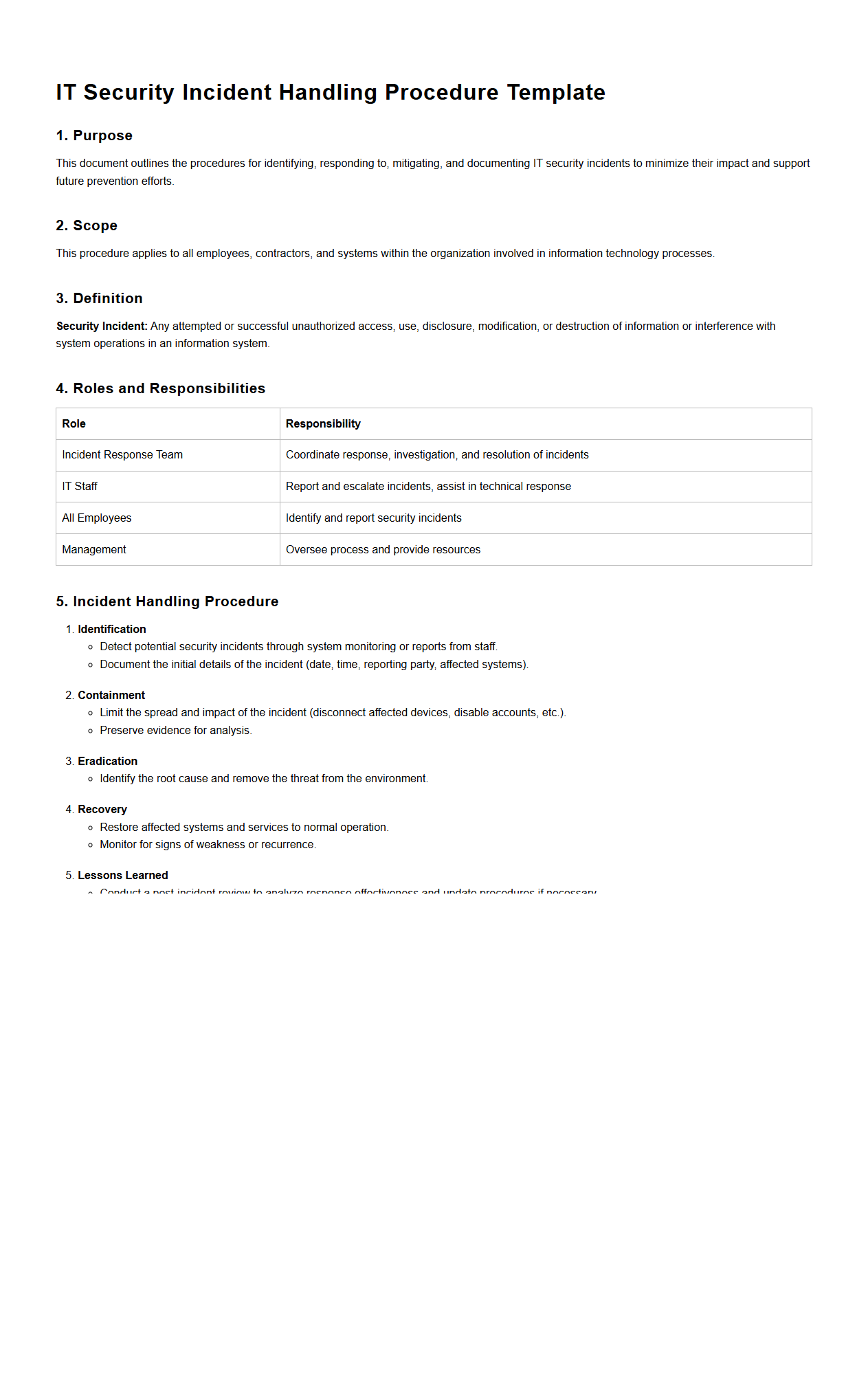
IT Security Incident Handling Procedure Template
The
IT Security Incident Handling Procedure Template document provides a structured framework for identifying, managing, and resolving security incidents within an organization. It includes predefined steps for incident detection, reporting, assessment, containment, eradication, recovery, and post-incident analysis to minimize damage and prevent recurrence. This template ensures consistent response protocols, compliance with regulatory requirements, and effective communication among IT security teams and stakeholders.
Cybersecurity Breach Response Plan Example
A
Cybersecurity Breach Response Plan Example document outlines a structured approach for organizations to detect, respond to, and recover from security incidents. It includes predefined roles, communication protocols, and step-by-step actions to minimize damage and ensure regulatory compliance. This example serves as a practical guide to prepare teams for managing data breaches effectively.
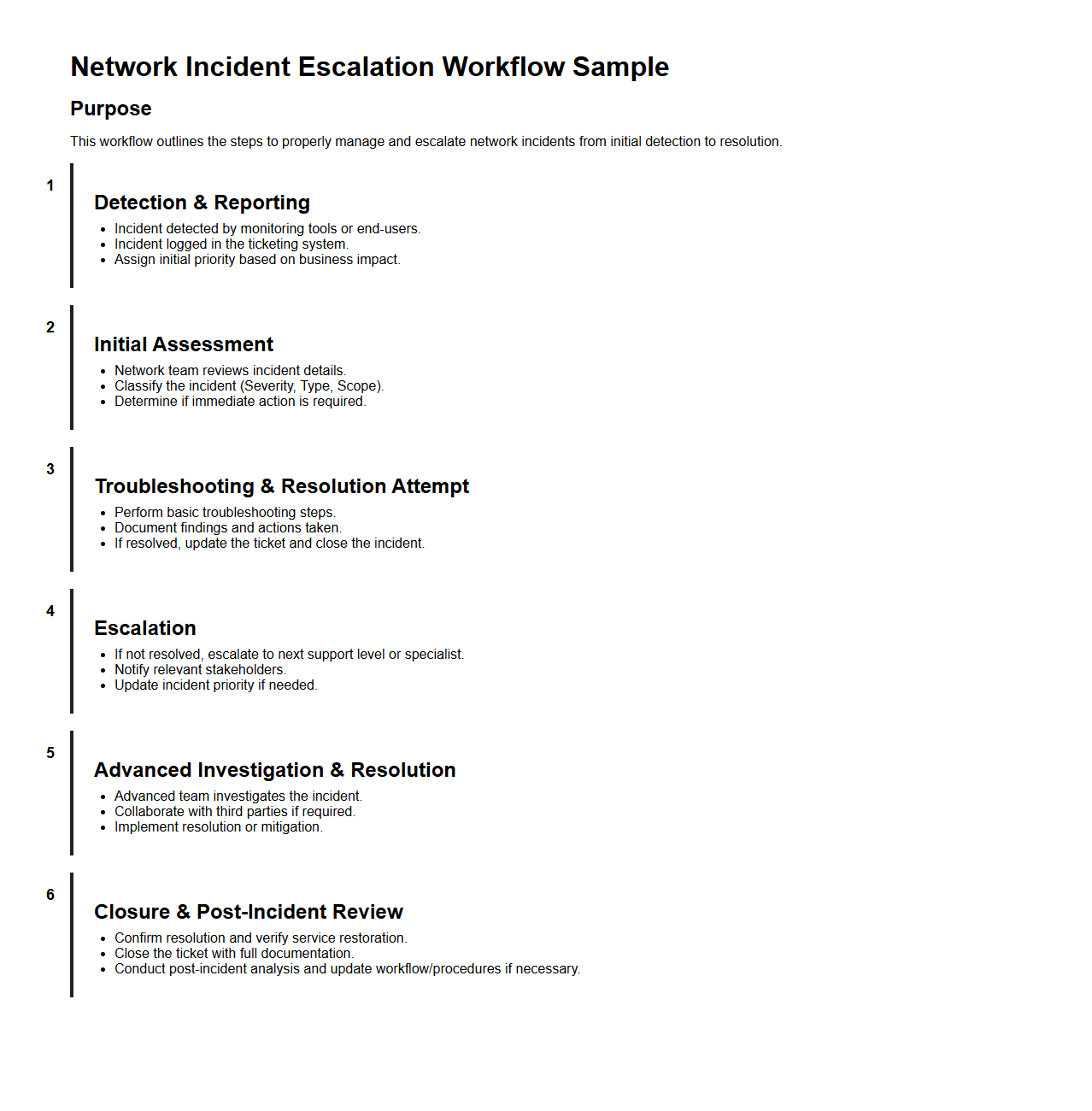
Network Incident Escalation Workflow Sample
The
Network Incident Escalation Workflow Sample document outlines a structured process for managing and escalating network-related issues efficiently. It defines specific roles, escalation paths, and response times to ensure timely resolution and minimize downtime. This workflow helps IT teams maintain service continuity by promoting clear communication and accountability during network incidents.
Data Loss Incident Management Plan Outline
A
Data Loss Incident Management Plan Outline document provides a structured framework for identifying, responding to, and mitigating data loss incidents within an organization. It details step-by-step procedures for incident detection, containment, recovery, and notification to ensure data integrity and compliance with legal regulations. This document serves as a critical guide for IT teams and stakeholders to minimize the impact of data breaches and restore normal operations efficiently.
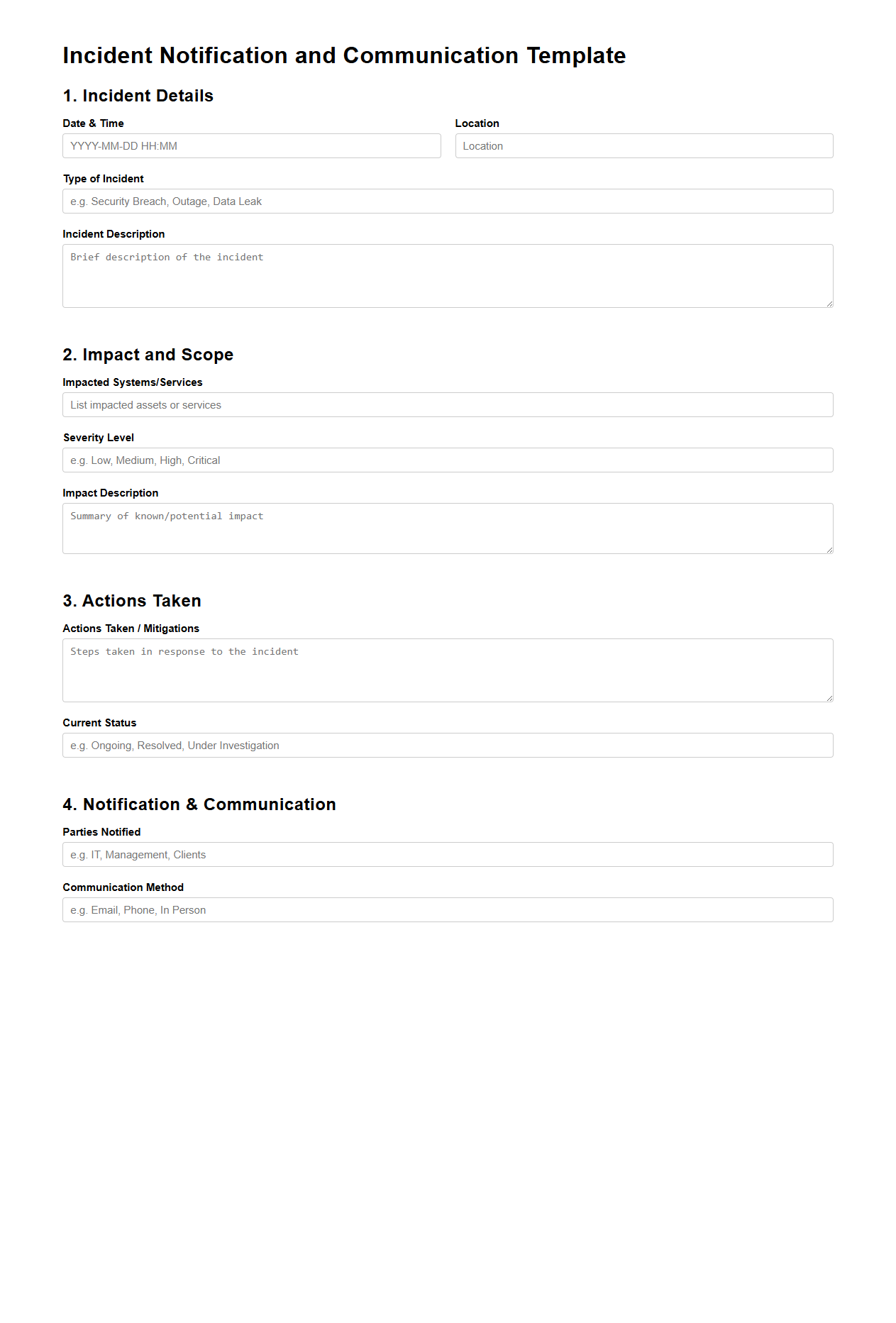
Incident Notification and Communication Template
An
Incident Notification and Communication Template document provides a structured format for reporting and communicating details of an incident promptly and clearly to all relevant stakeholders. It ensures consistent and efficient information dissemination, including the nature of the incident, impact assessment, response actions, and follow-up procedures. This template supports effective crisis management by facilitating timely updates and minimizing miscommunication during critical events.
Critical Infrastructure Threat Response Checklist
The
Critical Infrastructure Threat Response Checklist document serves as a comprehensive guide to identify, assess, and respond to potential threats targeting essential systems such as energy grids, water supply networks, and transportation hubs. It outlines specific protocols and action items designed to enhance preparedness, ensure rapid coordination among stakeholders, and minimize disruptions to vital services. By following this checklist, organizations can systematically manage risks and maintain operational continuity during security incidents.
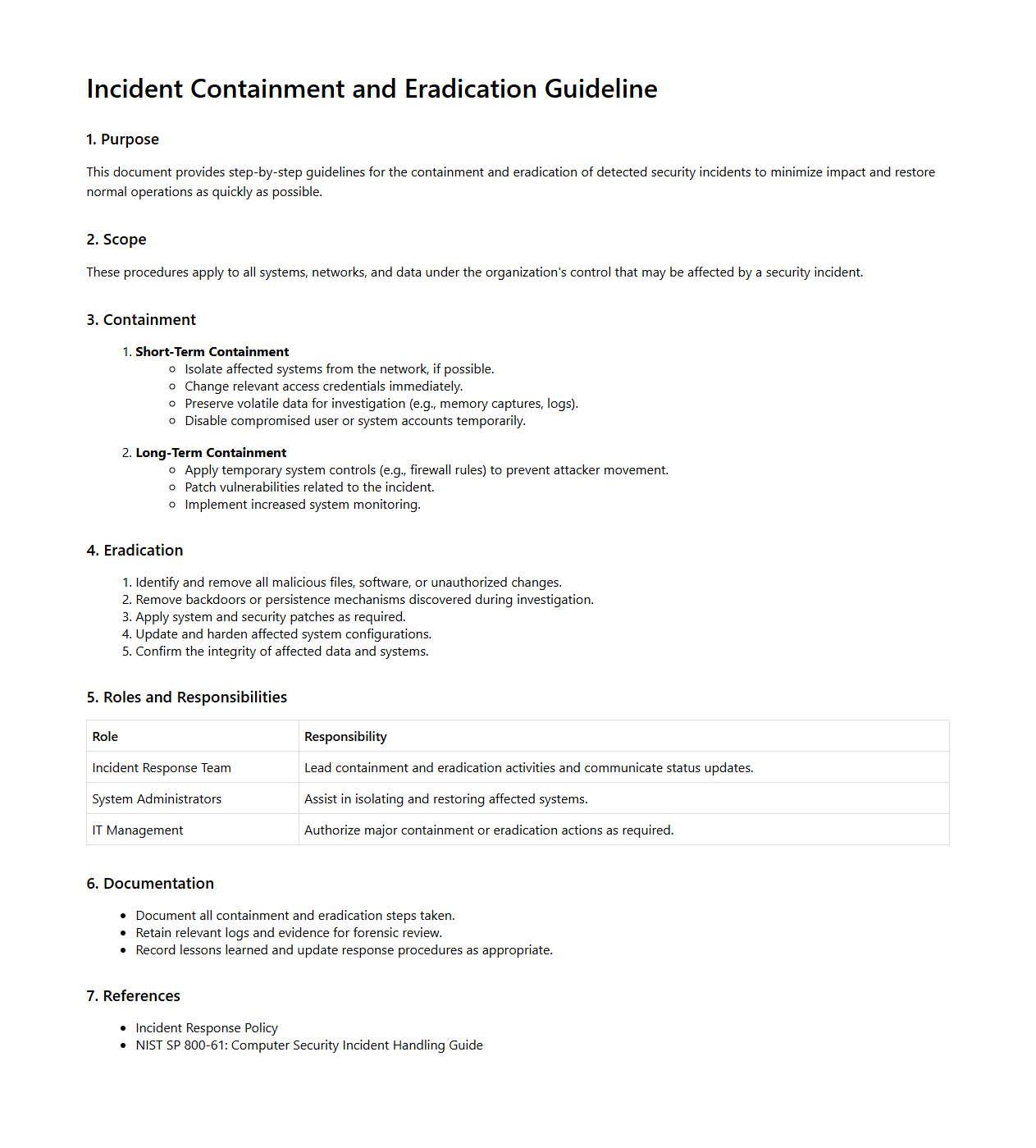
Incident Containment and Eradication Guideline
The
Incident Containment and Eradication Guideline document provides a structured approach to quickly identify, isolate, and remove threats from affected systems to minimize damage during a cybersecurity incident. It outlines best practices and step-by-step procedures for security teams to effectively contain breaches, eradicate malicious artifacts, and restore normal operations securely. This guideline ensures a consistent and efficient response to incidents, reducing downtime and preventing further exploitation.
Post-Incident Review and Reporting Framework
The
Post-Incident Review and Reporting Framework document outlines a structured approach to analyzing incidents, capturing lessons learned, and ensuring accountability within an organization. It defines the processes for documenting incident details, evaluating response effectiveness, and identifying opportunities for improvement to enhance future resilience. This framework supports continuous improvement by promoting transparency, collaboration, and systematic follow-up after any operational disruption.
Incident Roles and Responsibilities Matrix
The
Incident Roles and Responsibilities Matrix document clearly defines specific duties and accountabilities during an incident response to ensure efficient coordination and communication. It assigns precise roles to team members, specifying tasks such as incident detection, escalation, containment, mitigation, and recovery. This structured approach helps organizations minimize response times and improve overall incident management effectiveness.
IT Forensic Evidence Collection Procedure Sample
The
IT Forensic Evidence Collection Procedure Sample document outlines standardized methods for securely gathering digital evidence to maintain its integrity and admissibility in legal or investigative processes. It provides detailed steps on identifying, preserving, documenting, and transporting electronic data from various devices and networks while ensuring compliance with legal and organizational policies. This sample serves as a critical resource for IT professionals and forensic analysts to follow best practices in evidence handling and chain of custody management.
What processes are outlined for escalating unclassified security incidents within the Incident Response Plan Document?
The Incident Response Plan Document outlines a structured escalation process for unclassified security incidents, beginning with immediate incident detection and logging. The plan requires initial assessment by frontline IT personnel to determine the severity and potential impact. If necessary, incidents are escalated to higher-level response teams for further investigation and resolution.
How does the document address preservation and chain of custody for digital evidence during IT incidents?
The document emphasizes strict preservation protocols to maintain the integrity of digital evidence throughout the incident response lifecycle. It mandates detailed documentation and secure handling practices to ensure a clear chain of custody is established. This approach supports legal compliance and forensic accuracy during investigations.
What communication protocols are specified for informing external stakeholders in the event of a major infrastructure breach?
The Incident Response Plan specifies timely and transparent communication with external stakeholders, including regulators and affected parties. It defines authorized communication channels and designated spokespersons to ensure consistent and accurate information dissemination. Regular updates are mandated until the breach is fully resolved.
Which specific IT assets are prioritized for response and recovery according to the plan's asset classification?
The plan prioritizes critical IT assets based on their classification, focusing first on those essential to business continuity and security operations. High-value systems such as servers, databases, and network infrastructure receive immediate attention during incidents. This prioritization minimizes impact and accelerates recovery timelines.
How does the Incident Response Plan Document integrate lessons learned into future preventative strategies for IT infrastructure?
The document includes a formal review process to capture lessons learned after every incident, which informs continuous improvement efforts. Findings are analyzed to enhance policies, update training, and reinforce security controls. This iterative approach strengthens the organization's overall IT incident resilience.
More Technology Templates