LAN Topology Configuration Document Sample
A
LAN Topology Configuration Document Sample provides a detailed blueprint of how devices in a Local Area Network (LAN) are interconnected, including the arrangement of switches, routers, and access points. It outlines the physical and logical layout, IP addressing schemes, and connection protocols to ensure efficient network performance and management. This document serves as a crucial reference for network administrators to troubleshoot issues, plan expansions, and maintain optimal connectivity.
VLAN Assignment Document Sample
A
VLAN Assignment Document Sample is a template used to organize and record the allocation of Virtual Local Area Networks (VLANs) within a network infrastructure. It details VLAN IDs, corresponding departments or devices, IP subnet information, and port assignments to ensure proper network segmentation and traffic management. This document aids network administrators in maintaining clarity and consistency when configuring and troubleshooting VLANs.
Network Security Settings Document Sample
A
Network Security Settings Document Sample serves as a comprehensive template outlining the configuration parameters and security protocols essential for safeguarding network infrastructure. It details firewall rules, access control lists, encryption standards, and intrusion detection system configurations to ensure robust protection against cyber threats. This document aids organizations in standardizing security measures and facilitating compliance with regulatory requirements.
Wireless Network Setup Document Sample
A
Wireless Network Setup Document Sample provides a detailed template outlining the essential steps and configurations required to establish a secure and efficient wireless network. It includes key information such as network topology, SSID settings, security protocols like WPA3, IP addressing schemes, and device setup instructions. This document serves as a valuable reference for IT professionals to ensure consistent implementation and troubleshooting of wireless infrastructures.
IP Addressing Scheme Document Sample
An
IP Addressing Scheme Document Sample provides a structured template outlining the allocation and organization of IP addresses within a network. It details subnet divisions, VLAN assignments, and device IP allocations to ensure efficient network management and avoid address conflicts. This document serves as a critical reference for network engineers and administrators during network planning and troubleshooting.
Firewall Rule Configuration Document Sample
A
Firewall Rule Configuration Document Sample provides a standardized template outlining the specific rules and policies used to control network traffic through a firewall. It details criteria such as source and destination IP addresses, port numbers, protocols, and action types (allow, deny, drop) to ensure secure and efficient data flow. This sample document serves as a critical reference for IT administrators to consistently implement and review firewall settings, enhancing overall network security management.
Switch Port Configuration Document Sample
A
Switch Port Configuration Document sample document provides a detailed record of the settings and assignments for each port on a network switch, including VLAN IDs, port speeds, duplex modes, and security parameters. It serves as a vital reference for network administrators to ensure consistent configuration, troubleshoot connectivity issues, and maintain network performance. Having an organized and clear sample enhances efficiency in managing switch infrastructure and facilitates easier auditing and compliance checks.
VPN Configuration Document Sample
A
VPN Configuration Document Sample provides detailed instructions and settings required to set up a Virtual Private Network, ensuring secure and encrypted communication over the internet. It includes key elements such as server addresses, authentication methods, encryption protocols, and client configuration steps. This document serves as a reliable reference for IT professionals to standardize VPN deployment and troubleshoot connectivity issues efficiently.
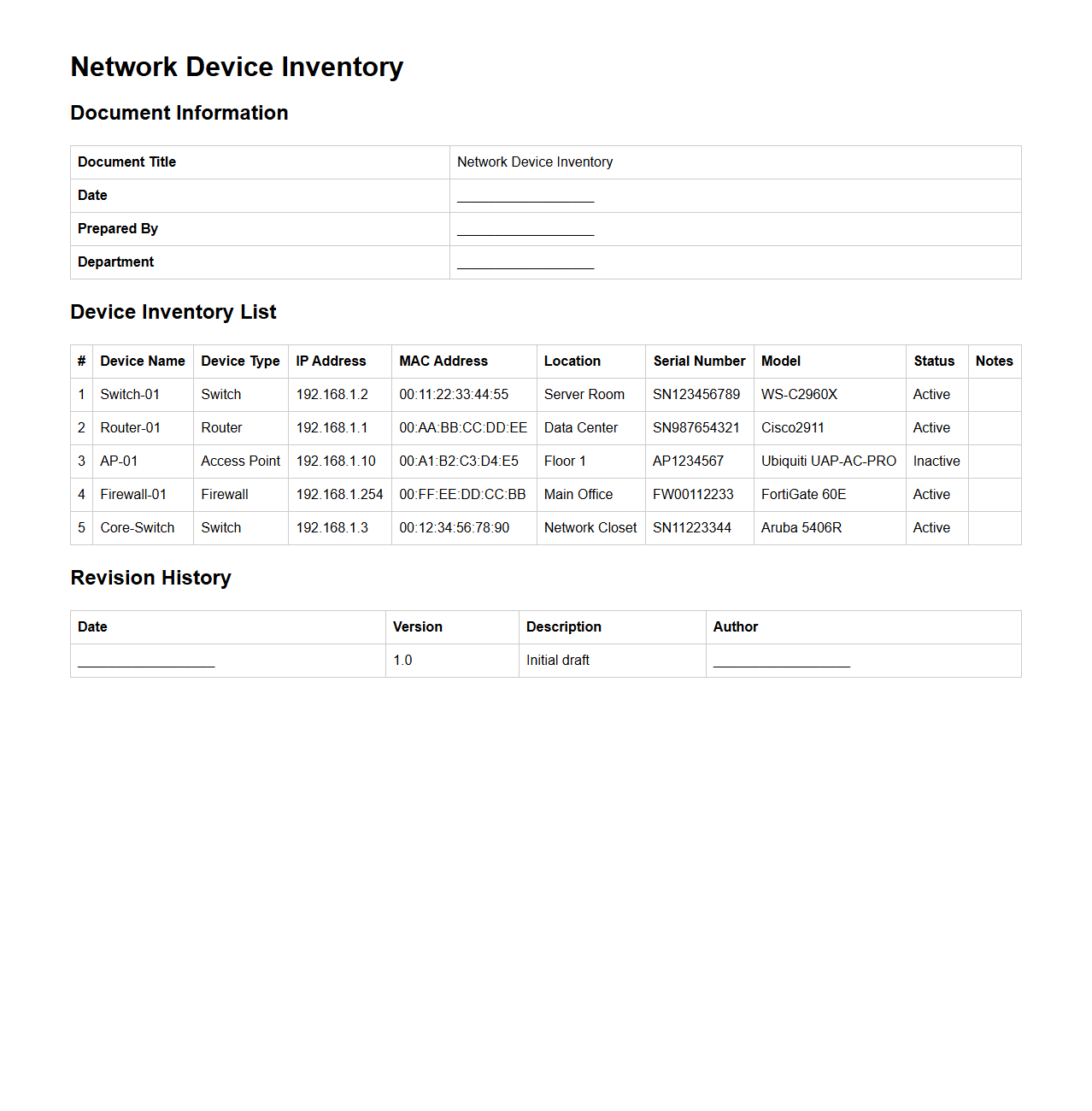
Network Device Inventory Document Sample
A
Network Device Inventory Document Sample is a structured template used for cataloging all hardware components within a network, including routers, switches, firewalls, and servers. It typically contains detailed information such as device model numbers, IP addresses, MAC addresses, firmware versions, physical locations, and maintenance schedules. This document facilitates efficient asset management, troubleshooting, and security compliance by providing a comprehensive overview of network infrastructure.
DHCP and DNS Settings Document Sample
DHCP (Dynamic Host Configuration Protocol) automates the assignment of IP addresses and network settings to devices, ensuring efficient and error-free connectivity. DNS (Domain Name System) translates domain names into IP addresses, enabling seamless navigation across the internet or internal networks. A
DHCP and DNS Settings Document Sample outlines configuration parameters, IP address range, lease duration, DNS server addresses, and domain search lists, facilitating standardized network setup and troubleshooting.
What protocols are specified for inter-VLAN routing in the network configuration document?
The document specifies the use of OSPF and RIP protocols for inter-VLAN routing to ensure efficient and dynamic routing between VLAN segments. It emphasizes Layer 3 switches configured with routing capabilities to manage traffic flow. Additionally, the document outlines the configuration of SVIs (Switch Virtual Interfaces) to facilitate smooth inter-VLAN communication.
How does the document address redundancy and failover for corporate WAN links?
The network configuration mandates the implementation of dual WAN links to provide redundancy and improve reliability. It prescribes the use of HSRP or VRRP protocols for automatic failover management. Regular testing of failover mechanisms is also highlighted to ensure seamless network availability during outages.
Are there predefined network segmentation policies for guest and IoT devices?
The document enforces strict network segmentation by isolating guest and IoT devices into separate VLANs. It requires the application of dedicated Access Control Lists (ACLs) to restrict access between these segments and the corporate network. This approach enhances security and minimizes potential attack vectors from less trusted devices.
What authentication mechanisms are mandated for administrative access in the configuration?
Administrative access is secured through mandatory use of RADIUS or TACACS+ authentication protocols. The document enforces multi-factor authentication (MFA) for all privileged accounts to bolster security. It also requires encrypted management sessions using protocols like SSH and HTTPS.
Does the document outline procedures for periodic configuration backup and version control?
The network configuration document mandates periodic automatic backups of all device configurations to a centralized server. It specifies implementation of a version control system to track changes and facilitate rollback when necessary. Regular audits and verification of backup integrity are also included as part of the procedures.