A Vulnerability Assessment Report Document Sample for IoT Devices provides a comprehensive analysis of security weaknesses in connected devices, detailing identified vulnerabilities, risk levels, and remediation recommendations. It serves as a critical tool for organizations to enhance their IoT security posture by systematically evaluating device firmware, communication protocols, and network configurations. This report sample aids in prioritizing security efforts and ensuring compliance with industry standards.
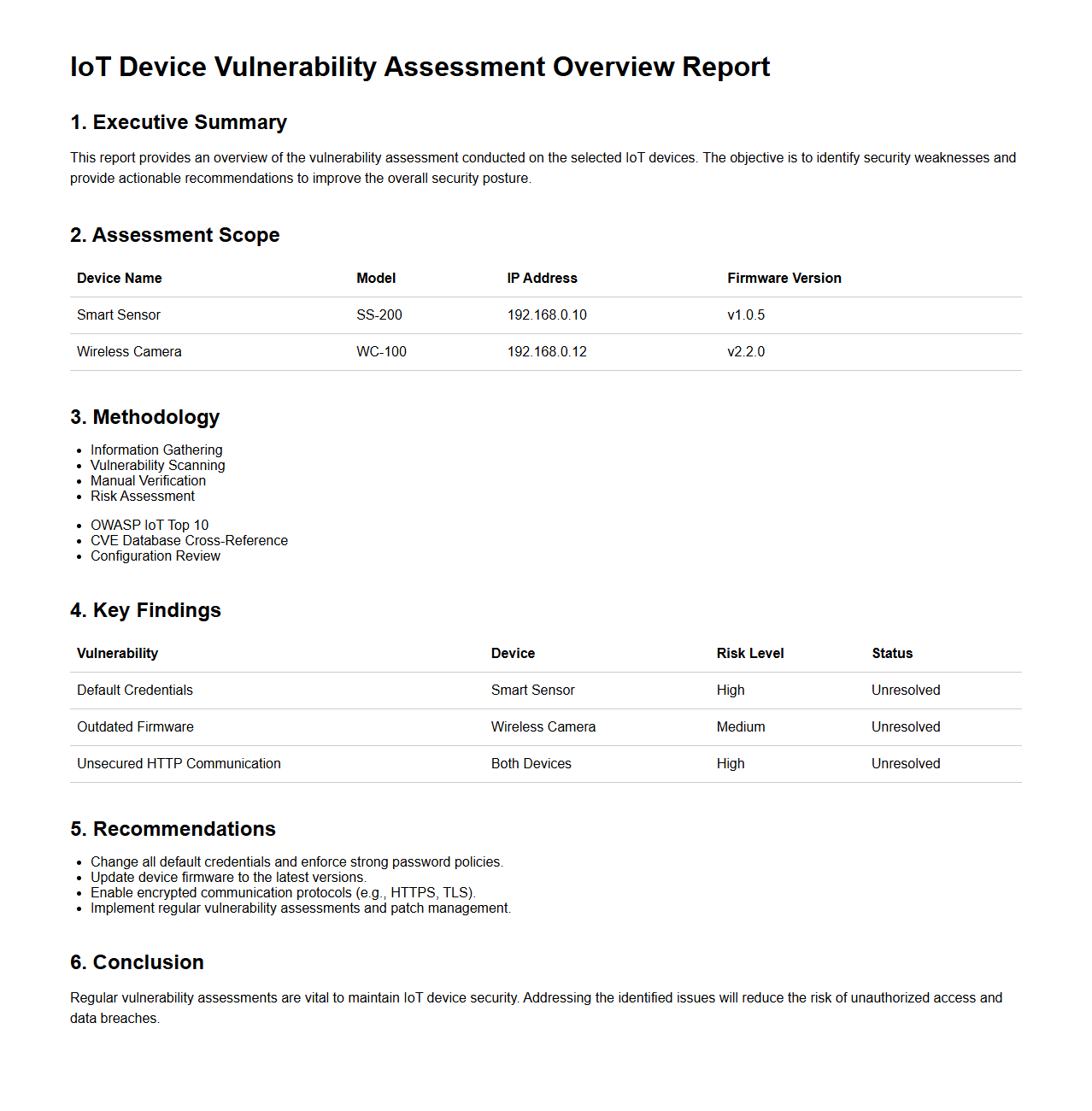
IoT Device Vulnerability Assessment Overview Report Sample
The
IoT Device Vulnerability Assessment Overview Report Sample document provides a comprehensive analysis of security weaknesses found in Internet of Things devices. It details identified vulnerabilities, potential risks, and recommended mitigation strategies to enhance device security and protect against cyber threats. This report serves as a critical resource for manufacturers, cybersecurity professionals, and stakeholders aiming to improve the resilience of connected devices.
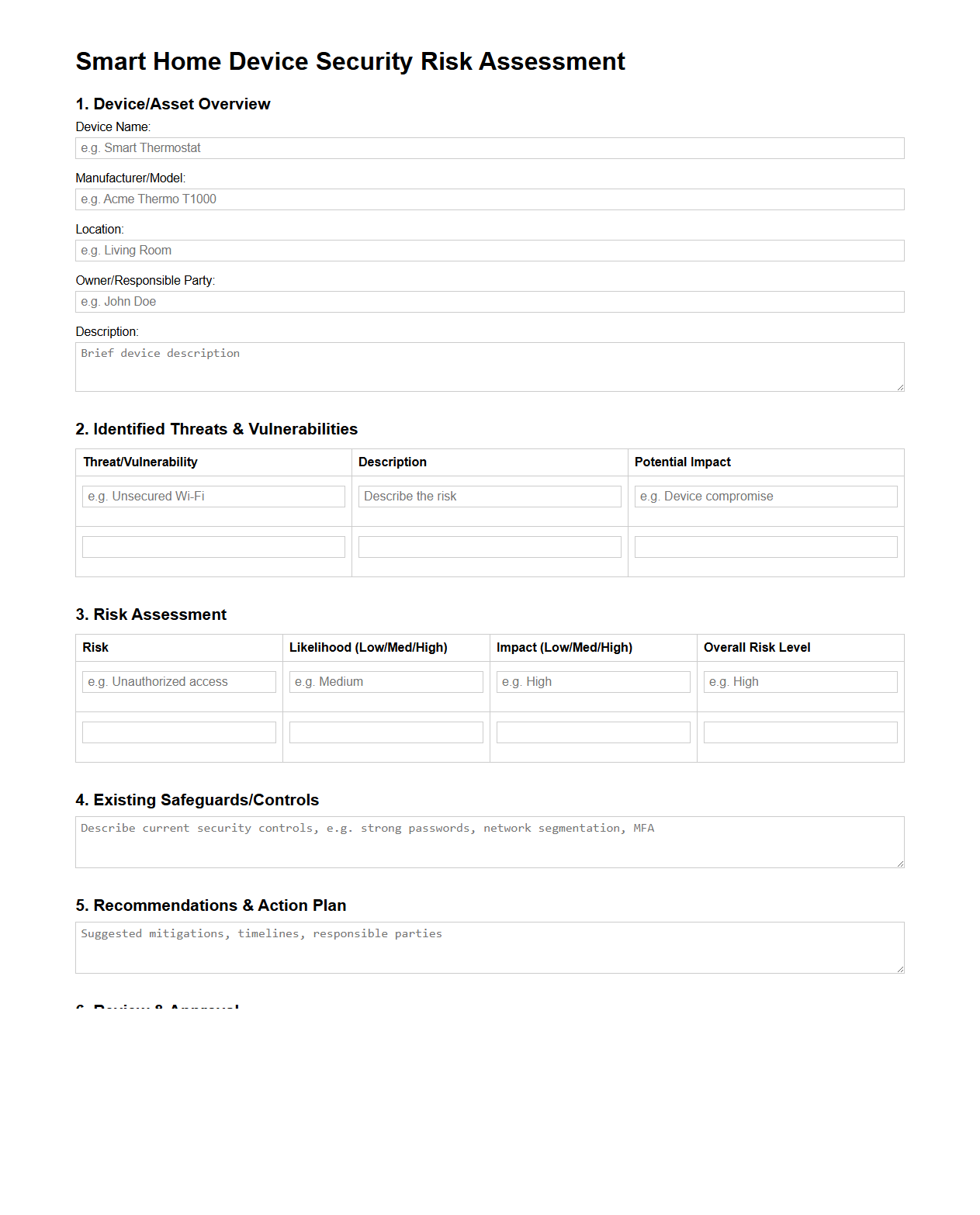
Smart Home Device Security Risk Assessment Document Template
A
Smart Home Device Security Risk Assessment Document Template is a structured framework designed to identify, evaluate, and mitigate potential cybersecurity threats associated with smart home devices. This template aids in systematically documenting risks related to device vulnerabilities, network exposure, and data privacy concerns to ensure robust security measures. It serves as a critical tool for homeowners and security professionals to implement effective controls and enhance the overall safety of interconnected home environments.
Industrial IoT Vulnerability Audit Report Example
An
Industrial IoT Vulnerability Audit Report document systematically identifies and assesses security weaknesses within industrial Internet of Things systems, including devices, networks, and software. It provides detailed findings on risk exposure, potential threats, and vulnerability severity levels, helping organizations prioritize remediation efforts. The report serves as a critical tool for enhancing operational security and ensuring compliance with industry standards.
Connected Medical Device Risk Analysis Report Format
The
Connected Medical Device Risk Analysis Report Format document outlines a structured approach to identifying, assessing, and mitigating risks associated with connected medical devices. It provides detailed sections for hazard identification, risk evaluation, control measures, and residual risk verification, ensuring compliance with regulatory standards like ISO 14971 and FDA guidelines. This format facilitates consistent documentation, enhances device safety, and supports thorough analysis throughout the device lifecycle.
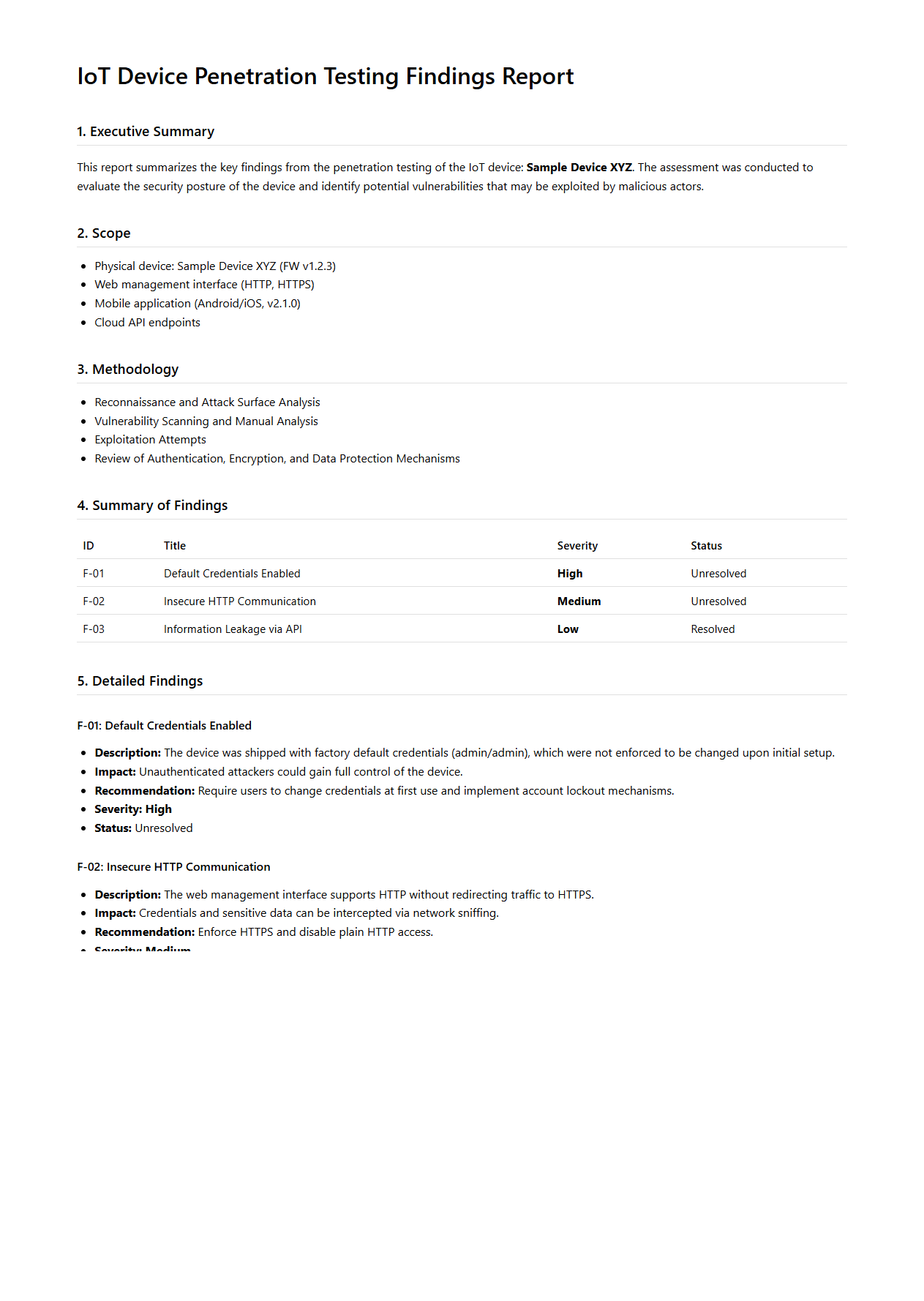
IoT Device Penetration Testing Findings Report Sample
The
IoT Device Penetration Testing Findings Report Sample document provides a detailed assessment of security vulnerabilities identified in Internet of Things (IoT) devices after comprehensive penetration testing. It includes prioritized findings, risk levels, and remediation recommendations to enhance device security and protect against cyber threats. This report is essential for IoT manufacturers, security teams, and stakeholders aiming to strengthen the device's resilience and ensure compliance with industry standards.
Consumer IoT Security Gap Analysis Report Outline
The
Consumer IoT Security Gap Analysis Report Outline document serves as a structured framework to identify and assess vulnerabilities in consumer Internet of Things devices. It breaks down critical security components such as device authentication, data encryption, and firmware updates to highlight existing weaknesses. This report outline guides organizations in prioritizing risk mitigation strategies and improving overall IoT device security posture.
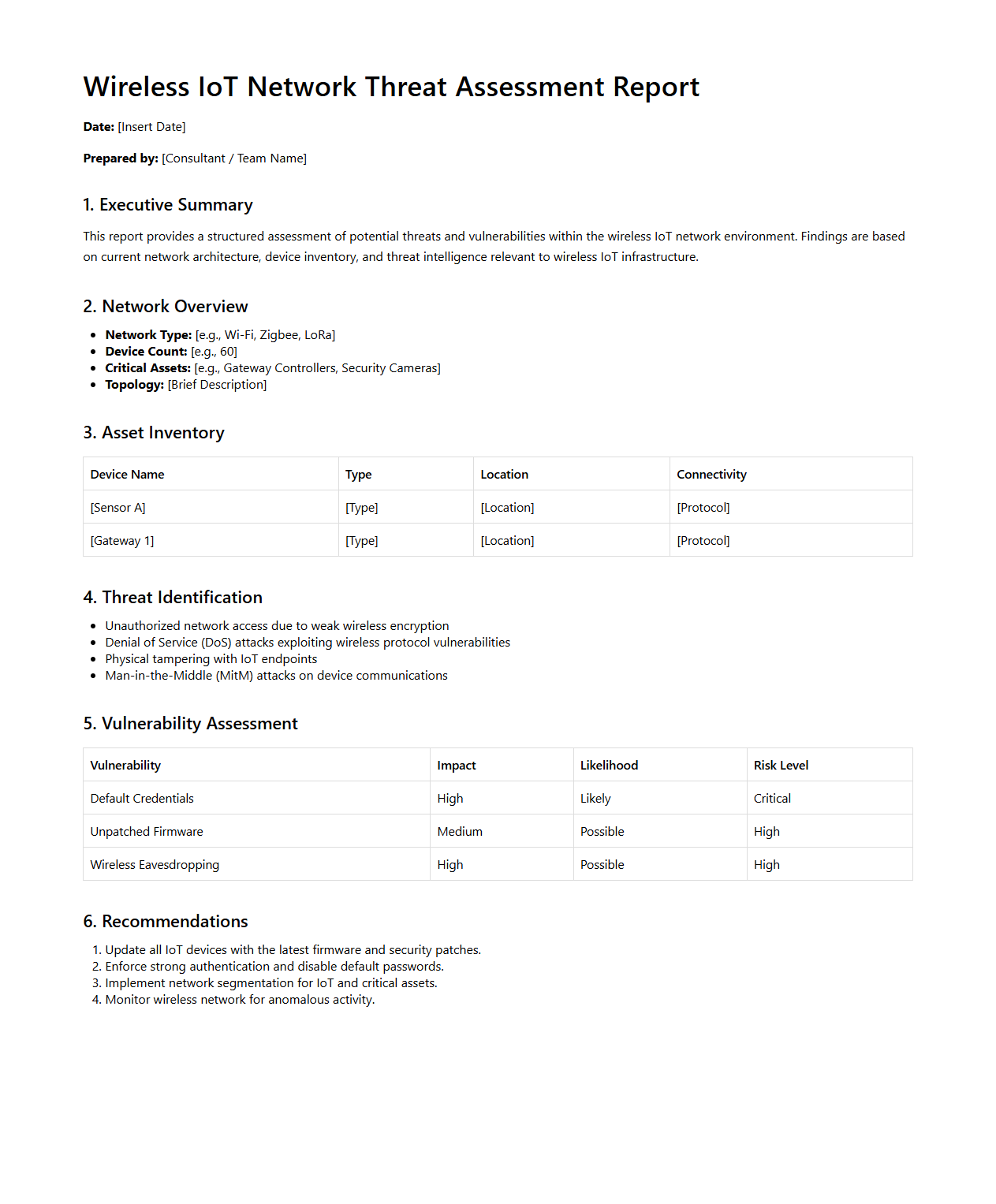
Wireless IoT Network Threat Assessment Report Sample
A
Wireless IoT Network Threat Assessment Report Sample document provides a detailed analysis of potential security vulnerabilities within wireless IoT infrastructures. It highlights common attack vectors, evaluates risk levels, and suggests mitigation strategies to protect connected devices and data integrity. This report serves as a crucial tool for cybersecurity professionals aiming to enhance IoT network resilience against evolving threats.
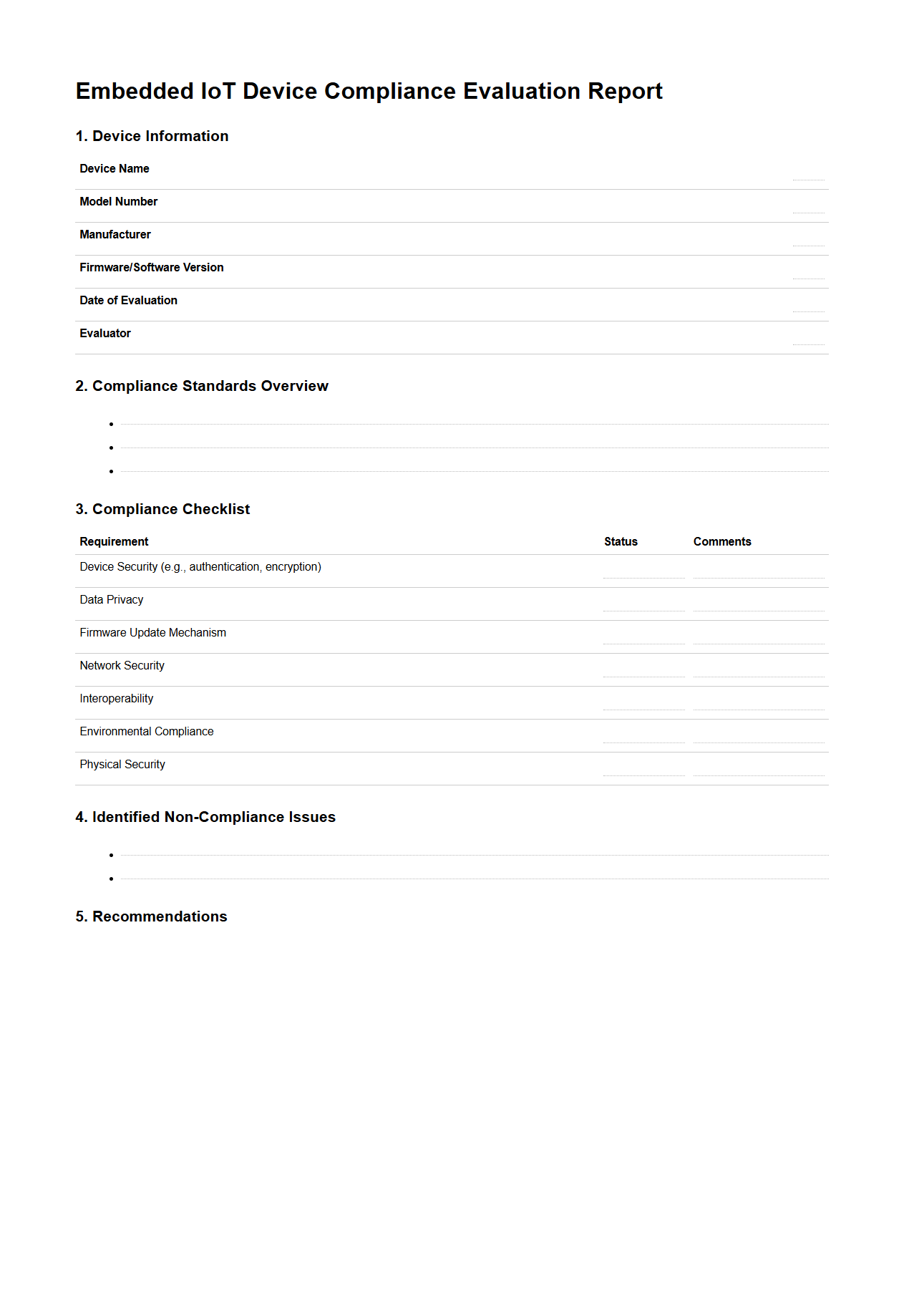
Embedded IoT Device Compliance Evaluation Report Template
The
Embedded IoT Device Compliance Evaluation Report Template is a structured document designed to systematically assess and verify the adherence of embedded IoT devices to industry standards, security protocols, and regulatory requirements. It facilitates clear documentation of test results, vulnerabilities, and compliance status, ensuring devices meet safety, interoperability, and performance benchmarks. This template is essential for manufacturers, auditors, and developers aiming to maintain robust security and functional integrity in IoT ecosystems.
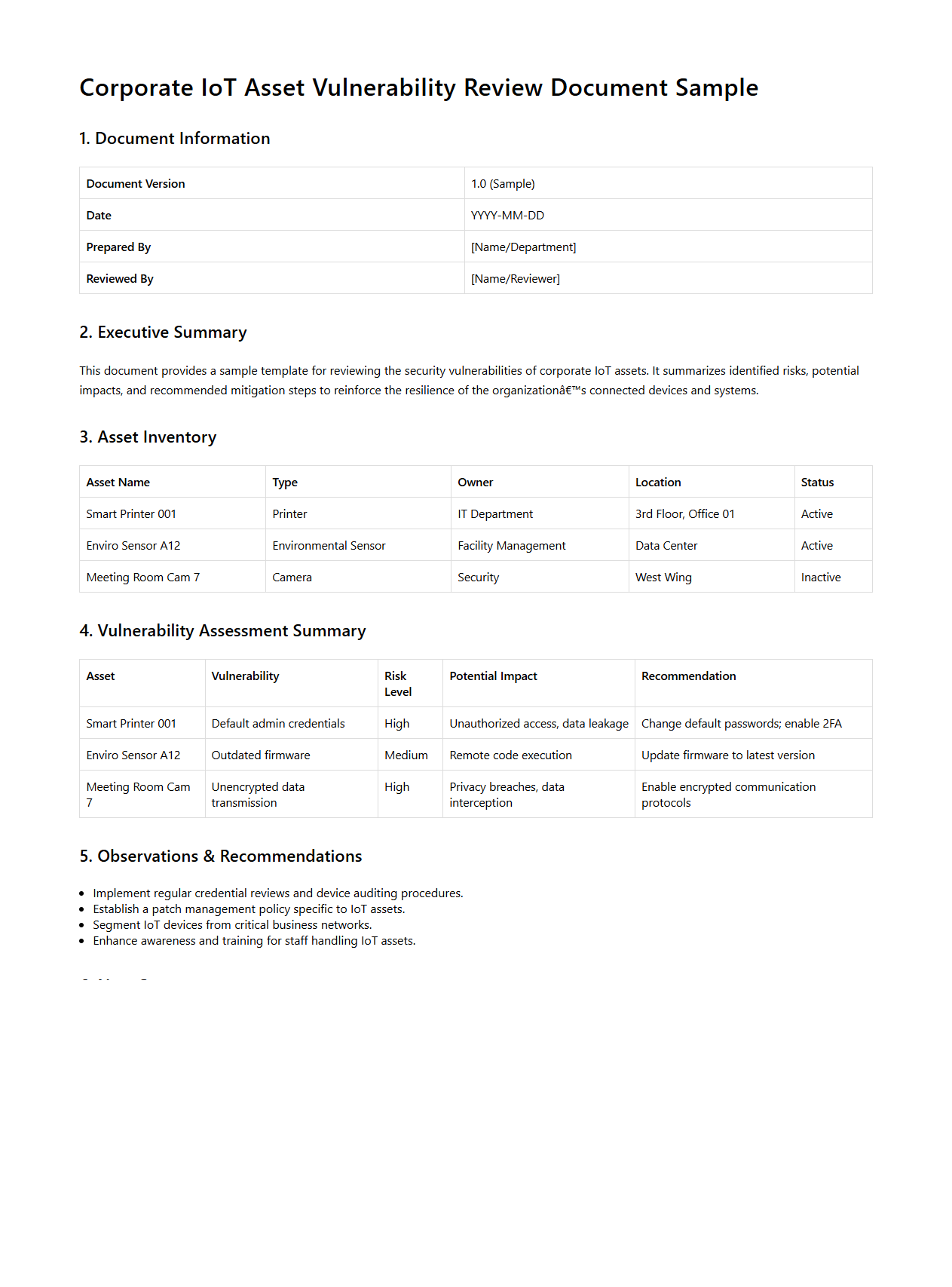
Corporate IoT Asset Vulnerability Review Document Sample
A
Corporate IoT Asset Vulnerability Review Document Sample provides a structured framework to assess security weaknesses in an organization's Internet of Things devices and connected assets. This document outlines methodologies for identifying, categorizing, and prioritizing vulnerabilities to mitigate risks related to unauthorized access, data breaches, and operational disruptions. It serves as a critical resource for cybersecurity teams aiming to enhance the resilience of corporate IoT infrastructures against evolving cyber threats.
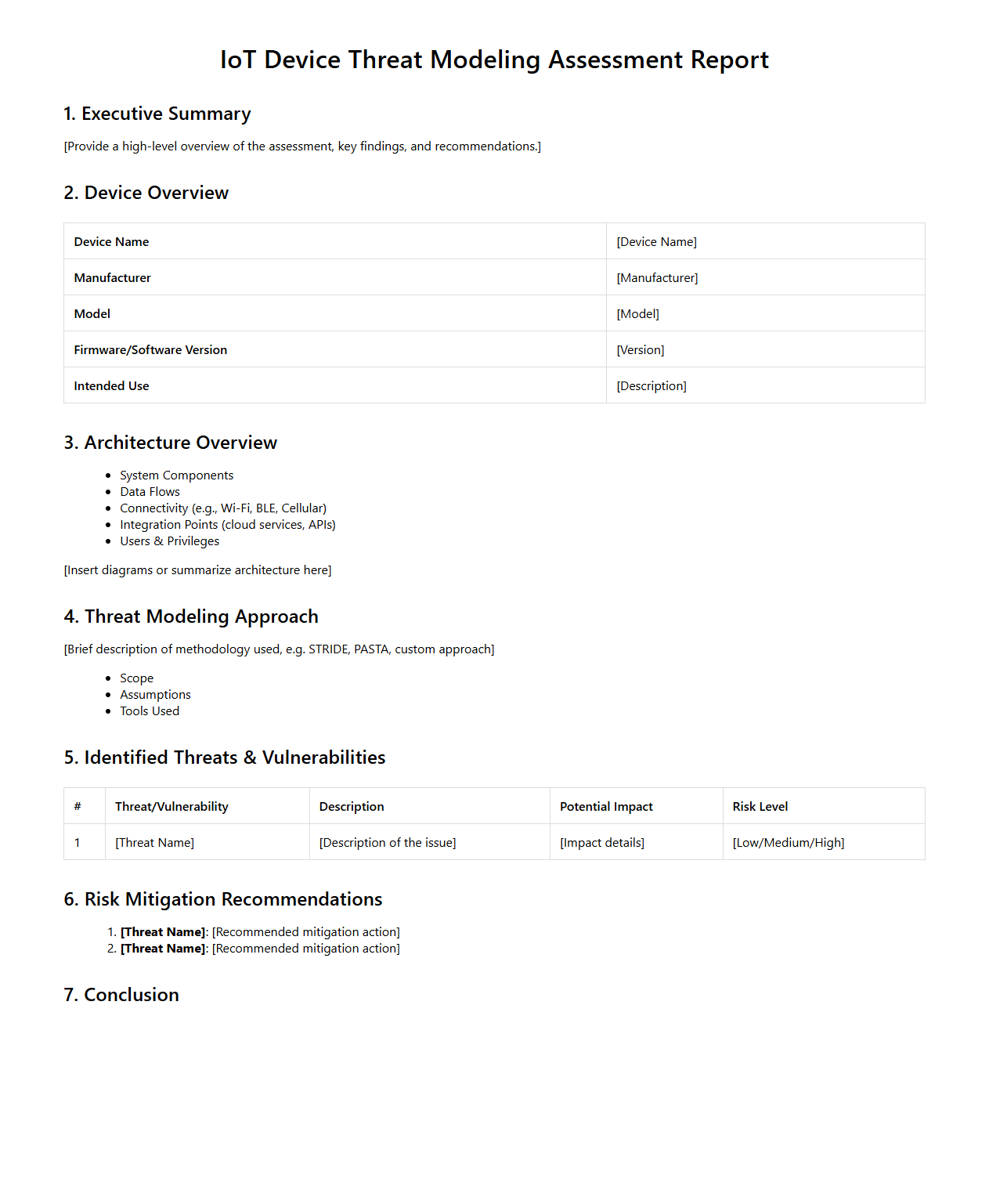
IoT Device Threat Modeling Assessment Report Format
An
IoT Device Threat Modeling Assessment Report Format document provides a structured framework for identifying and analyzing potential security vulnerabilities in IoT devices. It outlines key sections such as threat scenarios, risk ratings, mitigation strategies, and security controls to systematically evaluate device threats. This format ensures comprehensive documentation to guide security improvements and compliance efforts in IoT ecosystems.
What encryption protocols are evaluated in the IoT device vulnerability assessment report?
The report evaluates several encryption protocols commonly used in IoT devices, including TLS, WPA2, and AES. It assesses the strength and implementation of these protocols to identify potential weaknesses. The focus is on ensuring data confidentiality and integrity across IoT communication channels.
How does the report address firmware update mechanisms in IoT devices?
The report details the security of firmware update mechanisms by analyzing update authentication and encryption methods. It emphasizes the importance of secure update delivery to prevent unauthorized code execution. Additionally, the assessment checks for rollback protection and verification processes.
Are device authentication vulnerabilities specifically highlighted in the document?
Yes, the report specifically highlights device authentication vulnerabilities that could be exploited by attackers. It reviews the authentication protocols and identifies weak points such as default credentials and improper session management. Recommendations include strengthening multi-factor authentication where possible.
What methodology is used for IoT network traffic analysis in the assessment?
The assessment uses a combination of packet capture and deep network traffic analysis tools to monitor device communications. It applies behavioral analysis to detect anomalies indicative of security issues. This methodology aids in identifying unauthorized data exfiltration and protocol misuse.
Does the report include risk scoring specific to individual IoT device components?
Yes, the report assigns risk scoring to distinct IoT device components based on their vulnerability and potential impact. Each hardware and software module is analyzed separately to provide detailed risk profiles. This granular approach allows targeted mitigation strategies for improved security posture.
More Technology Templates