A Security Audit Document Sample for Cloud Applications provides a comprehensive framework to evaluate the security posture of cloud-based systems. It outlines key audit areas such as data protection, access controls, and compliance with industry standards. This sample enables organizations to identify vulnerabilities and implement robust security measures effectively.
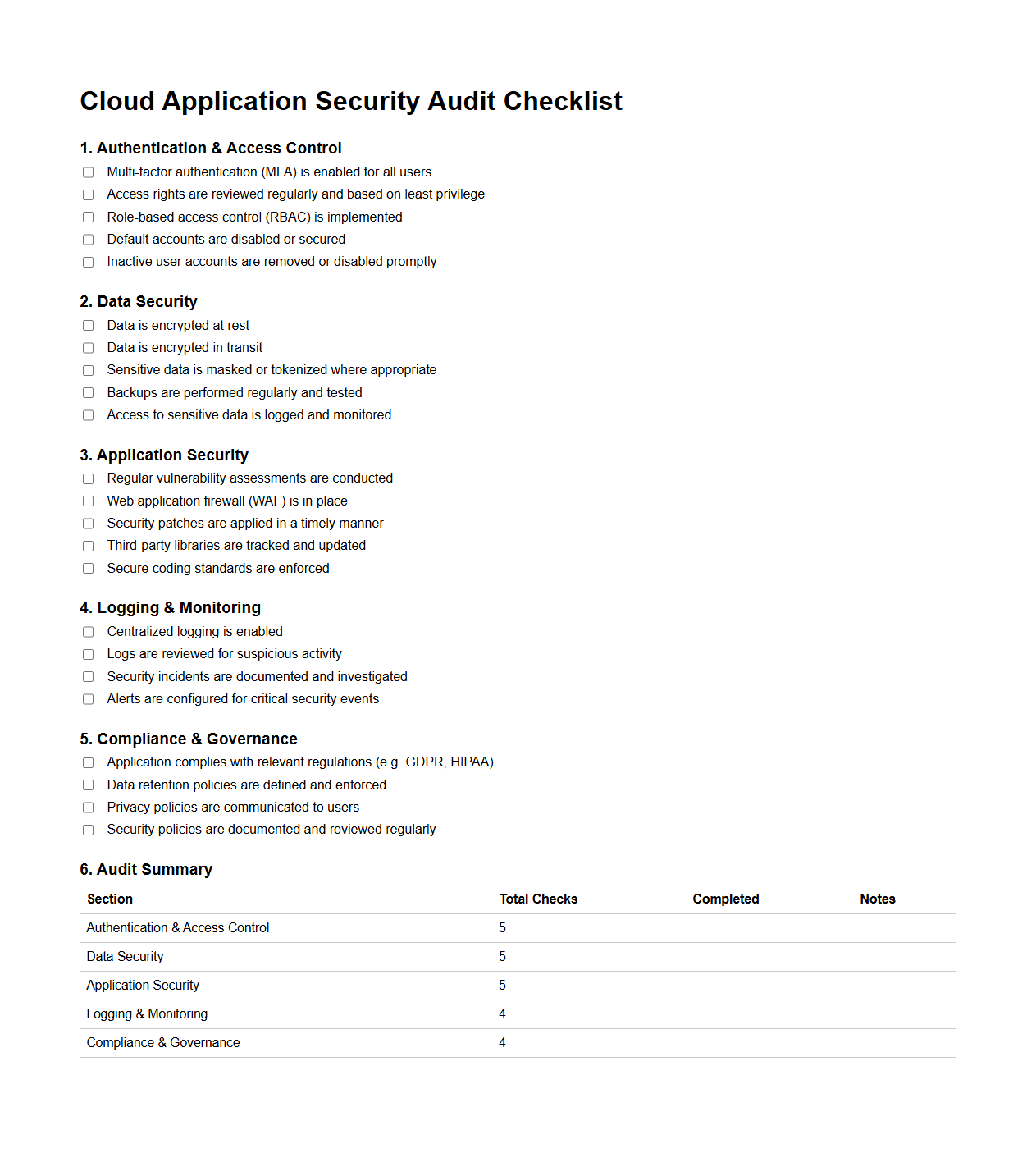
Cloud Application Security Audit Checklist
A
Cloud Application Security Audit Checklist document is a comprehensive guide used to evaluate the security posture of cloud-based applications by systematically reviewing key controls, configurations, and compliance requirements. It helps organizations identify vulnerabilities, ensure adherence to industry standards, and implement best practices across areas such as data protection, access management, and infrastructure security. This checklist supports continuous monitoring and risk mitigation efforts to safeguard sensitive information within cloud environments.
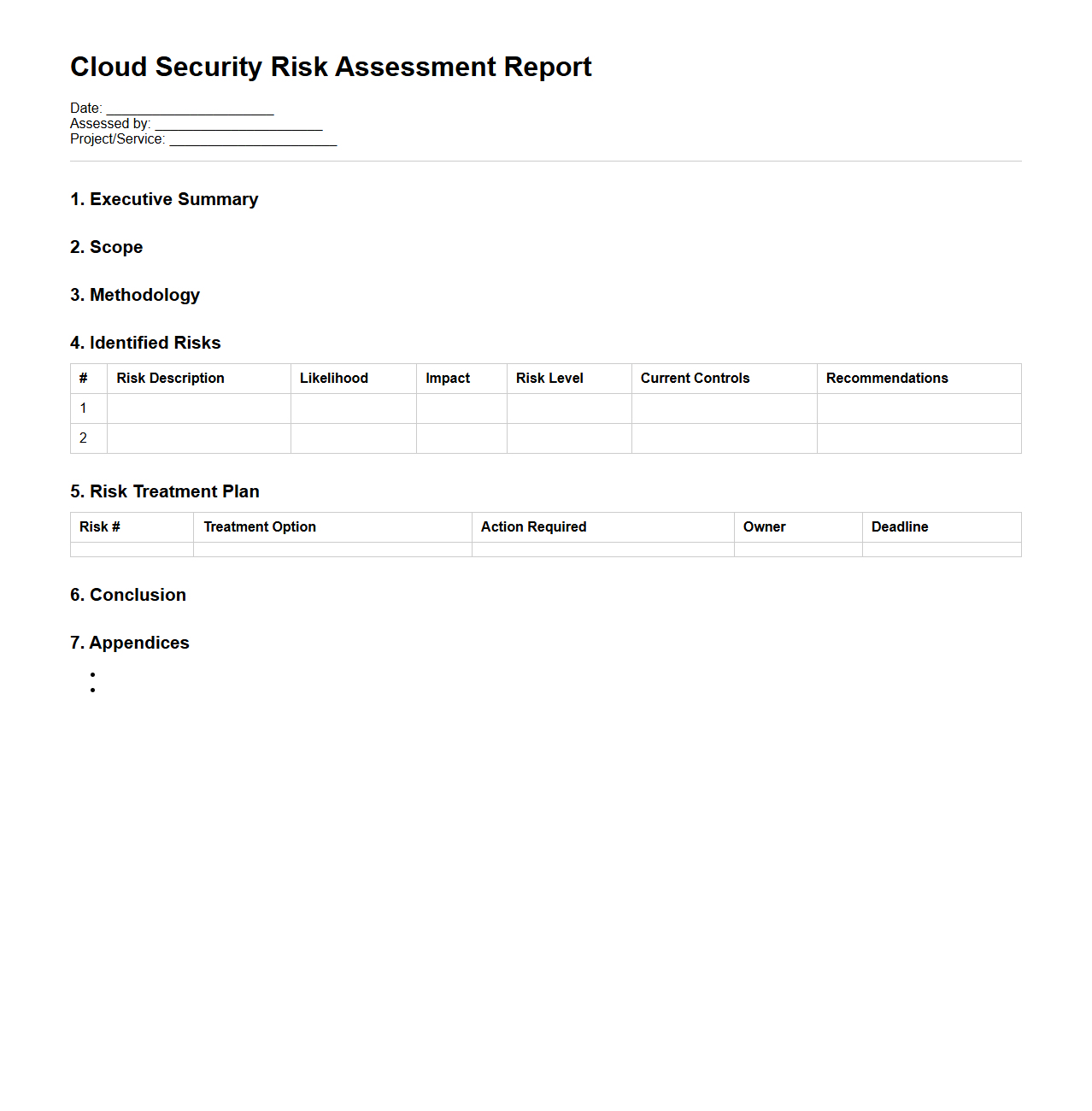
Cloud Security Risk Assessment Report
A
Cloud Security Risk Assessment Report document identifies, analyzes, and evaluates potential security threats and vulnerabilities within a cloud computing environment. It provides detailed insights into risks related to data breaches, misconfigurations, compliance gaps, and third-party access, helping organizations prioritize mitigation strategies. This report supports informed decision-making to enhance cloud infrastructure security and ensures adherence to regulatory requirements.
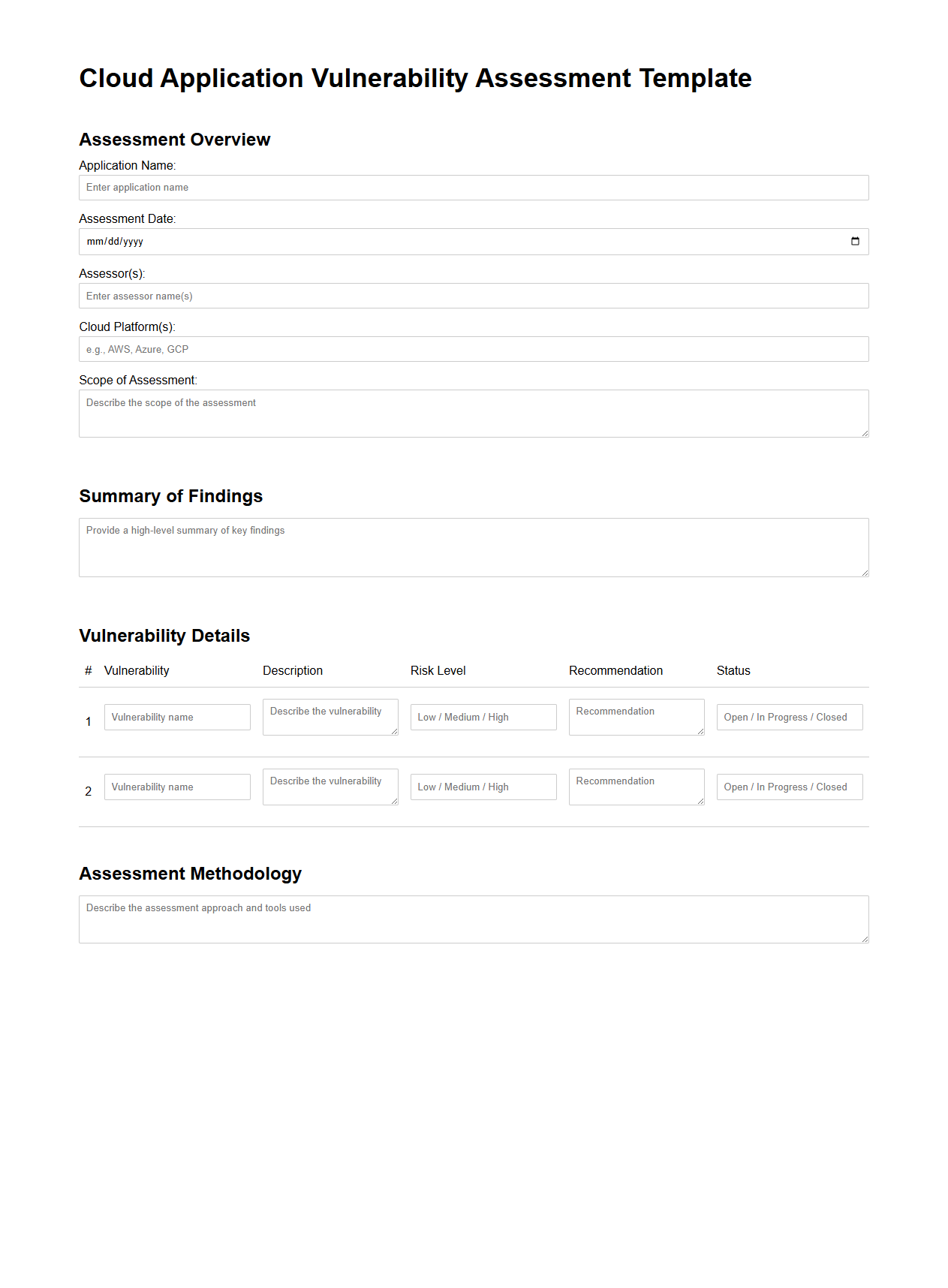
Cloud Application Vulnerability Assessment Template
A
Cloud Application Vulnerability Assessment Template document serves as a structured framework to identify, analyze, and document security weaknesses within cloud-based applications. It standardizes the evaluation process by outlining key areas such as authentication flaws, data exposure risks, misconfigurations, and compliance gaps. This template facilitates consistent vulnerability reporting, enabling security teams to prioritize remediation efforts and enhance overall cloud application security posture.
Cloud Service Provider Security Evaluation Form
The
Cloud Service Provider Security Evaluation Form document is a comprehensive tool used to assess the security posture of a cloud service provider by evaluating their compliance with industry standards, security controls, and risk management practices. It typically includes sections on data protection measures, access controls, incident response protocols, and regulatory adherence to ensure the provider meets organizational security requirements. Organizations use this form to systematically identify potential vulnerabilities and verify that cloud services align with their security policies before integration.
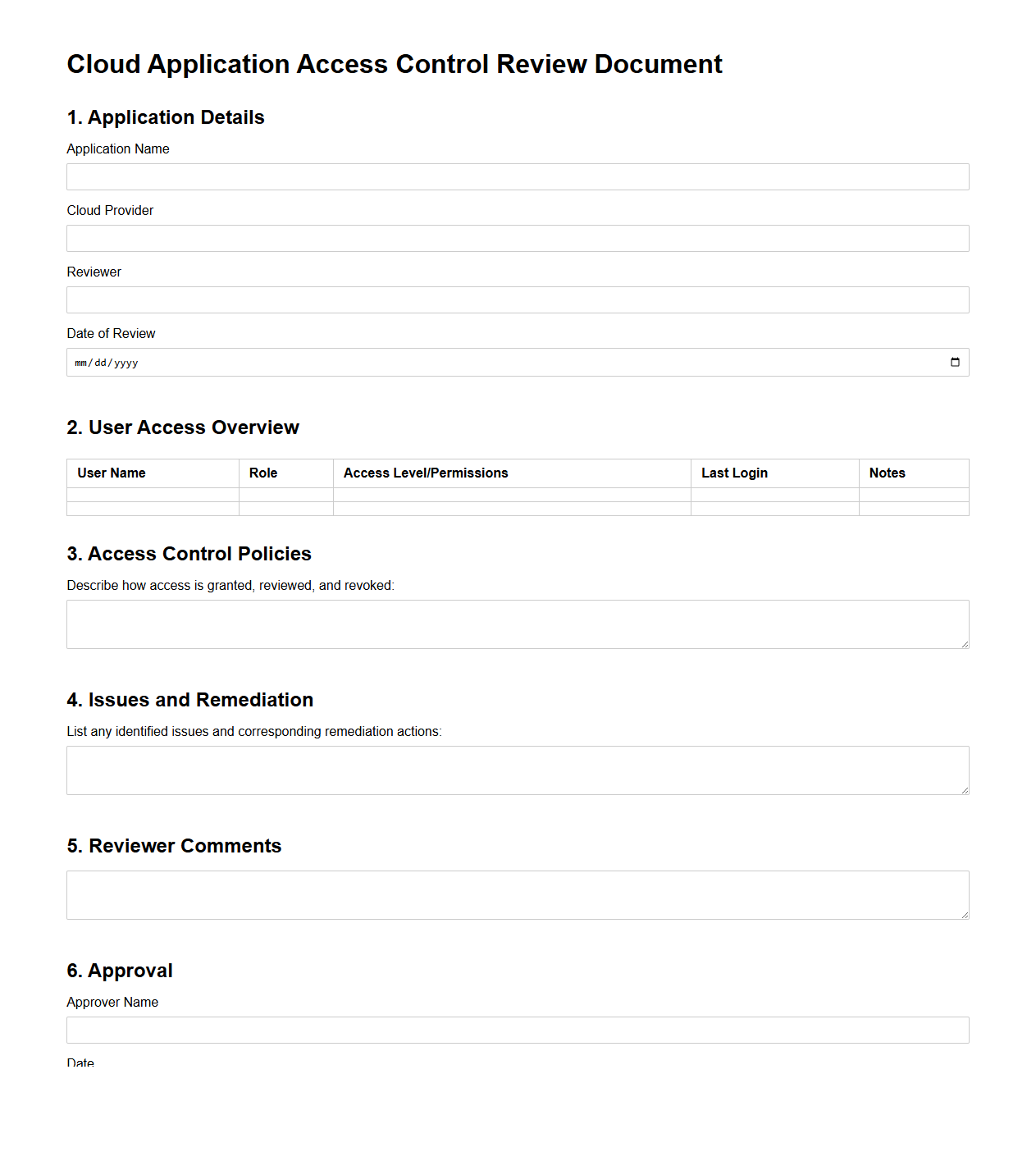
Cloud Application Access Control Review Document
A
Cloud Application Access Control Review Document outlines the procedures and criteria for evaluating user permissions and access rights within cloud-based applications, ensuring security compliance and minimizing unauthorized access risks. It details the review schedule, responsible personnel, and methodologies for auditing access logs, role assignments, and privilege escalations. This document is crucial for maintaining robust security posture and meeting regulatory requirements in cloud environments.
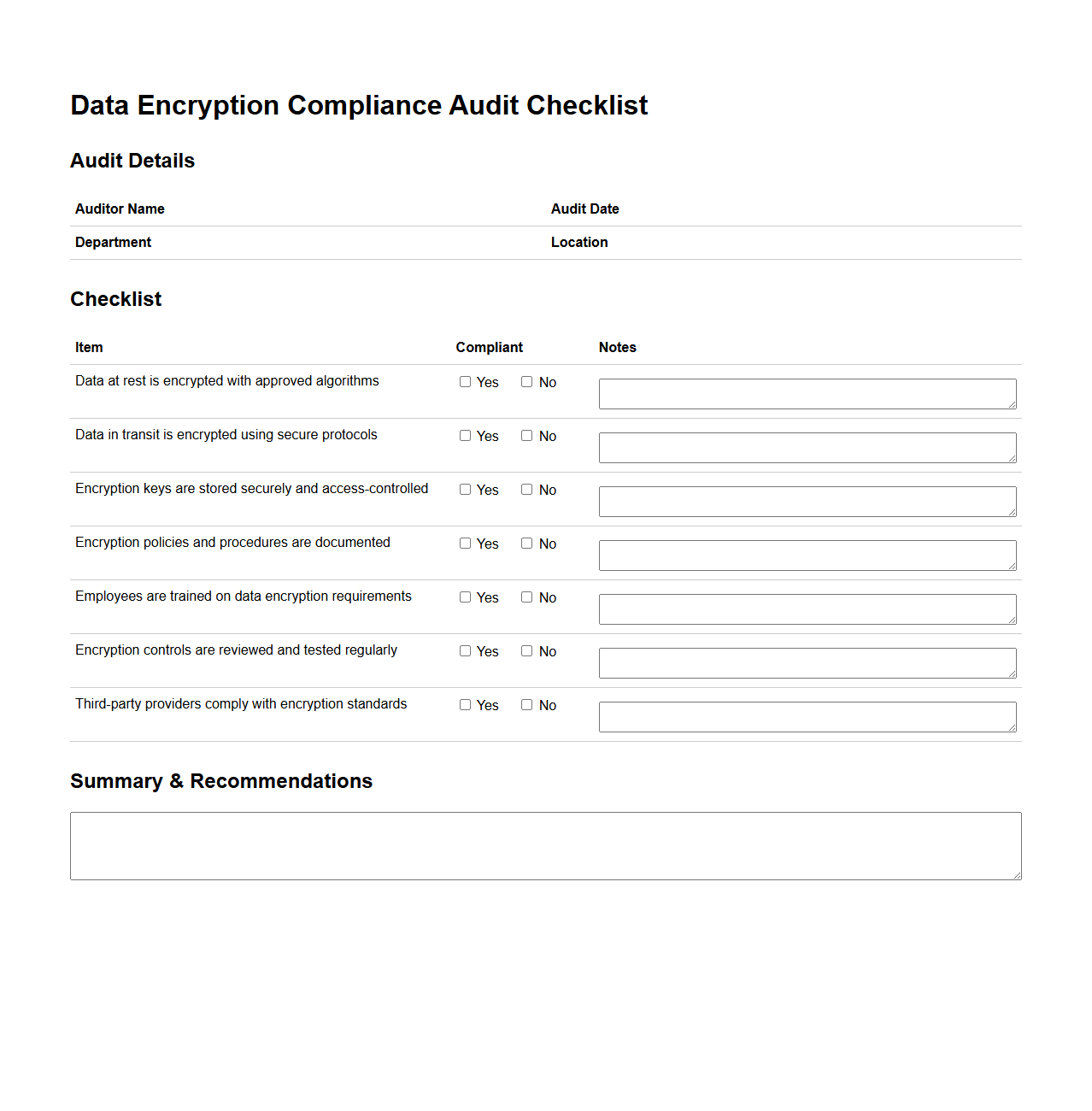
Data Encryption Compliance Audit Checklist
A
Data Encryption Compliance Audit Checklist document outlines essential criteria and best practices to ensure an organization's data encryption methods meet regulatory standards and industry requirements. This checklist serves as a systematic guide for auditors and IT teams to verify encryption protocols, key management processes, and data protection measures are properly implemented and maintained. Compliance with these guidelines helps mitigate risks of data breaches and ensures adherence to frameworks such as GDPR, HIPAA, and PCI DSS.
Multi-Tenant Cloud Security Audit Report
A
Multi-Tenant Cloud Security Audit Report document evaluates the security controls and compliance measures implemented within a shared cloud environment hosting multiple tenants. It details findings related to data segregation, access management, encryption standards, and vulnerability assessments to ensure tenant isolation and regulatory adherence. Organizations use this report to verify that cloud service providers maintain robust security frameworks protecting all tenants' sensitive information.
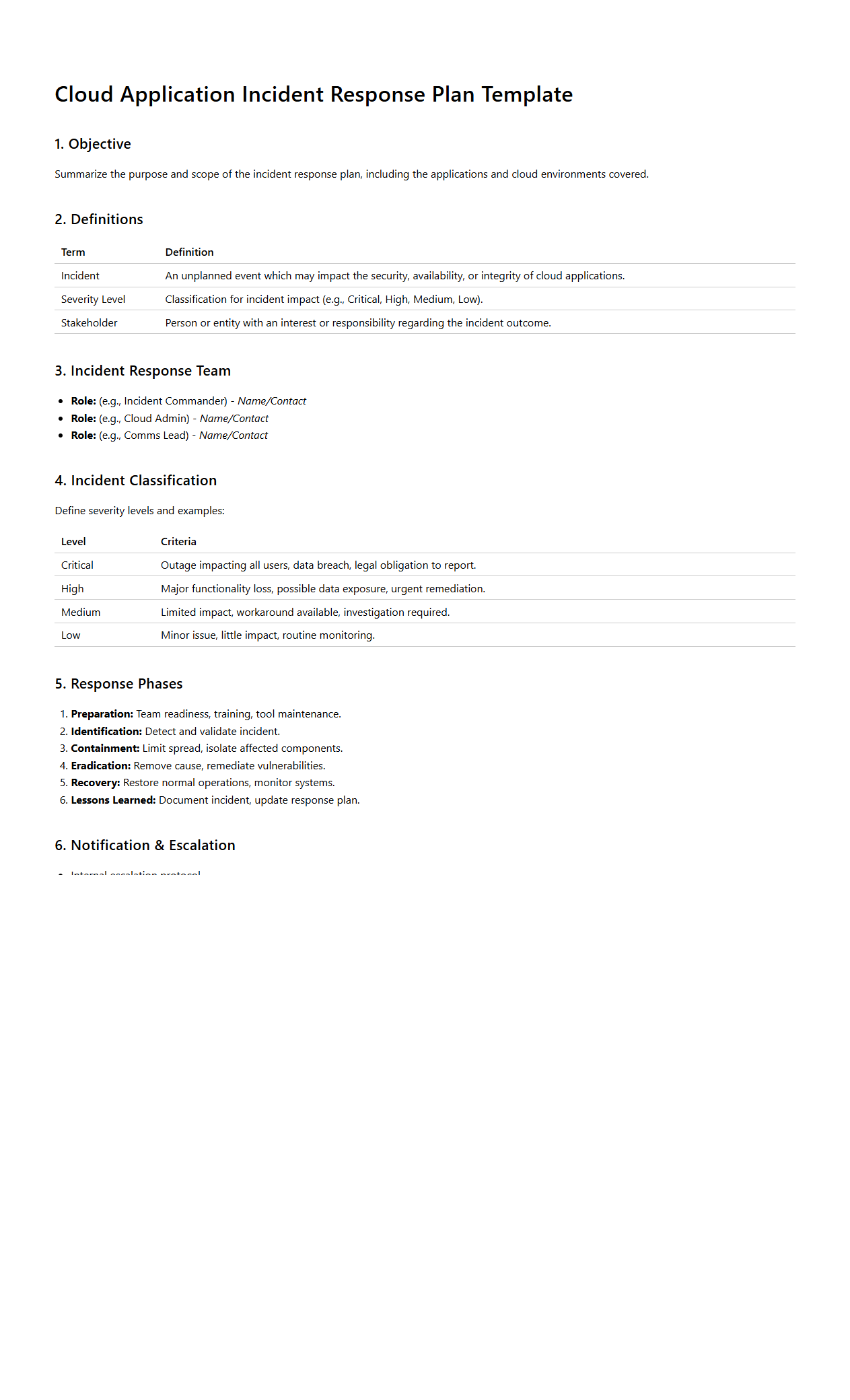
Cloud Application Incident Response Plan Template
A
Cloud Application Incident Response Plan Template document provides a structured framework for identifying, managing, and resolving security incidents specific to cloud-based applications. It outlines key roles, communication protocols, and step-by-step procedures to ensure rapid mitigation and recovery from vulnerabilities or breaches. This template helps organizations maintain compliance, minimize downtime, and protect sensitive data in cloud environments.
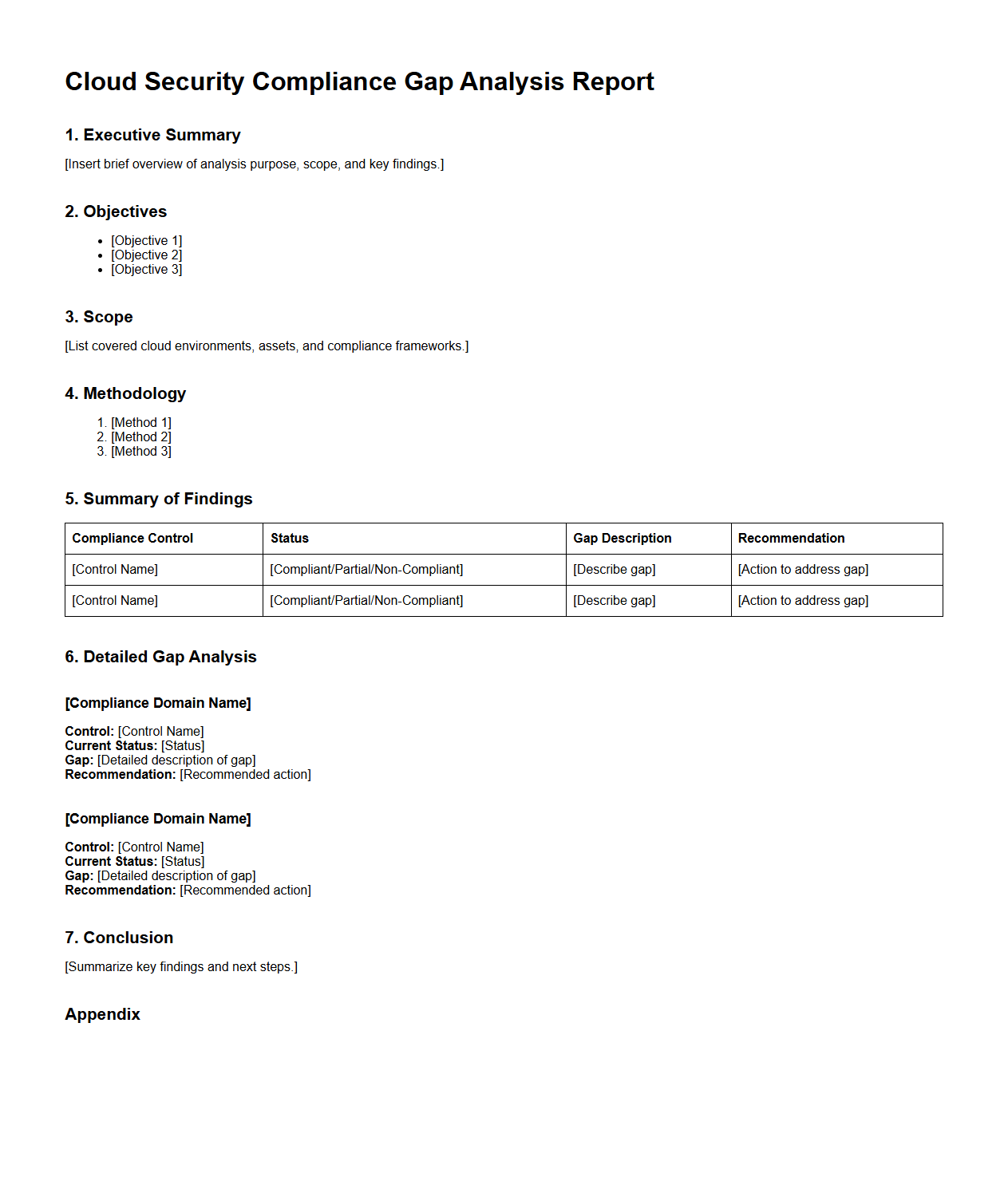
Cloud Security Compliance Gap Analysis Report
A
Cloud Security Compliance Gap Analysis Report document identifies discrepancies between an organization's current cloud security posture and industry standards or regulatory requirements. It evaluates controls, policies, and configurations to highlight vulnerabilities and compliance risks. Organizations use this report to prioritize remediation efforts and achieve regulatory adherence effectively.
Cloud Application Penetration Testing Report
A
Cloud Application Penetration Testing Report document provides a comprehensive assessment of security vulnerabilities within cloud-based applications by detailing findings from simulated cyberattacks. It identifies potential risks, highlights exploited weaknesses, and recommends remediation strategies to strengthen the application's defenses against unauthorized access and data breaches. This report serves as a critical tool for developers and security teams to enhance cloud application security posture and ensure compliance with industry standards.
What encryption standards are documented for data at rest and in transit in the audit?
The audit specifies the use of AES-256 encryption for data at rest to ensure maximum security. For data in transit, the document mandates compliance with TLS 1.2 or higher protocols. These standards guarantee that sensitive information remains protected both when stored and during transmission across networks.
How does the security audit address multi-tenancy risks in cloud applications?
The security audit emphasizes strong isolation mechanisms to mitigate multi-tenancy risks in cloud environments. It includes verifying access controls and ensuring tenant data segregation at both application and infrastructure levels. This approach reduces the chance of unauthorized data access between different cloud tenants.
What incident response protocols are specified for cloud service data breaches?
The document outlines a comprehensive incident response protocol including immediate breach detection and notification procedures. It mandates incident containment measures and detailed forensic analysis to understand breach impact. Additionally, the protocol specifies timely communication with affected stakeholders to maintain transparency.
Are third-party integrations and APIs evaluated for compliance in the audit document?
The audit includes a thorough evaluation of third-party integrations and APIs for compliance with security standards. It involves assessing data exchange security, authentication mechanisms, and vulnerability risks. This ensures that external components do not introduce exploitable weaknesses into the cloud environment.
Does the security audit document outline continuous monitoring mechanisms for cloud workloads?
The security audit mandates the implementation of continuous monitoring tools to oversee cloud workloads in real-time. This includes automated alerts for anomalous activities and ongoing vulnerability assessments. Continuous monitoring is crucial to promptly detect and respond to emerging security threats.
More Technology Templates