A Backup Strategy Document Sample for Database Management Systems outlines the procedures and policies for safeguarding critical data through regular backups. It details the types of backups, scheduling, storage locations, and recovery processes to ensure data integrity and availability. This document serves as a crucial reference for maintaining consistent database protection and minimizing data loss risks.
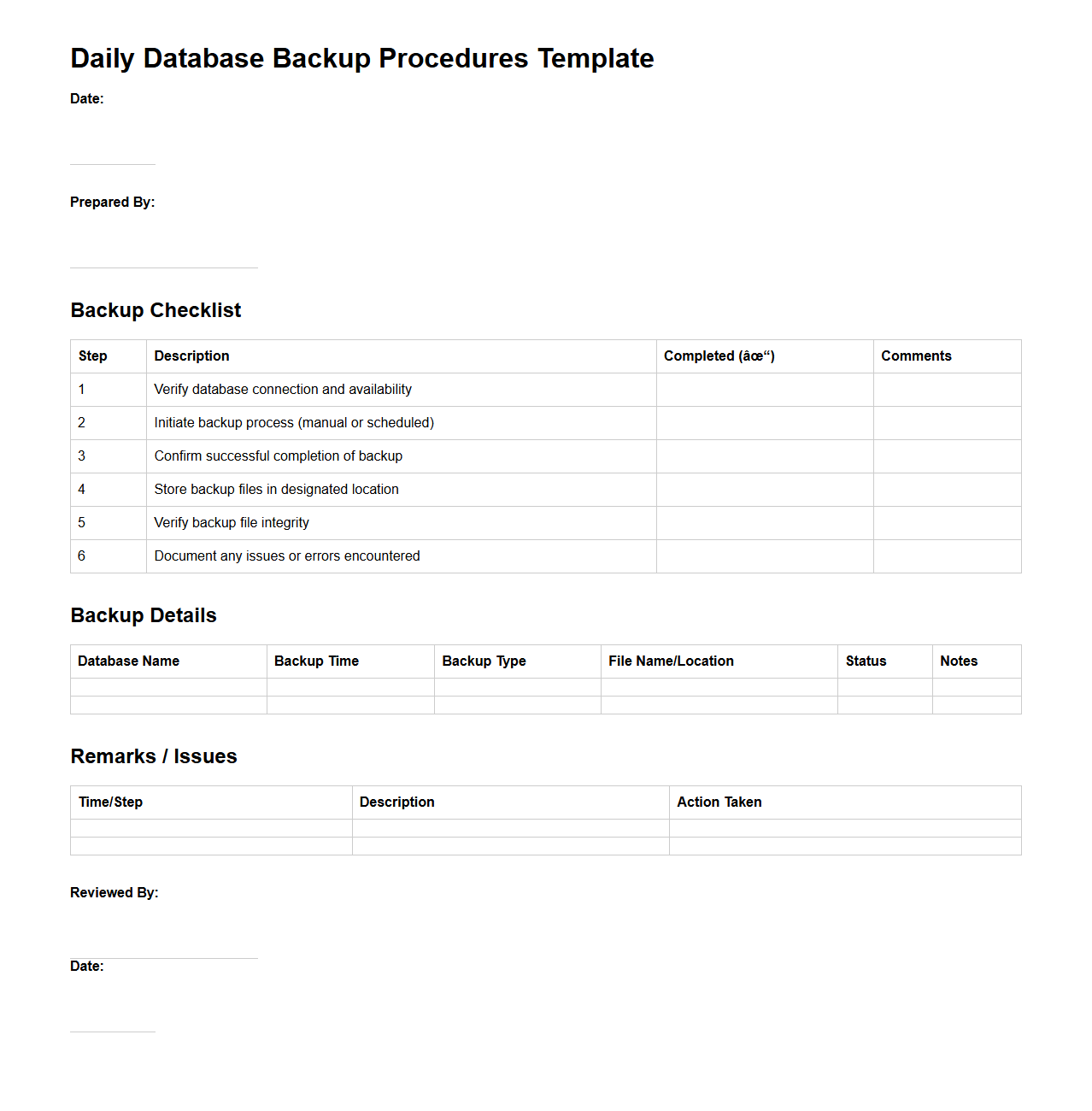
Daily Database Backup Procedures Template
The
Daily Database Backup Procedures Template document outlines a standardized process for performing routine backups of database systems to ensure data integrity and availability. It typically includes detailed steps for initiating backups, verifying backup success, and maintaining backup logs for audit purposes. This template is essential for database administrators aiming to minimize data loss and streamline recovery efforts in case of system failures.
Incremental Backup Policy Outline
An
Incremental Backup Policy Outline document defines the structured approach to regularly capturing only the data that has changed since the last backup, optimizing storage space and reducing backup time. It specifies the schedule, retention periods, recovery objectives, and responsibilities to ensure data integrity and rapid restoration. Implementing this policy is critical for efficient data management and minimizing downtime in disaster recovery scenarios.
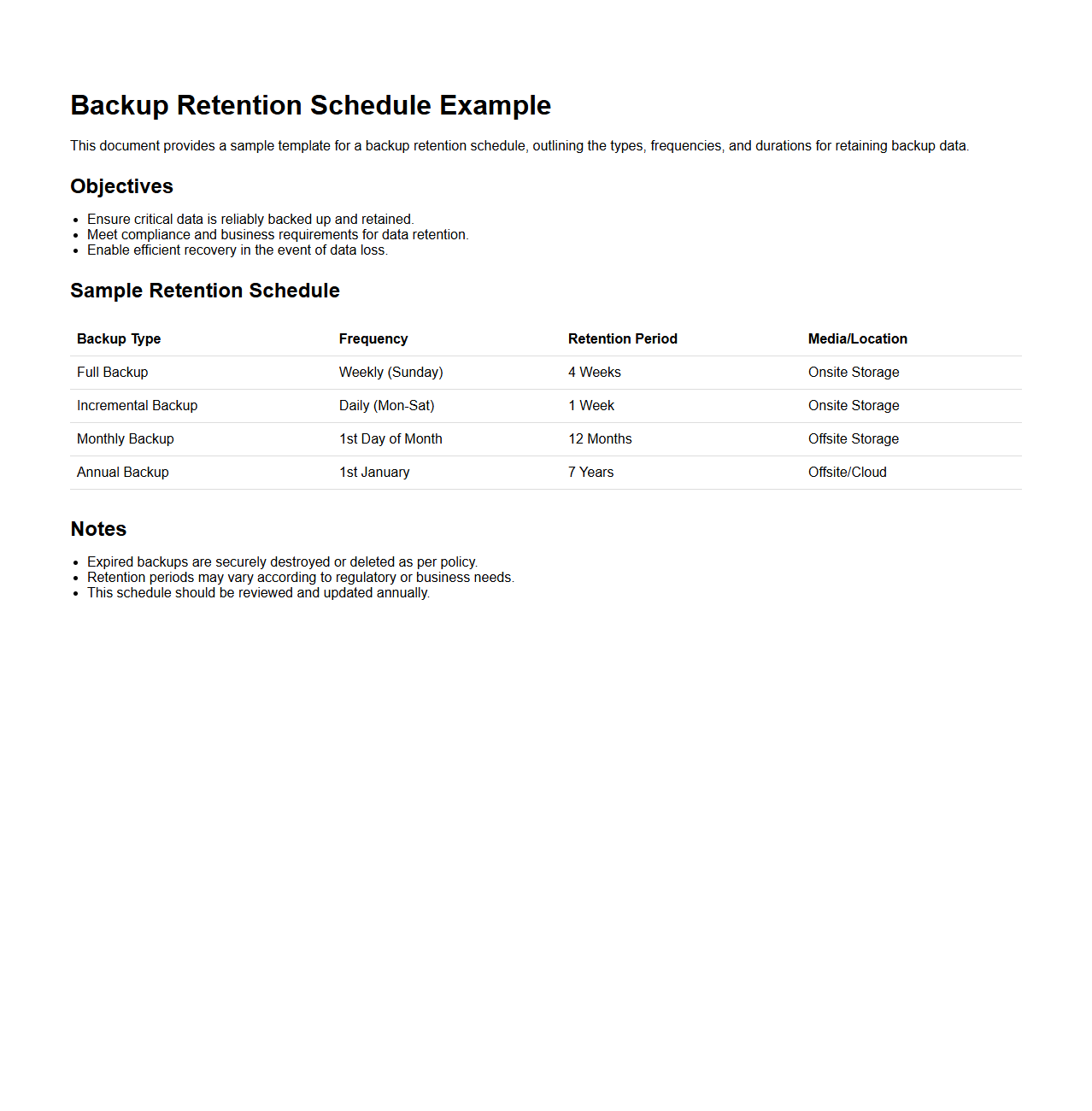
Backup Retention Schedule Example
A
Backup Retention Schedule Example document outlines the timeline and policies for storing and deleting backup data to ensure data availability and compliance with organizational or regulatory requirements. It specifies retention periods for different types of backups, such as daily, weekly, and monthly, guiding IT teams on when to archive or purge data. This document helps optimize storage resources while protecting against data loss and supporting disaster recovery processes.
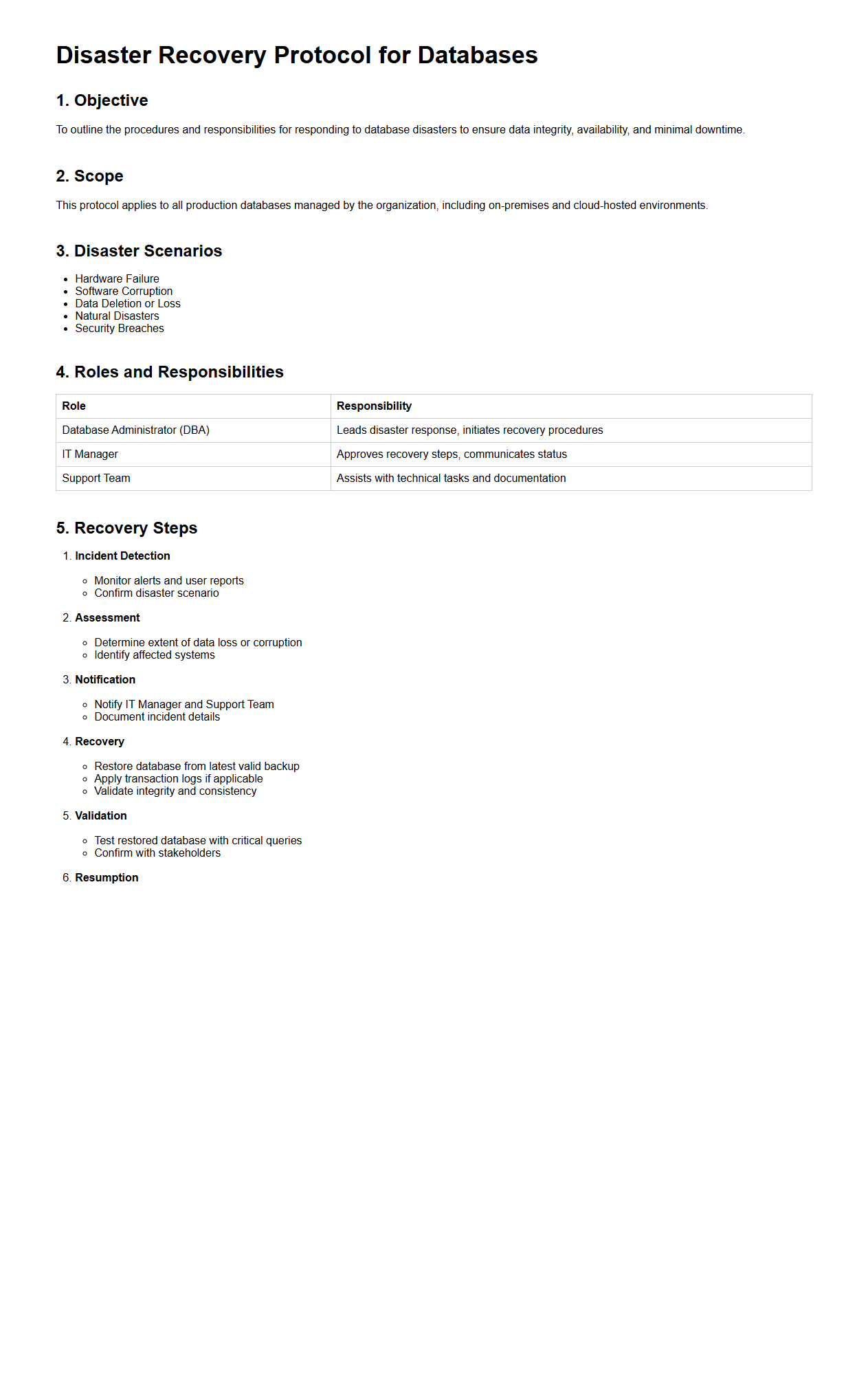
Disaster Recovery Protocol for Databases
A
Disaster Recovery Protocol for Databases document outlines structured procedures and strategies to restore database systems after unexpected events such as hardware failures, cyberattacks, or natural disasters. It specifies backup schedules, recovery point objectives (RPO), recovery time objectives (RTO), and roles responsible for executing recovery tasks. This document ensures data integrity, minimizes downtime, and supports business continuity by providing clear guidelines for timely database restoration.
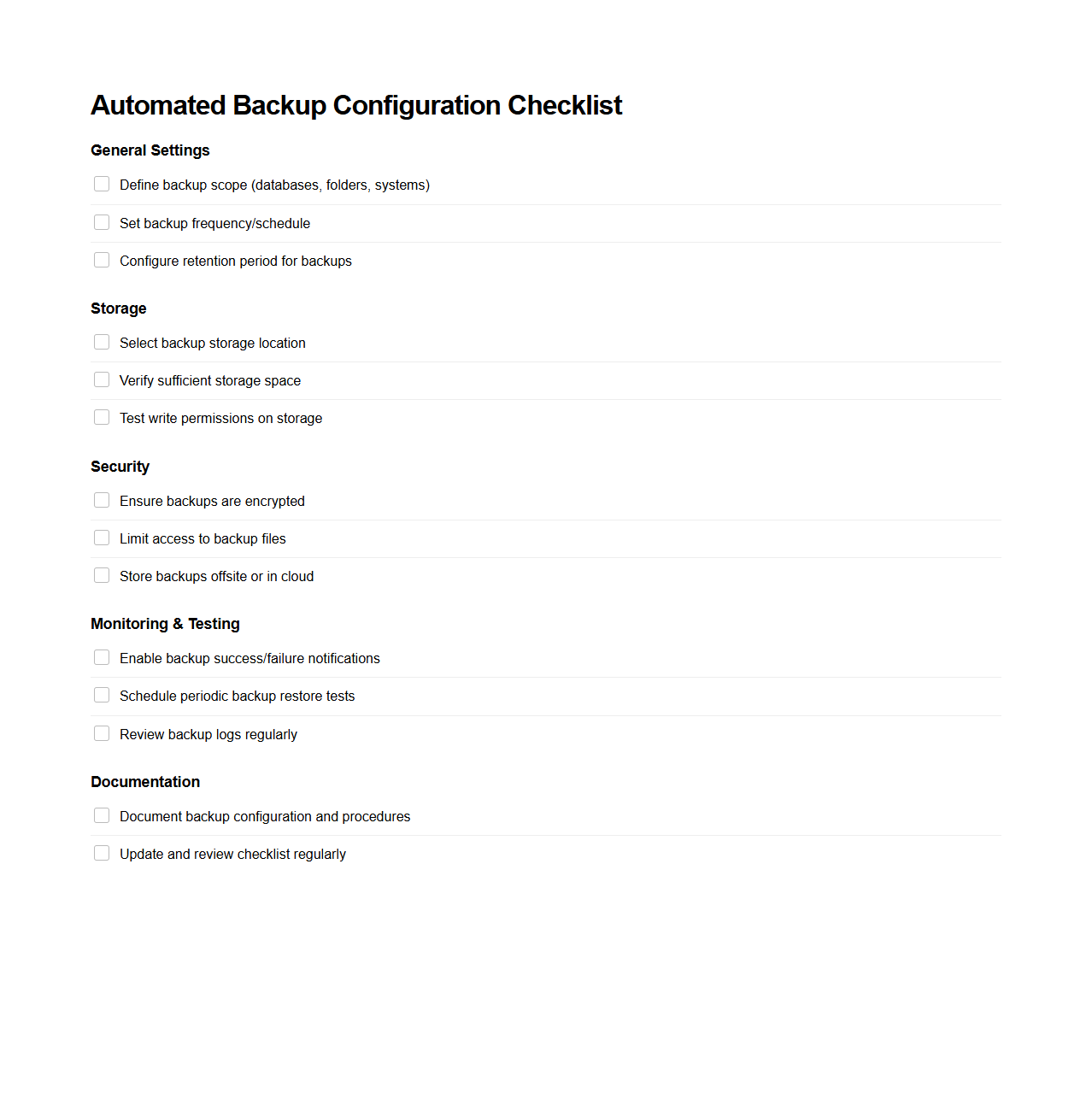
Automated Backup Configuration Checklist
The
Automated Backup Configuration Checklist document outlines essential steps and best practices to ensure reliable and consistent data backup processes through automation. It provides a detailed list of configuration settings, validation criteria, and schedules to minimize data loss risks and streamline disaster recovery efforts. This checklist aids IT teams in implementing and verifying automated backup systems to enhance data integrity and security.
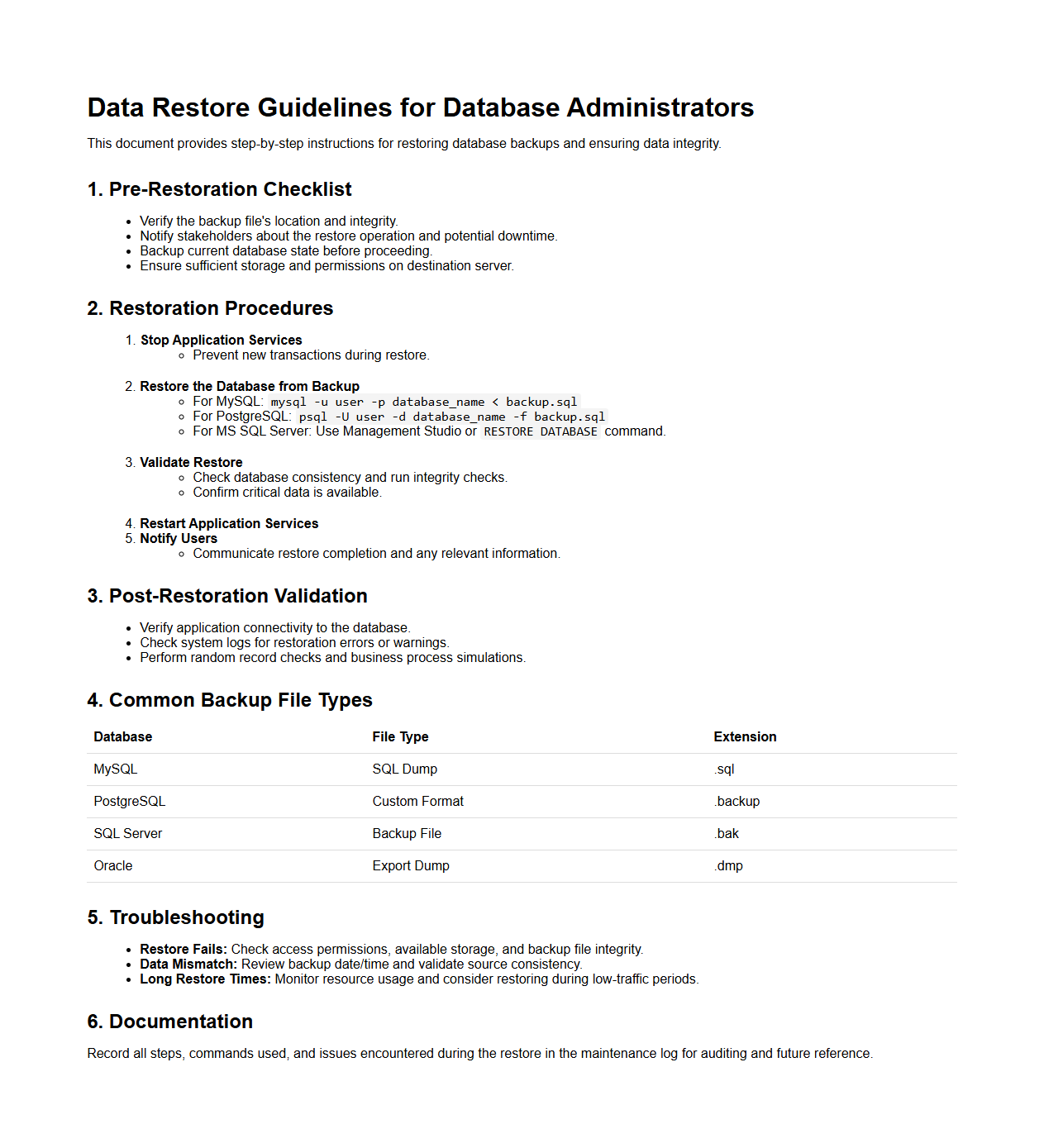
Data Restore Guidelines for Database Administrators
The
Data Restore Guidelines for Database Administrators document provides comprehensive procedures and best practices for efficiently recovering data in case of system failures or data corruption. It outlines step-by-step instructions for backup restoration, verification of data integrity, and minimizing downtime during restore operations. This guideline ensures database availability and data consistency, crucial for maintaining business continuity and disaster recovery strategies.
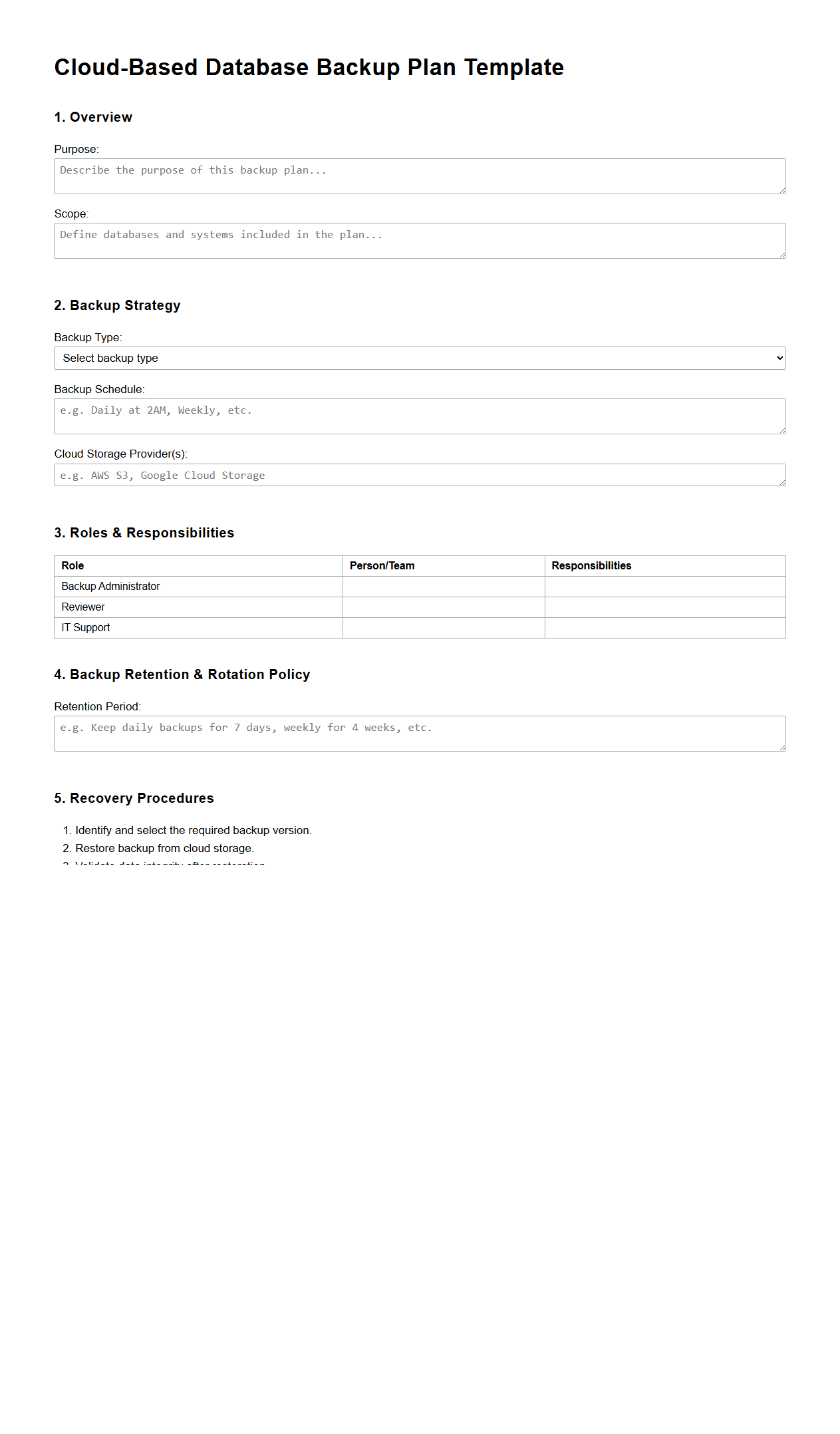
Cloud-Based Database Backup Plan Template
A
Cloud-Based Database Backup Plan Template document outlines a structured strategy for securely backing up databases to cloud storage, ensuring data integrity and quick recovery in case of data loss or system failure. It typically includes detailed procedures for backup frequency, data encryption methods, storage locations, and recovery testing schedules. This template is essential for organizations aiming to maintain continuous data protection while leveraging the scalability and reliability of cloud infrastructure.
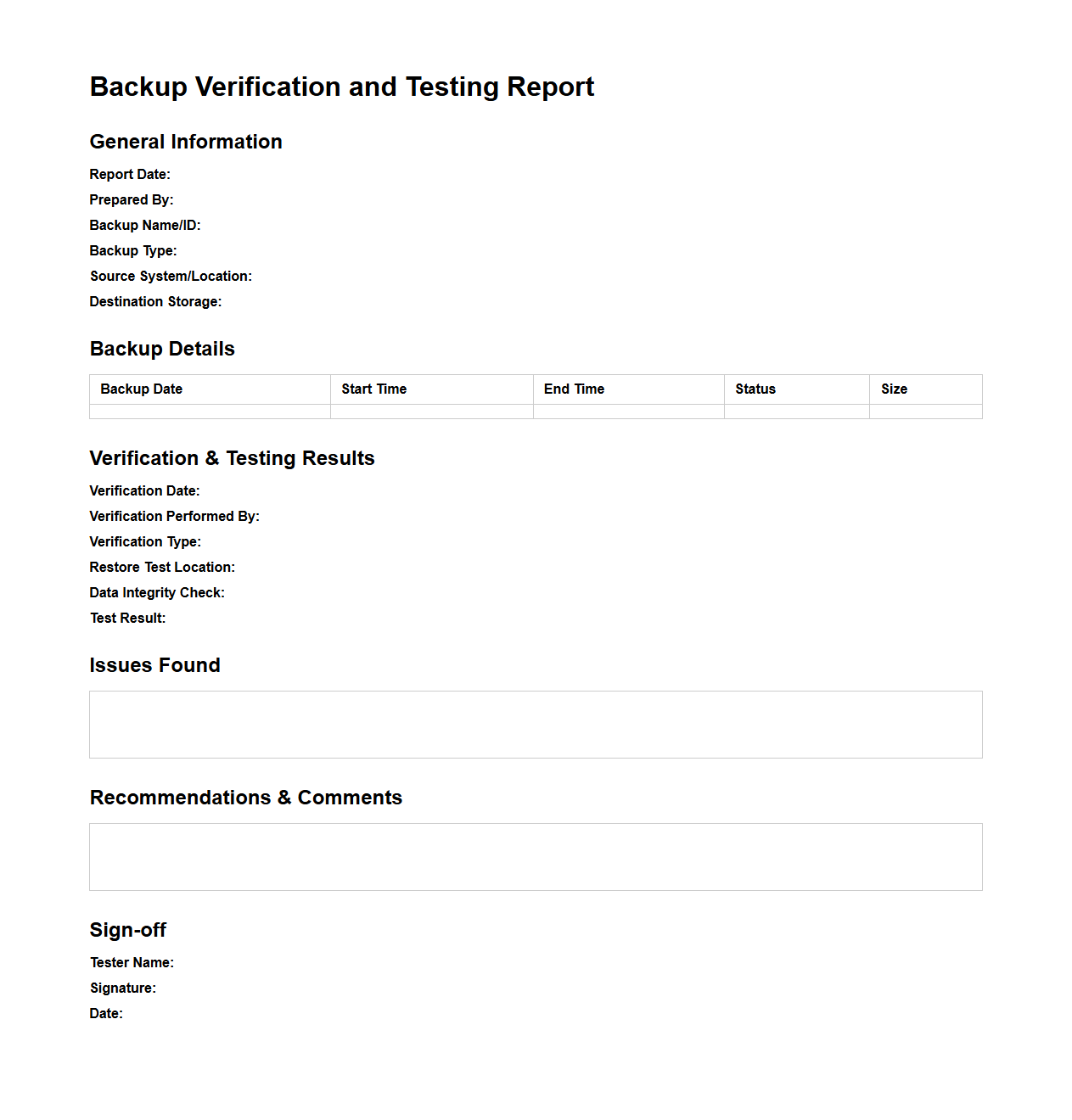
Backup Verification and Testing Report
A
Backup Verification and Testing Report document provides a detailed assessment of backup processes to ensure data integrity, reliability, and recoverability. It includes the results of scheduled tests, validation of backup completeness, and identification of potential issues or failures. This report is essential for maintaining compliance with data protection policies and minimizing the risk of data loss in disaster recovery scenarios.
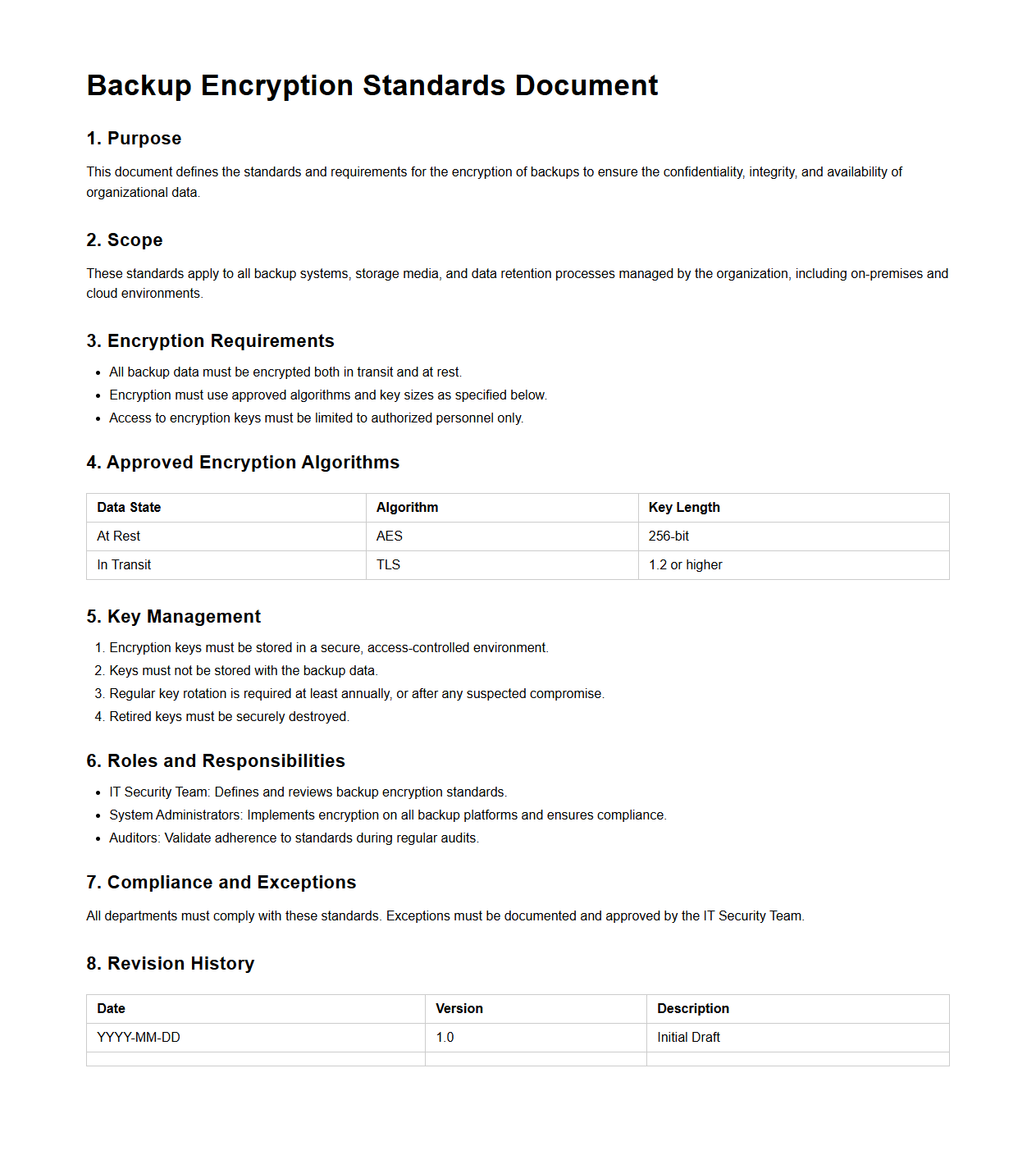
Backup Encryption Standards Document
The
Backup Encryption Standards Document outlines the required protocols and algorithms to ensure data protection during backup processes. It specifies encryption methods, key management practices, and compliance requirements to safeguard sensitive information from unauthorized access. This document is essential for maintaining data confidentiality and integrity across all backup operations within an organization.
Offsite Backup Storage Policy Example
An
Offsite Backup Storage Policy Example document outlines the procedures and guidelines for securely storing backup data at a location separate from the primary site to ensure data availability in case of onsite failures or disasters. It defines roles, responsibilities, encryption standards, retention periods, and access controls to protect backup integrity and confidentiality. This policy helps organizations maintain compliance with data protection regulations while minimizing the risk of data loss.
Retention Policies for Different Database Environments
The backup strategy defines retention policies tailored to various database environments to ensure data availability and compliance. Development and testing databases have shorter retention periods, typically 7 to 14 days, to optimize storage use. In contrast, production databases require longer retention, often 30 to 90 days, to safeguard critical business data.
Backup Encryption Procedures and Standards
The document mandates the use of encryption standards like AES-256 to secure backup data both in transit and at rest. It specifies protocols to encrypt backups before storage, ensuring data confidentiality and integrity. This approach complies with industry regulations and internal security policies.
Automated Monitoring Tools for Backup Verification
The strategy recommends deploying automated monitoring tools such as backup verification software that performs automatic integrity checks. These tools alert administrators in real-time about backup failures or inconsistencies. Integration with centralized monitoring dashboards is also emphasized for streamlined management.
Integration of Off-site and Cloud Backup Solutions
Off-site and cloud backup solutions are fully integrated into the guidelines to enhance disaster recovery capabilities. The document outlines secure transfer methods and scheduling to maintain up-to-date copies in geographically separate locations. It also highlights compliance with cloud security standards and periodic synchronization checks.
Disaster Recovery Testing Protocols
The backup strategy specifies rigorous disaster recovery testing protocols including scheduled simulations and failover drills. These tests validate the effectiveness of backup restoration and system recovery within defined recovery time objectives (RTO). Detailed documentation and continuous improvement practices are mandated to address any identified gaps.
More Technology Templates