A Network Configuration Document Sample for Wireless Networks provides a detailed template outlining the setup parameters, security settings, and hardware configurations required for a wireless network. It includes essential information such as SSID names, encryption methods, IP addressing schemes, and access point placements to ensure optimal performance and security. This document serves as a crucial reference for network administrators during deployment and troubleshooting processes.
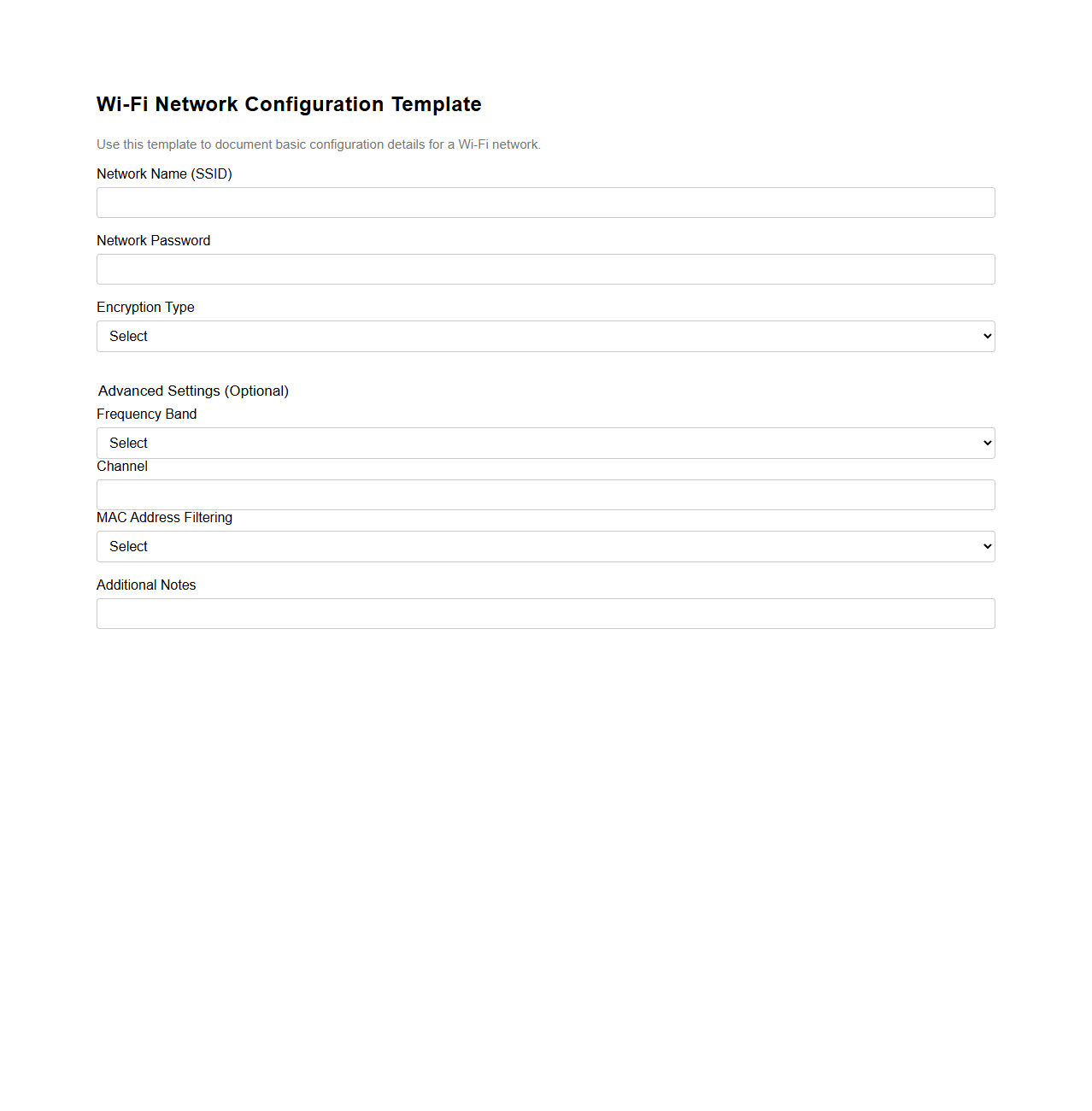
Wi-Fi Network Configuration Template
A
Wi-Fi Network Configuration Template document outlines standardized settings and parameters to streamline the setup of wireless networks across multiple devices or locations. It typically includes SSID names, security protocols such as WPA3, encryption methods, authentication details, and IP addressing schemes to ensure consistent network performance and security. Using this template reduces configuration errors, enhances network management efficiency, and supports compliance with organizational IT policies.
Wireless Access Point Setup Document
A
Wireless Access Point Setup Document provides detailed instructions for configuring a wireless access point, including network settings, security protocols, and hardware installation steps. It ensures proper integration with existing networks to optimize connectivity and signal strength. This document serves as a critical resource for IT professionals to maintain secure and efficient wireless environments.
Corporate WLAN Configuration Guide
The
Corporate WLAN Configuration Guide document provides detailed instructions and best practices for setting up and managing wireless local area networks within a corporate environment. It covers essential topics such as security protocols, network optimization, access point deployment, and device compatibility to ensure reliable and secure connectivity. This guide is designed to help IT professionals configure WLANs efficiently, minimizing downtime and enhancing overall network performance.
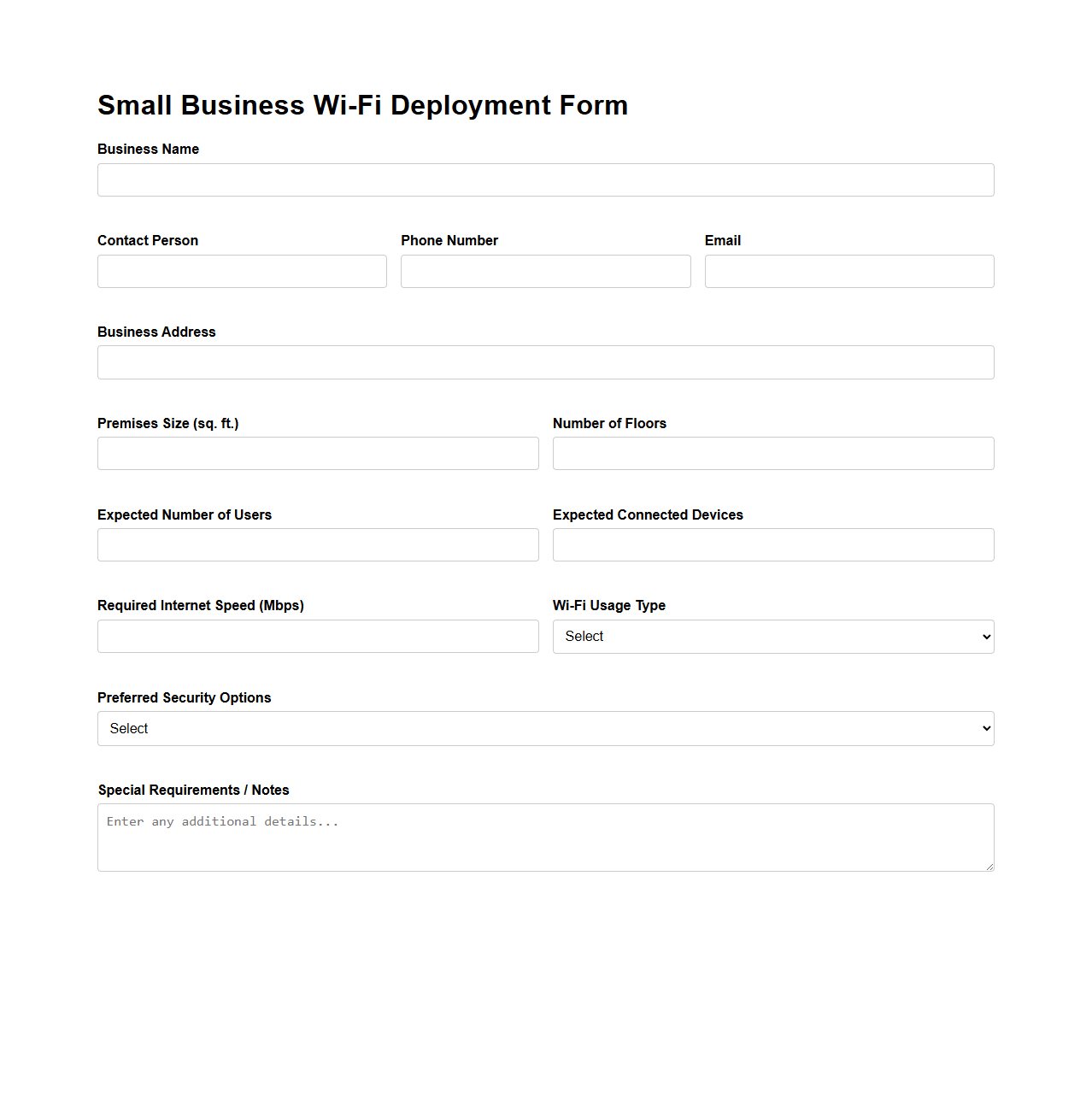
Small Business Wi-Fi Deployment Form
The
Small Business Wi-Fi Deployment Form document is designed to capture essential information required for setting up a wireless network tailored to the specific needs of a small business. It typically includes fields for business location, network specifications, hardware requirements, and security protocols to ensure a seamless and secure Wi-Fi installation. This form streamlines the deployment process by providing technicians and IT professionals with clear, organized data to optimize network performance and coverage.
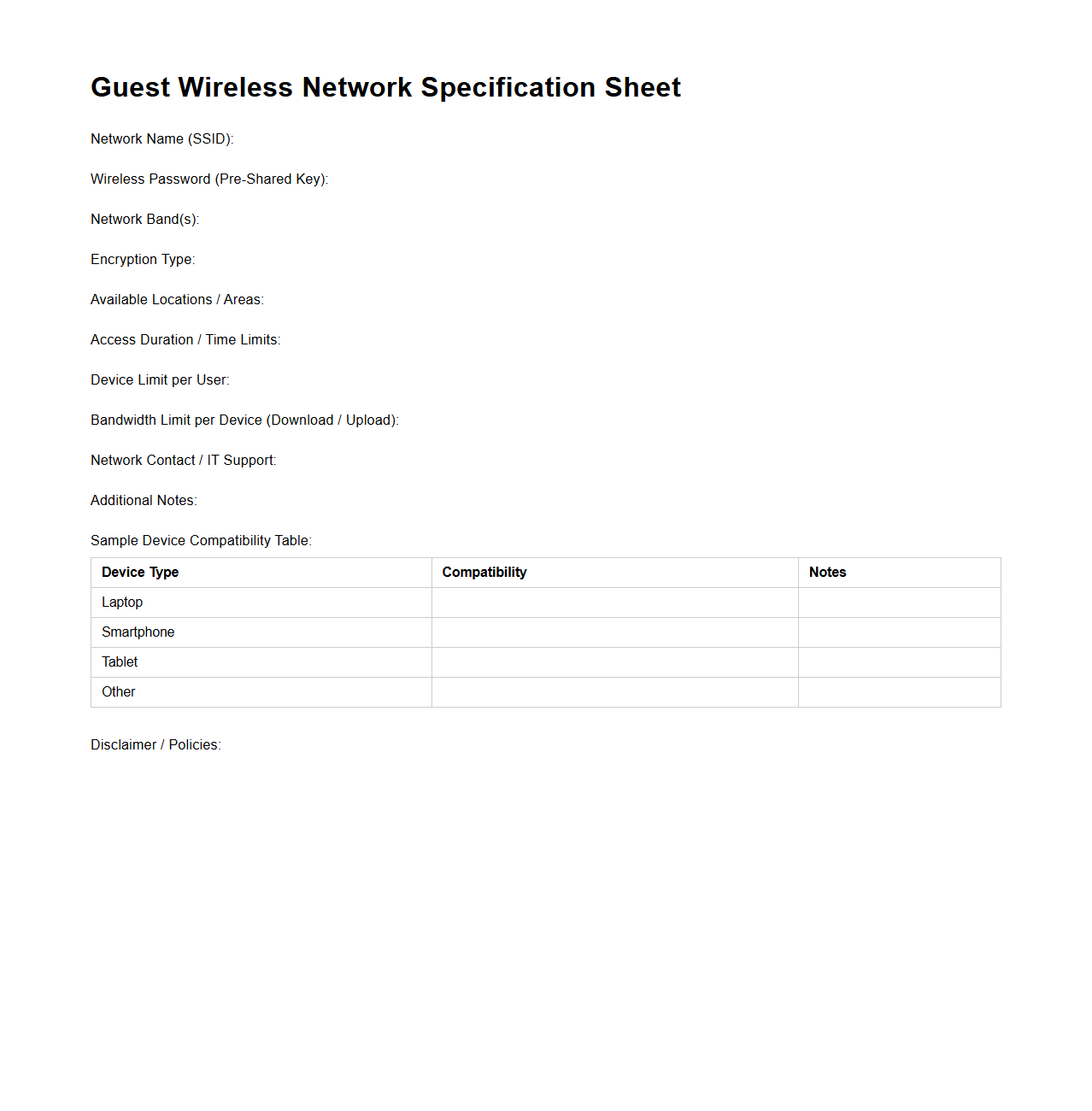
Guest Wireless Network Specification Sheet
A
Guest Wireless Network Specification Sheet document outlines the technical and security requirements for setting up a wireless network specifically for guest access. It includes details such as network SSID, encryption standards, bandwidth allocation, and user authentication methods to ensure secure and efficient connectivity. This document serves as a guideline for IT teams to implement and manage guest Wi-Fi services consistently across an organization.
Secure Wireless Network Design Document
A
Secure Wireless Network Design Document outlines the architectural framework and security protocols necessary to establish a protected wireless communication environment. It details encryption methods, authentication procedures, and access control policies to mitigate risks such as unauthorized access, data breaches, and signal interference. This document serves as a vital reference for network engineers and security professionals to ensure the wireless infrastructure adheres to organizational security standards and compliance requirements.
Enterprise Wireless Infrastructure Sample
An
Enterprise Wireless Infrastructure Sample document provides a detailed framework for designing, deploying, and managing wireless network systems within a corporate environment. It outlines best practices, technical specifications, security protocols, and scalability considerations to ensure robust and reliable wireless connectivity across all enterprise locations. This document serves as a critical guide for IT teams to implement efficient wireless solutions that support business operations and enhance workforce productivity.
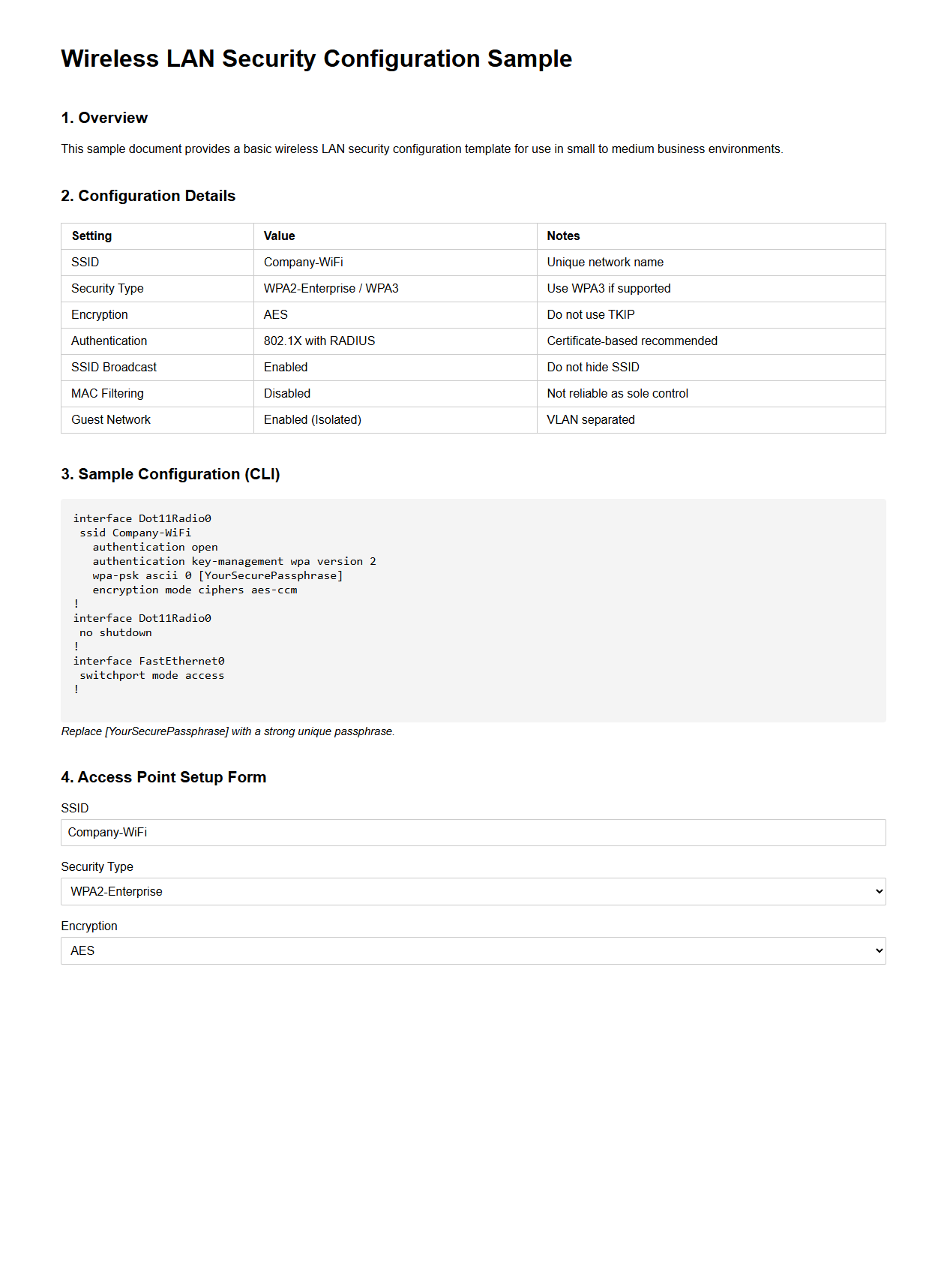
Wireless LAN Security Configuration Sample
The
Wireless LAN Security Configuration Sample document provides detailed guidelines and best practices for securing wireless local area networks (WLANs). It includes recommended settings for encryption protocols, authentication methods, and access control measures to protect sensitive data from unauthorized access. Network administrators rely on this document to implement robust security configurations that ensure the confidentiality, integrity, and availability of wireless communications.
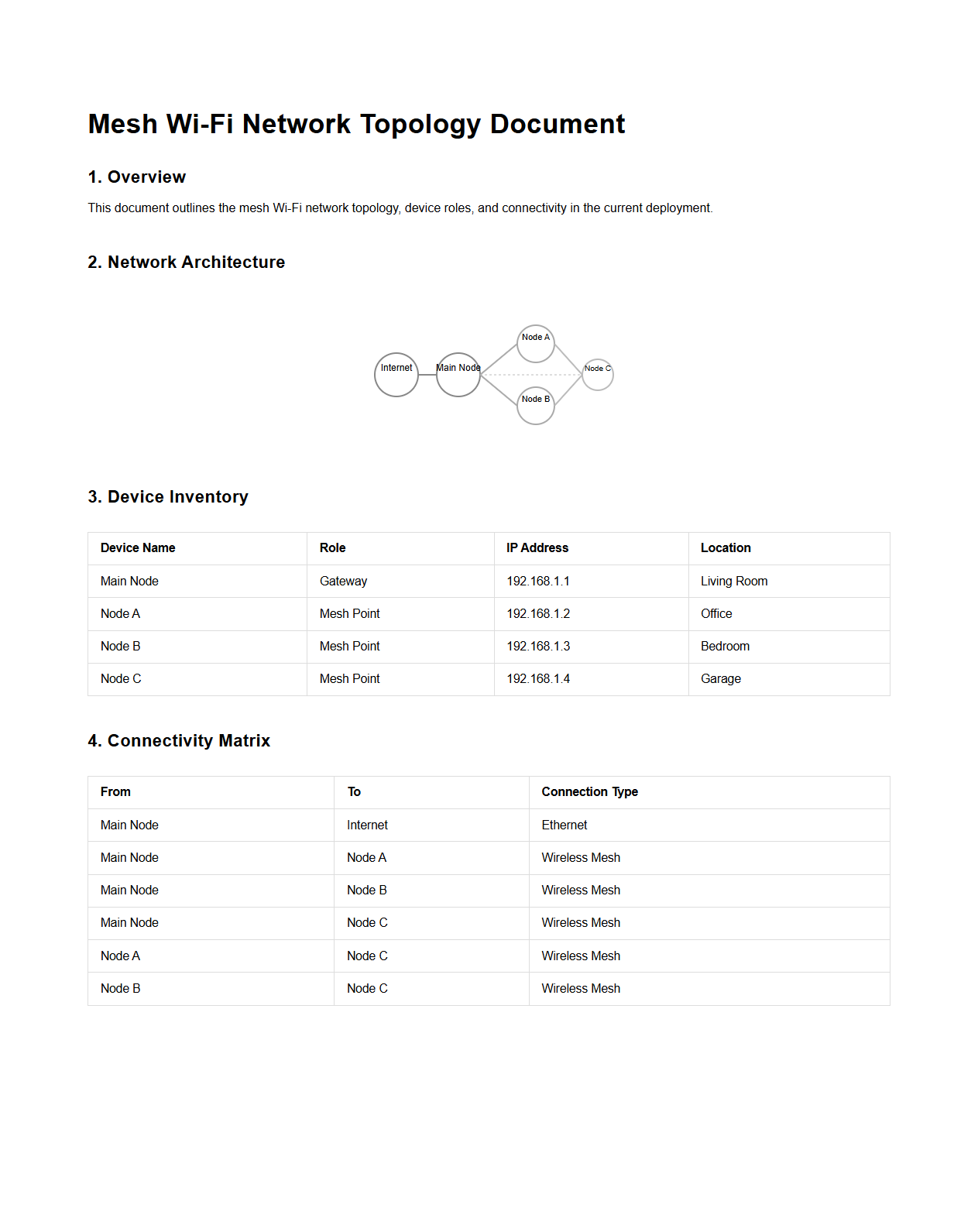
Mesh Wi-Fi Network Topology Document
A
Mesh Wi-Fi Network Topology Document outlines the structure and configuration of a mesh Wi-Fi system, detailing how multiple nodes communicate to provide seamless wireless coverage. It includes specifications on node placement, signal routing, and network protocols to optimize connectivity and minimize dead zones. This document serves as a guide for network deployment, troubleshooting, and performance optimization in environments requiring robust and scalable wireless solutions.
Wireless Network VLAN Assignment Template
The
Wireless Network VLAN Assignment Template document serves as a structured framework for mapping wireless devices and access points to specific VLANs, ensuring efficient network segmentation and security. It details the assignment criteria based on device type, user roles, or location, facilitating consistent configuration across the wireless infrastructure. This template helps network administrators streamline VLAN management and maintain optimal performance in complex wireless environments.
What security protocols are specified for SSID broadcasting in the network configuration document?
The document specifies WPA3 encryption as the primary security protocol for SSID broadcasting to ensure maximum protection against unauthorized access. It details the use of 802.1X authentication integrated with a RADIUS server for robust user verification. Additionally, the configuration prohibits broadcasting SSIDs on guest networks to enhance security through obscurity.
How does the document address VLAN segmentation for wireless client isolation?
The network configuration mandates strict VLAN segmentation to isolate wireless clients and prevent lateral movement within the network. Each SSID is mapped to a specific VLAN, ensuring that traffic from different user groups remains segregated. This segmentation is reinforced by Access Control Lists (ACLs) to control inter-VLAN communication.
Are there predefined QoS policies for VoIP traffic outlined in the configuration letter?
Yes, the document outlines predefined QoS policies prioritizing VoIP traffic to guarantee low latency and jitter. It uses traffic classification and marking techniques such as DSCP to give VoIP packets higher priority over data traffic. These policies ensure clear voice communication even in congested network scenarios.
How does the document recommend handling roaming between APs for seamless connectivity?
The document recommends configuring fast roaming protocols like 802.11r to enable seamless handoff between Access Points (APs). It emphasizes maintaining continuous session integrity without reauthentication delays during roaming. Additionally, optimized AP placement and consistent SSID configuration are advised for improved roaming performance.
What backup and redundancy measures are documented for wireless controller failures?
The configuration includes deploying redundant wireless controllers with active-passive failover mechanisms to ensure high availability. It specifies automatic session failover to backup controllers to minimize downtime during failures. Regular configuration backups and monitoring are also part of the documented resilience strategy.
More Technology Templates