A Penetration Test Report Document Sample for Web Applications provides a detailed analysis of security vulnerabilities identified during testing. It includes findings, risk assessments, and recommended remediation steps to enhance the application's security posture. This document serves as a critical tool for developers and security teams to understand and address potential threats effectively.
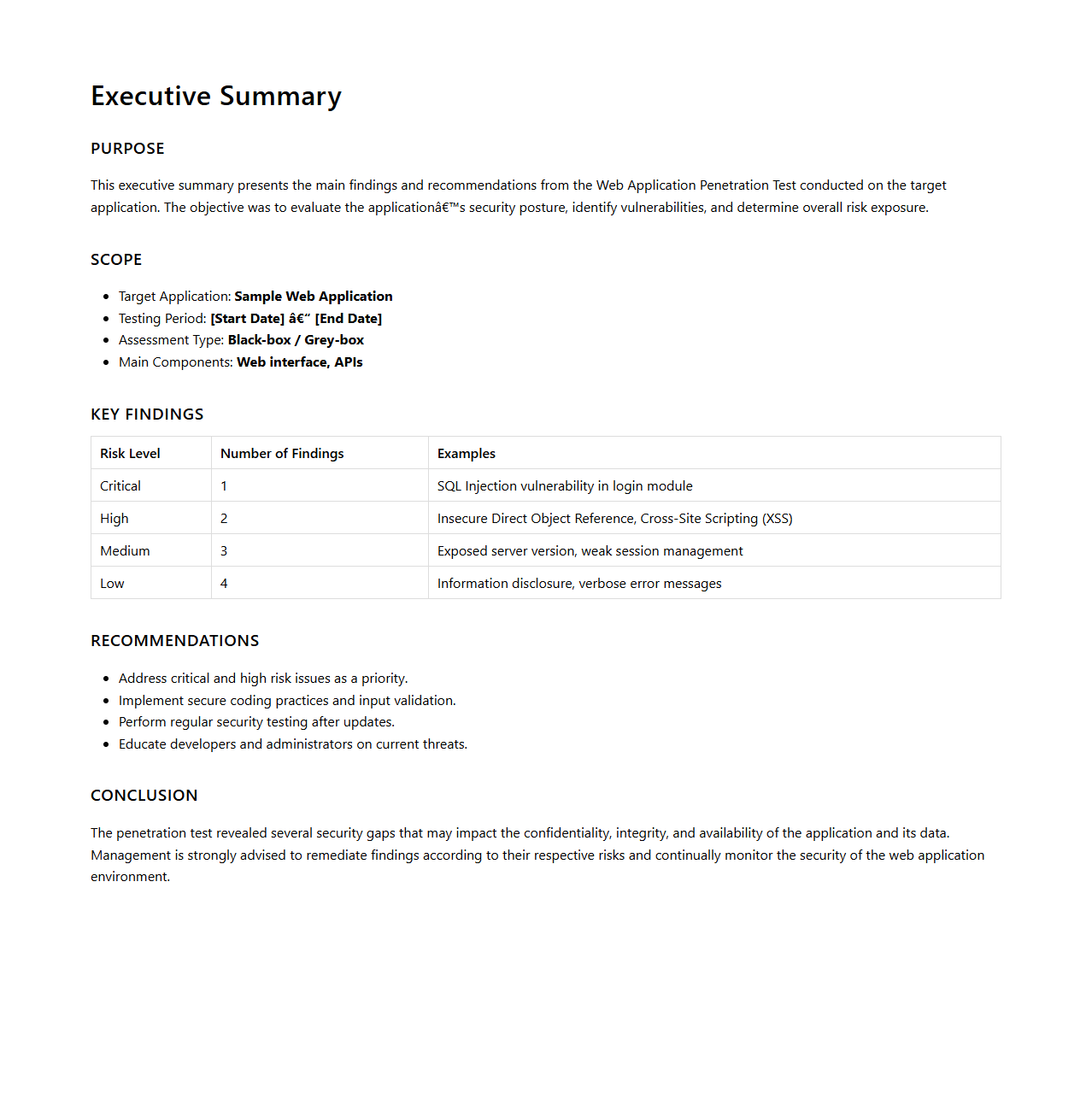
Executive Summary for Web Application Penetration Test
The
Executive Summary in a Web Application Penetration Test document provides a high-level overview of the security assessment's scope, key findings, and overall risk posture. It highlights critical vulnerabilities identified, their potential impact on business operations, and strategic recommendations to mitigate threats. This summary is designed for stakeholders to quickly grasp the security status without technical details, enabling informed decision-making.
Scope and Methodology Section for Web Application Testing
The
Scope and Methodology Section in a Web Application Testing document defines the boundaries of the testing process, detailing which features, functionalities, and modules will be tested and which are excluded. It outlines the specific testing approaches, techniques, and tools employed to validate the web application's performance, security, and usability. This section ensures clarity on the extent of testing efforts and establishes a structured framework for systematic evaluation.
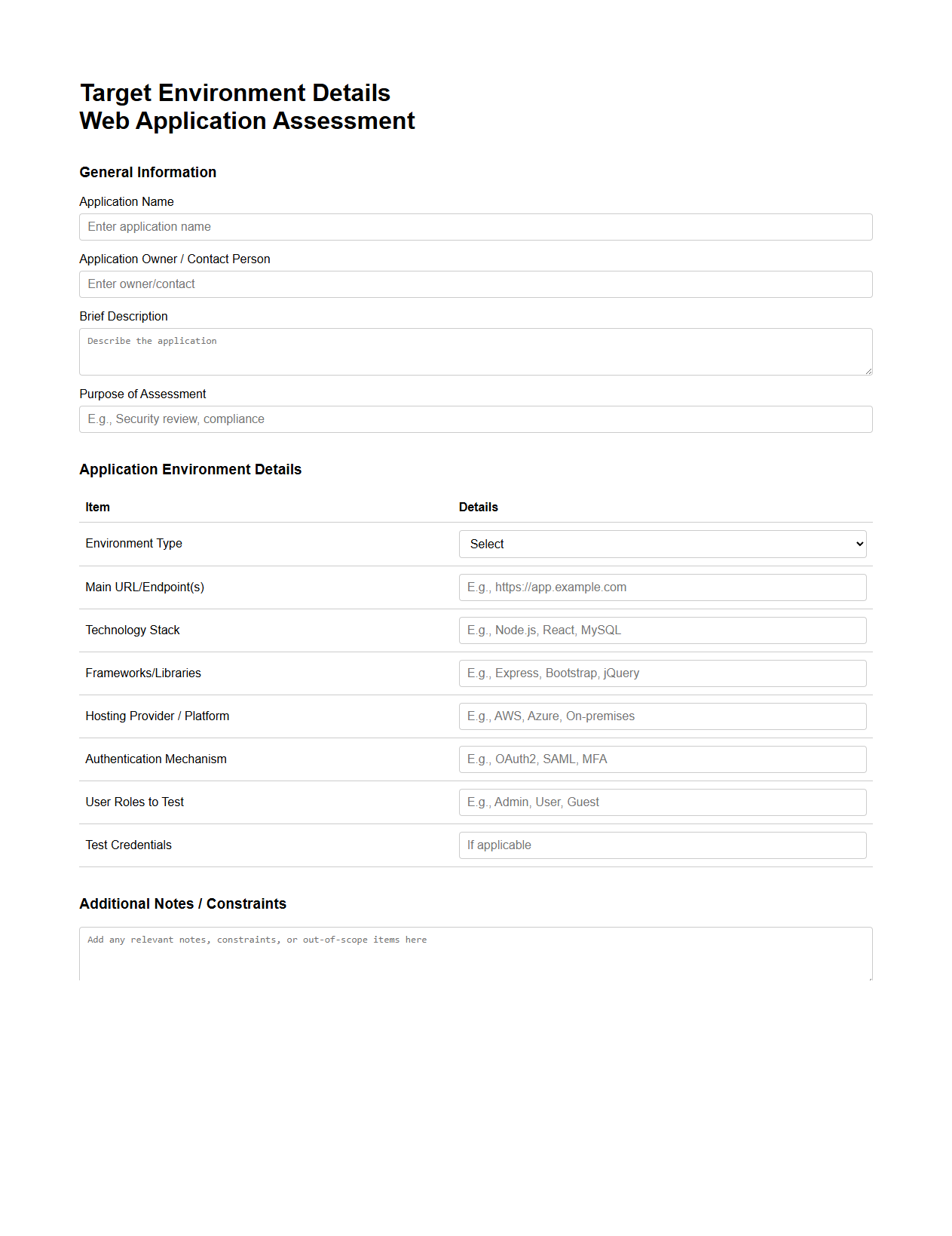
Target Environment Details for Web Application Assessments
The
Target Environment Details for Web Application Assessments document provides comprehensive information about the infrastructure where the web application operates, including details on servers, network configurations, software versions, and security controls. This document is essential for understanding the context and potential vulnerabilities within the specific environment, ensuring accurate risk analysis. It enables assessors to tailor security testing methodologies based on the unique characteristics and constraints of the deployment setting.
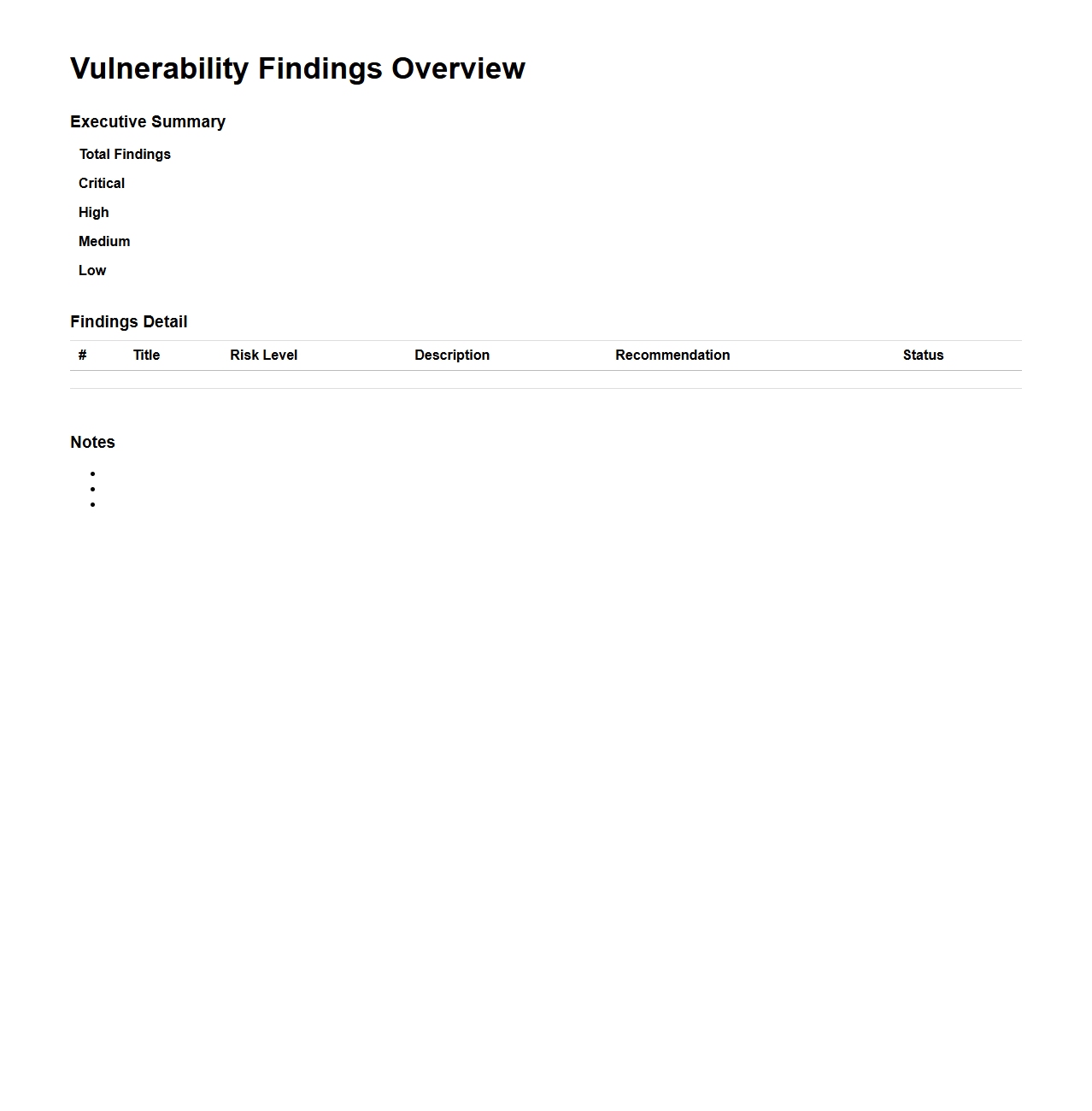
Vulnerability Findings Overview for Web Applications
The
Vulnerability Findings Overview for Web Applications document provides a comprehensive summary of identified security weaknesses within a web application, detailing their nature, impact, and potential risks. It categorizes vulnerabilities based on severity levels and highlights critical issues such as SQL injection, cross-site scripting (XSS), and authentication flaws. This overview serves as a crucial reference for developers and security teams to prioritize remediation efforts and strengthen the application's security posture.
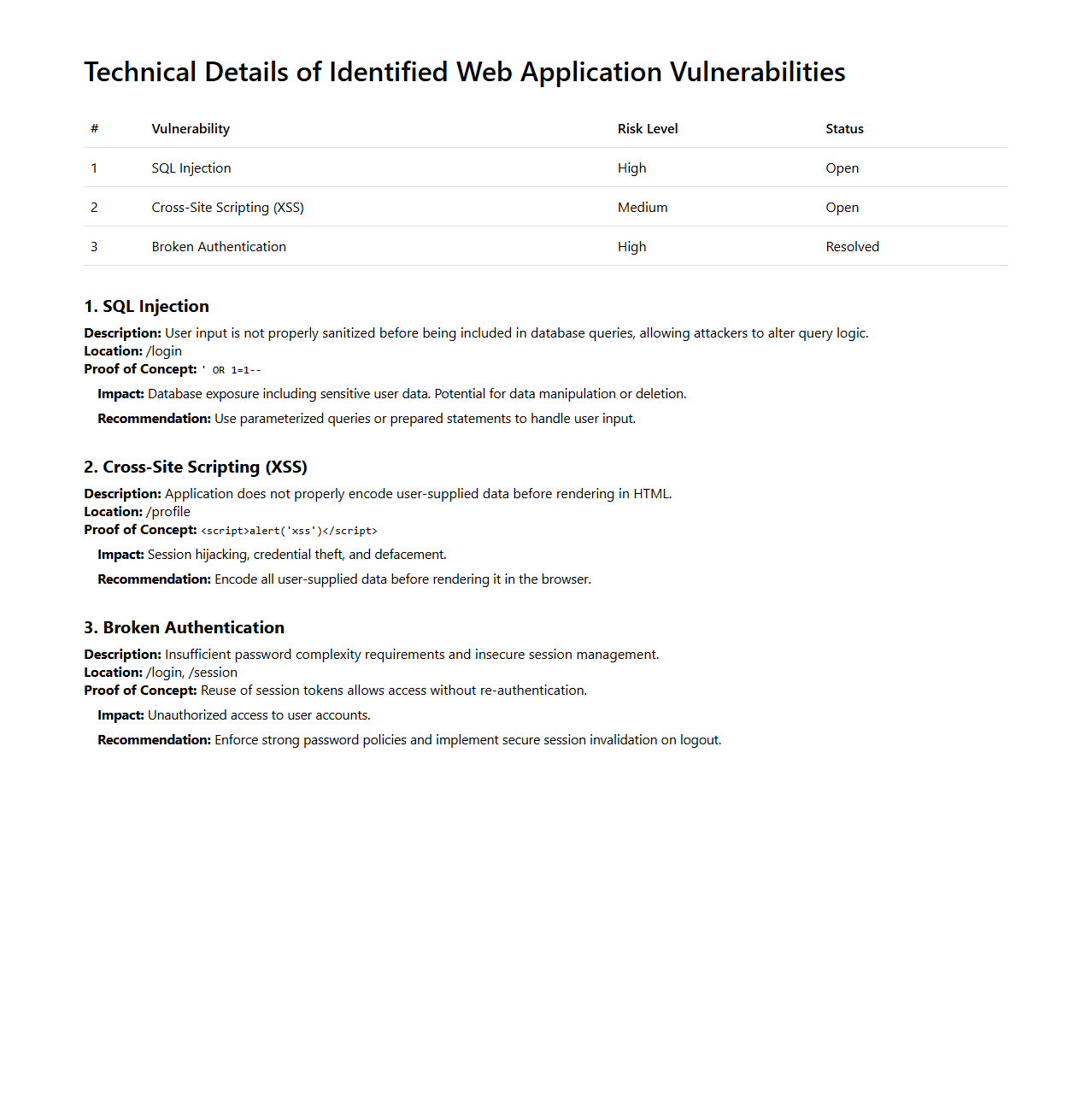
Technical Details of Identified Web Application Vulnerabilities
The
Technical Details of Identified Web Application Vulnerabilities document provides an in-depth analysis of security flaws discovered within a web application, including the specific nature, origin, and impact of each vulnerability. It details the exploited entry points, attack vectors, and underlying coding or configuration issues responsible for the security gaps. This document serves as a critical resource for developers and security teams to understand root causes and implement precise remediation measures.
Risk Assessment Matrix for Web Application Penetration Test
A
Risk Assessment Matrix for a Web Application Penetration Test document systematically categorizes potential security vulnerabilities by their likelihood and impact, enabling organizations to prioritize remediation efforts effectively. This matrix visually represents threat levels, helping security teams identify high-risk areas that require immediate attention to reduce exposure to cyberattacks. It supports decision-making by quantifying risks and aligning them with business objectives, optimizing resource allocation for enhanced web application security.
Remediation Recommendations for Exploited Web Application Issues
The
Remediation Recommendations for Exploited Web Application Issues document provides targeted guidance to address vulnerabilities identified in compromised web applications. It outlines specific corrective actions to eliminate security flaws such as injection attacks, cross-site scripting, and improper authentication mechanisms. This document serves as a practical resource to enhance web application security and prevent future exploitation.
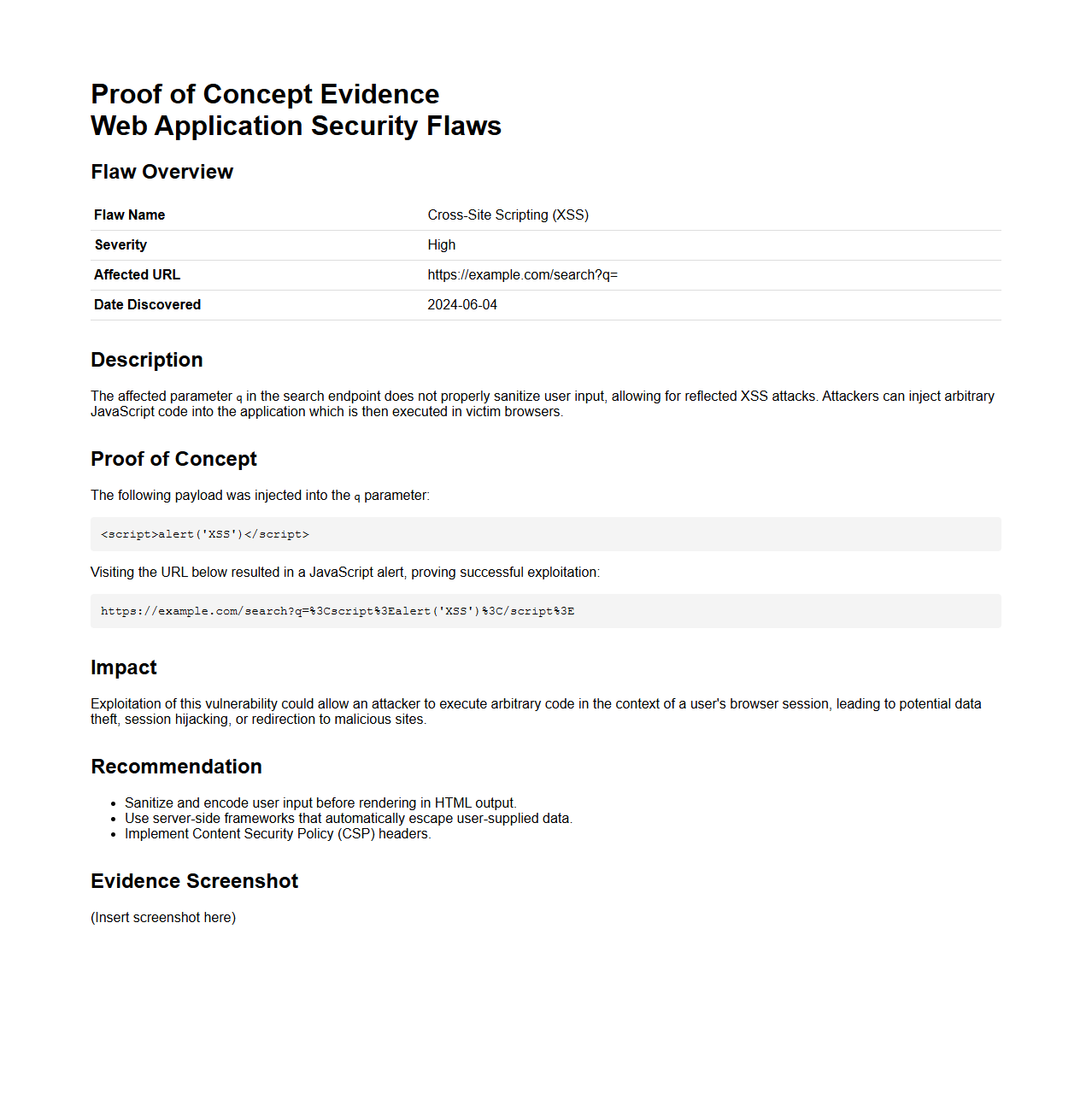
Proof of Concept Evidence for Web Application Security Flaws
The
Proof of Concept Evidence for Web Application Security Flaws document provides detailed demonstration and validation of identified vulnerabilities within a web application. It includes step-by-step reproduction of the security issues, supporting screenshots, or code snippets to verify the flaw's existence and potential impact. This document is essential for developers and security teams to understand, prioritize, and remediate security risks effectively.
Conclusion and Key Takeaways of Web Application Penetration Testing
The
Conclusion and Key Takeaways of a Web Application Penetration Testing document summarize the critical findings, vulnerabilities identified, and the overall security posture of the tested web application. This section provides actionable recommendations for mitigation strategies and emphasizes the importance of implementing regular security assessments to protect against evolving cyber threats. It serves as a concise reference for stakeholders to understand the risks and necessary steps to enhance their web application's defense.
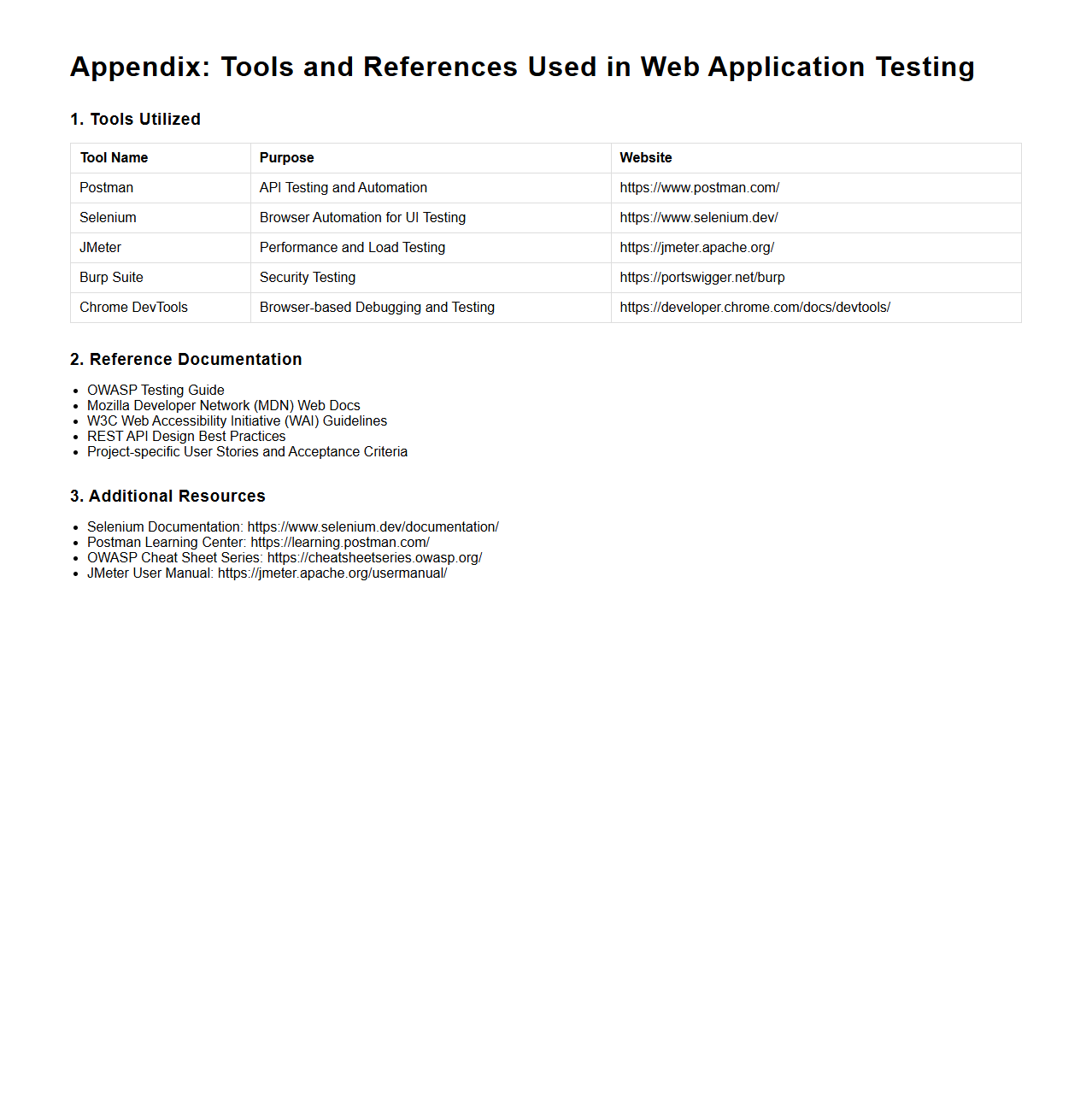
Appendix of Tools and References Used in Web Application Testing
The
Appendix of Tools and References Used in Web Application Testing document serves as a comprehensive resource listing essential software, frameworks, and authoritative sources employed throughout the testing process. This appendix provides detailed descriptions and links to automated testing tools, performance analyzers, security scanners, and relevant standards or guidelines adhered to during the evaluation. Including this appendix enhances the document's credibility and facilitates easy access to critical materials that support effective web application quality assurance.
What methodologies were followed in the web application penetration test report?
The penetration test report employed a comprehensive methodology based on industry-standard frameworks such as OWASP and NIST. It included both automated scanning tools and manual testing techniques to identify vulnerabilities. Additionally, the approach involved reconnaissance, vulnerability assessment, exploitation, and post-exploitation phases for thorough coverage.
Which specific OWASP Top 10 vulnerabilities were identified in the document?
The report highlighted several critical OWASP Top 10 vulnerabilities including Injection flaws, Cross-Site Scripting (XSS), and Broken Authentication. Sensitive data exposure and Security Misconfigurations were also frequently identified. Each vulnerability was detailed with impact analysis and real-world examples from the target application.
How are risk levels prioritized and categorized in the report findings?
Risk levels in the report are categorized as Critical, High, Medium, and Low based on impact and exploitability. The prioritization focuses on addressing Critical and High risks first to reduce immediate threats. This classification helps stakeholders systematically allocate resources for mitigation efforts.
What remediation steps are recommended for each critical issue discovered?
For each critical vulnerability, the report recommends tailored remediation strategies such as input validation, proper authentication mechanisms, and secure configuration changes. It emphasizes patching vulnerable components and implementing secure coding practices. Furthermore, adopting a continuous security testing regimen is advised for ongoing protection.
Does the report include evidence screenshots and Proof of Concept (PoC) for each vulnerability?
The report includes detailed evidence screenshots and Proof of Concept (PoC) code snippets for every identified vulnerability. These visual aids validate the presence and exploitability of the issues found. This approach enhances the clarity and credibility of the findings for technical and non-technical stakeholders alike.
More Technology Templates