A User Access Control Document Sample for Enterprise Systems outlines the procedures and policies for managing user permissions within a company's IT infrastructure. It ensures only authorized personnel have access to sensitive data and critical applications, reducing security risks and maintaining compliance with regulatory standards. This document serves as a benchmark for establishing robust access controls and enforcing accountability across enterprise systems.
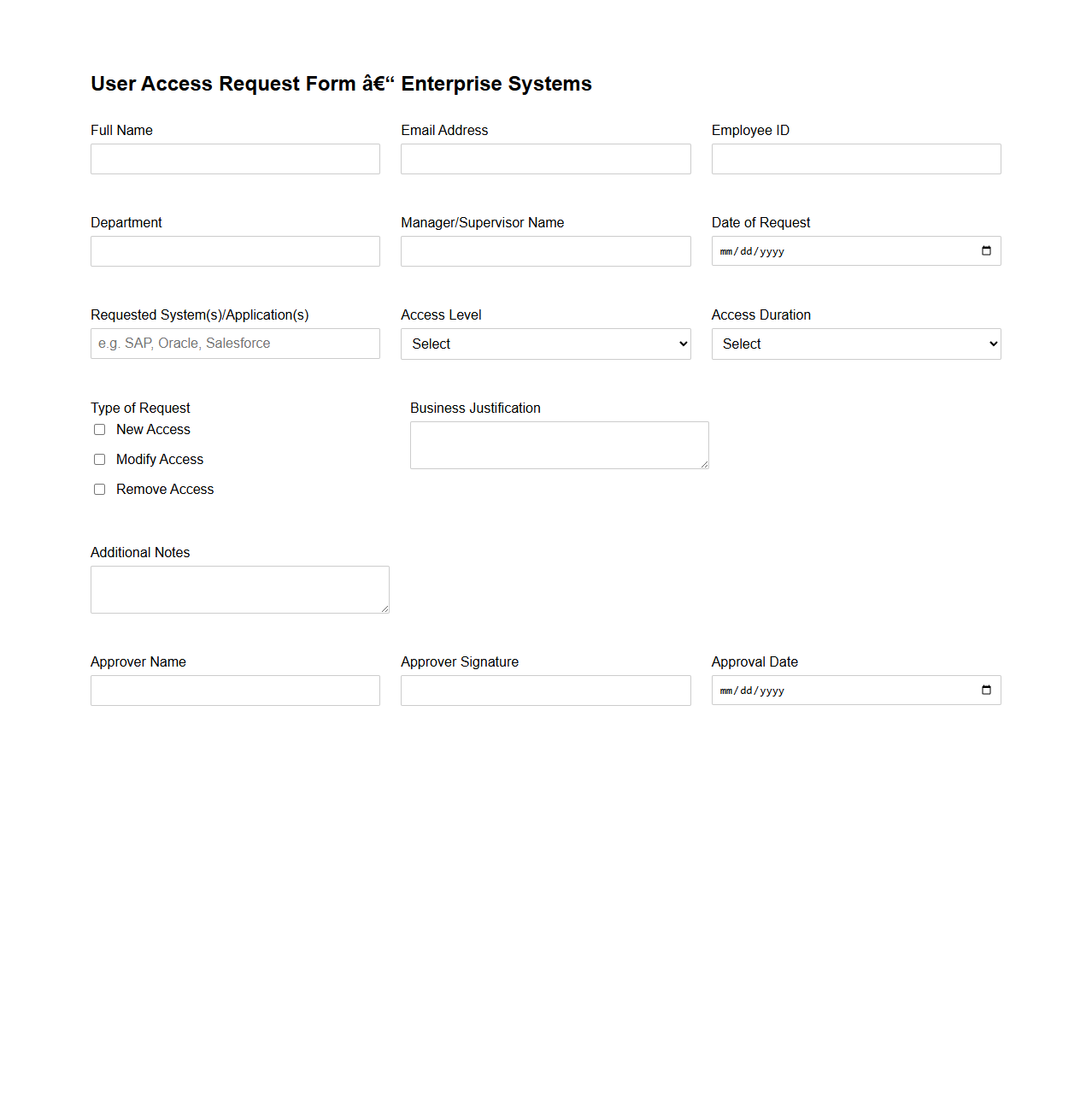
User Access Request Form Template for Enterprise Systems
A
User Access Request Form Template for Enterprise Systems document standardizes the process for requesting access to corporate applications and data, ensuring security and compliance with internal policies. It collects essential information such as user identity, requested access levels, justification, and approval workflows to streamline access control management. This template supports audit trails and reduces risks associated with unauthorized access in large organizations.
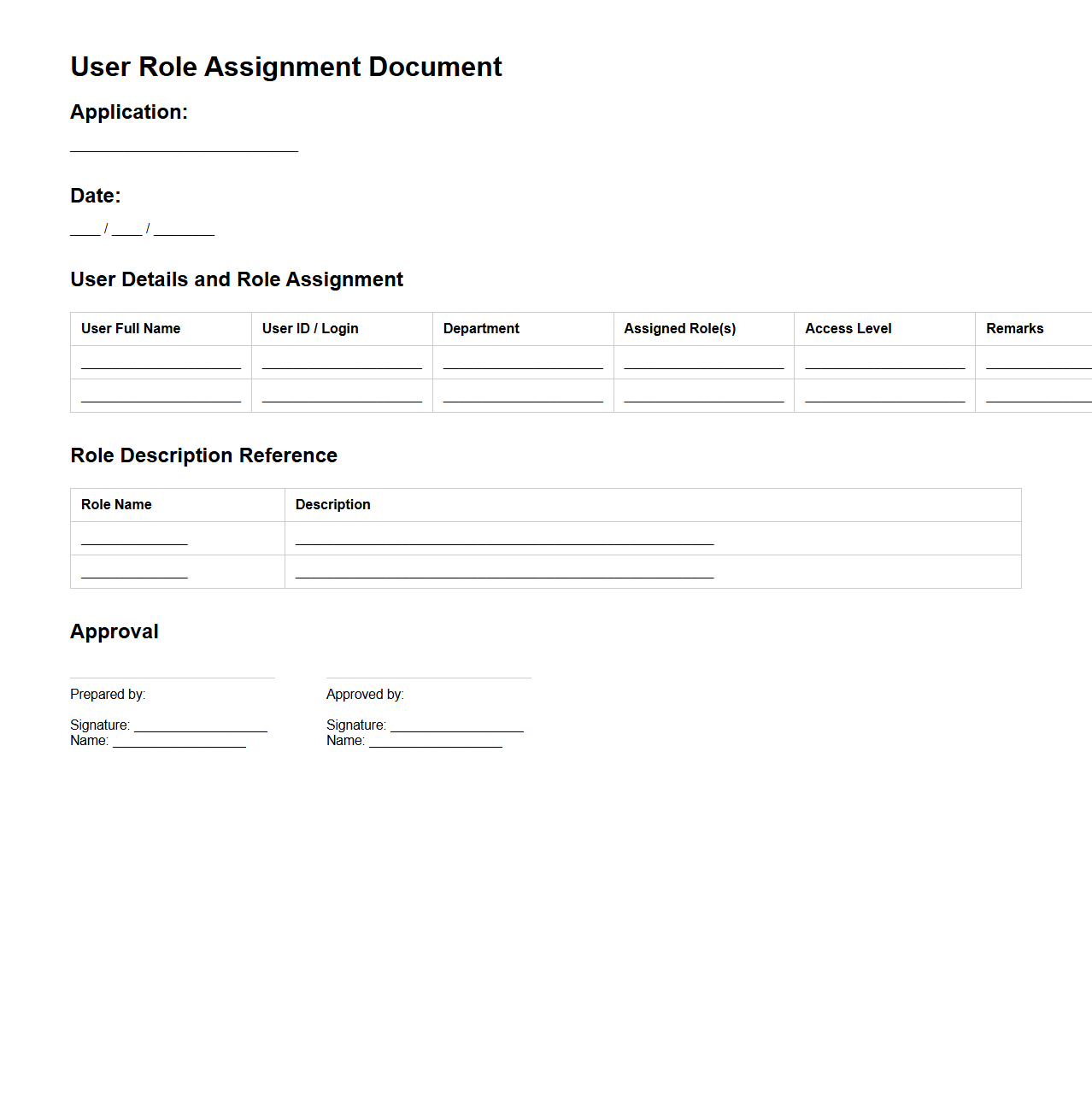
User Role Assignment Document Example for Corporate Applications
A
User Role Assignment Document for corporate applications outlines the specific access levels and permissions granted to each user or user group within an organization's software environment. It ensures proper allocation of roles to maintain security, compliance, and operational efficiency by clearly defining responsibilities tied to each role. This document serves as a critical reference for IT administrators and auditors to manage and review access controls across enterprise systems.
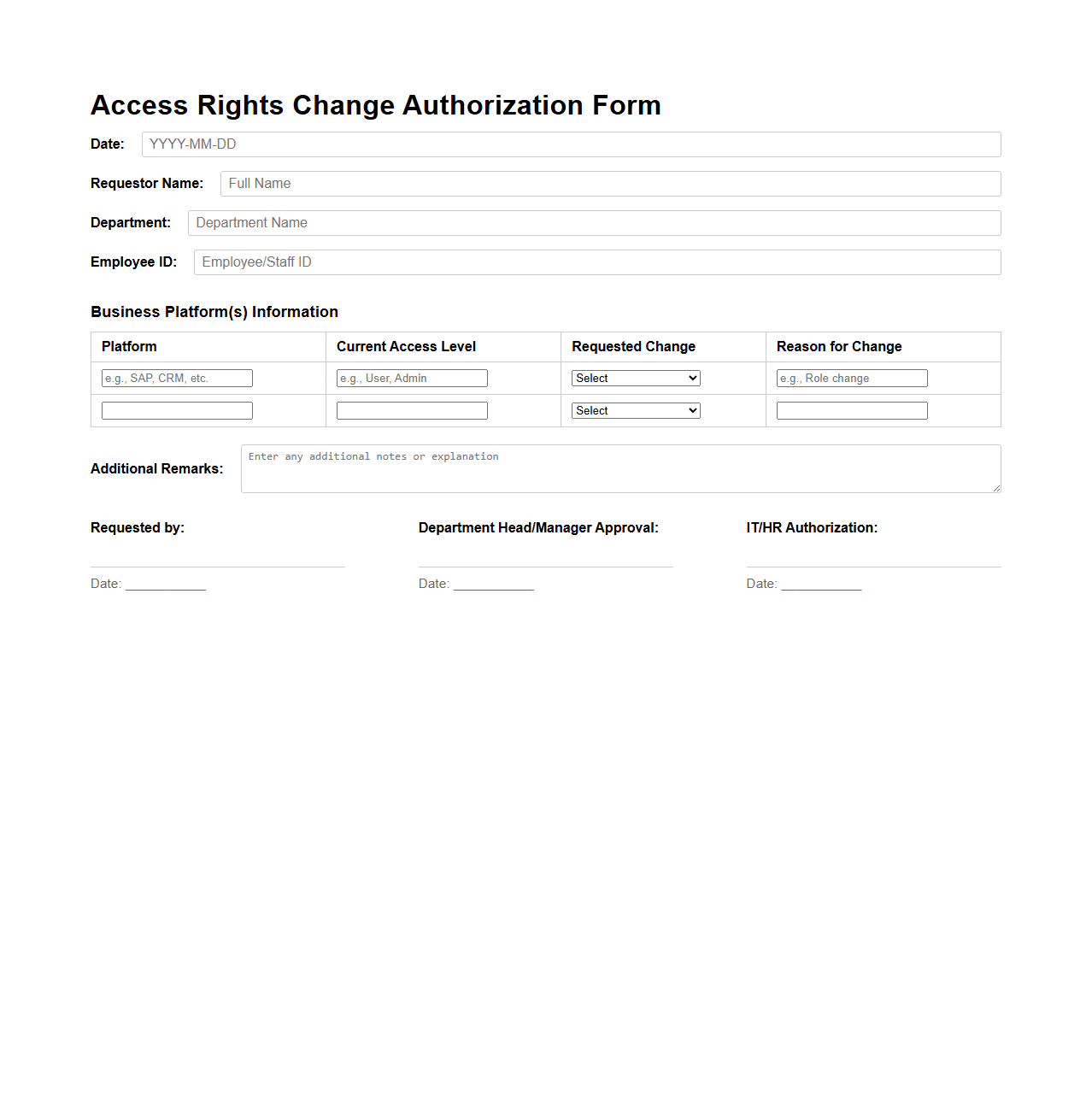
Access Rights Change Authorization Sample for Business Platforms
The
Access Rights Change Authorization Sample for Business Platforms document serves as a standardized framework to manage and approve modifications to user permissions within enterprise systems. It ensures that all access rights changes comply with organizational security policies and regulatory requirements by documenting authorization workflows and accountability. This document helps mitigate risks associated with unauthorized access or privilege escalations in critical business environments.
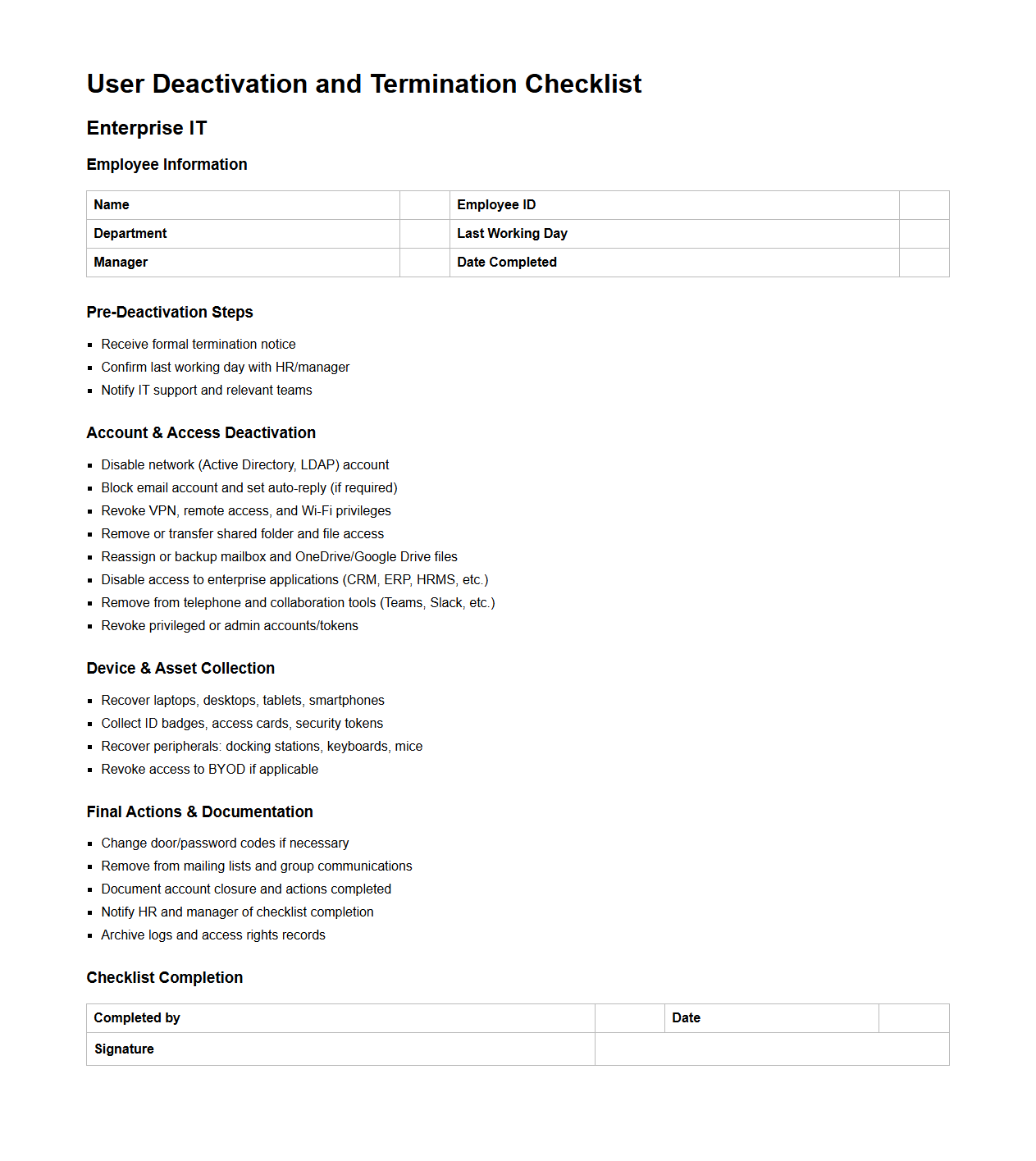
User Deactivation and Termination Checklist for Enterprise IT
The
User Deactivation and Termination Checklist for Enterprise IT document provides a systematic framework to securely manage the removal of user access upon employee departure or role changes. It ensures all enterprise systems, applications, and permissions are promptly and thoroughly revoked to protect sensitive data and maintain compliance with security policies. This checklist helps IT teams prevent unauthorized access, minimize security risks, and maintain operational integrity during user offboarding.
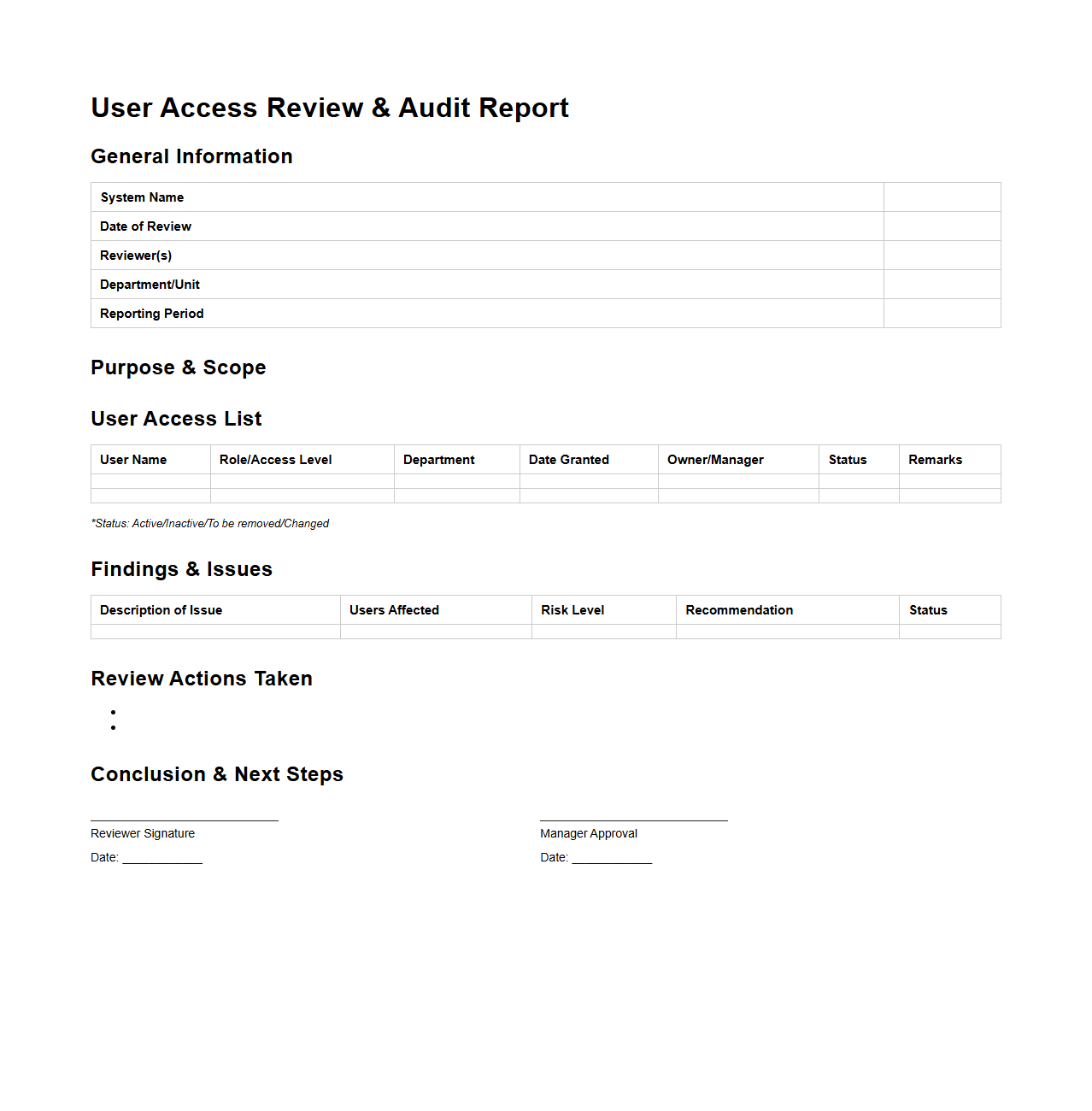
User Access Review and Audit Report Template for Information Systems
A
User Access Review and Audit Report Template for Information Systems document is a structured tool designed to systematically evaluate and verify user permissions within an organization's IT environment. It helps identify unauthorized access, ensure compliance with security policies, and highlight discrepancies in user roles and privileges. This template supports audit processes by providing a consistent format for tracking access reviews and generating comprehensive reports for management and regulatory purposes.
Privileged Account Management Document Example for Enterprise Environments
The
Privileged Account Management Document Example for Enterprise Environments serves as a comprehensive template to guide organizations in establishing policies and procedures for securing and managing privileged accounts. This document outlines best practices for controlling access, monitoring activity, and mitigating risks associated with administrative credentials in complex enterprise IT infrastructures. It ensures compliance with security standards while helping to prevent unauthorized access and safeguard critical systems.
Multi-Factor Authentication Setup Guide for Organizational Systems
The
Multi-Factor Authentication Setup Guide for Organizational Systems document provides step-by-step instructions to enhance security by requiring users to verify their identity through multiple verification methods. It details the configuration process for integrating authentication factors like passwords, biometrics, and security tokens across enterprise applications. This guide ensures standardized implementation to protect sensitive organizational resources from unauthorized access and cyber threats.
Temporary Access Grant Documentation Sample for Project Teams
The
Temporary Access Grant Documentation Sample for project teams serves as a structured template to record and manage short-term permissions granted to team members or external collaborators. This document ensures clear tracking of access duration, scope, and approval authorities, enhancing security and accountability within project environments. It helps organizations maintain compliance with data protection policies while facilitating efficient workflow collaboration.
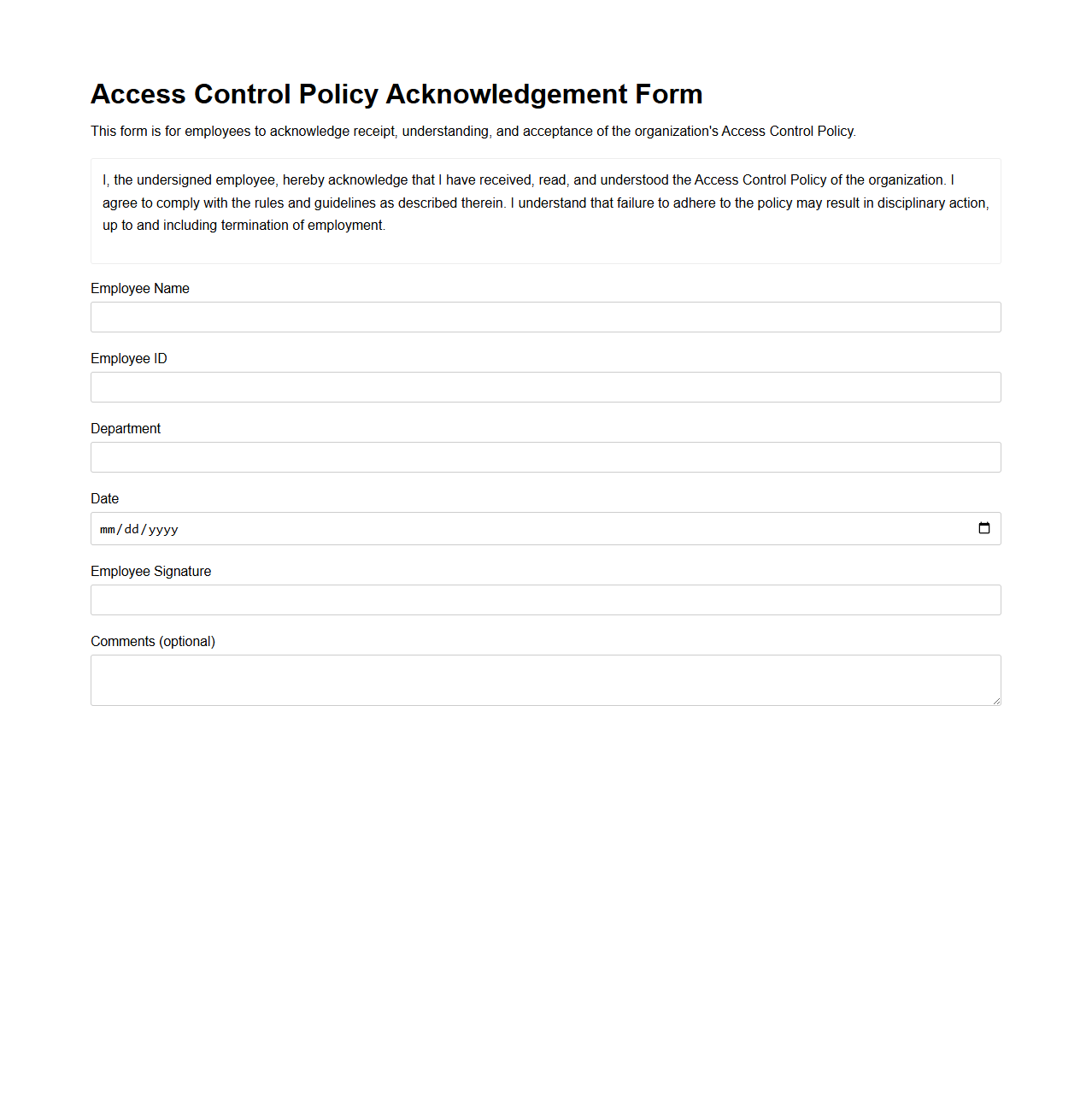
Access Control Policy Acknowledgement Form for Employees
An
Access Control Policy Acknowledgement Form for employees is a formal document that confirms an individual's understanding and compliance with the company's access control regulations. It outlines rules regarding authorized access to sensitive areas, systems, and data, ensuring employees recognize their responsibilities in protecting organizational assets. This form is critical for maintaining security protocols and minimizing unauthorized access risks.
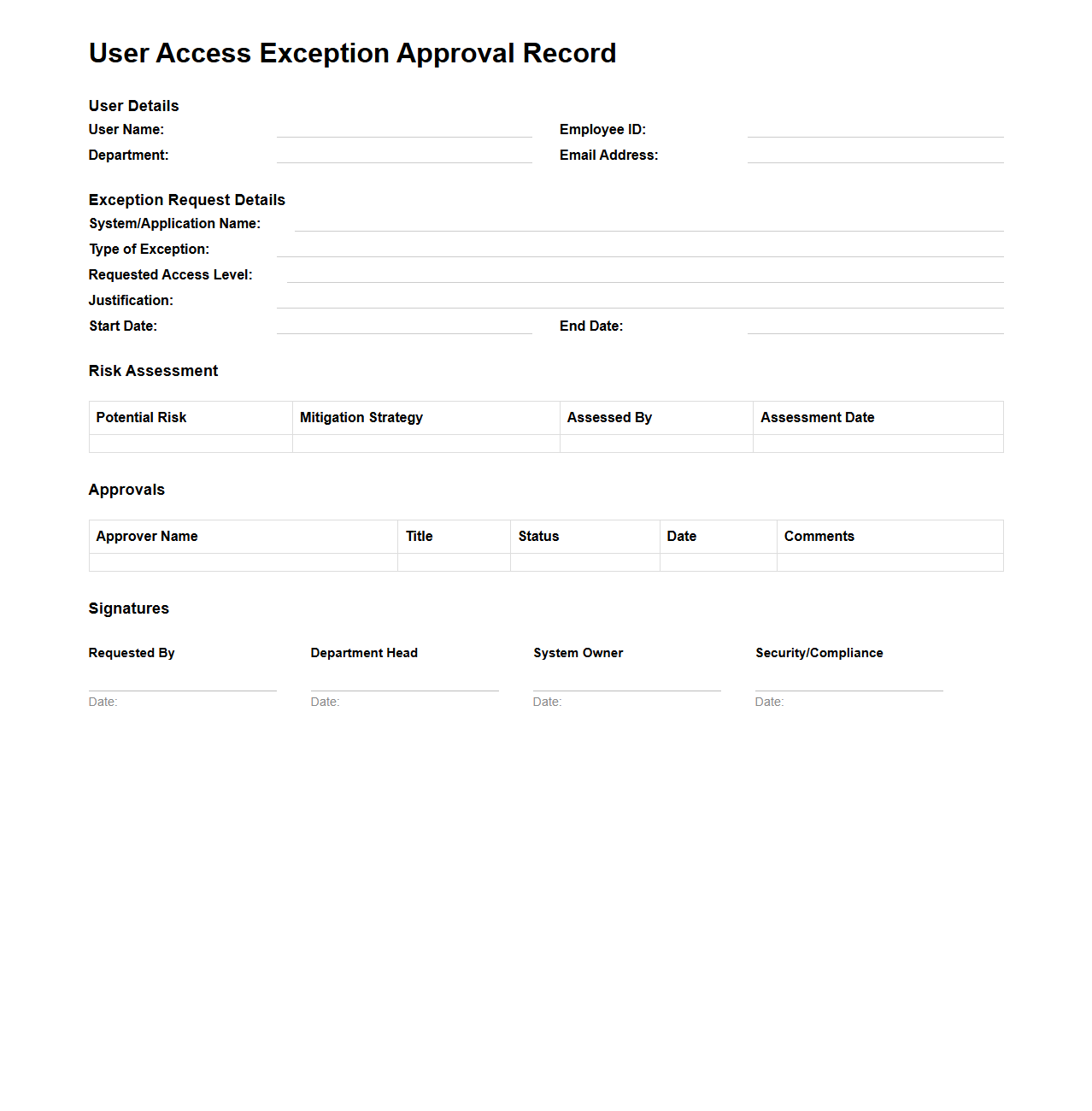
User Access Exception Approval Record for Secure Systems
The
User Access Exception Approval Record for Secure Systems document is a formal record that captures authorized deviations from standard user access policies within secure systems. It ensures that any exceptions granted to users--such as elevated privileges or extended access rights--are properly reviewed and approved by designated security personnel. This document is essential for maintaining compliance, tracking access changes, and supporting audit trails to enhance overall system security.
Authentication Methods for Privileged Enterprise Accounts
The User Access Control Document specifies multi-factor authentication (MFA) as the primary authentication method for privileged enterprise accounts. It emphasizes the use of strong password policies combined with token-based authentication or biometric verification. This approach ensures enhanced security and reduces risks of unauthorized access.
Periodic Review and Recertification of User Access Rights
The document mandates a regular review and recertification of user access rights at defined intervals, typically every 90 days. Managers and system owners are responsible for validating existing permissions to ensure compliance with least privilege principles. This process helps maintain updated and accurate access controls.
Procedures for Emergency or Temporary Access Provisioning
Emergency access is provisioned through a formal temporary access request system outlined in the document. Access is granted for a limited time frame and logged for audit purposes, ensuring accountability. After the emergency period, the temporary credentials are promptly revoked.
Audit Logging Requirements for Access Changes
The document requires comprehensive audit logging of all access changes, including additions, modifications, and revocations. Logs must capture the user identity, time of change, and approver details to support traceability. These records are critical for compliance and forensic investigations.
Handling of Access Revocation During Employee Offboarding
Access revocation is prioritized during the employee offboarding process to prevent residual access risks. The document outlines immediate disabling of accounts upon termination notification and revocation of all privileged permissions. This ensures secure separation and protects enterprise resources.
More Technology Templates