An Incident Response Document Sample for Network Security outlines step-by-step procedures for identifying, managing, and mitigating security breaches within a network environment. It includes roles and responsibilities, communication protocols, and technical guidelines to ensure efficient and effective incident handling. This template helps organizations minimize damage, recover quickly, and improve overall network protection.
Network Security Incident Reporting Template
A
Network Security Incident Reporting Template document standardizes the process of capturing essential details about cybersecurity breaches or suspicious activities within a network. It ensures consistent and thorough documentation of incident specifics, such as timelines, affected systems, attack vectors, and mitigation steps. This template facilitates prompt response, effective communication among IT teams, and compliance with regulatory requirements.
Incident Response Plan for Network Breach
An
Incident Response Plan for Network Breach is a detailed document outlining the specific procedures and protocols an organization follows when detecting and managing a network security breach. It includes steps for identifying the breach, containing the threat, eradicating malicious elements, and recovering affected systems while minimizing operational disruption. This plan also defines roles and responsibilities, communication strategies, and post-incident analysis to improve future security measures.
Initial Incident Notification Form for IT Security
The
Initial Incident Notification Form for IT Security serves as a standardized document used to promptly report and record the first details of a cybersecurity incident. It captures critical information such as the time of detection, nature of the incident, affected systems, and initial actions taken, enabling swift assessment and response. This form is essential for maintaining accurate incident logs, facilitating communication among IT teams, and ensuring compliance with organizational and regulatory requirements.
Network Intrusion Investigation Report
A
Network Intrusion Investigation Report is a detailed document that analyzes and summarizes unauthorized access or cyberattack attempts detected within an organization's network. It includes evidence collected from network logs, intrusion detection systems, and security tools, outlining the scope, methods, and impact of the intrusion. This report supports incident response efforts by providing insights for remediation, vulnerability mitigation, and future threat prevention.
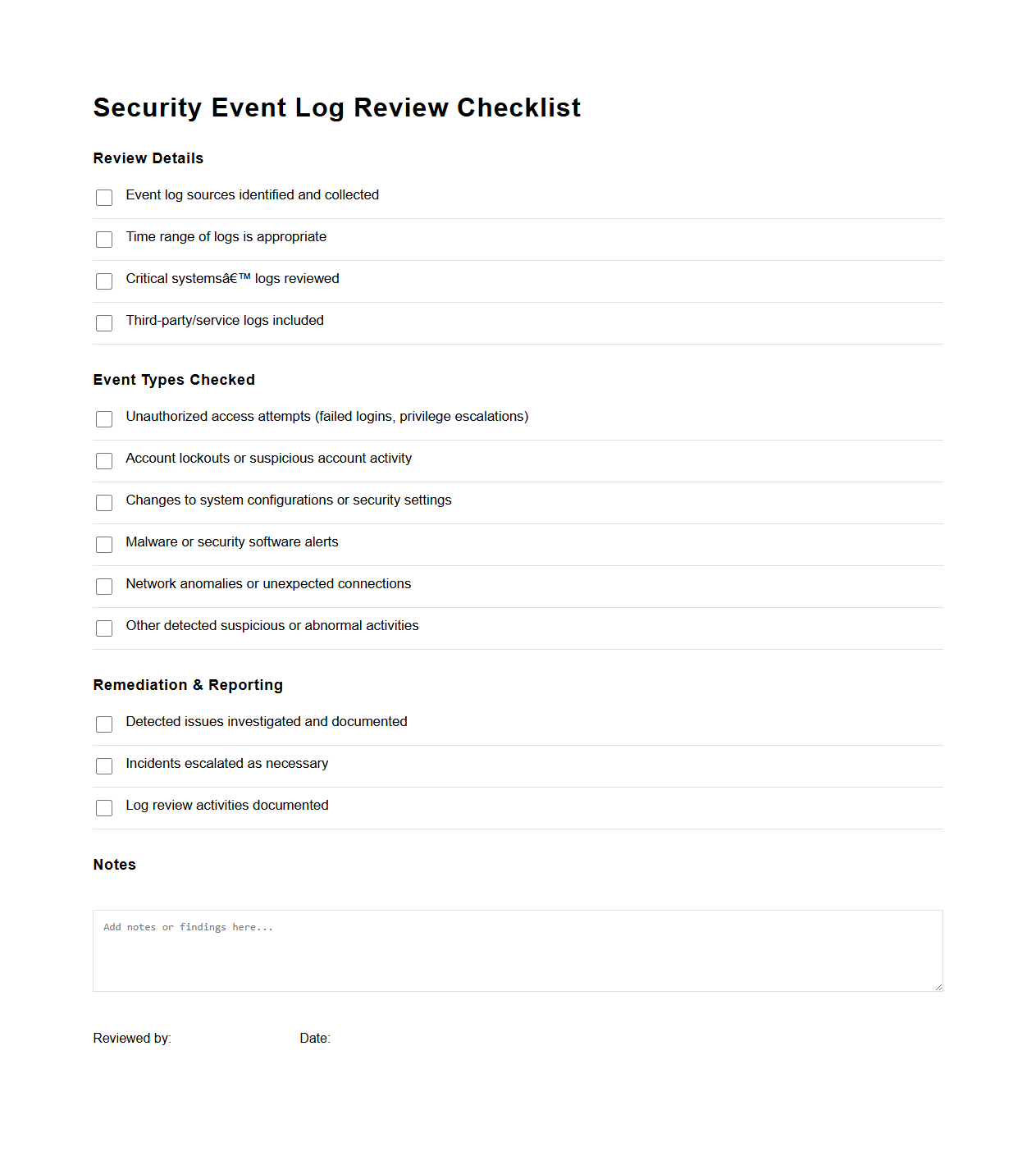
Security Event Log Review Checklist
The
Security Event Log Review Checklist document serves as a structured guide for systematically examining security logs to identify unusual activities, potential threats, and compliance issues. It outlines essential steps and criteria for analyzing logs from various sources such as firewalls, intrusion detection systems, and servers to ensure a comprehensive security posture. Regular use of this checklist enhances incident detection, supports forensic investigations, and helps maintain regulatory compliance by ensuring consistent log monitoring practices.
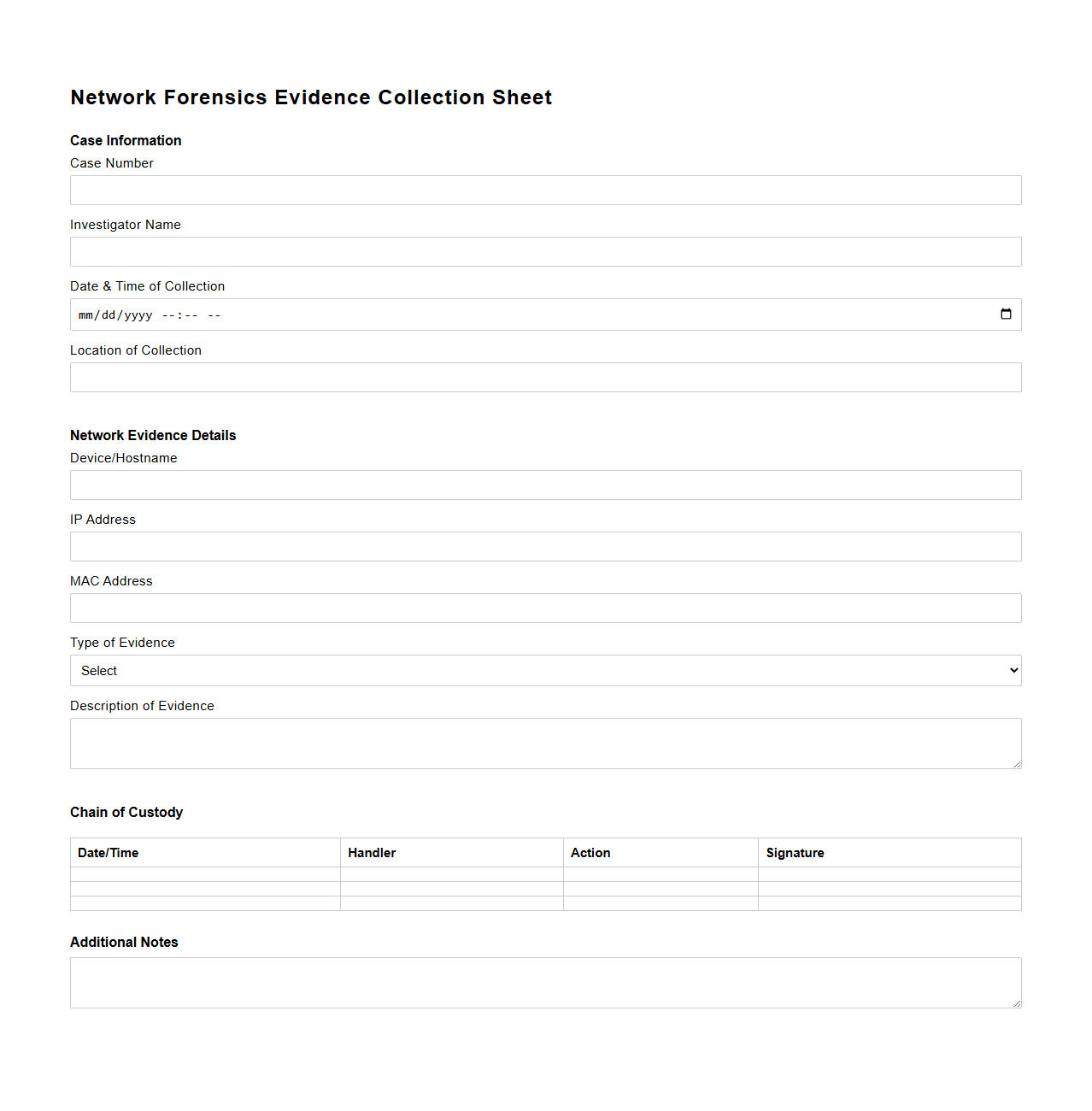
Network Forensics Evidence Collection Sheet
A
Network Forensics Evidence Collection Sheet document is a structured framework used to systematically record and preserve digital evidence gathered during network investigations. It ensures accurate documentation of data such as timestamps, source and destination IP addresses, protocols, and the methods used for data capture. This sheet plays a critical role in maintaining the integrity of evidence for legal proceedings and incident analysis.
Incident Containment and Mitigation Guide
The
Incident Containment and Mitigation Guide document provides a structured approach to quickly identify, isolate, and control cybersecurity threats to minimize damage. It outlines best practices, tools, and techniques for limiting the spread of an incident while preserving evidence for further analysis. This guide serves as a critical resource for security teams to effectively manage and reduce the impact of security breaches.
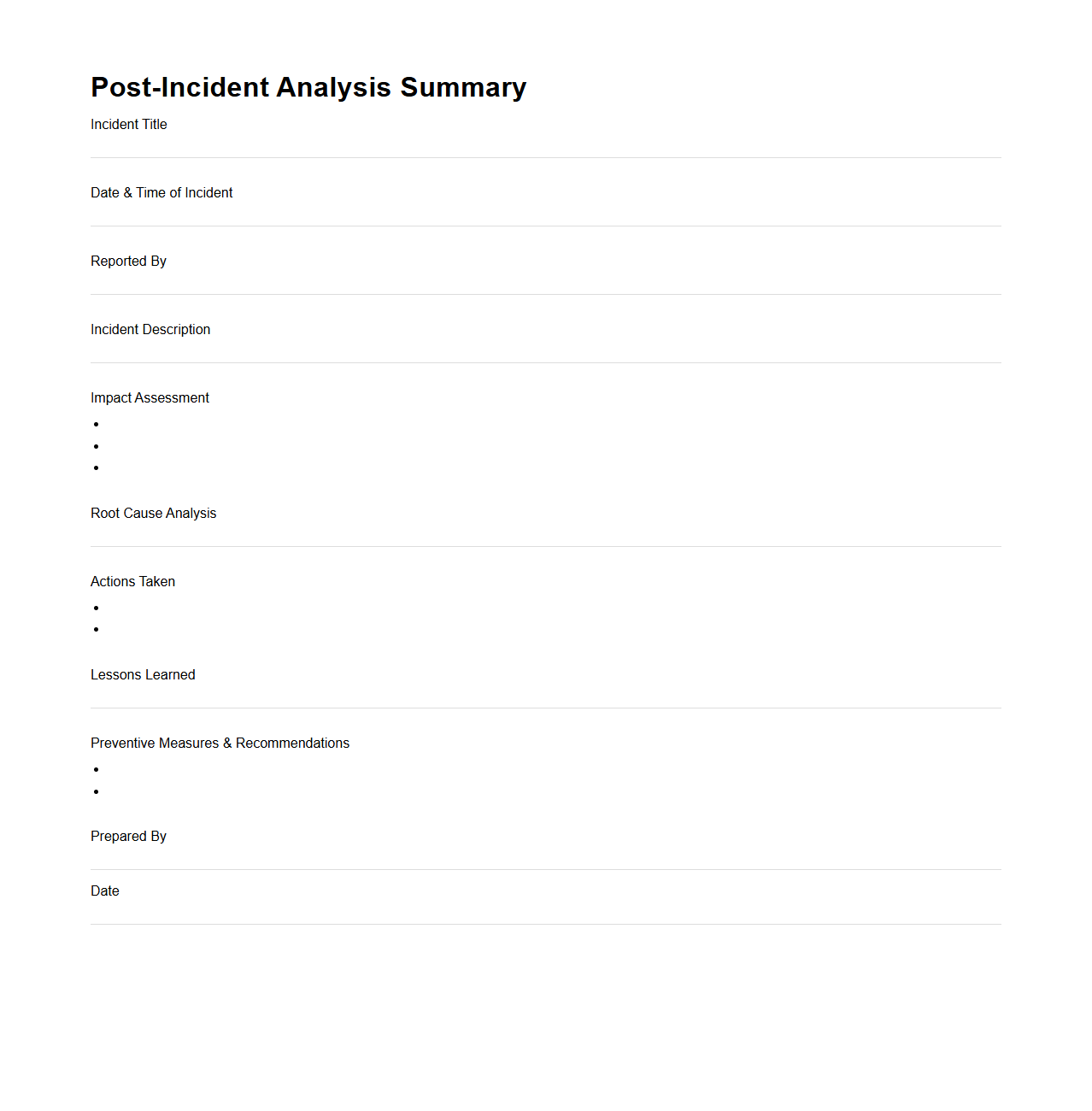
Post-Incident Analysis Summary
The
Post-Incident Analysis Summary document provides a detailed review of an incident, outlining the causes, impacts, and response actions taken. It serves as a critical tool for identifying vulnerabilities and improving future incident response strategies. This summary helps stakeholders understand lessons learned and ensures accountability in managing incident recovery.
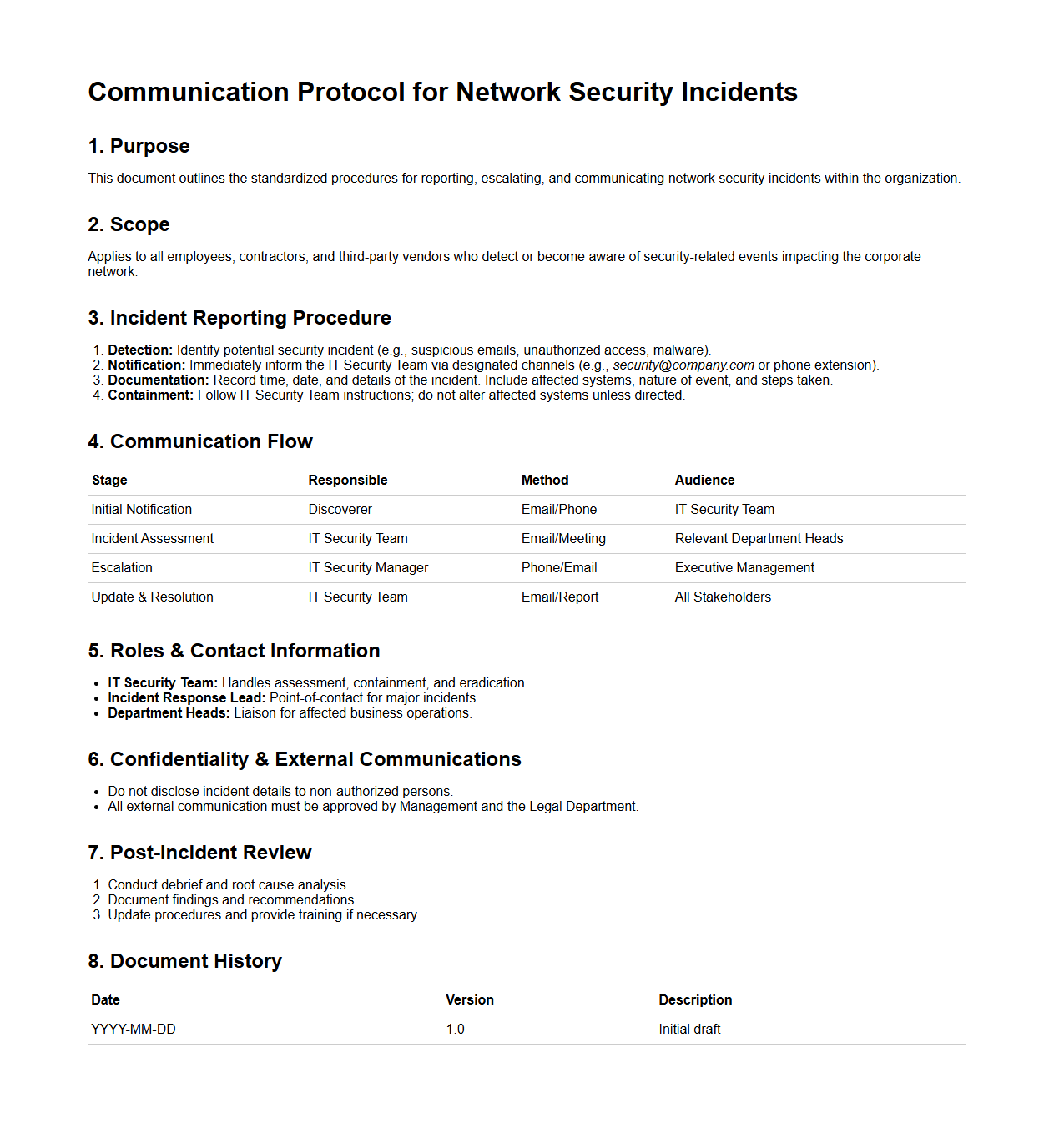
Communication Protocol for Network Security Incidents
A
Communication Protocol for Network Security Incidents document outlines the standardized procedures and guidelines to ensure effective information exchange during cybersecurity events. It specifies roles, responsibilities, message formats, and escalation paths to facilitate timely detection, containment, and resolution of network threats. This document is essential for coordinating response efforts and minimizing the impact of security breaches.
Root Cause Analysis Report for Network Security
A
Root Cause Analysis Report for Network Security document systematically identifies the underlying causes of security incidents or breaches within a network infrastructure. It provides detailed insights into vulnerabilities, attack vectors, and system failures that led to the compromise, enabling targeted remediation strategies. The report is essential for improving network defenses, minimizing future risks, and ensuring compliance with security standards.
What key elements must be included in a network security incident response document template?
A network security incident response document should include clear identification of incident types and severity levels. It must outline roles and responsibilities for the incident response team to ensure efficient handling. Additionally, predefined steps for detection, containment, eradication, and recovery must be detailed.
How should evidence collection procedures be detailed in the incident response letter?
The incident response letter should describe evidence collection procedures with a focus on maintaining chain of custody and data integrity. Precise methods for capturing logs, system images, and relevant artifacts should be specified. It must emphasize documenting timestamps and securing collected evidence to prevent tampering.
Which communication protocols should be outlined for reporting network security incidents?
The document must define communication protocols including internal reporting channels and external notifications to regulators or affected customers. It should specify timely escalation and confidentiality measures during information sharing. Contact hierarchies, including emergency contacts, should also be clearly listed.
How does the document address escalation steps for critical network breaches?
Escalation steps in the document prioritize critical network breaches by outlining predefined thresholds for severity and urgency. It mandates immediate notification of senior management and activation of the incident response team. Procedures for involving legal counsel and law enforcement, when necessary, are also included.
What post-incident review actions are specified in the incident response document?
The post-incident section requires conducting a thorough review to analyze root causes and response effectiveness. Documentation of lessons learned and suggested improvements is essential to strengthen future security measures. Additionally, the document outlines follow-up audits and updates to policies as part of continuous improvement.
More Technology Templates