A Cybersecurity Policy Document Sample for Enterprise Networks outlines essential guidelines and protocols to protect an organization's digital assets from cyber threats. It includes rules for network access, data protection, incident response, and employee responsibilities to ensure robust security across all enterprise systems. This document serves as a foundational tool for maintaining compliance and mitigating risks in complex network environments.
Network Access Control Policy Sample
A
Network Access Control Policy Sample document outlines the guidelines and rules governing user access to a company's network resources, ensuring only authorized devices and individuals can connect. This policy typically includes authentication methods, device compliance requirements, and procedures for handling access violations. Implementing such a policy enhances network security by preventing unauthorized access and reducing the risk of data breaches.
Incident Response Policy Sample
An
Incident Response Policy Sample document outlines predefined procedures and guidelines organizations follow to effectively detect, respond to, and recover from cybersecurity incidents. It establishes roles, responsibilities, communication protocols, and escalation paths to ensure a timely and coordinated response, minimizing damage and operational disruption. This sample document serves as a blueprint for creating customized incident response policies aligned with industry standards such as NIST or ISO 27001.
Acceptable Use Policy Sample for Enterprise Networks
An
Acceptable Use Policy Sample for Enterprise Networks document outlines the rules and guidelines that govern the appropriate use of corporate network resources by employees and authorized users. It defines permissible activities, restrictions on accessing certain websites or applications, and security protocols to protect sensitive enterprise data from unauthorized access or misuse. This policy helps organizations maintain network integrity, ensure compliance with regulatory standards, and reduce risks related to cybersecurity threats.
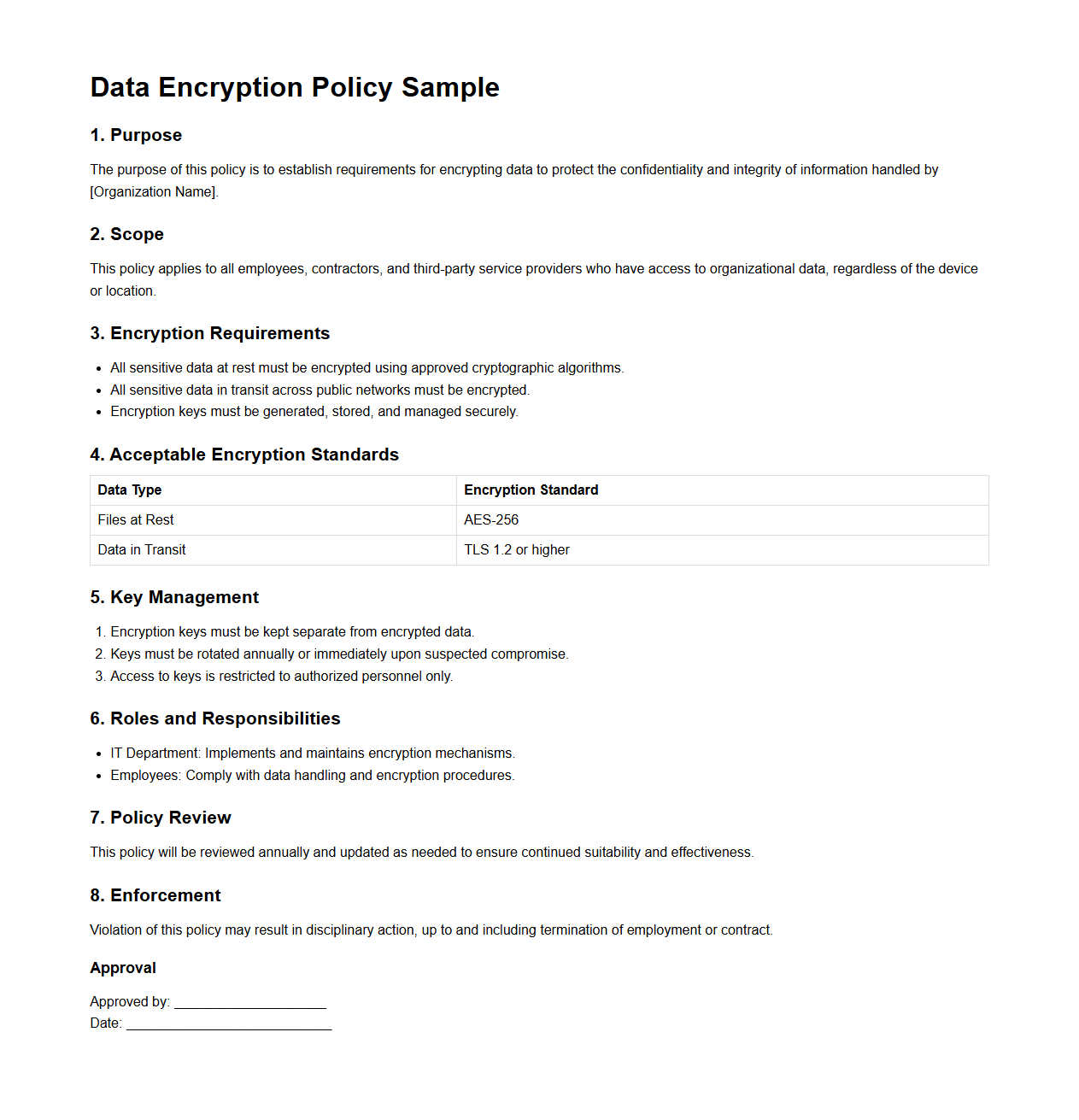
Data Encryption Policy Sample
A
Data Encryption Policy Sample document outlines the standards and procedures for protecting sensitive information through encryption techniques within an organization. It specifies encryption methods, key management practices, and compliance requirements to ensure data confidentiality and integrity. This policy serves as a critical guide for employees and IT teams to safeguard digital assets against unauthorized access and data breaches.
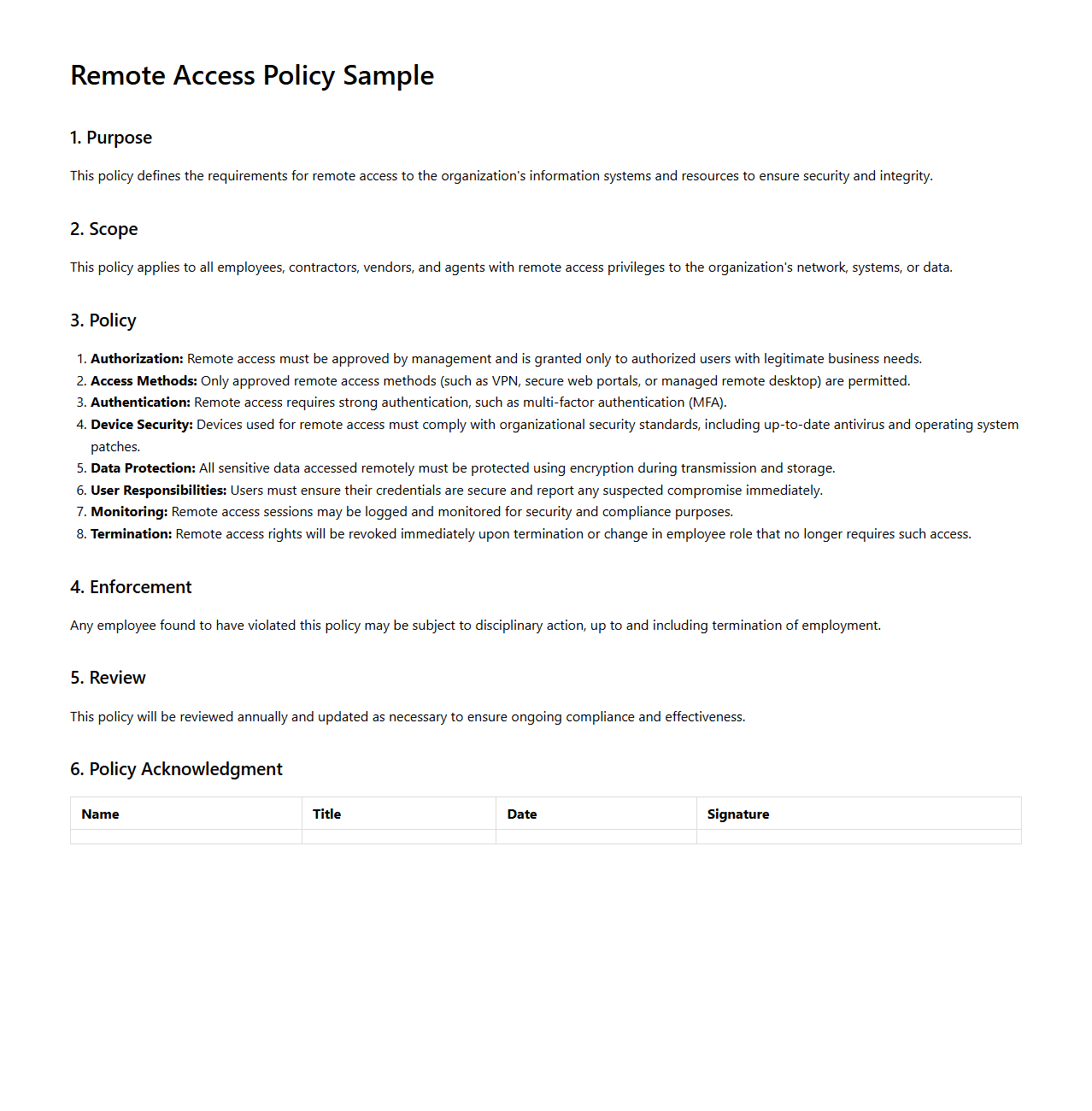
Remote Access Policy Sample
A
Remote Access Policy Sample document outlines organizational rules and procedures for securely connecting to internal systems from external locations. It defines authorized users, access methods, security measures such as VPN and multi-factor authentication, and compliance requirements to protect sensitive data. This sample serves as a guideline for creating tailored policies that ensure controlled and secure remote connectivity.
Firewall Management Policy Sample
A
Firewall Management Policy Sample document outlines standardized procedures and guidelines for configuring, monitoring, and maintaining firewalls to protect organizational networks from unauthorized access and cyber threats. It typically includes rules for firewall rule creation, change management, auditing, incident response, and compliance with security regulations. This policy ensures consistent security practices and helps reduce vulnerabilities by enforcing strict control over network traffic.
Password Management Policy Sample
A
Password Management Policy Sample document outlines standardized guidelines for creating, using, and maintaining secure passwords within an organization. It defines requirements such as password complexity, expiration periods, storage protocols, and usage rules to protect sensitive information from unauthorized access. Implementing this policy ensures consistent security practices and helps mitigate risks associated with password vulnerabilities.
Network Monitoring Policy Sample
A
Network Monitoring Policy Sample document outlines guidelines and procedures for tracking the performance, security, and availability of network infrastructure. It defines roles, responsibilities, acceptable monitoring tools, and protocols for data collection to ensure consistent and effective oversight. Organizations use this policy to maintain network integrity, quickly identify issues, and comply with regulatory standards.
Third-Party Access Policy Sample
A
Third-Party Access Policy Sample document outlines the guidelines and security measures for granting external vendors or contractors access to an organization's systems and data. This policy ensures controlled and monitored access to protect sensitive information, minimize security risks, and comply with regulatory requirements. It typically includes definitions of access levels, approval processes, and responsibilities for both the organization and third parties.
Wireless Network Security Policy Sample
A
Wireless Network Security Policy Sample document outlines guidelines and best practices to protect wireless network infrastructure from unauthorized access, data breaches, and cyber threats. It specifies security protocols, authentication methods, encryption standards, and user responsibilities to ensure data confidentiality and network integrity. Organizations use this sample as a template to create tailored policies that comply with regulatory requirements and industry standards.
How should access controls be specified for third-party vendors in the cybersecurity policy document?
Access controls for third-party vendors must be clearly defined with role-based permissions to limit exposure to critical systems. The policy should require vendors to use multifactor authentication and ensure data access is granted on a least-privilege basis. Regular audits and access reviews must be mandated to monitor vendor activities and revoke access when no longer necessary.
What incident response procedures must be documented for advanced persistent threats (APTs) targeting enterprise networks?
The policy must include detailed incident response procedures to detect, analyze, and mitigate APT attacks. It should specify steps for isolating affected systems, conducting forensic investigations, and communicating with relevant stakeholders. Continuous monitoring, threat intelligence sharing, and post-incident reviews are essential to enhance future defense mechanisms.
How does the policy address the management and encryption of sensitive data in cloud-based network environments?
The cybersecurity policy mandates strict management and encryption protocols for sensitive data stored in cloud environments. Data must be encrypted both in transit and at rest using industry-standard cryptographic algorithms. Access controls, logging mechanisms, and compliance with data privacy regulations are essential components for securing cloud-based data.
What guidelines are included for reviewing and updating firewall configurations in the enterprise network policy?
The policy requires regular firewall configuration reviews to ensure that rules align with current security needs and threat landscapes. Updates should be applied promptly to block unauthorized access and minimize vulnerabilities. Documentation of all changes and automated alerts for suspicious activities are crucial aspects of this guideline.
How are employee cybersecurity training and regular policy compliance audits documented within the policy?
Employee cybersecurity training is mandated to be conducted periodically to ensure ongoing awareness of evolving threats and best practices. The policy stipulates routine compliance audits to verify adherence to security controls and identify gaps. All training activities and audit outcomes must be documented and reviewed by leadership to enforce accountability.
More Technology Templates