A Vulnerability Assessment Document Sample for Smart Home Devices provides a structured framework to identify and evaluate security weaknesses in connected home technologies. It outlines potential threats, risk levels, and recommended mitigation strategies to enhance device protection. This document is essential for manufacturers and security professionals aiming to safeguard smart home ecosystems.
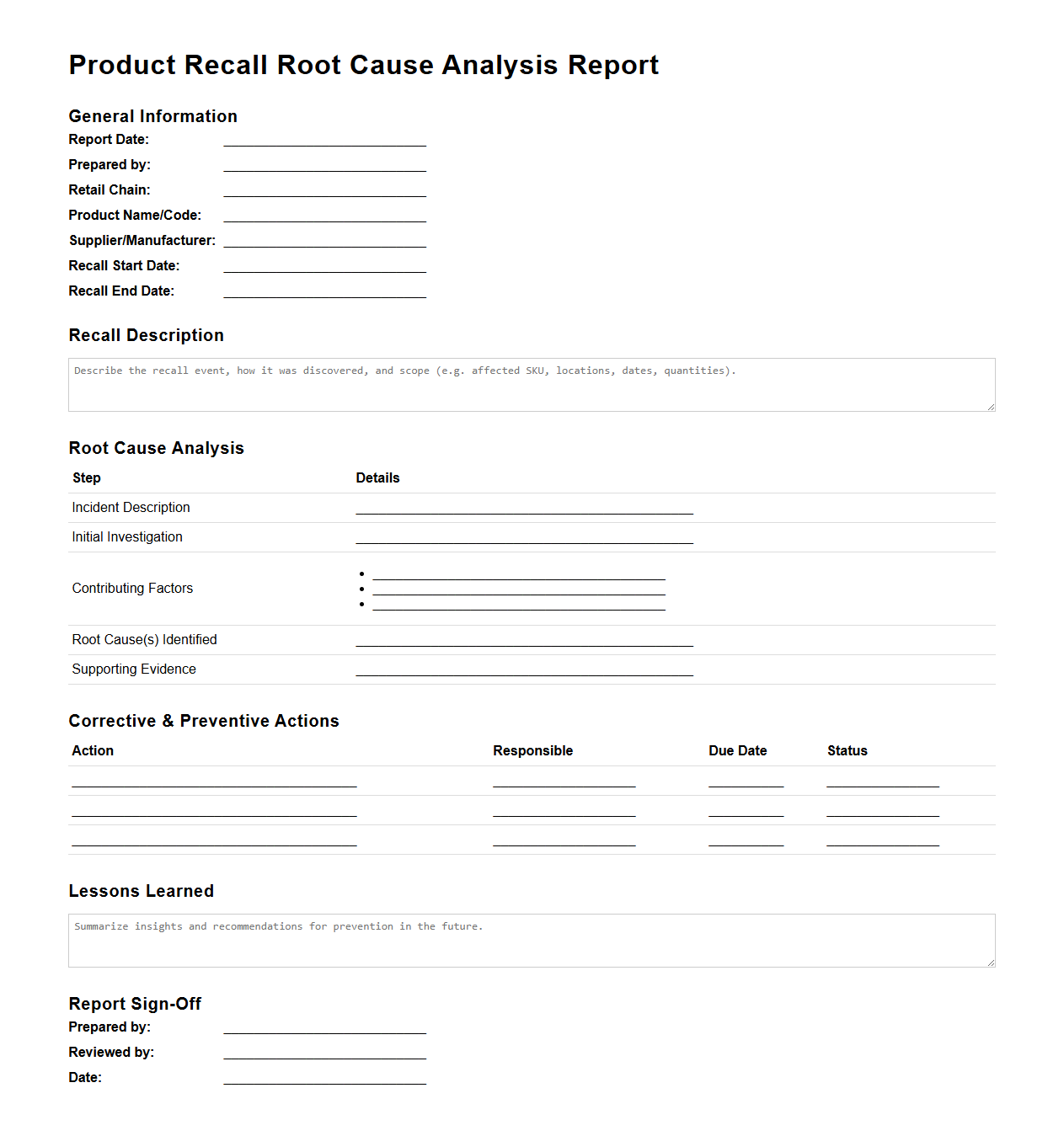
Risk Assessment Report Template for Smart Home Devices
A
Risk Assessment Report Template for Smart Home Devices document systematically identifies potential security, privacy, and operational risks associated with interconnected home technology. It provides a structured format to evaluate vulnerabilities, assess impact levels, and recommend mitigation strategies to ensure user safety and device reliability. This template is essential for manufacturers, developers, and security analysts aiming to enhance the resilience of smart home ecosystems against evolving threats.
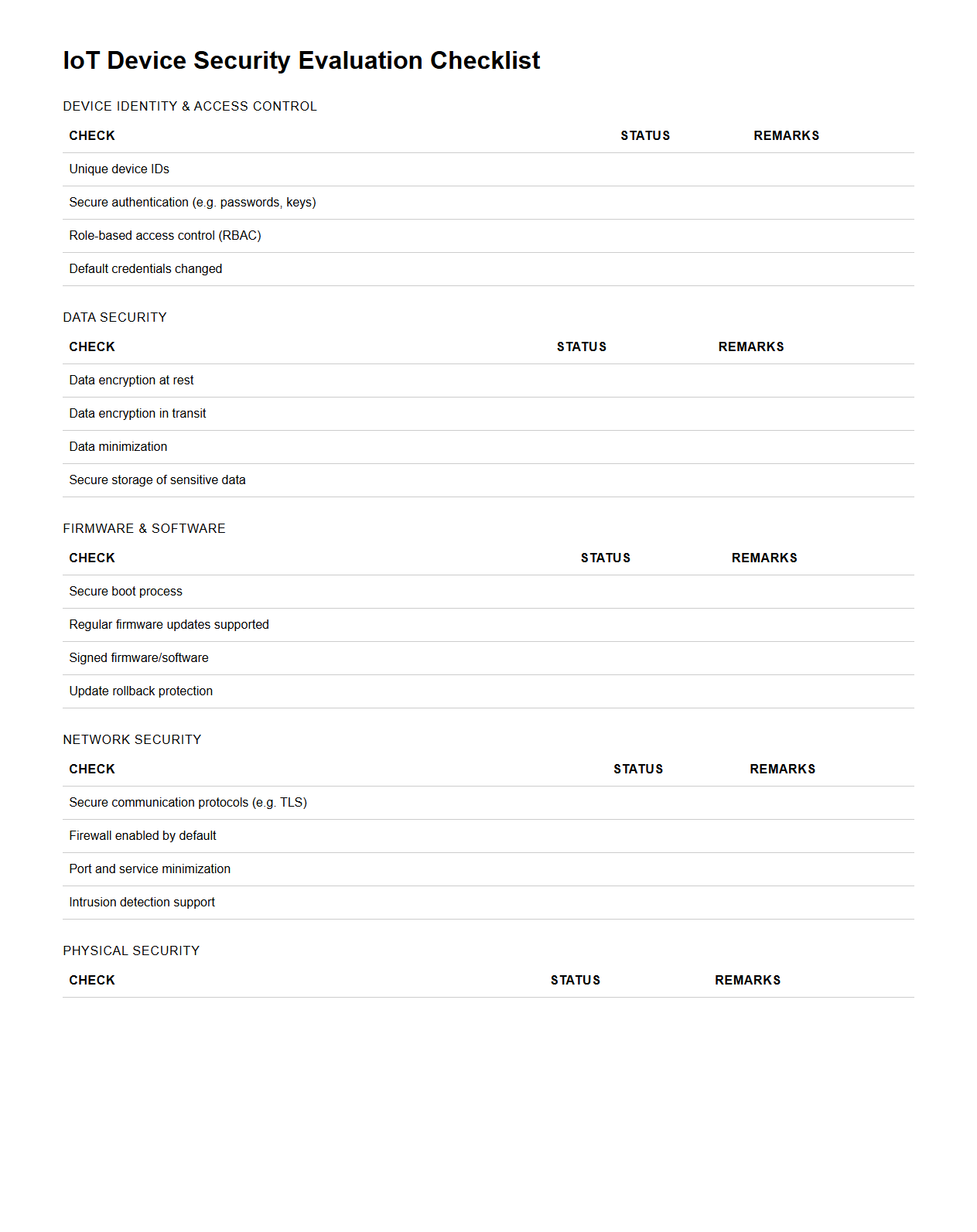
IoT Device Security Evaluation Checklist
The
IoT Device Security Evaluation Checklist is a comprehensive document designed to assess the security posture of Internet of Things devices by verifying compliance with industry standards and best practices. It covers key areas such as firmware integrity, data encryption, network security, and access control mechanisms to ensure robust protection against vulnerabilities. This checklist serves as a critical tool for manufacturers, developers, and security professionals to systematically identify and mitigate potential risks in IoT device ecosystems.
Smart Home Cyber Threat Analysis Sample
The
Smart Home Cyber Threat Analysis Sample document provides a comprehensive evaluation of potential security risks and vulnerabilities specific to smart home environments. It outlines common attack vectors such as unauthorized access, data breaches, and device manipulation, while offering practical mitigation strategies to enhance cybersecurity posture. This resource is essential for homeowners, developers, and security professionals aiming to safeguard interconnected devices and personal information against evolving cyber threats.
Device Vulnerability Audit Report Format
A
Device Vulnerability Audit Report Format document outlines the standardized structure for assessing and documenting security weaknesses within electronic devices. It includes sections for identifying device specifications, detailing vulnerabilities found, risk classifications, and recommended mitigation strategies. This format ensures consistent, comprehensive analysis critical for enhancing device security and compliance.
Network Penetration Testing Summary for Home Automation
Network Penetration Testing Summary for Home Automation document provides a detailed assessment of vulnerabilities within smart home systems, identifying potential security risks in connected devices and network infrastructure. The report highlights critical findings, such as weak authentication protocols, unpatched firmware, and insecure communication channels, essential for mitigating cyber threats in IoT environments.
Network Penetration Testing ensures comprehensive evaluation to enhance the overall security posture of home automation networks.
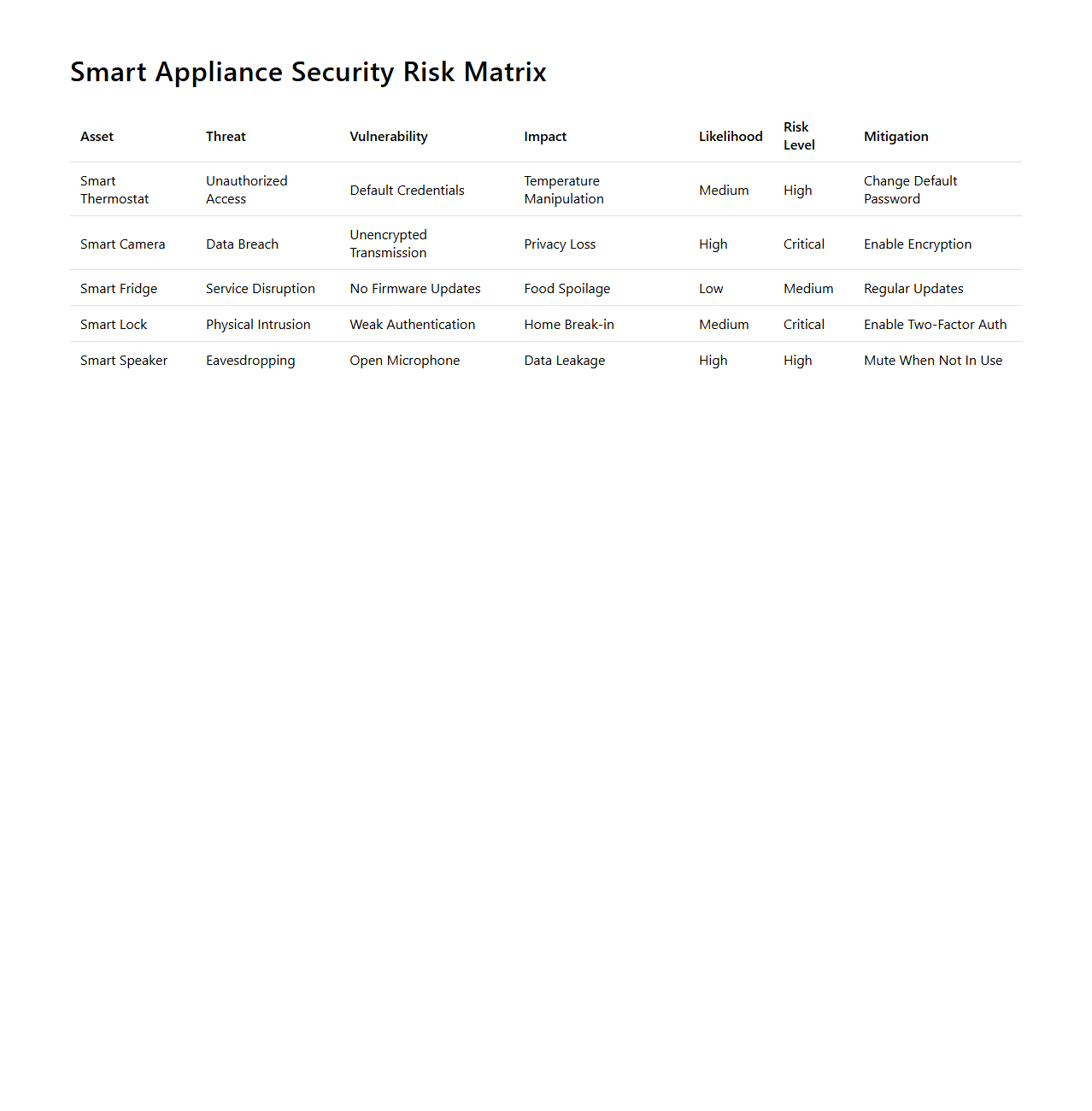
Smart Appliance Security Risk Matrix
The
Smart Appliance Security Risk Matrix document systematically identifies and categorizes potential security vulnerabilities associated with smart appliances, enabling manufacturers and users to assess risks effectively. It provides a structured framework to evaluate threats based on their likelihood and potential impact, supporting proactive security measures. This matrix helps prioritize security improvements by highlighting the most critical risks in smart home environments.
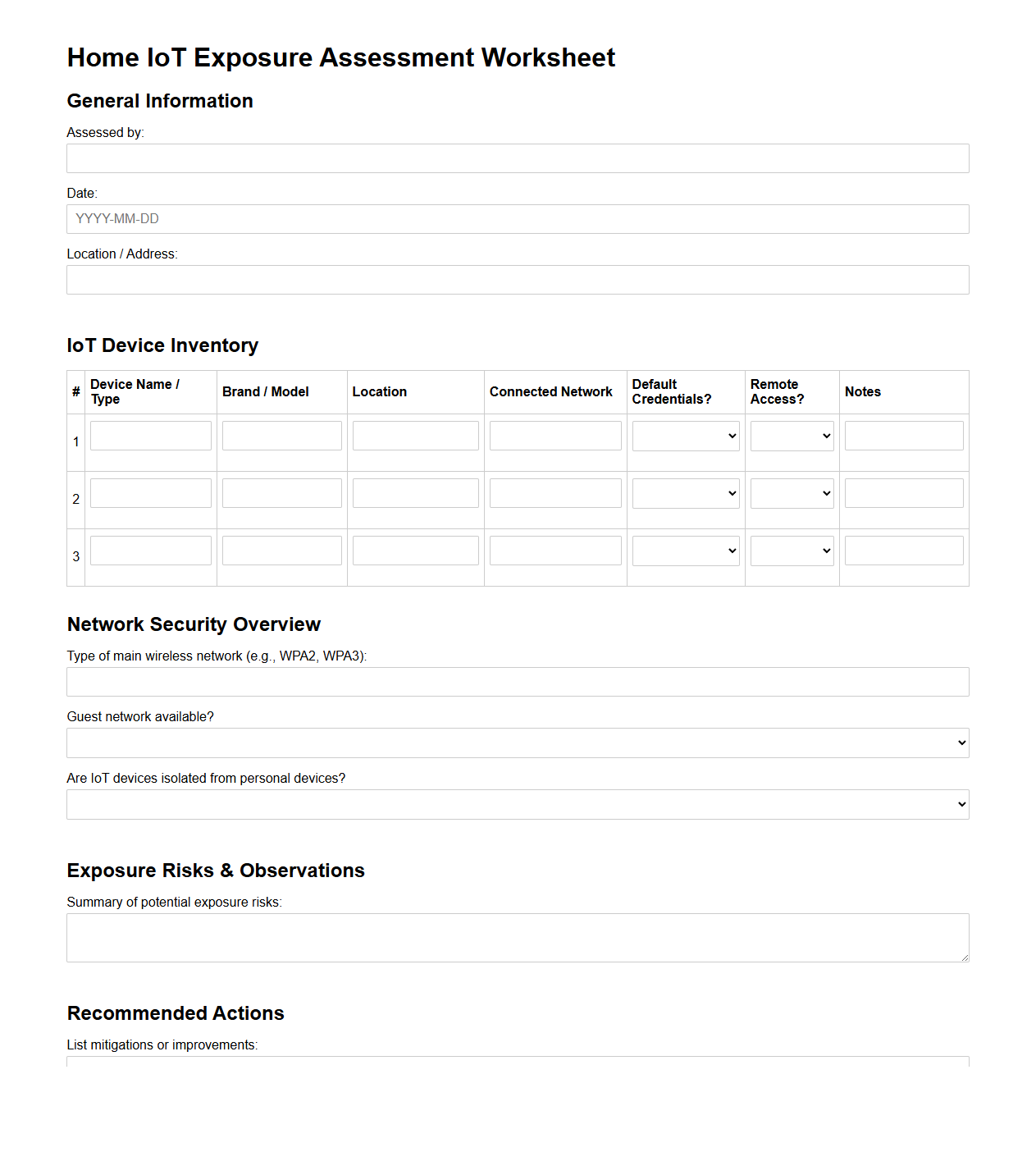
Home IoT Exposure Assessment Worksheet
The
Home IoT Exposure Assessment Worksheet document is a tool designed to evaluate potential risks associated with Internet of Things devices used within residential environments. It systematically identifies and assesses various exposure points, including network vulnerabilities and data privacy concerns, to ensure secure and safe IoT integration. This worksheet aids homeowners and security professionals in implementing effective mitigation strategies to protect connected home ecosystems.
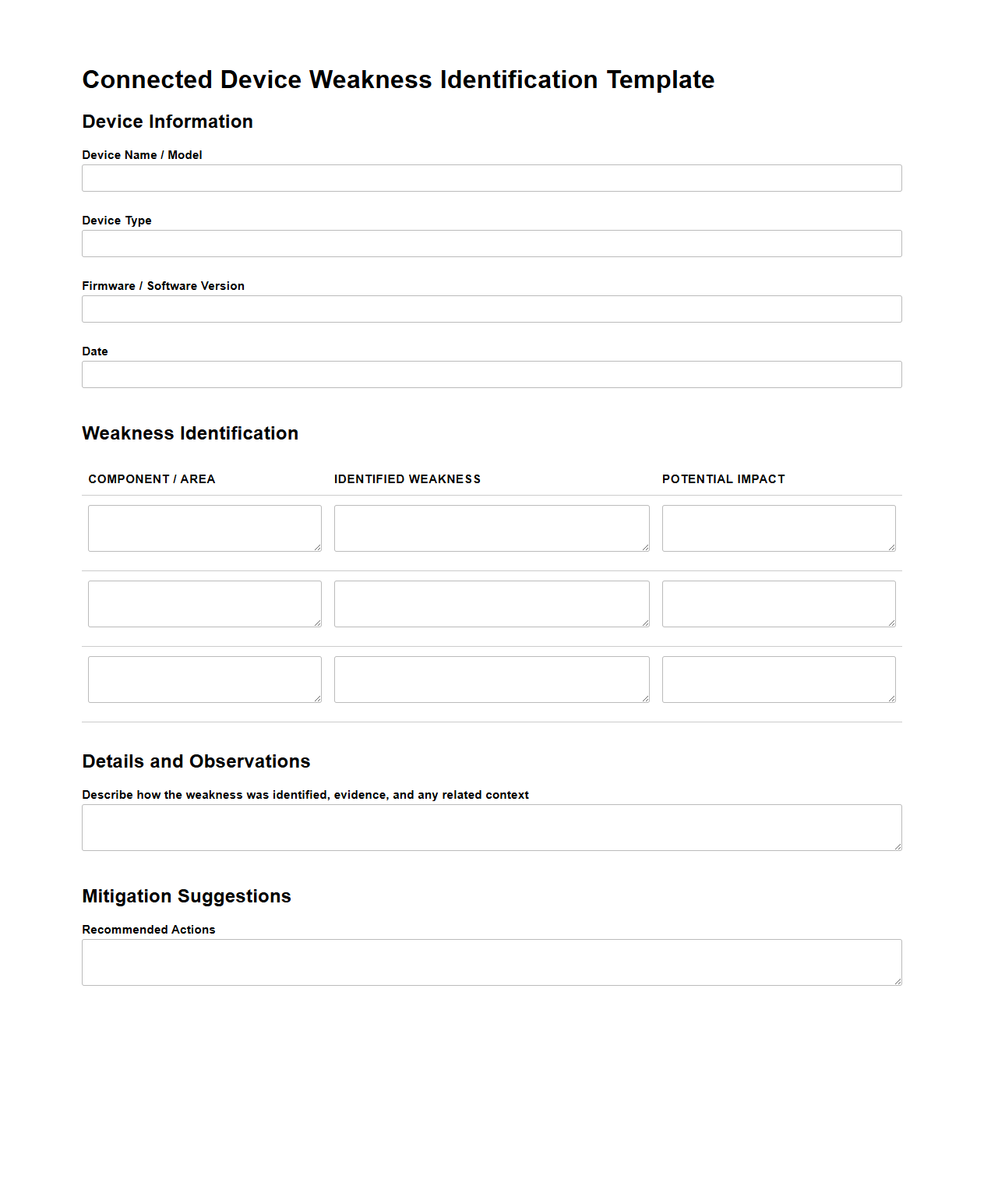
Connected Device Weakness Identification Template
The
Connected Device Weakness Identification Template document serves as a structured framework to systematically identify and categorize vulnerabilities in IoT devices and related technologies. It enables security teams to document potential weaknesses based on device architecture, communication protocols, and software dependencies, facilitating comprehensive risk assessments. This template supports proactive mitigation strategies by providing a standardized approach to vulnerability analysis in connected device ecosystems.
Smart Home Penetration Test Results Outline
The
Smart Home Penetration Test Results Outline document provides a structured summary of vulnerabilities identified during the security assessment of smart home devices and networks. It details findings such as unauthorized access points, data leakage risks, and firmware weaknesses, enabling stakeholders to understand security gaps clearly. The document also offers prioritized remediation recommendations to enhance the overall safety and integrity of smart home environments.
IoT Home System Vulnerability Inventory Sample
The
IoT Home System Vulnerability Inventory Sample document provides a structured overview of potential security weaknesses within smart home devices and networks. It catalogs identified vulnerabilities, categorizes them by risk level, and suggests mitigation strategies to enhance the protection of interconnected household technologies. This document serves as a critical tool for developers, security analysts, and homeowners aiming to safeguard IoT environments against cyber threats.
What encryption protocols are detailed in the vulnerability assessment for smart home device communications?
The assessment highlights TLS (Transport Layer Security) as the primary encryption protocol used in smart home device communications. It also references the use of AES (Advanced Encryption Standard) for securing data transmission between devices. The report emphasizes the importance of implementing robust encryption standards to defend against interception and unauthorized access.
How does the document address risks associated with third-party IoT integrations?
The report identifies significant risks linked to third-party IoT integrations due to varying security practices. It recommends thorough vetting of third-party vendors and continuous monitoring of their software updates. Additionally, the document advises enforcing strict access controls to minimize exposure from external components.
What device authentication methods are evaluated in the assessment report?
The document evaluates several device authentication methods, focusing on certificate-based authentication and secure token mechanisms. It highlights the effectiveness of multi-factor authentication in strengthening device identity verification. The report also discusses potential vulnerabilities in password-based methods if not implemented securely.
Are firmware update mechanisms analyzed for security gaps in the document?
Yes, the assessment thoroughly examines firmware update mechanisms for potential security vulnerabilities. It stresses the necessity of implementing secure update protocols such as digitally signed firmware and encrypted transmission channels. The report warns against the risks of outdated or improperly secured firmware leading to device compromise.
How are discovered vulnerabilities prioritized and recommended for remediation in the report?
The report employs a risk-based prioritization framework to classify vulnerabilities by severity and potential impact. It recommends immediate remediation for critical vulnerabilities, followed by systematic patching of less severe issues. Furthermore, the document provides tailored guidance for addressing each type of vulnerability efficiently.
More Technology Templates