A Incident Response Document Sample for Cybersecurity provides a structured template to effectively manage and mitigate cyber threats. It outlines clear procedures for identifying, containing, and recovering from security incidents, ensuring a swift and organized response. This document enhances an organization's preparedness by defining roles, communication plans, and step-by-step actions to minimize damage and restore normal operations.
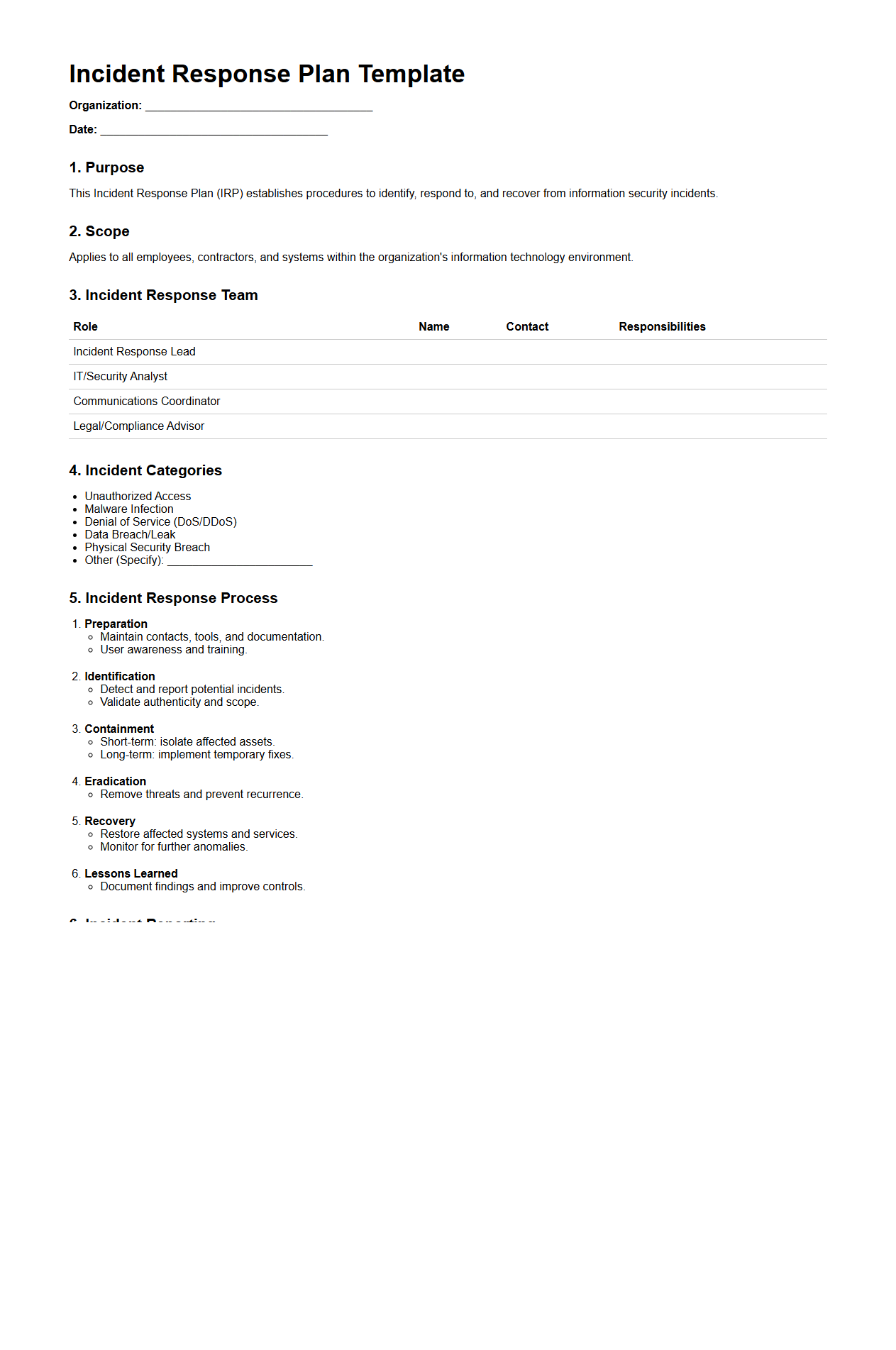
Incident Response Plan Template for Cybersecurity Teams
An
Incident Response Plan Template for cybersecurity teams serves as a structured framework designed to guide organizations in efficiently managing and mitigating the impact of security breaches. It outlines predefined roles, communication protocols, and step-by-step procedures for identifying, containing, eradicating, and recovering from cyber incidents. This template ensures a consistent, timely, and coordinated response to cyber threats, minimizing damage and supporting regulatory compliance.
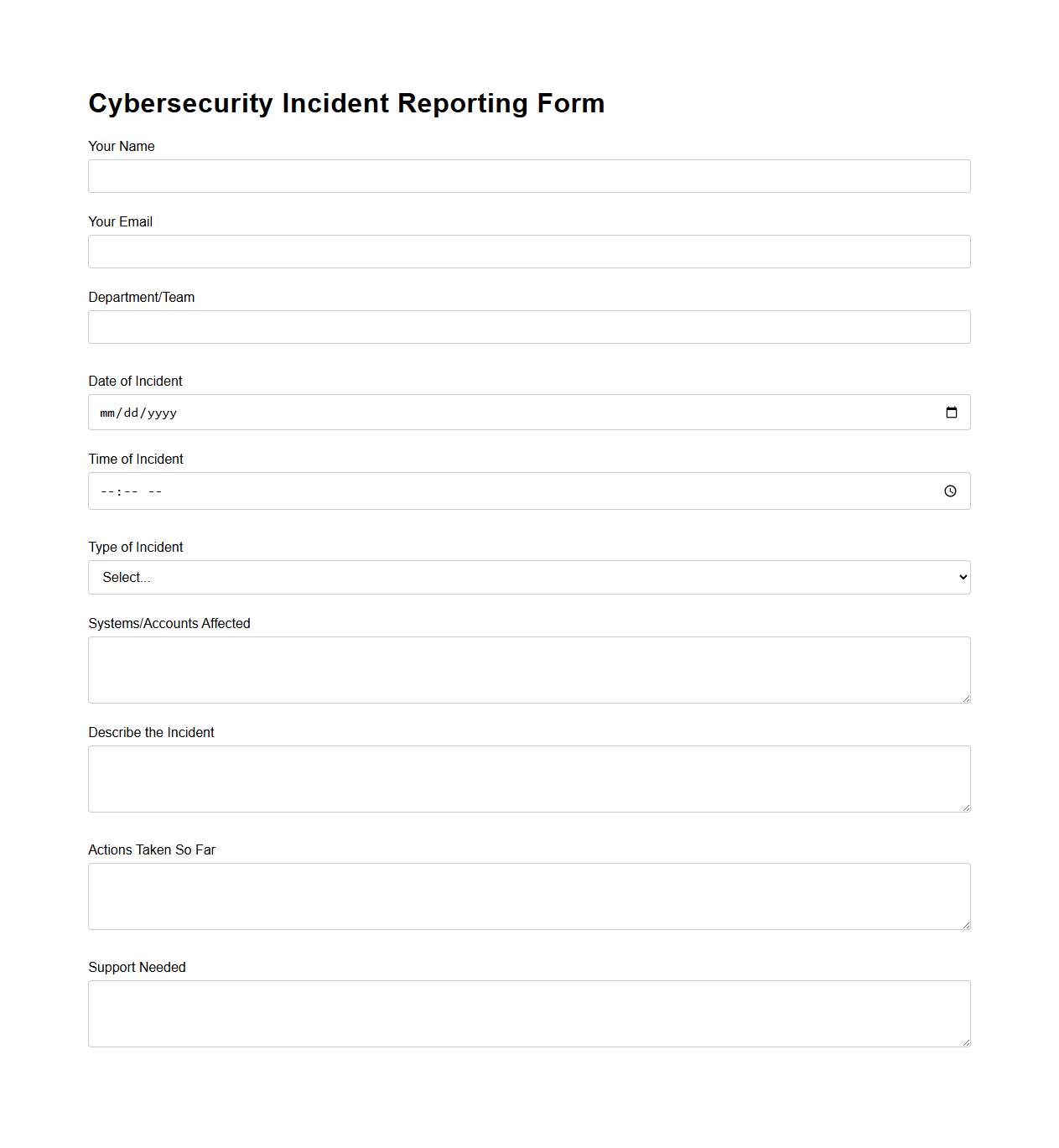
Cybersecurity Incident Reporting Form Example
A
Cybersecurity Incident Reporting Form Example document serves as a standardized template for organizations to document and report security breaches promptly. It typically includes fields for incident type, date and time, affected systems, description of the event, and immediate actions taken. Utilizing this form enhances incident response efficiency and supports compliance with regulatory requirements.
Security Breach Notification Letter Sample
A
Security Breach Notification Letter Sample document serves as a template for organizations to inform affected individuals about unauthorized access to their personal or sensitive information. It outlines key details such as the nature of the breach, the data compromised, and recommended steps for mitigation. This document ensures legal compliance and helps maintain transparency and trust with customers or clients.
Post-Incident Review Report for Cybersecurity Events
The
Post-Incident Review Report for Cybersecurity Events document provides a detailed analysis of a cybersecurity incident, outlining the timeline, root cause, impact, and response effectiveness. It serves as a critical tool for identifying vulnerabilities, improving security measures, and preventing future incidents by documenting lessons learned. This report is essential for compliance, risk management, and continuous improvement in an organization's cybersecurity posture.
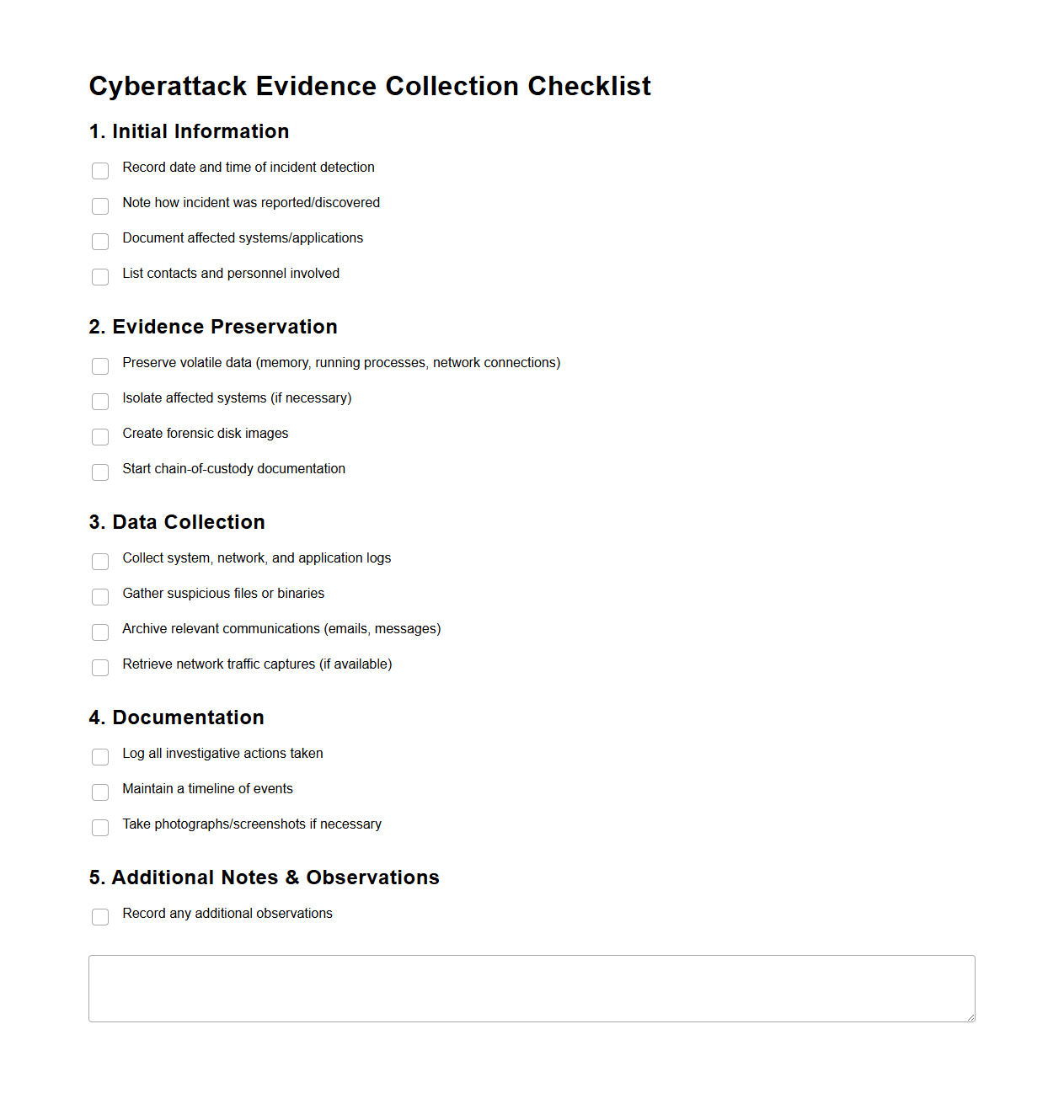
Cyberattack Evidence Collection Checklist
The
Cyberattack Evidence Collection Checklist document serves as a structured guide to systematically gather and preserve digital evidence following a cyberattack. It outlines essential steps such as identifying affected systems, securing logs, capturing volatile data, and maintaining chain of custody to ensure evidence integrity. This checklist is critical for incident response teams and forensic investigators aiming to conduct thorough analysis and support legal proceedings.
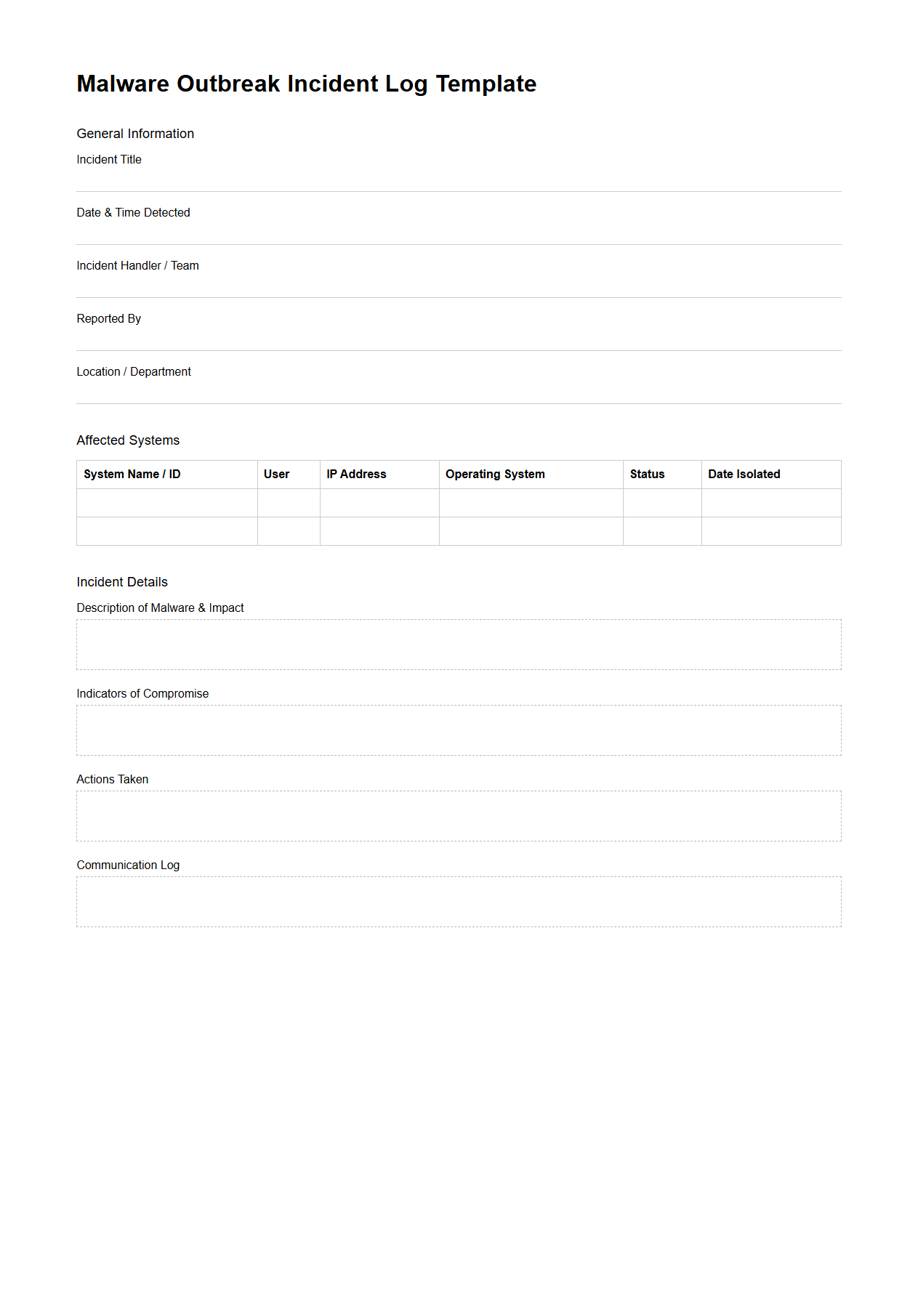
Malware Outbreak Incident Log Template
The
Malware Outbreak Incident Log Template document is a structured tool designed for systematically recording and tracking details of malware incidents within an organization. It captures critical information such as malware type, infection timeline, affected systems, response actions, and containment measures to enable efficient incident management and post-incident analysis. This template supports cybersecurity teams in ensuring consistent documentation, improving threat detection accuracy, and facilitating regulatory compliance during malware outbreak investigations.
Phishing Attack Response Documentation Sample
A
Phishing Attack Response Documentation Sample document provides a structured template for organizations to record their procedures and actions taken during a phishing incident. It includes detailed steps for detection, containment, mitigation, and recovery, ensuring a consistent and efficient response to minimize operational impact and data loss. This documentation serves as a crucial reference for cybersecurity teams to improve future incident handling and compliance reporting.
IT Security Incident Investigation Report
An
IT Security Incident Investigation Report document details the analysis and findings of a cybersecurity breach or threat within an organization's information technology infrastructure. It systematically records the nature of the incident, affected systems, investigation methods, and remedial actions taken to prevent recurrence. This report is crucial for ensuring accountability, compliance with regulatory standards, and enhancing future cybersecurity defenses.
Compromised Account Action List Example
A
Compromised Account Action List Example document provides a structured guide to identifying, responding to, and mitigating risks associated with compromised user accounts. It outlines specific steps such as account suspension, password resets, multi-factor authentication enforcement, and incident reporting to security teams. This document is crucial for maintaining security protocols and minimizing damage in cybersecurity breach scenarios.
Ransomware Incident Containment Procedure Form
The
Ransomware Incident Containment Procedure Form document outlines a structured approach to effectively isolate and mitigate ransomware attacks within an organization's IT environment. It includes step-by-step guidelines for identifying infected systems, halting the spread of malware, and preserving critical evidence for forensic analysis. This procedure is essential for minimizing operational disruption and safeguarding sensitive data during ransomware incidents.
Mandatory Steps in Incident Escalation
The Incident Response Document mandates immediate notification to the designated incident response team upon detection of a security event. It requires a clear escalation path defining the roles responsible for advancing the issue through management layers. Additionally, the document emphasizes timely communication to ensure swift containment and mitigation actions.
Specified Team Roles for Initial Detection and Assessment
The document specifies that the first responders are typically security analysts or IT staff tasked with monitoring and initial incident detection. These roles are responsible for assessing the severity and scope of the incident promptly. Their assessment determines the escalation level and necessary resource allocation for response efforts.
Evidence Preservation During Cybersecurity Incidents
The Incident Response Document highlights the importance of preserving digital evidence to support forensic investigation and legal compliance. It outlines protocols for collecting, handling, and storing data to prevent tampering or loss. Proper evidence preservation ensures that incident root causes can be accurately determined and documented.
Reporting Timelines for Notifying Stakeholders
The document enforces strict reporting timelines to notify stakeholders, including management and affected parties, within 24 hours of incident confirmation. It mandates regular status updates throughout the incident lifecycle to maintain transparency and coordinate response actions. These timelines help minimize impact and support regulatory compliance.
Post-Incident Review Procedures
The response documentation details comprehensive post-incident review procedures to evaluate the effectiveness of the response. This includes conducting debrief meetings, identifying lessons learned, and updating policies to prevent recurrence. Such reviews are crucial for continuous improvement of the security posture and incident response capabilities.
More Technology Templates